Jennifer Marsh
With a background in software engineering, Jennifer Marsh has a passion for hacking and researching the latest cybersecurity trends. Jennifer has contributed to TechCrunch, Microsoft, IBM, Adobe, CloudLinux, and IBM. When Jennifer is not programming for her latest personal development project or researching the latest cybersecurity trends, she spends time fostering Corgis.
by Jennifer Marsh | Aug 30, 2024 | Phishing & Email Spam |
QR codes are used for a wide range of purposes, including marketing, communications, and even in restaurants to direct diners to menus, and with the popularity of QR codes soaring it should be no surprise that they are being used by cybercriminals in their phishing campaigns. QR codes are similar to the bar codes on products. They are black and white images that contain information, which for QR codes is commonly a URL for a web page or hosted file. A camera on a smartphone is used to scan the code, which will detect the URL, and the user can click that URL to visit the resource. It is far more convenient than entering a URL on a mobile phone keypad.
The use of QR codes has been growing considerably. According to a 2024 report from QR Tiger on QR Code trends, there has been 47% year-over-year growth in QR code usage. The convenience of QR codes and their growing popularity have not been lost on cybercriminals who are using QR codes to direct unsuspecting users to malicious websites that host malware or are used to phish for credentials. As an added advantage, many traditional security solutions are unable to assess the URLs in QR codes and fail to block access to malicious sites.
QR code phishing (aka quishing) may involve QR codes sent via email. Instead of embedding a hyperlink in an email, a QR code is used to evade email security solutions. A novel campaign has recently been detected by security researchers at Netskope Threat Labs that uses QR codes to steal Microsoft 365 credentials. In this campaign, a Microsoft 365 product called Microsoft Sway is abused to host the spoofed web pages.
Microsoft Sway is used for creating newsletters and presentations and was first released by Microsoft under the M365 product suite in 2015. Since Microsoft Sway is a legitimate Microsoft cloud-based tool, a link to a Sway presentation is unlikely to be identified as malicious by security solutions, as Sway is a trusted platform. The link to the Sway presentation may be distributed in emails, SMS messages, and instant messenger platforms, or can be added to websites in an iframe. A QR code could even be used to direct a user to the Sway presentation.
That presentation includes a QR code that encodes a URL for a website that masquerades as a legitimate Microsoft site. If scanned, the user is directed to a web page where they are asked to enter their Microsoft 365 credentials. What makes this campaign even harder for users to identify is the transparent phishing technique used. Entering credentials will log the user into the legitimate site, and at the same time credentials are captured along with any MFA code, which are relayed to the attacker. The credentials and MFA code are then used to hijack the account.
TitanHQ offers several cybersecurity solutions that provide layered protection against advanced phishing attempts, including quishing. Since these scams target individuals, it is important to raise awareness of the threat by providing security awareness training to the workforce. The SafeTitan platform from TitanHQ includes a wealth of training content, including modules for raising awareness of quishing. The platform also includes a phishing simulator with quishing templates to test whether employees scan QR codes and visit the websites they encode.
Regardless of how a URL is communicated to a member of the workforce, it is possible to block access to a malicious URL with a DNS filter. TitanHQ’s DNS filter, WebTitan, blocks access to all known malicious websites and is constantly updated with the latest threat intelligence from a global network of users. As soon as a malicious URL is detected, the solution is updated and all WebTitan users are protected. QR code may direct users to websites where malware is downloaded. WebTitan can be configured to block file downloads from the internet by file type.
QR codes are commonly sent via email, so an advanced email security solution is required. SpamTitan is a cutting-edge spam filtering service that uses advanced detection techniques, including AI and natural language processing to identify and block these threats, even zero-minute phishing attempts. In contrast to many spam filters for incoming mail, SpamTitan can detect novel phishing and quishing attempts. Finally, businesses can add another layer of protection through PhishTitan, TitanHQ’s advanced anti-phishing solution for Microsoft 365 which blocks attempts to visit phishing sites and allows security teams to easily remediate phishing attempts across their entire email system.
Phishers are constantly developing new tactics and techniques for distributing malware and stealing credentials, but with TitanHQ solutions in place, you will be well protected against these rapidly evolving threats. Talk with TitanHQ’s cybersecurity experts today for more information on staying one step ahead of cybercriminals and keeping your company safe.
by Jennifer Marsh | Aug 30, 2024 | Internet Security, Security Awareness |
A malvertising campaign is behind a surge in FakeBat malware infections, according to researchers at Google’s Mandiant. FakeBat is a malware loader that is offered to other cybercriminals under the malware-as-a-service model. Once infected with FakeBat, system information is gathered and exfiltrated to its command-and-control server, and if the victim is of interest to the threat actor’s business partners, they can use FakeBat to download their own payloads onto an infected device. FakeBat, also known as EugenLoader, has fast become a major player among cyber threats with infections increasing significantly in recent months due to the ability of the malware to evade security solutions and hide the additional payloads it delivers.
FakeBat malware is primarily distributed via malvertising and drive-by downloads. Malvertising is the name given to malicious adverts that trick Internet users into downloading malicious software. Malicious adverts are created on online advertising platforms such as Google Ads, and the adverts then appear prominently at the top of search engines for certain search terms. They often catch unwary Internet users who fail to check the URL they are directed to after clicking an advert. Google has numerous safeguards in place to thwart attempts by threat actors to upload malicious adverts to its platform, but threat actors can bypass those security controls. Malicious adverts may also appear in the third-party ad blocks that many website owners add to their sites to generate additional revenue. The domains used for these scams can be convincing, as they often closely resemble the domain name of the legitimate software provider.
Drive-by downloads of malware can occur on many different websites, including attacker-owned domains and compromised sites. Websites may be created for the sole purpose of delivering malware, with black hat search engine optimization (SEO) techniques used to get web pages to appear high in the search engine listings for certain search terms. Cybercriminals may also compromise legitimate websites by exploiting vulnerabilities and then create new web pages on those sites for malware distribution. These sites often contain JavaScript that runs when a user lands on the site and generates a fake security warning, such as an alert that malware has been detected on their device. Software is offered to remove the malware, but downloading the installer will result in malware being installed.
These approaches are often used to target company employees, with adverts and malicious web pages offering popular software downloads. The adverts and websites are carefully crafted to make the user believe they are downloading the genuine software they seek. Oftentimes, the adverts and websites provide legitimate software; however, the installers also side-load malware. These malware infections often go unnoticed since the user gets the software they are expecting.
The malvertising campaigns that deliver FakeBat malware use signed MSIX installers that impersonate popular software products such as WinRAR, the password software KeePass, the gaming platform Steam, the video conferencing platform Zoom, and web browsers such as Brave. Malware known to be delivered by FakeBat includes information stealers (e.g. Redline Stealer, Lumma Stealer), banking trojans (e.g. IcedID), Remote access Trojans (e.g. SectopRAT), and more. The threat actor is also known to use phishing to distribute FakeBat malware.
Businesses should ensure they take steps to prevent malware infections via malvertising and drive-by downloads, as a single mistake by an employee can result in a costly malware infection and data breach and could potentially also lead to a ransomware attack and significant data loss.
TitanHQ offers cybersecurity solutions that offer multiple layers of protection against malware infections. Since these campaigns trick employees into installing malware, one of the best defenses is to provide comprehensive security awareness training. TitanHQ’s SafeTitan security awareness training platform makes it easy for businesses to improve the security awareness of their workforce by eradicating risky behaviors and teaching employees how to recognize, avoid, and report threats. The platform also includes a phishing simulator to test employees’ skills at identifying phishing attempts with training content automatically generated in response to simulation failures.
Technical defenses are also important to prevent employees from visiting malicious websites. The WebTitan DNS filter is a powerful tool for carefully controlling access to websites. WebTitan blocks access to all known malicious sites and can be configured to block certain file downloads from the Internet, such as MSIX installers. TitanHQ’s SpamTitan cloud-based spam filter and the PhishTitan anti-phishing solution provide cutting-edge protection against phishing attempts. The engine that powers these solutions has been independently tested and demonstrated to block 100% of known malware. SpamTItan also includes email sandboxing for identifying malware by its behavior, in addition to twin antivirus engines for blocking known malware, and machine learning capabilities to detect novel phishing threats.
To find out more about improving your defenses against malvertising, drive-by downloads, phishing, and other cyber threats, give the TitanHQ team a call. All TitanHQ solutions are also available on a free trial to allow you to put them to the test before making a purchase decision.
by Jennifer Marsh | Aug 29, 2024 | Phishing & Email Spam, Security Awareness |
If a phishing attempt is successful and a threat actor gains access to an employee’s email account, it is common for the compromised email account to be used for internal phishing. Some malware variants also allow threat actors to hijack email accounts and send malware internally, adding a copy of the malware to a message thread to make it appear that a file was attached in response to a past email conversation.
There are several different scenarios where these types of attacks will occur such as business email compromise attacks to gain access to an email account that can be used for the scam – a CEO, executive, HR, or IT department account for example; to distribute malware extensively to compromise as many accounts as possible; to gain access to multiple email accounts, or to compromise multiple accounts to gain access to sensitive data.
In industries where data breach reporting is mandatory, such as in healthcare in the United States, email account breaches are regularly reported where unauthorized activity is detected in a single email account, and the subsequent investigation reveals multiple employee email accounts have been compromised through internal phishing.
Internal phishing attempts are much harder to identify than phishing attempts from external email accounts. Even when email security solutions incorporate outbound scanning, these phishing attempts are often not recognized as malicious as the emails are sent from a trusted account. The recipients of these emails are also much more likely to trust an internal email than an external email from an unknown sender and open the email, click a link, or open a shared file.
Attackers may also spoof an internal email account. It is easy to find out the format used by a company for their emails, and names can be found on professional networking sites. A good email security solution should be able to identify these spoofed emails, but if they arrive in an inbox, an employee may be fooled into thinking that the email is a genuine internal email.
It is important for businesses to take steps to combat internal phishing as it is a common weak point in email defenses. Unfortunately, there is no single technical control that can protect against these phishing attempts. What is required is a combination of measures to provide layered protection. With layered security, if one measure fails to protect against a threat, others are in places that can thwart the attempt.
The best place to start is with a technical measure to identify and block these phishing threats. Spam filter software naturally needs to have inbound as well as outbound scanning; however, standard checks such as reputation scans are not enough. An email security solution should have AI and machine learning capabilities for assessing how emails deviate from standard emails sent internally and for in-depth analysis of message content. Link scanning is also important, with URL rewriting to identify the true destination of embedded URLs, OLE detection, and email sandboxing to identify malicious attachments – not just malware but also malicious links in email attachments.
Security awareness training is vital as employees may not be aware of threats they are likely to encounter. Security awareness training should include internal phishing and employees should be made aware that they should not automatically trust internal emails as they may not be what they seem. Security awareness training should be accompanied by phishing simulations, including simulated phishing attempts from internal email accounts. These will give employees practice in identifying phishing and security teams will learn how susceptible the workforce is and can then take steps to address the problem.
Multi-factor authentication is required. If a phishing attempt is not identified by either a security solution or the employee, and the employee responds and divulges their credentials, they can be used by the threat actor to access the employee’s email account. Multi-factor authentication protects against this by requiring another factor – in addition to a password – to be provided. The most robust form of MFA is phishing-resistant MFA, although any form of MFA is better than none.
TitanHQ can help protect against phishing attacks of all types through the SpamTitan cloud-based spam filtering service, the PhishTitan anti-phishing solution for M365, and the SafeTitan Security awareness training and phishing simulation platform.
The engine that powers SpamTitan and PhishTitan has an exceptional phishing catch rate, including internal phishing attempts. The engine incorporates AI- and machine learning algorithms that can detect novel phishing attempts and emails that deviate from the normal emails sent internally, as well as OLE detection, URL rewriting, and email sandboxing for catching novel malware and phishing threats.
The SafeTitan Security awareness training platform includes an extensive library of training content to teach security best practices, eradicate risky behaviors, and train employees on how to recognize an extensive range of threats. The phishing simulator makes it easy to conduct internal phishing tests on employees to test knowledge and give employees practice at identifying email threats. Usage data shows the platform can reduce employee susceptibility to phishing attempts by up to 80%.
For more information about improving your phishing defenses, speak with TitanHQ today.
by Jennifer Marsh | Aug 28, 2024 | Spam Software |
Phishing is the name given to a type of cyberattack where the threat actor uses deception to trick an individual into taking an action that benefits the threat actor. A lure is used to get the targeted individual to respond and these attacks typically create a sense of urgency. Urgency is required as phishers need users to act quickly rather than stop and think about the request. The faster the response, the less time there is to identify the scam for what it is. There is often a threat to help create a sense of urgency, such as negative consequences if no action is taken.
Phishing can take place over the phone, SMS, and instant messaging platforms, but email is the most common way of getting the phishing lure in front of an employee. It is now common for businesses to provide security awareness training to the workforce to raise awareness of phishing threats and to have a spam email filter in place to detect and quarantine these malicious emails before they reach inboxes; however, even with robust defenses in place, some malicious emails will arrive in inboxes and employees are often tricked into responding.
Security awareness training programs teach employees to stop and think before taking any request in an email, which is the last thing phishers want the recipients of their emails to do. One of the ways they can get a quick response is to make the recipient believe that the email has been sent from an internal email account, either through spoofing or by using a compromised internal email account. Some of the lures used in phishing attempts that the majority of employees will at least open and read, are detailed below.
HR Themed Phishing Emails
One of the ways that phishers increase the chance of a user responding is to use Human Resources (HR)-themed lure, as any communication from the HR department is usually taken seriously by employees. These phishing attempts include the types of notifications that HR departments often send via email, examples of which include:
- Changes to working hours
- Updates to working practices
- Dress code changes
- Upcoming training/cybersecurity training sessions
- Annual leave notifications
- Payroll information requests
- Tax matters
- Healthcare and wellness benefit updates
- Employee rewards programs
- Notifications about disciplinary procedures
IT Department Notifications
Notifications from the IT department are also common as employees typically open these emails and act quickly. These include:
- Internet activity reports
- Security alerts
- The discovery of unauthorized software
- Changes to access rights
- Requires software installations
Notifications from Board Members
Phishers often impersonate the CEO or other executives, as they know that employees will want to respond quickly and are unlikely to question requests from these authority figures. CEOs are commonly impersonated in business email compromise attacks, where the threat actor tries to get an employee to make a wire transfer to their account, purchase gift cards, or divulge sensitive information. These emails may include a hyperlink to a website where the user is told they must enter their login credentials, a hyperlink to a website where a file download takes place, or the emails may include an attachment. Common file types used in these email campaigns include PDF files, HTML attachments, Office files, and compressed files. These files may contain malware or malicious scripts, or may be used to hide information from spam filtering software. For example, PDF files are commonly used that contain malicious links. By adding the link to the PDF file, there is less chance that spam filtering software will find and follow the link.
How to Defend Against These Common Email Threats
Defending against email attacks requires advanced anti spam software and regular security awareness training for the workforce. SpamTitan from TitanHQ is an advanced cloud-based anti-spam service that performs comprehensive checks for spam and malicious emails, including an inbound spam filter and outbound filtering with data loss prevention. SpamTitan performs reputation checks of the sender’s domain and email account, recipient verification, anti-spoofing checks, and alias recognition, and allows geoblocking to prevent the delivery of emails from certain locations (overseas, for instance).
SpamTitan also incorporates extensive content filtering mechanisms, including rewriting URLs to identify the true destination, URL checks to identify malicious content, anti-phishing measures including machine learning algorithms to detect suspicious content that deviates from the standard emails typically received, Bayesian analysis to identify spam and phishing, OLE detection, dual antivirus engines, and email sandboxing. Sandboxing is key to blocking malware threats, including previously unseen malware. With SpamTitan in place, the vast majority of threats will not arrive in inboxes. In recent independent tests, SpamTitan had a 99.99% spam detection rate, a 99.98% phishing detection rate, and a 100% malware detection rate, with zero false positives.
TitanHQ also offers a comprehensive security awareness training platform called SafeTitan. SafeTitan makes it easy for businesses to create and automate security awareness training programs for the workforce, and tailor programs for different departments and user groups. The content is fun and engaging and is delivered in modules of more than 10 minutes, which makes security awareness training easy to fit into busy workflows. SafeTitan also includes a phishing simulator for assessing the effectiveness of training and for giving employees practice at identifying phishing attempts, including the types of phishing attempts mentioned in this article that often fool employees.
SpamTitan and SafeTitan, like all TitanHQ solutions, are easy to implement, use, and maintain, and are available on a free trial. For advice on improving cybersecurity at your business and for further information on TitanHQ solutions, call the team today and take the first step toward improving your security posture.
by Jennifer Marsh | Aug 27, 2024 | Security Awareness |
Do you provide security awareness training to your workforce? If so, when was the last time you updated the content? Chances are you are not keeping your employees sufficiently up to date on the rapidly changing tactics, techniques, and procedures used by cybercriminals which means your training will not be as effective as it should be.
Security awareness training used to be a relatively straightforward process aimed at teaching members of the workforce good cybersecurity practices such as choosing complex passwords, exercising caution when entering sensitive information on screen to ensure they are not being watched, and looking for spelling mistakes, grammatical errors, unusual email addresses, and other signs of phishing emails. Providing an annual security awareness training session once a year or biannually was satisfactory, but things are now very different.
Cybercriminals are constantly developing new ways of tricking employees, translators are much more accurate than they once were, and generative AI can be leveraged not only to create phishing emails free of errors but these tools can also be used to create new lures to trick employees into responding, not to mention the use of deepfakes that can be incredibly convincing.
While the main threat is still email-based attacks, cybercriminals are using a range of methods to reach employees including SMS messages, instant messaging services, social media platforms, and voice phishing, and often a combination of those methods. For example, initial contact may be made via email, and the recipient is told to call the provided phone number urgently to prevent a payment for a subscription service from being taken from their account. Tactics are also changing rapidly, with new attacks on employees constantly being developed. Any training program that is not constantly being changed to reflect these new tactics means there will be significant knowledge gaps and cybercriminals will be all too quick to exploit.
While the aim of security awareness training for many businesses is to raise the baseline level of knowledge and ensure that everyone is aware of security risks that they are likely to encounter, given the rapidly changing threat landscape and the sophistication of phishing and BEC attacks, more needs to be done.
Security awareness training should be an ongoing process, with training provided regularly throughout the year. Training should be provided at least monthly and preferably weekly, using short training modules that can be completed in just a few minutes. Providing training regularly in small bite-size chunks helps to keep cybersecurity fresh in the mind, makes it more likely that the information will be remembered, allows businesses to keep employees up to date on changing tactics, and it is much easier to fit the training into busy workflows. The training content can be completed when employees find they have 10 minutes spare.
Developing a training course is time-consuming, especially when the content needs to be regularly refreshed. The easiest approach is to use a training vendor who keeps their content up to date based on the latest threat intelligence and provides a platform that makes creating tailored training courses for businesses and the individuals who work there a quick and easy process.
The SafeTitan platform from TitanHQ has been developed to make security awareness training simple for employers, allowing them to create effective training courses tailored for each individual, job role, or department. The platform makes it easy to automate training programs so they run continuously throughout the year, including automated training in response to errors by employees. When a security error is made, training relevant to that error is immediately generated. That means the problem is nipped in the bud as training is delivered when it is most likely to have the desired effect – changing behavior to prevent similar errors in the future.
The SafeTitan platform includes hundreds of training modules of no more than 10 minutes, which can be easily customized and compiled into training courses for all job roles and knowledge levels, with new content constantly added based on the latest threat intelligence. The platform includes a phishing simulator that allows simulations to be conducted to give employees practice at identifying threats as well as to provide management with feedback on the effectiveness of the training. Weak links can be identified and corrected through further training and, like the training courses, the simulations can be automated.
The SafeTitan platform allows businesses to adopt a more proactive approach to security awareness training to stay one step ahead of cybercriminals and develop a security culture through training where employees can recognize, avoid, and report security threats. Coupled with the SpamTitan anti-spam service and the PhishTitan anti-phishing platform, businesses will be well protected in this ever-changing threat landscape.
Give the TitanHQ team a call to find out more about improving your technical defenses against phishing, malware, and other threats as well as creating a formidable human firewall. All TitanHQ solutions are available on a free trial and the team will be happy to arrange a product demonstration to help get you started.
by Jennifer Marsh | Aug 27, 2024 | Phishing & Email Spam, Security Awareness |
Business email compromise (BEC) and vendor email compromise (VEC) attacks can result in huge financial losses that can prove catastrophic for businesses, and these attacks are being conducted with increasing regularity.
BEC and VEC attacks have their roots in phishing and often involve phishing as the first stage of the attack. These attacks involve impersonation of a trusted person through spoofed or compromised email accounts. The attacker then tricks the targeted individual into disclosing sensitive information or making a fraudulent wire transfer. In the case of the latter, the losses can be considerable. A company employee at Orion, a Luxembourg carbon black supplier, resulted in fraudulent transfers of $60 million. The employee was tricked into believing he was conversing with a trusted vendor and made multiple fraudulent transfers to the attacker’s account.
BEC and VEC attacks are among the most difficult email threats to detect, as they often use legitimate, trusted email accounts so the recipient of the email is unaware that they are conversing with a scammer. Since the attacker often has access to emails, they will be aware of confidential information that no other individual other than the genuine account holder should know. The attacker can also check past emails between the account holder and the victim and can mimic the writing style of the account holder. These attacks can be almost impossible for humans to distinguish from genuine communications. Scammers often reply to existing email threads, which makes these scams even more believable.
BEC/VEC scammers are increasingly turning to AI tools to improve their attacks and AI tools make these scams even harder for humans and email security solutions to identify. AI tools can be fed past emails between two individuals and told to create a new email by mimicking the writing style, resulting in perfect emails that could fool even the most security-aware individual.
Some of the most convincing VEC attacks involve the use of compromised email accounts. The attacker gains access to the account through phishing or stolen credentials and searches through the account for information of interest that can be used in the scam. By searching through sent and stored emails, they can identify the vendor’s clients and identify targets. They are then sent payment requests for fake invoices, or requests are made to change the bank account information for genuine upcoming payments.
Due to the difficulty of identifying these threats, a variety of measures should be implemented to improve defenses, including administrative and technical controls, as well as employee training. In order to beat AI tools, network defenders need to adopt AI themselves, and should implement a spam filter with AI and machine learning capabilities, such as the SpamTitan cloud-based spam filtering service.
SpamTitan analyzes the genuine emails received by the company to create a baseline against which other emails can be measured. Through machine learning, Bayesian analysis, and other content checks, SpamTitan is able to identify the signs of BEC/VEC and alert end users when emails deviate from the norm. An anti-phishing solution is also strongly recommended to protect accounts against initial compromise and to raise awareness of potential threats. PhishTitan from TitanHQ incorporates cutting-edge threat detection with email banners warning about external emails and other threats and allows IT teams to rapidly remediate any attacks in progress.
Security awareness training is essential for raising awareness of the threat of BEC and VEC attacks. Since these scams target executives, IT, and HR staff, training for those users is vital. They should be made aware of the threat, taught how to identify these scams, and the actions to take when a potentially malicious message is received. With the SafeTitan security awareness training program it is easy to create training courses and tailor the content to cover threats each user group is likely to encounter to ensure the training is laser-focused on the most pertinent threats.
While spam email filtering and security awareness training are the most important measures to implement, it is also important to strengthen defenses against phishing through the adoption of multi-factor authentication on all email accounts, to prevent initial compromise. Administrative controls should also be considered, such as requiring employees to verify any high-risk actions, such as changes to bank accounts or payment methods, and maintaining a contact list of verified contact information to allow phone verification of any high-risk change. This two-step verification method can protect against all BEC/VEC attacks and prevent fraudulent payments.
by Jennifer Marsh | Aug 27, 2024 | Industry News |
TitanHQ has upgraded its award-winning SpamTitan email security solution, with the latest release including several enhancements to improve protection against malware, phishing, and other advanced threats. The latest release – version 9 – of the flagship email security solution is named SpamTitan Skellig, which includes major enhancements to the anti-spam engine at the core of the solution to improve malware detection and new phishing enhancements to protect against ever-evolving sophisticated threats.
SpamTitan is a leading cloud-based anti-spam service that has been shown in recent independent tests to provide exceptional protection against spam, phishing emails, and malware. The hosted spam filter includes a next-gen email sandbox, up-to-the-minute threat intelligence feed, AI and machine learning algorithms, twin antivirus engines, and more. In June 2024, Virus Bulletin put the new version of SpamTitan to the test and gave it VBSpam+ certification, with the solution achieving the second-highest final score in the test of 12 leading email security solutions. SpamTitan successfully blocked all malware samples, only missed one phishing email, and did not generate any false positives. SpamTitan had a malware catch rate of 100%, a phishing catch rate of 99.99%, a spam catch rate of 99.98%, and was given an overall score of 99.984%.
The update to SpamTitan Skellig will ensure that users continue to have best-in-class protection against email threats but there is more to the update than protecting against threats. SpamTitan has long been popular with end users due to the ease of use of the solution, which is why users consistently give the solution 5-star reviews. The latest release includes a brand new UI that is even more intuitive with improved navigation and better administrative functions across the board and makes it easier to onboard new users.
The upgraded version is available to all new users and current users can upgrade and get better protection at no additional cost for the upgrade and no change to the subscription price, with full assistance provided with upgrading if required. You can find out more about migrating to the new version here.
by Jennifer Marsh | Aug 20, 2024 | Phishing & Email Spam |
Russian threat actors have been conducting increasingly advanced phishing campaigns against media organizations, international NGOs, and other targets perceived as being a threat to Russia. According to a recent report from Access Now and Citizen Lab, several international NGOs have reported being targeted with spear phishing emails in a campaign that has been ongoing since the start of 2023.
The campaign has been attributed to a threat actor known as COLDRIVER (aka Star Blizzard, Calisto) which multiple governments have attributed to the Russian Federal Security Service (FSB), and another campaign has been conducted by a second threat group, a relatively;y new threat group known as COLDWASTREL, whose interests align with those of COLDRIVER.
The campaigns aim to steal credentials rather than infect devices with malware. Spear phishing emails are used to make initial contact and trick the targets into disclosing their credentials. Emails are sent to individuals that have been highly personalized to maximize the probability of the recipient responding. A common theme was to make initial contact by masquerading as a person known to the target, including colleagues, funders, and U.S. government employees.
One of the common lures used in the emails was to request that the recipient review a document relevant to their work, which for media companies was often a draft article. In some of the emails, the document that the target was requested to view was not attached to the email. The failure to attach the file is likely a tactic used by the threat actor to see if the recipient responds and to only provide the file if they do. That could help to ensure that only the intended recipient is presented with the malicious file, reducing the risk of detection.
The file is often a PDF file, which if opened, only displays blurred text. The target is told that the text has been encrypted using an online service e.g. ProtonDrive. In order to view the document, the recipient is required to click a link. If the link is clicked, JavaScript code is fetched from the attacker’s server which fingerprints the system. If deemed to be of interest, they are directed to a URL that has a CAPTCHA check that must be passed to prevent bots from landing on the destination URL.
The landing page presents the user with a login prompt relevant to their email service, such as Gmail or ProtonMail, which may be pre-populated with the user’s email address so they are only required to enter their password and multifactor authentication code. If they are entered, the threat actor will obtain a session cookie that will allow them to access the account for some time before they are required to reauthenticate, allowing them to immediately access sensitive information in the target’s email account and associated online storage, such as Google Drive. The domains used for these campaigns did not remain operational for more than 30 days and they were registered with Hostinger, which rotates the IP addresses for the domains every 24 hours in an effort to prevent the sites being blocked by security solutions.
The targets of the campaign who spoke with the researchers chose to remain anonymous. They included Russian opposition figures in exile, NGO staff members in the US and Europe, funders, and media organizations. The researchers suggest that the campaign may have been conducted more broadly on other targets that are perceived threats to Russia. The researchers said a common theme among the targets was that they had extensive networks among sensitive communities and links to Russia, Ukraine, and Belarus.
Spear phishing campaigns can be highly effective as they are hyper-focused on small numbers of individuals and often are highly researched preceding initial contact to ensure that the right person is impersonated and a lure is used that the target is likely to respond to. Various measures are also used to reduce the chance of detection, including avoiding sending malicious content in the initial email, the use of CAPTCHA checks, and rotating IP addresses. Standard email security solutions may fail to detect these threats which means it is often down to the individuals to identify and avoid these threats. The consequences of failing to do so can be severe, especially for the targeted individuals in this campaign who could be subjected to physical harm or arrest and imprisonment.
Spear phishing is also used by cybercriminals in their campaigns, and while these attacks are typically financially motivated, they can cause significant harm to businesses. Similar tactics are used and the campaigns can be highly effective. To block spear phishing and other sophisticated phishing attacks, businesses need to have advanced email security measures that include email sandboxing and machine learning algorithms to identify potentially malicious emails, since standard checks of the sender’s reputation, embedded URLs, and malware scans are unlikely to identify anything suspicious. This is an area where TitanHQ can help. Give the team a call to find out more about protecting against advanced phishing and malware threats.
by Jennifer Marsh | Aug 19, 2024 | Uncategorized |
The latest figures from Microsoft indicate that in 2024, around 1 million businesses worldwide are using Microsoft 365, and in the United States alone there are around 1 million users of its Office suite. That makes Microsoft 365 a big target for cybercriminals, and phishing is the main way that M365 users are targeted. Microsoft includes cybersecurity protections for its customers that can block phishing emails and malware, and those protections do a reasonable job of blocking malicious emails; however, threats do bypass defenses and reach end users, which is why many businesses choose to augment Microsoft’s protections with third-party anti-phishing and anti-malware solutions, and now there is another good reason to bolster protection.
Recent research has uncovered a flaw in Microsoft’s anti-phishing measures that allows cybercriminals to bypass its email safety alerts. Microsoft’s First Contact Safety Tip generates these warnings when a user receives an email from an unfamiliar email address to warn them that the email may be malicious. The email will include the message “You don’t often get emails from xxx@xxx.com. Learn why this is important.” That message warns the user to take extra care and if it is not shown in the email the user may assume that the message is legitimate.
That warning message is added to the body of the HTML email and the problem with that approach is it is possible to manipulate the message by embedding Cascading Style Sheets (CSS), which is what researchers at Certitude discovered. They demonstrated that by manipulating the CSS within the HTML of the email, they were able to hide that warning, They did that by hiding the anchor tags (<a>) so the link is not displayed, changing the font color to white, and forcing the email to have a white background, ensuring that the text is not displayed since it is also in white. While the warning is still included in the email this trick renders it invisible. They also showed that it is possible to spoof Microsoft’s encrypted and signed icons to make the email appear secure.
Microsoft has confirmed that the finding is valid but has chosen not to address the problem at this time. Microsoft has instead marked the issue for potential resolution through future product updates but there have been no known cases of this tactic being used in the wild and the issue was deemed to be sufficiently severe to qualify for immediate servicing.
This issue serves as a reminder about M365 cybersecurity. Microsoft produces some excellent products that are invaluable to businesses, but Microsoft is not a cybersecurity vendor and while protections have been added, they can be circumvented. Microsoft 365’s EOP and Defender solutions do a good job at blocking most threats, but malicious emails do get through to inboxes where they can be opened by end users. The Microsoft 365 spam filter only provides an average level of protection against email threats.
TitanHQ has developed cybersecurity solutions to address M365 security gaps and provide greater protection for Microsoft 365 users through the SpamTitan spam filter for M365 and PhishTitan anti-phishing solution, both of which integrate seamlessly with Microsoft 365 and add important extra layers of protection against phishing, scam emails, and malware.
The engine that powers the SpamTItan and PhishTitan solutions has been independently tested and confirmed to provide superior protection through advanced features designed to catch more malicious emails. Those measures include a powerful next-generation email sandbox for protecting against advanced email attacks. When emails pass initial checks and scans using twin antivirus engines, they are sent to the sandbox for deep inspection, which allows malware to be identified from its behavior rather than a signature. These solutions include AI and machine learning protection, where malicious emails can be identified based on how they deviate from the normal emails received by a business, improving protection against zero-day threats – phishing and business email compromise emails that have not been seen before.
The PhishTitan solution has been developed specifically for Microsoft 365 to provide unmatched protection against phishing threats. PhishTitan displays banner notifications in emails to warn end users about suspicious content, which will provide protection should Microsoft’s First Contact Safety Tip be hidden. Links in emails are rewritten to display their true destination, and the solution makes it quick and easy for security teams to remediate phishing threats throughout the entire email system.
The engine that powers these solutions has recently been shown to beat leading email security solutions such as Mimecast for catch rate, malware catch rate, and has far lower false positives. In the June Virus Bulletin Test, TitanHQ had a 99.99% phishing catch rate, a spam catch rate of 99.98%, a malware catch rate of 100%, and zero false positives. PhishTitan catches 20 unique and sophisticated threats per 80,000 emails received that Microsoft 365 misses. Give TitanHQ a call today to find out more about these solutions and how adding extra layers of protection can strengthen your business’s security posture.
by Jennifer Marsh | Aug 15, 2024 | Phishing & Email Spam, Security Awareness |
Business Email Compromise (BEC) has long been one of the costliest types of cybercrime. According to the latest data from the Federal Bureau of Investigation (FBI) Internet Crime Compliant Center (IC3), almost 21,500 complaints were received about BEC attacks in 2023 resulting in adjusted losses of more than $2.9 billion. Between October 2013 and December 202, more than $50 billion was lost to BEC scams domestically and internationally.
What is Business Email Compromise?
BEC, also known as email account compromise (EAC), is a sophisticated scam that involves sending emails to individuals that appear to have come from a trusted source and making a legitimate-sounding request, which is typically a change to bank account details for an upcoming payment or payment of a fake invoice.
One such scam targets homebuyers, with the attacker impersonating the title company and sending details for a wire transfer for a down payment for a house purchase. Businesses are commonly targeted and asked to wire money for an upcoming payment to a different bank account. While the scammer is usually based overseas, the bank account may be at a bank in the victim’s home country. When the funds are transferred by the victim they are immediately transferred overseas or withdrawn, making it difficult for the funds to be recovered.
BEC attacks often start with phishing emails. The scammers use phishing to gain access to an employee’s email account, then the account is used to send phishing emails internally. The goal is to compromise the account of an executive such as the CEO or CFO. That account can then be used for the BEC part of the scam. Alternatively, vendors are targeted, such as construction companies, and their accounts are used for BEC attacks on their customers.
Once a suitable email account has been compromised, the scammers search through previous emails in the account to find potential targets – the company’s customers in the case of a vendor account or individuals responsible for making wire transfers in the case of a CEO’s account. The attackers study previous communications between individuals to learn the writing style of the account holder, and then craft their messages impersonating the genuine account owner. AI tools may also be used for this part of the scam or even researching targets. Alternatively, email accounts and websites may be spoofed, using slight variations of legitimate email addresses and domains. The information needed to conduct the scam may be gleaned from public sources or stolen via malware infections.
From here, a single request may be sent or a conversation may ensue over several emails to build trust before the request is made. Considerable time and effort is put into these scams because the effort is worth it for the scammers. The losses to these scams can be huge. Fraudulent wire transfers are often for tens of thousands of dollars or more, and with two recent scams, the losses have been immense.
Tens of Millions Fraudulently Obtained in BEC Scams
INTERPOL recently reported that it had successfully recovered more than $40 million stolen in a single BEC attack. The scammers targeted a commodities firm in Singapore, impersonating one of the company’s suppliers. In July, an email was received that had apparently been sent by the supplier requesting a pending payment be sent to a new bank account, in this case, the account was based in Timor Leste. In this scam, the email was sent from an account that differed slightly from the supplier’s legitimate email address. That difference was not identified and the bank account details were changed. A payment of $42.3 million was made to the account, and the transfer was only determined to be fraudulent when the supplier queried why the payment had not been received. INTERPOL was able to assist with the recovery of $39 million, and seven arrests were made which also involved the recovery of a further $2 million.
There has since been an even bigger scam and the victim was not so fortunate. The chemical manufacturing company Orion reported falling victim to a BEC attack that resulted in a $60 million loss. The Luxembourg firm told the U.S. Securities and Exchange Commission (SEC) that a non-executive employee was tricked into transferring the funds to multiple third-party accounts. So far, that loss has not been recovered.
How to Reduce Risk And Defeat BEC Attacks
Defending against BEC attacks can be a challenge, as legitimate email accounts are often used and the scammers are expert impersonators. The use of AI tools makes these scams even more difficult to identify. Defending against BEC attacks requires a defense-in-depth approach to prevent malicious emails from being delivered and prepare the workforce by improving awareness of the threats.
Security awareness training is vital. All members of the workforce should receive training and be made aware of BEC scams (and other cybersecurity threats). Training should cover the basics of these scams, such as why they are conducted and the attackers’ aims, as well as the red flags to look for. Phishing simulations can be highly beneficial, as BEC scams can be simulated to put training to the test and give individual practice at identifying these scams. TitanHQ’s SafeTitan platform includes BEC training material and a phishing simulator and makes it easy for businesses to improve their human defenses against BEC attacks.
Policies and procedures should be developed and implemented to reduce risk. For instance, it should be company policy for any requested change to banking credentials to be reviewed by a supervisor, and for any requested bank account changes by vendors to require verification by phone, using previously verified contact information.
It is vital to implement technical security measures to prevent email accounts from being compromised, malware from being installed, and to identify and block BEC emails. Traditional anti-spam software often fails to detect these sophisticated threats. A standard anti-spam appliance will perform a range of checks on the sender’s reputation and may be able to detect and block spoofed emails, but generally not emails sent from legitimate compromised accounts. Traditional anti-spam and antivirus solutions can detect known malware, but not novel malware threats.
What is needed is a next-generation hosted anti-spam service with machine learning and AI capabilities that can learn about the standard emails sent and received by a company or individual and determine when emails deviate from the norm and flag them as suspicious. AI-based protection is needed to defeat cybercriminals ‘ use of AI tools. The spam filtering service should also include email sandboxing in addition to standard anti-virus protection to identify and block novel malware threats, to prevent the malware infections that are used to gather information to support BEC attacks. SpamTitan from TitanHQ has all these features and more, with recent independent tests confirming the solution provides exceptional protection against phishing, spam, and sophisticated threats such as BEC attacks.
The most important thing to do is to take proactive steps to improve your defenses. Doing nothing could see your business featured in the next set of FBI statistics. Give the TitanHQ team a call today to discuss the best defenses for your business and find out more about how TitanHQ can help block BEC attacks and other cyber threats.
by Jennifer Marsh | Jul 31, 2024 | Network Security |
Each year, IBM conducts a study of data breaches to determine how much these incidents are costing businesses, the main factors that contribute to that cost, and how attackers are gaining access to their victims’ networks. Aside from 2020, data breach costs have continued to increase annually, and this year is no exception. The average cost of a data breach has risen from $3.86 million in 2018 to $4.88 million in 2024 and has increased by 10% since last year. The highest costs were incurred at critical infrastructure entities, especially healthcare organizations. Breaches at the latter were the costliest at an average of $9.77 million per incident.
The report is based on 3,556 interviews with individuals at 604 organizations who had knowledge about data breaches at their respective organizations. The data breaches included in the report involved between 2,100 and 113,000 compromised records and occurred between March 2023 and February 2024. The calculations include direct costs such as the breach response, ransom paid, forensic analysis, and regulatory fines, as well as indirect expenses such as in-house investigations, loss of business, and loss of customers.
This year’s Cost of a Data Breach Report revealed the high cost of breaches stemming from phishing, business email compromise, social engineering, and stolen credentials, which are the costliest incidents to resolve. Breaches stemming from stolen credentials and phishing were the costliest root cause, as was the case in 2023. Compromised credentials were the leading attack vector and were behind 16% of breaches, with phishing the next most common behind 15% of breaches. In terms of cost, phishing attacks cost an average of $4.88 million and compromised credentials cost $4.81 million. Business email compromise attacks were also costly at an average of $4.88 million with social engineering incidents costing an average of $4.77 million.
The report dives into the factors that contribute to the cost of a breach and the main areas where businesses have been able to reduce costs. The main factors that contributed to the cost of a breach were security system complexity, a security skills shortage, and third-party breaches, which are difficult things to address. Businesses have been able to reduce breach costs by implementing a number of measures, and the two biggest factors were employee training and AI/machine learning insights, with one constant identified being the use of AI and automation in security.
Employee training was determined to reduce the average breach cost by $258,629, with the most important aspect of training related to detecting and stopping phishing attacks. If a business is targeted in a phishing campaign, it may not be possible to prevent all employees from being fooled by the campaign, but through regular training and phishing simulations, the severity of the incident can be greatly reduced. For instance, a recent phishing attack on a U.S. healthcare organization resulted in more than 50 email accounts being compromised. More effective training could have prevented many of those employees from being tricked, greatly reducing the severity of the attack and the cost of remediation.
AI and machine learning insights were determined to reduce the average breach cost by $258,538, a close second in terms of cost reduction. Cybercriminals are leveraging AI in their attacks, especially for phishing and social engineering attacks. Network defenders need to leverage AI and machine learning tools to help them defend against these attacks and identify phishing, social engineering, and BEC threats, which are becoming much harder for humans to spot. Automation is key, especially due to the cybersecurity skills shortage – one of the leading factors that increases breach costs. Network defenders are overworked, and automation is key to reducing their workload, especially since it is difficult to find and retain skilled cybersecurity staff.
At TitanHQ, we understand the importance of staff training, and the benefits of AI, machine learning, and automation and offer businesses an easy way to implement these and better protect themselves from cyberattacks, remediate incidents quickly and efficiently, and ensure that their workforce is well trained and aware of cyber threats and how to avoid them. Security awareness training is provided through the SafeTitan platform, which includes an extensive library of engaging training content to teach security best practices, raise awareness of cyber threats, and teach employees how to recognize and avoid threats including phishing, social engineering, and business email compromise.
The content is constantly refreshed to account for changing work practices, technology, and the latest tactics, techniques, and procedures being used by cybercriminals. The phishing simulator includes hundreds of templates taken from real-world phishing attempts to reinforce training and identify employees who fall for phishing attempts. It is quick and easy to create training courses and phishing simulations, and importantly, to automate them to run continuously throughout the year. The platform also automatically delivers training modules to employees in response to mistakes such as phishing simulation failures, to ensure training is delivered in real-time when it is needed the most and likely to have the greatest impact.
TitanHQ offers two cutting-edge products to protect against email-based attacks, especially phishing and social engineering attempts. SpamTitan is a cloud-based anti-spam service (or can be provided as a gateway spam filter) that incorporates exceptional malware protection, email sandboxing, AI, and machine learning algorithms to identify and quarantine sophisticated threats, including novel threats that have not been seen before. In recent independent tests, the machine learning algorithms and other threat detection features achieved a detection rate of over 99.99%.
PhishTitan incorporates the same AI and machine learning capabilities to identify and block more threats in Office 365 environments. PhishTitan layers extra protection on top of Microsoft 365’s EOP and Defender provides best-in-class phishing protection. PhishTitan is also a remediation solution for automating the response to phishing threats to reduce the burden on IT staff, including instant inbox threat removal of emails containing malicious URLs and tenant-wide remediation with robust cross-tenant features for detection and response.
With these solutions, businesses can improve protection, prevent data breaches, and greatly reduce costs while easing the burden on their IT staff. They are also easy to implement and use, as we understand that IT staff don’t need any more management headaches. For more information, give the TitanHQ team a call to discuss your requirements, find out more about the products, and arrange a product demonstration. All three products are also available in a free trial to allow you to put them to the test and see the difference they make.
by Jennifer Marsh | Jul 31, 2024 | Phishing & Email Spam |
A massive phishing campaign that involved around 3 million emails a day was made possible due to a misconfiguration in Proofpoint’s email servers. The vulnerability was exploited to get the emails DomainKeys Identified Mail (DKIM) signed and approved by SPF, thereby ensuring the emails were delivered to inboxes.
Researchers at Guardio identified the campaign, which ran from January 2024 to June 2024 and at its peak involved sending around 14 million emails a day. The purpose of the campaign was to steal credit card numbers and set up regular credit card payments. The emails impersonated well-known brands such as Nike, Disney, Coca-Cola, and IBM. As is common in phishing attempts, the headers of the emails were spoofed to make it appear that the email had been sent by a genuine company. The majority of spam filters would be able to detect this spoofing and block the emails because they use Sender Policy Framework (SPF) and DKIM, specifically to detect and prevent spoofing.
Emails must be sent from approved servers to pass SPF checks and they must be authenticated using the DKIM encryption key for the domain. With DKIM, public-key cryptography is used to sign an email with a private key when it leaves the sender’s server, and the recipient server uses the public key to verify the source of the message. If the from filed matches the DKIM check is passed and the email is determined to be authentic and will be delivered. If not, the email will identified as spam and will be blocked. In this campaign the emails were all properly signed and authenticated, ensuring that they would be delivered.
For an email that impersonated Nike, a spoofed email address would be used with the nike.com domain, which thanks to passing the SPF and DKIM checks, would be verified by the recipient as having been authenticated. The recipient may be fooled that the email has come from the genuine company domain, and since the emails themselves contained that company’s branding and provided a plausible reason for taking action, the user may click the link in the email.
As with most phishing emails, there is urgency. Action must be taken quickly to avoid negative consequences, such as an impending charge, notification about the closure of an account, or another pressing matter. If the link is clicked, the user will be directed to a phishing site that also spoofs the brand and they are asked to provide their credit card details. Alternatively, they are offered a too-good-to-be-true offer, and by paying they also enroll in an ongoing subscription involving sizeable monthly charges.
The way that the attackers got around the checks was to send the emails from an SMTP server on a virtual server under their control and to route them through a genuine Office 365 account on an Online Exchange server, then through a domain-specific Proofpoint server which sent the email on to the intended recipient. Since the Proofpoint customers being spoofed had authorized the Proofpoint service to send emails on their behalf as an allowed email sender, the attackers only had to find a way to send spoofed emails through the Proofpoint relay. Due to a misconfiguration that allowed Microsoft Office 365 accounts to easily interact with its relay servers, they were able to do just that, pass SPF and DKIM checks, and make their fake emails appear to be clean.
They obtained the MX record for the company being spoofed by querying the domain’s public DNS, then routed the email through the correct Proofpoint host that is used to process email for that domain. Since the Proofpoint server was tricked into believing that the emails had come from the genuine domains of its customers – such as Nike and Disney – the emails were then forwarded to the intended recipients rather than being quarantined.
Spammers are constantly developing new methods of defeating the best email security solutions and while email security products can usually block spam and malicious emails, some will be delivered to recipients. This is why it is important to have layered defenses in place to protect against all phases of the attack. For instance, in this attack, spam filters were bypassed, but other measures could detect and block this attack. For instance, a web filter can be used to prevent a user from visiting a phishing website linked in an email, and security awareness training should be conducted to teach employees how to identify the signs of phishing, to check the domain of any website linked in an email, and to also check the domain when they arrive on any website.
by Jennifer Marsh | Jul 29, 2024 | Phishing & Email Spam |
Businesses that rely on Microsoft Defender for detecting malware and phishing emails may not be as well protected as they think. While Defender performs a reasonable job at blocking malware, spam, and phishing emails, it lacks the high detection levels of many third-party anti-phishing solutions.
Take malware for example. A study conducted in 2022 by AV-Comparatives found Defender only had a 60.3% offline detection rate. Fast forward to Q2, 2024, and TitanHQ’s email security suite was put to the test alongside 12 other email security solutions by Virus Bulletin. In the independent tests, TitanHQ had a malware catch rate of 100%.
In the same round of testing, TitanHQ’s spam filter for Office 365 and the email security suite had a spam catch rate of over 99.98%, a phishing email catch rate of 99.99%, and was given an overall final score of 99.984, the second highest in the tests. It is possible to configure an email solution to provide maximum protection; however, that will be at the expense of an elevated number of false positives – genuine emails that are inadvertently marked as potentially suspicious and are quarantined until they are released by an administrator. In the tests, TitanHQ had a 0.00% false positive rate, with no genuine emails misclassified.
Another issue with Microsoft Defender is the exception list, which contains locations such as files, folders, and processes that are never scanned. These are used to ensure that legitimate apps are not scanned, to prevent them from being misclassified as malware. The problem is that the exception list lacks security protections, which means it can be accessed internally by all users. Should a device be compromised, a threat actor could access the exceptions list, identify folders and files that are not scanned, and use those locations to hide malware.
Given the increasingly dangerous threat environment and the high costs of a cyberattack and data breach, businesses need to ensure they are well-defended, which is why many businesses are choosing to protect their Microsoft 365 environments with TitanHQ’s PhishTitan anti-phishing solution.
PhishTitan is a cloud-based, AI-driven solution for Microsoft 365 that integrates seamlessly into M365 to increase protection from sophisticated phishing attacks. Rather than replacing Microsoft’s EOP and Defender protections, PhishTitan augments them and adds next-generation phishing protection, not only ensuring that more threats are blocked but also giving users easy-to-use remediation capabilities.
PhishTitan adds advanced threat detection capabilities through machine learning and LLM to identify the zero-day and emerging threats that are missed by Defender. PhishTitan provides real-time protection against phishing links in emails in addition to checks performed when the email is received. URLs are rewritten for Link Lock protection with all links reassessed at the point a user clicks to ensure that URLs that have been made malicious after delivery are detected and blocked. If the link is detected as malicious, access to that URL will be prevented.
PhishTitan also adds banner notifications to emails to alert users to unsafe content and emails from external sources, and the auto-remediation feature allows all threats to be instantly removed from the entire mail system, with robust cross-tenant features for detection and response for MSPs.
PhishTitan has also been developed to be quick to set up and configure. There is no need to change MX records, setup typically takes less than 10 minutes, and the solution is incredibly easy to manage. Why put up with inferior threat detection and complex interfaces, when you can improve the Office 365 phishing protection with an easy-to-use anti-phishing solution
Don’t take our word for it though. Take advantage of the free trial of PhishTitan to see for yourself. Product demonstrations can also be arranged on request.
by Jennifer Marsh | Jul 26, 2024 | Phishing & Email Spam |
CrowdStrike has confirmed that a significant proportion of Windows devices that were rendered inoperable following a faulty update last Friday have now been restored to full functionality; however, businesses are still facing disruption and many scams have been identified by cybercriminals looking to take advantage.
One of those scams involves a fake recovery manual that is being pushed in phishing emails. The emails claim to provide a Recovery Tool that fixes the out-of-bounds memory read triggered by the update that caused Windows devices to crash and display the blue screen of death. The phishing emails include a document attachment named “New_Recovery_Tool_to_help_with_CrowdStrike_issue_impacting_Windows. docm.” The document is a copy of a Microsoft support bulletin, which claims that a new Microsoft Recovery Tool has been developed that automates recovery by deleting the CrowdStrike driver that is causing the crash. The user is prompted to enable content; however, doing so will allow a macro to run, which will download a malicious DLL, which launches the Daolpu stealer – an information stealer that collects and exfiltrates credentials, login information, and cookies stored in Chrome and Firefox.
Another campaign has been identified that capitalizes on the defective Falcon Sensor update. The spear phishing campaign targeted German firms and attempts to distribute a fake CrowdStrike Crash Reporter installer via a website that spoofs a legitimate German company. The website was registered a day after the CrowdStrike disruptions started. If the user attempts to download the installer by clicking the download button in the email, a ZIP archive will be delivered that includes a malicious InnoSetup installer. If executed, the user is shown a fake CrowdStrike branded installer. The installer is password-protected to prevent analysis and the final payload could not be determined.
Another campaign attempts to distribute Lumma information-stealing malware. The campaign uses the domain, crowdstrike-office365[.]com, and tricks the recipient into downloading a fake recovery tool to deal with the boot loop that prevents Windows devices from booting up. If the downloaded file is executed, it delivers a malware loader, which will, in turn, deliver the Lumma infostealer.
These are just three campaigns that use the CrowdStrike outage to deliver malware, all of which use email as the way to make contact with individuals affected by the outage. Many other campaigns are being conducted and a large number of CrowdStrike-themed domains have been registered since the problems started. Other malicious domains used in campaigns include the following, all of which should be blocked.
crowdstrike-helpdesk.com
crowdstrike.black
crowdstrikefix.zip
crowdstrikebluescreen.com
crashstrike.com
fix-crowdstrike-bsod.com
crowdstrike-falcon.online
crowdstrike-bsod.com
crowdstrikedoomsday.com
crowdstrikedown.site
crowdstrikefix.com
isitcrowdstrike.com
crowdstriketoken.com
crowdstrike0day.com
crowdstrikeoutage.com
These scams are likely to continue for some time, so it is important to remind employees of the high risk of malicious emails and warn them to exercise extreme caution with any emails received. Employees should be told to report any suspicious emails to their security team.
TitanHQ offers a range of cybersecurity solutions to block phishing and malware distribution campaigns, all of which are quick and easy to implement and can protect you in a matter of minutes. They include the WebTitan web filter for blocking access to known malicious websites, such as those detailed in this email; the PhishTitan anti-phishing solution for Office 365, and the SpamTitan corporate email filter for blocking phishing emails. The latter incorporates email sandboxing for blocking novel and obfuscated malware threats. TitanHQ also provides a comprehensive security awareness training platform and phishing simulator for improving your human defenses by raising awareness of cyber threats and providing timely training content on the latest tactics used by cybercriminals in targeted attacks on employees.
Give the TitanHQ team a call today for further information on improving your defenses, or take advantage of the free trial available with all TitanHQ products to get immediate protection.
by Jennifer Marsh | Jul 25, 2024 | Industry News |
TitanHQ has announced a new strategic alliance with ATS Network Management, a provider of network management solutions, monitoring, security, and performance management services across South Africa and the African continent. Under the alliance, ATS Network Management will become a value-added distributor and will incorporate TitanHQ’s portfolio of cybersecurity and compliance solutions into its service stack, packaging the solutions with other tools and services to provide a more comprehensive range of services to its clients and ensuring they are shielded from constantly evolving cyber threats.
ATS Network Management will now be able to offer its clients email security and phishing prevention and remediation through TitanHQ’s PhishTitan solution for Office 365, as well as email filtering to remove malware, phishing, and unwanted emails from email systems and protect against malicious links with TitanHQ’s SpamTitan solution. SpamTitan is an award-winning email security solution with email sandboxing that protects against the full range of email threats. Independent tests have recently confirmed that SpamTitan has a 99.99% phishing catch rate and 100% malware catch rate, and it is one of the best-loved MSP spam filtering solutions.
To protect against web-borne threats and control access to the Internet, ATS Network Management will be providing DNS filtering using WebTitan. WebTitan blocks access to known malicious sites, prevents user-specified file types from being downloaded from the internet to protect against malware and control shadow IT, and restricts access to categories of web pages to improve employee productivity. To protect against the interception of sensitive email data in transit, ATS Network Management will be using EncryptTitan, and email archiving services will be offered through ArcTitan for compliance purposes.
Due to the number of threats targeting employees directly, it is vital for businesses to raise awareness of cyber threats and teach employees cybersecurity best practices. This is an area where many businesses turn to their MSPs for assistance. ATS Network Management will be offering its clients comprehensive security awareness training through SafeTitan, TitanHQ’s security awareness training platform. In addition to allowing businesses to create and automate tailored training courses with engaging content, the platform includes a phishing simulator to allow them to automate phishing simulations to identify knowledge gaps and provide targeted training where it is needed.
The partnership will help TitanHQ expand its footprint in Africa while ensuring that African businesses can benefit from TitanHQ’s cutting-edge security solutions and defend their businesses from increasingly sophisticated cyber threats.
by Jennifer Marsh | Jul 22, 2024 | Phishing & Email Spam |
On July 19, 2024, Windows workstations and servers were disabled as a result of a bug in a software update for CrowdStrike Falcon Sensor. When the update was installed on Windows devices, it caused them to show the Blue Screen of Death or get stuck in a boot loop, rendering the devices unusable. Microsoft revealed that its telemetry showed 8.5 million Windows devices had been affected in around 78 minutes.
CrowdStrike Falcon platform is a cybersecurity solution that incorporates anti-virus protection, endpoint detection and response, threat intelligence, threat hunting, and security hygiene, and it is used by many large businesses around the world, including around half of Fortune 500 firms. The disruption caused by the update has been colossal. Airlines had to ground flights, airports were unable to check people in, healthcare providers were unable to access electronic patient records and had to cancel appointments and surgeries, financial institutions faced major disruption, and some media companies were unable to broadcast live television for hours. Even organizations that did not use the Falcon product were adversely affected if any of their vendors used the product. The incident has been called the worst-ever IT outage, with huge financial implications.
It did not take long for cybercriminals to take advantage of the chaos. Within hours, cybercriminals were registering fake websites impersonating CrowdStrike offering help fixing the problem, and domains were registered and used in phishing campaigns promising a rapid resolution of the problem. Given the huge financial impact of suddenly not having access to any Windows devices, there was a pressing need to get a rapid resolution but the fixes being touted by cybercriminals involved downloading fake updates and hotfixes that installed malware.
Those fake updates are being used to deliver a range of different malware types including malware loaders, remote access Trojans, data wipers, and information stealers, while the phishing campaigns direct users to websites where they are prompted to enter their credentials, which are captured and used to access accounts. Cybercriminals have been posing as tech specialists and independent researchers and have been using deepfake videos and voice calls to get users to unwittingly grant them access to their devices, disclose their passwords, or divulge other sensitive codes.
CrowdStrike has issued a fix and provided instructions for resolving the issue, but those instructions require each affected device to be manually fixed. The fix was rolled out rapidly, but CrowdStrike CEO George Kurtz said it will likely take some time for a full recovery for all affected users, creating a sizeable window of opportunity for threat actors. Due to the surge in criminal activity related to the outage, everyone should remain vigilant and verify the authenticity of any communications, including emails, text messages, and telephone calls, and only rely on trusted sources for guidance. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has reminded all organizations of the importance of having robust cybersecurity measures in place to protect their users, assets, and data, and to remind all employees to avoid opening suspicious emails or clicking on unverified links in emails.
It is important to have multiple layers of security protection to identify, detect, and avoid these attacks, including AI-driven phishing protection, web filtering to block access to malicious websites, anti-virus software to detect and neutralize malware, and security awareness training for employees. TitanHQ can help to secure your business in all of these areas and offers a cloud-based spam filtering service (SpamTitan) which includes email sandboxing and email antivirus filter, phishing protection for Office 365 (PhishTitan), and the SafeTitan security awareness training and phishing simulator.
by Jennifer Marsh | Jul 1, 2024 | Phishing & Email Spam |
Phishing attacks and business email compromise scams are leading causes of losses to cybercrime and attacks have increased in 2024. According to the Federal Bureau of Investigation, phishing is the leading cause of complaints to its Internet Crime Complaint Center and business email compromise currently ranks second out of all tracked forms of cybercrime in terms of total losses.
Over the coming days and weeks, there are several events that cybercriminals take advantage of in their attacks and scams. The UEFA European Football Championship is currently taking place in Germany and thousands of individual phishing campaigns have been detected so far that are piggybacking on the popularity of the championship in Europe and beyond.
Cybercriminals often take advantage of sporting events and commonly use lures related to tickets, which usually sell out months before the first football is kicked and this year is no exception. Now that the tournament is underway and broadcasters and other legitimate entities are running competitions offering free tickets to the finals, scammers are doing the same and are using email and social media networks to advertise their scams. These campaigns use realistic websites that are almost identical to the brands they spoof and attempt to steal sensitive information such as credit card numbers and login credentials.
Many of the phishing attacks and scams impersonate businesses associated with the tournament. These include accommodation providers, airlines and travel companies, and others. The Wimbledon tennis tournament is underway, which will be shortly followed by another major sporting event in Paris – The 2024 Olympics. The latter has a huge global audience and there is a high risk of cyber threat activity using Olympics-themed lures. Cybercriminals are impersonating event organizations, sponsors, ticketing systems, and travel companies. Many cyber espionage groups and nation-state actors are likely to target the Olympics, in addition to financially motivated threat actors.
This week, there is a major celebration in the United States on July 4. Independence Day is a very active time for a host of malicious actors who conduct scams related to the celebrations, including holiday-themed texts and emails, fake giveaways and vouchers, and Independence Day event ticket scams. Being a major holiday in the United States when staffing levels are greatly reduced, it is a time when many ransomware groups choose to strike as their activities are less likely to be identified.
Also on July 4, 2024, a major event is taking place across the Atlantic in the UK. The UK general election will be taking place to decide the next government and scammers are already taking advantage and are using deepfake scams and malicious websites used to steal information and influence voters. It will be a similar story in the United States in the run-up to the November Presidential election.
With so many events taking place, it is vital for everyone to be on their guard and be constantly alert to the threat of scams, phishing, and malware attacks. Due to the elevated threat from phishing, businesses should step up their security awareness training to raise awareness of cyber threats and teach cybersecurity best practices. It is a good idea to use these events in your internal phishing simulations to identify any knowledge gaps and provide immediate training to any individual who fails a phishing simulation.
Security awareness training is made simple with SafeTitan from TitanHQ. SafeTitan is a comprehensive security awareness training platform that teaches security best practices to eradicate risky behaviors, raises awareness of the threat from phishing and malware, teaches the red flags to look for in emails and texts, and what to do if a potential threat is found. The phishing simulator can be used to automate internal phishing simulations to test awareness of threats and how employees are applying their training.
It is also a good time for businesses to bolster email security with an advanced email security solution. SpamTitan from TitanHQ is an advanced email security solution that uses predictive techniques to identify malicious emails, including AI and machine learning to block phishing threats and email sandboxing to block malware. SpamTitan integrates seamlessly with Microsoft 365 and is consistently rated as one of the best spam filters for Outlook, improving the native defenses that Microsoft offers. TitanHQ also offers a host of cybersecurity solutions for managed services providers, including advanced phishing protection, to help them better protect their clients.
If you want to improve protection this summer against increasingly sophisticated cyberattacks and scams, give the TitanHQ team a call to find out more about improving your security posture.
by Jennifer Marsh | Jun 30, 2024 | Phishing & Email Spam |
Many malware infections start with a malicious email that contains a file attachment with a malicious script that downloads malware if executed. One response to a single email is all it takes to infect the user’s device with malware, which may be able to spread across the network or at least provide the threat actor with the foothold they need in the network for follow-on activities. There is a much worse scenario, however. Rather than a single user infecting the network with one malware variant, that single response to the malicious email results in multiple malware infections. One campaign has been identified that does just that. A malware cluster bomb is delivered that can infect the user’s device with up to 10 different malware variants.
The campaign was identified by researchers at KrakenLabs and has been attributed to a threat actor known as Unfurling Hemlock. The campaign is being conducted globally with at least 10 countries known to have been attacked, although most of the victims have so far been located in the United States. The campaign has been running since at least February 2024 and uses two methods to deliver the malware variants – malicious emails and malware loaders installed by other threat groups. The threat actor has already distributed hundreds of thousands of malicious files in the 5 months since the operation is believed to have commenced.
In the email campaign conducted by Unfurling Hemlock, the victim is tricked into downloading a file called WExtract.exe which contains nested cabinet files, each containing a different malware variant. If the file is executed, the malware is extracted in sequence, and each malware variant is executed in reverse order, starting with the last malware variant to be extracted. Each malware cluster bomb has between four and seven stages, with some of those stages delivering multiple malware variants.
The malware variants delivered vary but they consist of information stealers, backdoors, malware loaders, and botnets. Information stealers include Redline Stealer, Mystic Stealer, and RisePro, and malware loaders including Amadey and SmokeLoader. Other malware variants are used to disable security solutions such as Windows Defender, help with obfuscation and hiding malware payloads, gathering system information, and reporting on the status of the malware infections.
It is not clear how the threat actor is using these malware infections. They could be delivering malware for other threat actors and selling the access, using the malware to harvest credentials to sell on the darkweb, conducting their own attacks using whatever malware variant serves their purpose, or a combination of the three. What the attack does ensure is maximum flexibility, as there are high levels of redundancy to ensure that if some of the malware variants are detected, some are likely to remain.
The delivery of multiple malware variants means this campaign could be highly damaging, but it also increases the chance of detection. While antivirus software is a must and may detect some of the malware variants, others are likely to go undetected. The key to blocking attacks is to prevent the initial phishing emails from reaching end users and to provide training to the workforce to help with the identification and avoidance of these malicious emails.
Many email security solutions rely on antivirus engines to detect malware but cybercriminals are skilled at bypassing these signature-based defenses. TitanHQ’s SpamTitan anti-spam software, SpamTitan, uses dual antivirus engines as part of the initial checks but also email sandboxing for behavioral analysis. Suspicious emails are sent to the sandbox where files are unpacked and their behavior is analyzed in depth. The behavioral analysis identifies malicious actions, resulting in the messages being quarantined for further analysis by the security team. SpamTitan also includes AI and machine-learning algorithms to check how messages deviate from the emails typically received and can identify new threats that have previously not been seen. SpamTitan is a highly effective Microsoft 365 spam filter and can be provided as a gateway spam filter or a cloud-based anti-spam service.
End user training is an important extra layer of security that helps eradicate bad security practices and teaches employees how to recognize and avoid malicious emails. Should a malicious bypass email security defenses, trained employees will be more likely to recognize and report the threat to the security team. Training data from SafeTitan, TitanHQ’s security awareness training platform and phishing simulator, shows the training and phishing simulations can reduce susceptibility to email attacks by up to 80% when provided regularly throughout the year.
Give the TitanHQ sales team a call today for more information on these and other cybersecurity solutions to improve your defenses against the full range of cyber threats.
by Jennifer Marsh | Jun 29, 2024 | Industry News, Spam Software |
For the second consecutive quarter, TitanHQ’s SpamTitan and PhishTitan solutions earned the #2 spot in the VBSpam+ awards, with a 99.99% phishing catch rate. For more than 20 years, the Virus Bulletin information security portal has been conducting fully independent benchmarking tests of cybersecurity solutions, including email security, anti-malware, and anti-phishing solutions. In the phishing and malware tests, Virus Bulletin fired a barrage of threats and spam at security solutions, but it is not sufficient to just be able to block malware, phishing, and spam. Email security solutions need to be able to block those threats without also blocking genuine emails so Virus Bulletin also sent a range of genuine emails to the email security solutions to make sure they were not overblocking and preventing genuine messages from being delivered quickly.
SpamTitan is provided as a cloud spam filter or gateway spam filter and incorporates machine learning and AI-based detection and sandboxing technology for predictive and behavioral analysis to identify zero-day threats. PhishTitan is TitanHQ’s inline phishing protection solution for Microsoft 365, which improves the Microsoft 365 spam filter. For every 80,000 emails sent to Microsoft 365 accounts, PhishTitan catches 20 threats that Microsoft’s most advanced security offering misses (E5 premium). PhishTitan auto-remediates these phishing threats. The same anti-spam, anti-malware, and anti-phishing engine powers both SpamTitan and PhishTitan.
The technological superiority of these solutions was demonstrated in the Virus Bulletin tests. In the Virus Bulletin Q1,2024 benchmarking tests, SpamTitan & PhishTitan achieved an impressive second place in the round of testing with a 99.914% phishing catch rate with a 0.000% false positive rate and a malware catch rate of 99.511%. TitanHQ achieved an overall final score of 99.983%
In the Q2, 2024 benchmarking tests, Virus Bulletin assessed 12 leading email security solutions and TitanHQ performed even better, achieving a phishing catch rate of 99.990%, a malware catch rate of 100.000%, and a false positive rate of 0.000%, resulting in a second-place spot for the second consecutive quarter with an overall final score of 99.984%. TitanHQ was pipped to the top spot by just 0.004% and outperformed email security providers such as Sophos, FortiMail, Mimecast, N-able, SpamAssassin, and Zoho Mail. The test ensures that TitanHQ collects another VBSpam+ certification for Q2, 2024. The scores clearly demonstrate that TitanHQ provides powerful and effective anti-spam and anti-phishing solutions for businesses and Managed Service Providers which are capable of blocking ever-evolving cyber threats. The benchmarking tests cement TitanHQ’s position as a leader in the cybersecurity industry.
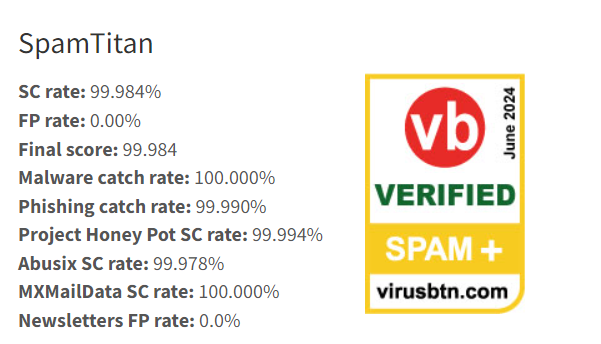
“This test reaffirms TitanHQ’s unrivaled prowess in spam and phishing protection—we stand as the first choice for combating phishing attempts and spam infiltrations,” said Ronan Kavanagh, CEO at TitanHQ. “Our customers need not settle for anything less. With TitanHQ solutions, they receive unparalleled defense against phishing and spam and experience minimal false positives.”
Ronan Kavanagh explained that the company is attracting an unprecedented number of new Managed Service Provider customers who have decided to make the switch from other solutions to TitanHQ, not only because of the impressive level of protection provided, but also the low management overhead, ease of use, and the MSP features of both SpamTitan and PhishTitan, which were developed from the ground up to meet the needs to MSPs. “Their resounding feedback echoes the sentiment: TitanHQ delivers immediate and substantial threat mitigation. These independent test results validate our ongoing efforts, ensuring our customers benefit from top-tier protection against phishing, spam, and viruses at a compelling value proposition.”
by Jennifer Marsh | Jun 29, 2024 | Phishing & Email Spam, Spam Advice |
Around 40% of businesses use Office 365 for email, which includes Exchange Online Protection (EOP) with standard licenses for blocking spam and other email threats. While EOP will block a substantial amount of unwanted spam emails and malicious emails, the level of protection provided falls well below what many businesses need as too many threats pass through undetected.
Businesses can opt for a more expensive Business Premium license to improve Microsoft’s spam filter for Office 365, as this license includes Defender for Office 365. Alternatively, businesses can pay for Defender as an add-on. While Defender improves the phishing detection rate, this security feature only adds a little extra protection to EOP, and many malicious emails still go undetected. The E5 license provides the greatest amount of protection but it is prohibitively expensive for many businesses, and even this license does not give you cutting-edge protection.
Fortunately, there is a way to improve Office 365 email filtering that will provide you with excellent protection against phishing, malware, spam, and other email threats without having to cover the cost of expensive licenses and add-ons. That solution is to use a third-party email security solution that augments the spam filter for Office 365 regardless of the license you have. Many businesses prefer to use a third-party solution rather than placing all of their trust in Microsoft – a company that has recently struggled with preventing hackers from compromising its own systems.
SpamTitan from TitanHQ is a cloud-based email security solution that integrates seamlessly with Office 365 to greatly increase protection against email threats such as phishing, business email compromise, malware, and data theft by insiders, and is easy to set up, configure, and manage.
There are several features of SpamTitan that are lacking in Microsoft’s security solutions. In addition to performing reputation checks and blocking known malicious email addresses and domains, SpamTitan uses predictive techniques for detecting spam and phishing emails, such as Bayesian analysis, machine learning, and heuristics. These features allow SpamTitan to detect and block zero-day phishing threats and business email compromise, which Microsoft struggles to detect and block.
SpamTitan performs extensive checks of embedded hyperlinks to combat phishing, including checks of Shortened URLs. Office 365 malware detection is greatly improved with dual antivirus engines for detecting known malware and email sandboxing. The sandboxing feature includes machine learning and behavioral analysis for the safe detonation of files in an isolated environment, and message sandboxing is vital for detecting and blocking the zero-day malware threats that EOP and Defender miss.
SpamTitan cloud-based email filtering is also an ideal choice for Managed Services Providers looking to provide their customers with more advanced email security, especially for small- and medium-sized clients unwilling to pay for E5 licenses. SpamTitan has been developed from the ground up to meet the needs of MSPs and manage email security with minimal management overhead.
TitanHQ can also MSPs additional protection against phishing with TitanHQ’s new anti-phishing solution, PhishTitan. PhishTitan uses a large language model (LLM) and AI to analyze emails to identify phishing attempts. The solution incorporates multiple curated feeds to detect malicious URLs linked in phishing emails, adds banners to emails from external sources to warn end users about potential threats, and adds post-delivery remediation across multiple tenants allowing phishing emails to be instantly removed from the email system with a single click.
The best way to find out more about the full capabilities of SpamTitan and PhishTitan and how they work is to call the TitanHQ team. A product demonstration can be arranged and you can take advantage of a free trial to see for yourself the difference these solutions make and how they can significantly improve threat detection with Office 365.
by Jennifer Marsh | Jun 28, 2024 | Phishing & Email Spam |
Two new malware distribution campaigns have been detected that deliver dangerous information-stealing malware, both targeting individuals looking to download free and pirated software.
Trojaninized Cisco Webex Meetings App Delivers Malware Loader and Information Stealer
Another malware distribution campaign has been identified that is using trojanized installers for free and pirated software to deploy a malware loader called Hijack Loader, which in turn delivers an information stealer. In the attacks, the victim was tricked into downloading a trojanized version of the Cisco Webex Meetings App, a video streaming app. The user downloaded a password-protected archive (RAR) file, which contained a file called setup.exe. When the victim executed the file, DLL sideloading was used to launch the HijackLoader, which was injected into a Windows binary.
HijackLoader connects with its command-and-control server and downloads another binary, an information stealer called Vidar Stealer. The malware bypasses User Account Control (UAC), escalates privileges, and adds an exception to the Windows Defender exclusion list. Vidar Stealer is used to steal credentials from browsers and deliver additional malware payloads, including a cryptocurrency miner. This campaign primarily targets organizations in Latin America and the Asia Pacific region.
Google Ads Used to Target Mac Users and Deliver Poseidon Malware
An information stealer called Poseidon is being distributed via malicious Google Ads that claim to provide the popular Arc web browser. The campaign targets Mac users and delivers a trojanized version of the Arc browser installer. If the installer is launched, the user gets the browser but is also infected with the malware.
According to an analysis from Malwarebytes, the new information stealer has similar features to the notorious Atomic Stealer, including a file grabber, crypto wallet extractor, and the ability to steal passwords from password managers such as Bitwarden and KeepassXC, passwords stored in browsers, and browser histories. The targeting of password managers makes this malware particularly dangerous, potentially allowing the theft of all passwords. The researchers believe the malware has been set up as a rival to Atomic Stealer
How to Protect Your Business
Protecting against malware requires a defense-in-depth approach to security, where several different security solutions provide multiple overlapping layers of protection. These security measures should include the following:
Antivirus software – Antivirus software is a must. The software will be able to detect malware when it is downloaded onto a device or is executed. The malware is identified by its signature, which means that a particular malware variant must be known and its signature must be present in the malware definition list used by that software. Antivirus software will not detect novel malware variants without behavioral analysis of files.
Web filter – One of the best defenses against malware distributed via the internet is a web filter. The web filter blocks downloads of malicious files by preventing downloads of executable files from the Internet, blocking access to known malicious websites, and limiting the sites that users can visit on their corporate-owned devices. The main advantage of a web filter is the threat is dealt with before any files are downloaded from the Internet.
Security awareness training – Users should be warned about the risks of downloading software from the Internet, be taught how to identify the signs of phishing and malicious emails, and be trained on security best practices. The latter should include carefully checking the domain of the website offering software and making sure it is the official website of the software vendor or a reputable software distributor.
Email security solution – Malware is often delivered via email, usually via a malicious script in an attached file or via a linked web page. An email security solution needs to have antivirus capabilities – signature-based detection and behavioral analysis in an email sandbox. The former will detect known malware variants and email sandboxing is used to detect novel malware variants. Your email security solutions should also include AI-based detection, which can identify malicious messages based on how they differ from standard messages received by your business and perform comparisons with previous malware distribution campaigns.
While TitanHQ does not provide antivirus software, TitanHQ can help with web filtering (WebTitan), email security (SpamTitan), phishing protection (PhishTitan), and security awareness training (SafeTitan). For more information on improving your defenses against malware and TitanHQ’s multi-award-winning cloud-based email security and internet security solutions for businesses and managed service providers, give the TitanHQ team a call today.
by Jennifer Marsh | Jun 27, 2024 | Industry News, Phishing & Email Spam, Security Awareness |
A phishing campaign targeting the Los Angeles Department of Public Health saw more than 50 employee email accounts compromised and the sensitive information of more than 200,000 individuals was exposed.
In this campaign, the threat actor impersonated a trustworthy sender and emailed a link that directed employees to a malicious website where email credentials were harvested. The website had been crafted to appear legitimate and requested they log in. When their credentials were entered, they were captured and used to access the employees’ email accounts. 53 employees fell for the scam. Their email accounts contained highly sensitive information that could be used for identity theft and fraud, including names, dates of birth, and Social Security numbers, as well as financial information and health insurance information. This campaign clearly demonstrates the damage that can be caused by phishing, and how a well-crafted campaign can fool many employees and result in a costly data breach.
While this phishing attack stands out due to the number of email accounts compromised, successful phishing attacks are common in healthcare. Healthcare employees are targeted via email, SMS, and other communication platforms, including over the phone. The Federal Bureau of Investigation and the Department of Health and Human Services recently issued a joint cybersecurity advisory about a campaign targeting IT helpdesk workers at healthcare organizations. Cybercriminals call IT helpdesks and impersonate employees to request password resets and enroll new devices to receive multifactor authentication codes. In this campaign, the attackers seek email credentials and then pivot to systems used for automated clearinghouse (ACH) payments to divert payments to their own accounts.
The Los Angeles Department of Public Health phishing attack serves as a reminder of the importance of conducting regular security awareness training. Employees need to be trained how to recognize phishing attempts. Through regular training, employees can be made aware of the red flags they need to look for in all communications and will be conditioned to be always on the lookout for threats and to report any potential threats to their security team. Healthcare employees who receive regular security awareness are less likely to be tricked by phishing scams. Training data from TitanHQ shows that organizations that conduct regular security awareness training with the SafeTitan security awareness training platform and phishing simulations using TitanHQ’s phishing simulator can reduce susceptibility to phishing scams by up to 80%.
The SafeTitan platform allows healthcare organizations to easily create and automate security awareness training programs and to tailor the training courses to different departments and users, ensuring that the training is relevant and focuses on the cyber threats that each user group is likely to encounter. The platform is modular, with each module taking no longer than 10 minutes to complete, making it easy for busy healthcare workers to fit the training into their workflows. The training content is engaging, fun, and enjoyable, and covers all threats and teaches cybersecurity best practices.
Phishing simulations can be easily conducted to test the effectiveness of training and identify employees who have not taken the training on board, allowing them to be provided with further training. The SafeTitan platform is the only security awareness training platform that delivers training in real-time in response to security mistakes, ensuring additional training is provided instantly at the moment when it is likely to have the greatest impact on changing behavior.
In addition to training, healthcare organizations must implement technical safeguards for HIPAA Security Rule compliance. TitanHQ offers a range of cloud-based security solutions for healthcare organizations to manage risks and achieve Security Rule compliance. These include SpamTitan anti-spam software which incorporates AI and machine learning algorithms to predict phishing attempts and dual antivirus engines and email sandboxing to combat malware. The WebTitan web filter protects against internet-based threats and can be used to block access to malicious and risky websites and block executable file downloads from the Internet to combat malware. Healthcare organizations that use Microsoft 365 can improve phishing protection with PhishTitan – a next-generation AI-based anti-phishing solution that offers unmatched protection against phishing and allows rapid remediation of phishing threats, preventing phishing attempts from compromising multiple email accounts.
All TitanHQ solutions are quick and easy to implement and use and can help healthcare organizations achieve and maintain HIPAA compliance, block more threats, and avoid costly data breaches. Contact TitanHQ today for more information about improving your security posture.
by Jennifer Marsh | Jun 26, 2024 | Website Filtering |
A malvertising campaign has been identified that targets users looking to download popular software such as Google Chrome and Microsoft Teams and delivers a backdoor malware called Oyster. The threat actor has registered lookalike domains that offer the software to download; however, the installer delivers the backdoor, with PowerShell used for persistence. After the malware is executed, the legitimate software is installed. Since the user gets the software they are expecting, they are unlikely to realize that their device has been infected.
The Oyster backdoor has been linked to the Russian threat group behind the infamous TrickBot Trojan. Once installed, the malware connects with its command-and-control server, gathers information about the host, and allows the threat actors to remotely execute code on the infected device. According to researchers at Rapid7 who identified the campaign, the threat actor has been observed delivering additional malware payloads on infected devices.
Malvertising is a common method of malware delivery that takes advantage of a lack of security awareness and attentiveness. Threat actors create adverts on legitimate ad networks for popular software solutions and pay to have their ads appear when users search for the software solutions they are impersonating. Just because an advert appears at the top of the search engine listings on Google or Bing it does not mean that the advert is legitimate. Clicking the link will direct the user to a site that is a carbon copy of the legitimate website that it spoofs, where they can download the software installer. These campaigns can be identified by the domain, which should be carefully checked to make sure it is the website of the official software provider.
Typosquatting is also commonly used, where threat actors register almost identical domains to the company they are impersonating. The domains usually have a transposed or missing letter. If the domain is not carefully checked, the user is unlikely to realize they are not on the official website. Threat actors use black hat search engine optimization techniques to get the websites to appear high up in the search engine listings.
By targeting software downloads, where the user is expecting to download an installer, the threat actor does not need to convince the user to execute the malicious file. If they fail to identify the scam before downloading the installer, their device is highly likely to be infected. Security awareness training should cover the methods used by threat actors to distribute malware over the Internet and should condition employees to always carefully check the domain to make sure it is the legitimate vendor’s website. Rather than develop a security awareness training program from scratch, businesses should consider using a vendor that can provide a comprehensive training platform that is constantly updated with new training content covering new attack methods and scams. A security awareness training program should run continuously, to build awareness, teach security best practices, and ensure that employees are constantly reminded of the importance of security.
In addition to training, technical measures should be implemented. A web filter should be used to prevent access to known malicious web pages and block downloads of executable files from the Internet, with policies implemented that require any software to be provided through or by the IT team. TitanHQ can help to improve your defenses against malware with a suite of cybersecurity solutions, including the SafeTitan security awareness training and phishing simulation platform, the WebTitan web filter to prevent access to malicious websites, SpamTitan email security with sandboxing to block malicious emails, and PhishTitan to improve phishing detection and mediation for businesses that use Microsoft 365.
For more information about these and other cybersecurity solutions from TitanHQ, give the sales team a call. All TitanHQ SaaS solutions are available on a free trial to allow you to test them in your own environment before making a purchase decision, with customer support provided throughout the trial.
by Jennifer Marsh | Jun 24, 2024 | Spam Software |
Email security solutions are used for blocking threats before they reach end users, including phishing and spear phishing emails, malware, spam, and other unwanted emails. Email security solutions have been an essential cybersecurity measure for decades and have been helping businesses to keep inboxes free of threats and to detect and block insider threats such as the theft of sensitive company data and personally identifiable information by employees.
One area where many email security solutions fail to perform well is the detection of malware. Email security solutions traditionally use anti-virus engines for detecting malware threats and they are constantly updated with new signatures when novel malware variants are detected. While these threat intelligence feeds ensure that email security solutions can detect known malware variants, there is a delay between a malware variant being detected and the signature being uploaded to the malware definition list. That delay may be a few minutes, hours, or days and cybercriminals exploit that window of opportunity.
While these signature-based defenses were sufficient for many decades, new malware variants are constantly being released with small changes that are sufficient to defeat signature-based detection methods. Cybercriminals are automating that process and are using large language models (LLMs) to accelerate the release of new malware variants.
Signature-based detection is still essential, but another feature is now required – one that can detect novel malware variants even if they have never been seen before. That feature is email sandboxing. An email sandbox is an isolated environment, often in the cloud, where emails are sent for deep analysis. When an email passes frontline checks and scans using anti-virus engines, they are sent to the sandbox for deep inspection.
The sandbox is designed to appear to be a genuine endpoint to trick the malware that it has reached its intended destination. The malware executes and performs its initial routines, such as connecting to its command-and-control center and reporting system information. Those actions are detected, the malware is quarantined, and the security team is alerted about the attempted attack. If the checks are passed, the email is released and delivered to the intended recipient. Without this vital security feature, many malicious emails will be delivered to end users.
While there are clear benefits to email sandboxing, there is one disadvantage and that is sandboxing message delivery delays. Time must be allowed for deep analysis, especially as some malware variants delay malicious actions to defeat sandboxes. That means that there is a delay in delivering messages that have been sent to the sandbox and are found to be clean. That delay could be around 20 minutes in some cases, which is far from ideal. To reduce delays to a minimum, it is possible to whitelist certain trusted senders to ensure that their messages are never sent to the sandbox and adjust the rules of the email security solution to limit the emails that are sent to the sandbox.
SpamTitan from TitanHQ uses dual anti-virus engines for signature-based detection and a Bitdefender-powered email sandbox for detecting novel malware variants. In addition to performing reputation checks to identify untrusted senders, SpamTitan includes pattern filtering that allows security teams to specify their own terminology for blocking messages, geo-filtering to block emails from certain geographical regions where the company does not operate, and AI and machine learning algorithms for predicting new phishing threats and assessing how emails deviate from standard messages usually received by the business.
SpamTitan is a multi-award-winning email security solution that can be provided as a hosted email filter or as a gateway spam filter to be installed on existing hardware as a virtual appliance. It has been developed to be quick and easy to install and use, works seamlessly with Microsoft 365 to improve protection, and is an ideal email security solution for Managed Service Providers to provide advanced email security to customers.
If you do not have a sandbox for email with your email security solution, now is the time to consider changing to a more advanced email security solution. Give the TitanHQ team a call for more information and to help get you set up on a free trial.
by Jennifer Marsh | Jun 19, 2024 | Internet Security |
Ascension, one of the largest private healthcare systems in the United States, fell victim to a ransomware attack on May 8, 2024, that forced systems offline, including patients’ medical records which were not fully restored for a month. The attack caused massive disruption, and without access to electronic health records, staff were forced to record patient information manually.
Patient care was seriously affected, with delays in diagnosis and treatment, and the lack of access to medical records resulted in medical errors. Without technology to perform routine safety checks, patient safety was put at risk. The investigation into the attack is still ongoing, but evidence has already been found that files containing sensitive data were stolen in the attack. The scale of the data breach has yet to be determined but for a healthcare system as large as Ascension, the breach could be considerable.
The ransomware attack occurred as a result of a simple error by a single employee, who was tricked into downloading a malicious file from the internet. That file provided the attackers with a foothold in the network, from where they were able to launch a devastating ransomware attack. Ascension said it has no reason to believe that the file download was a malicious act and is satisfied that it was an honest mistake by the employee. Sadly, it is the type of mistake that frequently results in ransomware attacks and costly data breaches.
Ascension has not disclosed how the file was downloaded, whether it was from general web browsing, malvertising that directed the employee to a malicious website, or if they clicked a link in a phishing email. Regardless of how the employee arrived at the malicious site, the attack could have been prevented with the right technology in place. It is possible to protect against all of the above-mentioned methods of malware delivery with a web filter. WebTitan from TitanHQ is a DNS-based web filter for businesses to prevent employees from visiting websites hosting malware and to block the web-based component of phishing attacks.
WebTitan is fed threat intelligence to provide real-time protection against malicious websites. As soon as a malicious website is detected, it is added to the database and all WebTitan users are prevented from visiting that URL. WebTitan categorizes and blocks around 60,000 malware and spyware domains each day and if an attempt is made to visit one of those URLs, whether it is via a link in an email, malvertising, or general web browsing, the attempt is blocked and the user is directed to a locally hosted block page.
WebTitan is updated constantly with vast click stream traffic from actively visited URLs from 500 million end users, and the data is used to categorize websites. WebTitan users can then place restrictions on 53 categories of websites that employees can visit on their work devices, eliminating risks from common sources of malware such as torrent and file-sharing sites for which there is no business reason for access. Further, as an additional protection against malware, WebTitan can be configured to block downloads of certain file types from the internet, such as executable files that are commonly used to deliver malware. For the majority of employees, there is rarely a business need to download executable files.
Malware is commonly delivered via email, either via attachments containing malicious scripts and macros or via embedded hyperlinks. It is important to have an advanced email security solution in place to block this method of malware delivery. SpamTitan is a cloud-based anti-spam service that protects against known malware using twin antivirus engines that scan attachments for the signatures of malware. To protect against novel malware threats, SpamTitan incorporates a Bitdefender-powered email sandbox, where suspicious messages are sent for deep inspection. An email sandbox is key to blocking malware threats and essential due to the volume of novel malware variants now being distributed.
While technological solutions are essential, it is also important to provide security awareness training to the workforce to improve awareness of cyber threats and teach security best practices. This is another area where TitanHQ can help. SafeTitan is a comprehensive security awareness training platform and phishing simulator that is proven to reduce susceptibility to phishing attacks that helps businesses develop a human firewall and combat the many threats that target employees.
For more information on improving your defenses against malware and phishing threats, give the TitanHQ team a call. All TitanHQ cybersecurity solutions are also available on a free trial to allow you to put them to the test before making a purchase decision.
by Jennifer Marsh | Jun 3, 2024 | Phishing & Email Spam, Security Awareness |
Earlier this month, warnings were issued about the Black Basta ransomware group, after an increase in activity in recent weeks. Now a new tactic has emerged to gain initial access to networks that ultimately leads to a Black Basta ransomware attack.
Storm-1811 is a highly sophisticated financially motivated cybercriminal group that was first detected in April 2022. Unlike many cybercriminal groups that start slowly, Storm-1811 conducted more than 100 attacks in its first 7 months. The latest campaign linked to the group is a type of tech support scam and is conducted over the phone through voice phishing (vishing).
The threat actor targets users and uses social engineering techniques over the phone to convince the user that they need to take urgent action to fix a fictitious problem on their computer. The threat actor often impersonates a member of the IT help desk or even Microsoft technical support. This attack leverages Quick Assist – a legitimate Windows app that is used to establish a remote connection to a device.
Quick Assist is a useful tool for providing IT support. If a friend or family member is having difficulty with their computer, they can provide remote access to a more technically skilled family member to sort out the problem remotely. Through Quick Assist, it is possible to view the display, make annotations, and take full control of the connected device.
Any remote access tool can be abused by a threat actor and Quick Assist is no different. If the user is convinced that the request is genuine and access to their device is granted, the threat actor will be able to perform a range of malicious actions. In this campaign, the threat actor installs a range of malicious tools to allow them to achieve their objectives, including remote monitoring and management (RMM) tools such as ScreenConnect and NetSupport Manager, and malware including Qakbot and Cobalt Strike. After gaining access, Storm-1811 actors can steal data and the access will ultimately lead to a Black Basta ransomware attack.
One point where this campaign could fail is convincing a user that they have a problem with their computer that requires remote access to fix. To get around this problem, Storm-1811 threat actors create a problem that needs to be addressed. One of the ways they do this is by conducting an email-bombing campaign. They identify email addresses of employees at the targeted company and bombard them with spam emails by signing them up to various high-volume email subscription services. When they make the call, the user will no doubt be frustrated by the spam emails, and it is easy to convince them that the problem can be sorted via Quick Assist.
The user just needs to press CTRL plus the Windows Key and Q to initiate Quick Assist, and then enter the security code provided by the threat actor and confirm that they want to proceed with screen sharing. The threat actor can then request remote access through the session and, if granted by the user, will be provided with full control of the user’s device. If they get to that point while the user is still on the phone, the threat actor will be able to explain any installation of a program as part of the remediation efforts. The threat actor can then unsubscribe the user from the various email subscriptions to make them believe that the problem has been resolved. Since the tools used by the threat actor can easily blend in, the attack is likely to go undetected until ransomware is used to encrypt files.
There are two easy ways to reduce susceptibility to this attack. The first is for IT teams to block or uninstall Quick Assist if they are not using the tool for remote access. Since other remote access tools may be used in these tech support scams, it is also vital to educate the workforce about tech support scams.
Users should be trained never to provide remote access to their device unless they initiate the interaction with their IT help desk or Microsoft support. Many companies provide security awareness training to the workforce that focuses on email phishing since this has long been the most common method of gaining access to internal networks.
Security awareness training should also educate users about other forms of phishing, including SMS phishing (smishing), vishing, and phishing via instant messaging services. With SpamTitan, creating, automating, and updating training content with the latest tactics used by cybercriminals is easy. The platform includes an extensive range of engaging training modules and is constantly updated with new content based on real-world attacks by cybercriminal groups.
When you train your workforce with SafeTitan, you can greatly reduce susceptibility to the different types of cyberattacks. Give the TitanHQ team a call today for further information or use the SafeTitan link to sign up for a free trial.
by Jennifer Marsh | May 31, 2024 | Internet Security |
Downloading unofficial and pirated software from the Internet carries a significant risk of malware infections. Malware is often packaged with the installers or with the cracks/key generators that provide the serial keys or codes to activate the software.
Cybercriminals use a variety of methods for driving traffic to their malicious websites, including malicious Google Ads, adverts on other third-party ad networks, SEO poising to get their malicious sites appearing high in the search engine listings, and via torrent and warez sites. A warning has recently been issued about the latter by AhnLab Security Intelligence Center (ASEC).
The campaign identified by the researchers distributes Microsoft Office, Microsoft Windows, and the Hangul Word Processor. The pirated software is available through torrent sites and includes a professional-looking installer. The installer for Microsoft Office allows users to select the Office products they want to install in either the 32-bit or 64-bit version and select the language.
If the installer is run, the user will get the software they are looking for; however, in the background, a malware cocktail will be installed. The threat actor behind this campaign is distributing several different malware payloads, including coinminers, remote access trojans (RATs), downloaders, and anti-AV malware.
When the installer is run, an obfuscated .NET downloader is executed which connects to the attacker’s Telegram/Mastadon channels and obtains a Google Drive or GitHub URL from where Base64 encrypted strings are obtained. Those strings are decrypted on the device and are PowerShell commands. Task Scheduler is used to execute the PowerShell commands, which install the malware. The scheduled tasks also allow the threat actor to consistently install other malware variants on the infected device.
By using Task Scheduler, the threat actor can reinstall malware if it is detected and removed, and since an updater is installed, the PowerShell commands can change. Even if the initial URLs are blocked, others will be added to ensure malware can still be delivered.
Initially, the threat actor was installing the updater together with either the Orcus RAT or the XMRig cryptocurrency miner. Orcus RAT provides the threat actor with remote control of an infected device, and has keylogging capabilities, can take screenshots, access the webcam, and exfiltrate data. XMRig is configured to only run when it is unlikely to be detected and will quit when system resource usage is high.
In the latest campaign, the threat actor also installs 3Proxy, which allows abuse of the infected device as a proxy, PureCrypter for downloading and executing additional malware payloads, and AntiAV malware, which disables antivirus and other security software by modifying the configuration files.
While this campaign appears to be targeting users in South Korea, it clearly shows the risks of downloading pirated software. Due to the inclusion of the updater and the installation of PureCrypter, remediation is difficult. Further, new malware variants are being distributed every week to evade detection.
Employees often download software to make it easier for them to do their jobs, and Torrent sites are a common source of unauthorized software. Businesses should therefore implement policies that prohibit employees from downloading software that has not been authorized by the IT department and should also implement controls to prevent Torrent and other software distribution sites from being accessed.
With TitanHQ’s WebTitan DNS filter, blocking access to malicious and risky websites could not be simpler. Simply install the cloud-based web filter and configure the solution by using the checkboxes in the user interface to block access to these categories of websites. WebTitan is constantly updated with the latest threat intelligence to block access to known malicious websites, and it is also possible to block downloads of executable files from the Internet.
For more information on improving Internet security with a DNS-based web filter, give the TitanHQ team a call. WebTitan, like all other TitanHQ products, is available on a free trial, with product support provided to ensure you get the most out of the solution during the trial.
by Jennifer Marsh | May 30, 2024 | Phishing & Email Spam |
Last month, the UK government published the findings of its 2024 cyber security breaches survey. The annual survey was conducted by the Department for Science, Innovation and Technology (DSIT) in partnership with the Home Office between September 2023 and January 2024 on 2,000 UK businesses, 1,004 registered UK charities, and 430 educational institutions. The survey provides insights into the nature of cyberattacks and data breaches experienced in the UK and confirms that attacks are increasing.
In the past year, 50% of surveyed businesses and almost one-third of charities (32%) experienced at least one cybersecurity breach or attack, with medium-sized businesses (70%), large businesses (74%), and high-income charities with £500,000+ annual income (66%) more likely to experience a cybersecurity breach.
It is often reported that cyberattacks are becoming more sophisticated; however, the most common cyber threats are relatively unsophisticated and are often effective. The most common type of cyberattack was phishing, which was reported by 84% of businesses and 83% of charities, with impersonation of organizations – online and via email – reported by more than one-third of businesses (35%) and charities (37%). Malware was used in 17% of attacks on businesses and 14% of attacks on charities. In terms of prevalence, phishing was by far the most common type of cybercrime. 90% of businesses and 94% of charities that were victims of cybercrime experienced at least one phishing attack.
The costliest type of phishing attack is business email compromise (BEC). BEC covers several types of attacks, with the most common involving criminals accessing work email accounts and using them to trick others into transferring funds or sending sensitive data. For example, a threat actor gains access to an email account of a vendor and uses the account to send an email to a customer containing a fake invoice or a request to change bank account information for an upcoming payment.
The losses to BEC attacks can be considerable. Attacks frequently result in fraudulent transfers of tens of thousands of pounds or in some cases hundreds of thousands or millions. With such large sums involved, criminals put considerable effort into these scams. Targets are researched, phishing is used to compromise an employee email account, internal phishing is used to gain access to the right accounts, the contents of accounts are studied to identify information that can be used in the scam, and the legitimate account holder is impersonated in the attack on the targeted organization or individual.
The goal in these attacks is often to gain access to the email account of the CEO or a senior executive, and that account is used to conduct a scam internally or externally. Since the request comes from a trusted authority figure and uses their legitimate account, the request is often not questioned.
BEC attacks can be difficult to identify by employees but also by email security solutions as trusted accounts are used for the scams and the emails usually do not contain any malicious content such as a URL to a phishing website or malware. These attacks use social engineering and target human weaknesses.
Defending against BEC and phishing attacks requires a combination of measures. Since targets are extensively researched, businesses should consider reducing their digital footprint and making it harder for cybercriminals to obtain information that can be used in convincing phishing and BEC campaigns, especially by reducing the amount of information that is available online about senior staff members.
Anti-spam software is a must for blocking the initial phishing attacks that are used to compromise accounts; however, an advanced solution is required to block sophisticated BEC attacks. TitanHQ’s cloud-based anti-spam service – SpamTitan – performs a barrage of spam checks for inbound and outbound emails to identify spam, phishing, and BEC content, including reputation checks of domains and accounts, scans of message content, sandboxing to identify malicious attachments, and AI and machine learning analysis to identify emails that deviate from the standard messages typically received by an organization.
PhishTitan is an anti-phishing solution for Microsoft 365 that enhances Microsoft’s anti-phishing measures and catches the phishing threats that Microsoft misses. The solution adds banners to emails to warn employees about potentially malicious content and allows security teams to quickly remediate phishing attempts across the entire email environment.
Since phishing and BEC attacks target human weaknesses, it is vital to provide training to the workforce. The aim should be to improve awareness and condition employees to always be on the lookout for a scam and to err on the side of caution and report suspicious emails to their IT security team. Phishing simulations are useful for helping staff to recognize phishing emails and identify knowledge gaps. TitanHQ’s SafeTitan training platform has all the content you need to run effective training programs to improve defenses against phishing and BEC attacks.
Contact TitanHQ today about these solutions and other ways you can improve your defenses against phishing, BEC, and other types of cyberattacks.
by Jennifer Marsh | May 30, 2024 | Phishing & Email Spam, Security Awareness |
Phishing tactics are constantly changing and while email is still one of the most common ways of getting malicious content in front of end users, other forms of phishing are growing. Smishing (SMS phishing) has increased considerably in recent years, and vishing (voice phishing) is also common, especially for IT support scams.
Another method of malware delivery that has seen an enormous increase recently is the use of instant messaging and VoIP social platform Discord. Discord is a platform that has long been popular with gamers, due to being able to create a server with voice and text for no extra cost, both of which are necessary for teamspeak in gaming. While gamers still account for a majority of users, usage for non-gaming purposes is growing.
The platform is also proving popular with cybercriminals who are using it for phishing campaigns and malware distribution. According to Bitdefender, the antivirus company whose technology powers the SpamTitan email sandboxing feature, more than 50,000 malicious links have been detected on Discord in the past 6 months. Around a year ago, a campaign was detected that used Discord to send links to a malicious site resulting in the delivery of PureCrypter malware – a fully featured malware loader that is used for distributing information stealers and remote access trojans.
Discord responded to the misuse of the platform and implemented changes such as adding a 24-hour expiry for links to internally hosted files, which made it harder for malicious actors to use the platform for hosting malware. While this move has hampered cybercriminals, the platform is still being used for malware distribution. One of the latest malicious Discord campaigns is concerned with obtaining credentials and financial information rather than distributing malware.
The campaign involves sending links that offer users a free Discord Nitro subscription. Discord Nitro provides users with perks that are locked for other users, such as being able to use custom emojis anywhere, set custom video backgrounds, HD video streaming, bigger file uploads, and more. Discord Nitro costs $9.99 a month, so a free account is attractive.
If the user clicks the link in the message, they are directed to a fake Discord website where they are tricked into disclosing credentials and financial information. Other Discord Nitro lures have also been detected along the same theme, offering advice on how to qualify for a free Discord Nitro subscription by linking to other accounts such as Steam. According to Bitdefender, 28% of detected malicious uses are spam threats, 27% are untrusted, around 20% are phishing attempts and a similar percentage involve malware distribution.
Any platform that allows direct communication with users can be used for phishing and other malicious purposes. Security awareness training should cover all of these attack vectors and should get the message across to end users that they always need to be on their guard whether they are on email, SMS, instant messaging services, or the phone. By running training courses continuously throughout the year, businesses can develop a security culture by training their employees to be constantly on the lookout for phishing and malware threats and developing the skills that allow them to identify threats.
Developing, automating, and updating training courses to include information on the latest threats, tactics techniques, and procedures used by threat actors is easy with the SafeTitan security awareness training platform. SafeTitan makes training fun and engaging for end users and the platform has been shown to reduce susceptibility to phishing and malware threats by up to 80%.
If you are not currently running a comprehensive security awareness training program for your workforce or if you are looking to improve your training. Give the TitanHQ team a call and ask about SafeTitan. SafeTitan is one product in a suite of cloud-based security solutions for businesses and managed service providers, which includes an enterprise spam filter, a malicious file sandbox for email, a DNS-based web filter, email encryption, email archiving, and phishing protection for M365.
by Jennifer Marsh | May 29, 2024 | Internet Security |
There has been a marked increase in malware distribution campaigns in recent months using fake adverts that direct users to malicious websites where sensitive information such as login credentials or credit card numbers is collected, or malware is distributed. This tactic is called malvertising.
One of the most common types of malvertising is the creation of malicious adverts for software solutions, which are displayed when users search for software in search engines. The reason why software-related malvertising is effective is users are searching for a software solution, which means they will be expecting to download an installer. Software installers are executable files, and malware can be packed into the installers. When the installer is executed, the user will get the software they are expecting but malware will also installed in the background.
There are a variety of defenses against malvertising. Installing an ad blocker will prevent the adverts from being displayed, security awareness training should teach employees to always be wary of adverts and to hover their mouse arrow over the advert to show the destination URL and ensure that the URL matches the software being offered. Another important defense is a web filter, which will block access to the malicious sites that the adverts direct users to. Web filters such as WebTitan can also protect against Internet-based malware distribution that doesn’t use malvertising to drive traffic to malicious websites, and can also block downloads of executable files from the Internet for individuals or user groups.
For example, a campaign has recently been detected that uses booby-trapped websites that generate a fake web browser update warning. The websites have embedded JavaScript code which redirects users to an update page where they can apply important browser security updates. The user proceeds to download what appears to be a zip file that contains the updater; however, the updater is a JavaScript file that will launch PowerShell scripts that will download and execute a malware payload from the threat actor’s remote server. In this campaign, at least two malware payloads are delivered – the BitRAT remote access trojan and the Lumma Stealer information stealer.
Another browser update scam has been identified that involves tricking the user into copying, pasting, and executing a PowerShell command to protect their browser; however, the PowerShell command will deliver and execute malware.
While an ad blocker will block the malicious adverts in these campaigns, it will not block drive-by malware downloads and attacks that use email, SMS, and instant messaging services to distribute malicious links. WebTitan is a more comprehensive web security solution that has multiple curated threat intelligence feeds that block access to a malicious website for all WebTitan users within about 5 minutes of a malicious site being detected anywhere in the world. The solution will also block downloads of executable files and has an easy-to-implement and configure category-based filter, that allows businesses to block access to risky and/or non-work-related websites.
WebTitan adds an extra layer to your security defenses to protect against malware distribution and the web-based component of phishing attacks. Further, being a DNS-based filter there is no latency, and the solution can be used to protect devices on and off the network, with the latter possible by installing a roaming agent on mobile devices.
For further information on malvertising protection, web filtering, and DNS and URL filtering, give the TitanHQ team a call.
by Jennifer Marsh | May 28, 2024 | Internet Security |
Phishing and spam emails are commonly used for malware distribution; however, it has become much harder for malware and malicious scripts to evade email filtering solutions, especially advanced email security solutions with sandboxing and AI and machine learning capabilities. Some threat actors have had greater success using Google Ads to drive traffic to sites hosting trojanized installers for popular software.
Google Ads allows advertisers to bid to place adverts at the top of the search engine listings for key search terms, giving the adverts the most prominent position on the page. While Google has controls in place to prevent malicious ads from appearing, a small number of threat actors successfully circumvent those controls. Some of the most effective uses of malicious Google Ads are for software solutions. If threat actors can direct users to a malicious site that resembles a legitimate software provider, the user is likely to download and run the installer and inadvertently infect their device with malware.
One such campaign was recently uncovered by security researchers at Malwarebytes. While they were unable to identify the final malicious payload, they believe the goal was to deliver an information stealer. An information stealer is a type of malware that runs in the background and gathers information about the system. Information stealers often target login information such as usernames and passwords and can capture keystrokes, take screenshots, search histories, cookies, steal from cryptocurrency wallets, and more.
In this campaign, the threat actors targeted search terms related to the Arc browser for Windows, a freeware web browser that was launched in July 2023 for MacOS. The web browser has many features that set it aside from other web browsers and it has received five-star reviews from reviewers and users since its launch in 2023. The highly anticipated Windows version was released on April 30, 2024, and the malvertising campaign was prepared ahead of the launch.
One potential problem with a campaign such as this is malvertisers need to direct traffic to their own website where the malicious installer is hosted. If you are looking to download Adobe Reader, for example, and the advert displays anything other than the Adobe.com domain, you would know not to click. With Google Ads, malvertisers can display the legitimate domain in the Ad and then redirect the user to their own domain when they click the ad.
In this campaign, like many other malvertising campaigns, the threat actor uses lookalike domains that closely resemble the legitimate domain – Arc[.]net, and the page looks exactly like the legitimate site that it spoofs. If the user clicks to download the installer and executes the file, it will install the Arc browser as well as a malicious script that downloads and executes the malware payload. The malware will then run silently in the background and the user will likely be unaware that anything untoward has happened.
Employees often look for software to allow them to work more efficiently and download software from the web. For businesses, malicious Google Ads are a serious threat and can easily lead to a costly malware infection and data breach. To protect against malware infections via the web, many businesses rely on antivirus software that scans for malware when it has been downloaded. The problem is these solutions are often signature-based and can only detect malware variants if they have the signatures in their malware definition lists. New variants are constantly being released that differ sufficiently to evade signature-based detection mechanisms.
In addition to antivirus software, businesses should consider implementing a web filter such as WebTitan. WebTitan is a DNS-based web filter with no latency, so there is no impact on page load and download speeds. The filter is fed threat intelligence from a network of 500 million end users and is constantly updated with the latest intelligence and will block attempts to visit known malicious sites. If a user attempts to visit a known malicious URL, the attempt will be blocked before a connection is made. WebTitan can also be configured to block certain file downloads from the web, such as executable files. This will stop malware from being installed and will also help to curb shadow IT. WebTitan can also be configured to block third-party adverts on websites to combat malvertising.
In addition to these software solutions, businesses should provide security awareness training to the workforce to explain the risks of malware, teach security best practices, and eradicate risky behaviors. This is another area where TitanHQ can help. TitanHQ has a comprehensive security awareness training platform – SafeTitan – which is the only behavior-driven security awareness solution that delivers security training in real-time in response to security errors by employees. SafeTitan is an effective way of modifying user behavior and building a human firewall of users.
To find out more about web filtering with WebTitan and security awareness training with SafeTitan, give the TitanHQ team a call. Both solutions are also available on a free trial to allow you to test them out before making a purchase decision.
by Jennifer Marsh | May 27, 2024 | Phishing & Email Spam, Security Awareness, Spam Advice, Spam News |
Email phishing is the most common form of phishing, with email providing threat actors with an easy way of getting their malicious messages in front of employees. Phishing emails typically include a URL along with a pressing reason for clicking the link. The URLs are often masked to make them appear legitimate, either with a button or link text relevant to the lure in the message. Email attachments are often added to emails that contain malicious scripts for downloading a variety of malicious payloads, or links to websites where malware is hosted.
While there are many email security solutions available to businesses, many lack the sophistication to block advanced phishing threats as they rely on threat intelligence, antivirus software, and reputation checks. While these are important and effective at blocking the bulk of phishing and malspam emails, they are not effective at blocking zero-day attacks, business email compromise, and advanced phishing threats.
More advanced features include email sandboxing for detecting and quarantining zero-day malware threats and malicious scripts, greylisting for increasing the spam catch rate, and AI and machine learning capabilities that can assess messages and identify threats based on how they differ from the messages that are typically received by the business. SpamTitan, a cloud-based anti-spam service from TitanHQ, has these features and more. Independent tests have shown that the solution blocks more than 99.99% of spam emails, 99.95% of malware, and more than 99.91% of phishing emails. SpamTitan can be provided as a hosted email filter or as a gateway spam filter for installation on-premises on existing hardware, serving as a virtual anti-spam appliance.
Microsoft 365 users often complain about the phishing catch rate of the protections provided by Microsoft, which are EOP only for most licenses and EOP and Defender for the most expensive licenses. While these protections are effective at blocking spam and known malware, they fall short of what is required for blocking advanced threats. To improve Microsoft 365 security and block the threats that Microsoft misses, TitanHQ has developed PhishTitan. PhishTitan augments Microsoft 365 defenses and is the easiest way of improving the Office 365 spam filter. These advanced defenses are now vital due to the increase in attacks. The Anti-Phishing Working Group (APWG) has reported that more phishing attacks were conducted in 2023 than ever before.
Massive Increase in Text Message Phishing Scams
Blocking email phishing attempts is straightforward with advanced email security solutions, which make it much harder for phishers to get their messages in front of employees. One of the ways that threat actors have adapted is by switching to SMS phishing attacks, which no email security solution can block. APWG has reported a major increase in SMS-based phishing attempts.
A recent study attempted to determine the extent to which SMS phishing is being used. Researchers used SMS gateways – websites that allow users to obtain disposable phone numbers – to obtain a large number of phone numbers for the study. They then waited to see how long it took for SMS phishing messages to be received. The study involved 2,011 phone numbers and over 396 days the researchers received an astonishing 67,991 SMS phishing messages, which averages almost 34 per number. The researchers analyzed the messages and identified 35,128 unique campaigns that they associated with 600 phishing operations. Several of the threat actors had even set up URL shortening services on their own domains to hide the destination URLs. With these shortening services, the only way to tell that the domain is malicious is to click the link.
Blocking SMS phishing threats is difficult for businesses and the primary defense is security awareness training. SMS phishing should be included in security awareness training to make employees aware of the threat, as it is highly likely that they will encounter many SMS phishing threats. The SafeTitan security awareness platform makes creating training courses simple and the platform includes training content on all types of threats, including SMS, voice, and email phishing. With SafeTitan it is easy to create and automate campaigns, as well as deliver training in real-time in response to employee errors to ensure training is provided when it is likely to have the greatest impact – immediately after a mistake is made.
by Jennifer Marsh | May 26, 2024 | Phishing & Email Spam, Security Awareness |
Cloudflare Workers is being abused in phishing campaigns to obtain credentials for Microsoft, Gmail, Yahoo!, and cPanel Webmail. The campaigns identified in the past month have mostly targeted individuals in Asia, North America, and Southern Europe, with the majority of attacks conducted on organizations in the technology, finance, and banking sectors.
Cloudflare Workers is part of the Cloudflare Developer Platform and allows code to be deployed and run from Cloudflare’s global network. It is used to build web functions and applications without having to maintain infrastructure. The campaigns were identified by researchers at Netskope Threat Labs. One campaign uses a technique called HTML smuggling, which involves abusing HTML5 and JavaScript features to inject and extract data across network boundaries. This is a client-side attack where the malicious activities occur within the user’s browser. HTML smuggling is most commonly associated with malware and is used to bypass network controls by assembling malicious payloads on the client side. In this case, the malicious payload is a phishing page.
The phishing page is reconstructed in the user’s browser, and they are prompted to log in to the account for which the attacker seeks credentials, such as their Microsoft account. When the victim enters their credentials, they will be logged in to the legitimate website and the attacker will then collect the tokens and session cookies.
Another campaign uses adversary-in-the-middle (AitM) tactics to capture login credentials, cookies, and tokens, and allow the attackers to compromise accounts that are protected with multi-factor authentication. Cloudflare Workers is used as a reverse proxy server for the legitimate login page for the credentials being targeted. Traffic between the victim and the login page is intercepted to capture credentials as well as MFA codes and session cookies. The advantage of this type of attack is the user is shown the exact login page for the credentials being targeted. That means that the attacker does not need to create and maintain a copy of the login page.
When the user enters their credentials, they are sent to the legitimate login page by the attacker, and the response from the login page is relayed to the victim. The threat actor’s application captures the credentials and the tokens and cookies in the response. In these CloudFlare Workers phishing campaigns, users can identify the scam by looking for the *.workers.dev domain and should be trained to always access login pages by typing the URL directly into the web browser.
Defending against sophisticated phishing attacks requires a combination of security measures including an email security solution with AI/machine learning capabilities and email sandboxing, regular security awareness training, and web filtering to block the malicious websites and inspecting HTTP and HTTPS traffic. For more information on improving your defenses, give the TitanHQ team a call.
by Jennifer Marsh | May 15, 2024 | Network Security, Phishing & Email Spam, Security Awareness |
The Black Basta ransomware-as-a-service (RaaS) group has been aggressively targeting critical infrastructure entities in North America, Europe, and Australia, and attacks have been stepped up, with the group’s affiliates now known to have attacked at least 500 organizations worldwide. In the United States, the group has attacked 12 of the 16 government-designated critical infrastructure sectors, and attacks on healthcare providers have increased in recent months.
Black Basta is thought to be one of multiple splinter groups that were formed when the Conti ransomware group shut down operations in June 2022. The group breaches networks, moves laterally, and exfiltrates sensitive data before encrypting files. A ransom note is dropped and victims are required to make contact with the group to find out how much they need to pay to a) prevent the publication of the stolen data on the group’s leak site and b) obtain the decryption keys to recover their encrypted data.
The group uses multiple methods for initial access to victims’ networks; however, the primary method used by affiliates is spear phishing. The group has also been observed exploiting known, unpatched vulnerabilities in software and operating systems. For instance, in February 2024, the group started exploiting a vulnerability in ConnectWise (CVE-2024-1709). The group has also been observed abusing valid credentials and using Qakbot malware. Qakbot malware is commonly distributed in phishing emails.
The Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Department of Health and Human Services (HHS), and Multi-State Information Sharing and Analysis Center (MS-ISAC) recently issued a cybersecurity alert about Black Basta in response to the increase in attacks. The alert shares indicators of compromise and the tactics, techniques, and procedures used by the group in recent attacks. All critical infrastructure organizations have been advised to implement a range of mitigations to make it harder for Black Basta ransomware affiliates to access internal networks and move laterally. The recommended mitigations will also strengthen defenses against other ransomware groups and should be considered by all businesses and organizations.
Phishing and spear phishing are common access vectors for ransomware groups and the initial access brokers many of the groups work with, including the operators of Qakbot malware. Strengthening phishing defenses should therefore be a priority. TitanHQ offers three products that help improve phishing defenses: SpamTitan Email Security, PhishTitan, and the SafeTitan security awareness training and phishing simulation platform.
SpamTitan is a comprehensive email security and spam filtering service that blocks the full range of threats including spam, phishing, malware, viruses, and other malicious emails. Independent tests have confirmed the solution has a 99.99% spam catch rate, Bayesian autolearning and heuristics defend against advanced email threats, recipient verification using SPF, DKIM, and DMARC, antivirus protection is provided using two leading anti-virus engines, and the solution incorporates sandboxing for deep analysis of suspicious files. The sandbox is capable of detecting threats from their behavior rather than email signatures and is capable of identifying and blocking zero-day malware threats. The solution is regularly rated the best spam filter for business by independent software review sites and is one of the most popular spam filters for MSPs.
PhishTitan is a powerful anti-phishing solution for businesses that use Microsoft 365 that protects against the advanced attacks that Microsoft’s EOP and Defender miss. The solution includes auto-remediation features to help businesses rapidly respond when they are targeted by cybercriminal groups, and integrates seamlessly with Microsoft 365, augmenting Microsoft’s protections to ensure that more phishing threats are identified and blocked. PhishTitan adds banner notifications to emails from external email accounts and warnings about unsafe content, rewrites URLs to show the true destination, provides time-of-click protection against malicious URLs, provides threat data and analytics to help users assess their risk profile, and subjects all emails to AI and LLM analysis, detecting phishing threats with a high degree of accuracy and blocking threats that Microsoft misses. The solution also uses real-time analysis and threat assessments to neutralize business email compromise and spear phishing attacks before they begin.
It is important to train the workforce on how to recognize and report phishing attempts. SafeTitan is a comprehensive security awareness training platform that provides training in bite-sized chunks. The training modules are no longer than 10 minutes and are easy to fit into busy workflows. By providing regular training each month, businesses can develop a security culture and significantly improve resilience to phishing and spear phishing attacks, especially when combined with phishing simulations. The phishing simulator includes templates from real-world ransomware campaigns, and they are regularly updated based on the latest threat intelligence.
As an additional protection, multi-factor authentication should be implemented on all accounts, and phishing-resistant MFA is the gold standard. Since vulnerabilities are often exploited, it is important to ensure that software, firmware, and operating systems are kept up to date with patches applied promptly. Ransomware groups such as Black Basta are quick to exploit known vulnerabilities in their attacks. Remote access software should be secured and disabled if it isn’t used, networks should be segmented to hamper lateral movement, and backups should be regularly made of all critical data, with copies stored securely offsite on air-gapped devices. Further recommended mitigations can be found in CISA’s StopRansomware Guide.
by Jennifer Marsh | May 14, 2024 | Industry News, Phishing & Email Spam |
TitanHQ has announced two new strategic alliances that will improve access to the company’s cybersecurity solutions in the Indian subcontinent and the Middle East. Evanti Tech is a Mumbai-based provider of IT infrastructure, cloud, and security services that helps to protect Indian businesses against cyberattacks, ransomware attacks, and other cybersecurity threats. The new alliance with TitanHQ will see Evanti Tech serve as a value-added distributor, incorporating TitanHQ’s cloud-based email security solutions into its cybersecurity suite to provide its clients with multi-layered protection capable of defending against a constantly evolving cyber threat landscape. The addition of TitanHQ’s email security solutions will allow the company to better protect its clients from email-based threats such as ransomware, malware, phishing, spear phishing, and business email compromise.
TitanHQ has also announced a new alliance with the Dubai, UAE-based cybersecurity managed service (CSMS) provider Nanjgels. Nanjgels protection methodology is based on five pillars of security – Protect, Identify, Detect, Remediate, Respond, with the company providing infrastructure security, user security, network security, data & app security, and security operations and response. Under the new alliance, Nanjgels will be adding SpamTitan email security solutions to its portfolio and will be offering them to all clients in the region to help them improve email security and block spam, phishing, spear phishing, BEC, ransomware, and other email threats.
The SpamTitan suite of products has been developed from the ground up to meet the needs of managed service providers and help them better protect their clients from email-based threats. SpamTitan includes double anti-virus protection to block known malware threats, email sandboxing to identify and block zero-day malware threats, protection against malicious links in emails, and spam detection mechanisms such as SPF, DKIM, DMARC, and greylisting to block more than 99.99% of spam and unwanted emails. The solution scans inbound and outbound emails and includes data loss protection features to combat insider threats.
Multi-award-winning SpamTitan is an ideal solution for protecting Microsoft 365 accounts. Almost 20% of phishing emails circumvent Microsoft 365 Exchange Defender and Microsoft Exchange Online Protection (EOP). SpamTitan integrates seamlessly with Microsoft 365 to augment defenses and block the phishing and malware threats that Microsoft misses. SpamTitan has achieved 36 consecutive VB Bulletin Anti-Spam awards, and recent independent tests have confirmed the solution blocks in excess of 99.95% of malware.
TitanHQ’s multi-tenant solutions are hugely popular with managed service providers as they make it easy to sell, onboard, manage, and deliver advanced security solutions directly to their client base and reduce the amount of time that MSPs need to devote to protecting their clients. TitanHQ offers antispam solutions for MSPs, phishing protection, DNS filtering, email encryption, email archiving, security awareness training, and phishing simulations. If you are a managed service provider looking to improve security, contact TitanHQ to find out more about the TitanShield program and the products you can easily add to your security stack to better protect your clients.
by Jennifer Marsh | Apr 30, 2024 | Email Scams, Network Security, Phishing & Email Spam |
The U.S. government and education sectors are being targeted by cybercriminals looking to steal sensitive data. These sectors hold large volumes of sensitive data that are easily monetized, victims can be extorted, and access to compromised networks can be sold to other cybercriminal groups such as ransomware gangs. These attacks can result in significant data breaches, major financial losses, and reputational damage that is hard to repair.
The campaign uses a combination of two malware variants and vulnerability exploitation, and the attack starts with phishing emails with malicious attachments. The campaign was identified by researchers at Veriti and delivers the notorious Agent Tesla remote access trojan (RAT) and an information-stealing malware called Taskun. Agent Tesla provides attackers with remote access to networks and is often used by initial access brokers for compromising networks, with the access sold on to other cybercriminal groups. Agent Tesla can be used to download additional payloads and has comprehensive information-stealing capabilities. The malware can log keystrokes, take screenshots, and steal credentials from browsers, wireless profiles, and FTP clients.
Taskun malware is spyware that also has information-stealing capabilities. In this campaign, the malware is used to compromise systems and make it easier for Agent Tesla to be installed, establish persistence, and operate undetected for long periods. The campaign involves emails with malicious attachments, with social engineering techniques used to trick employees into running malicious code that exploits unpatched vulnerabilities in operating systems and Office applications. The campaign involves a reconnaissance phase to identify the vulnerabilities that can be exploited to maximize the chance of a highly impactful compromise. The vulnerabilities exploited in this campaign include several Microsoft Office remote code execution vulnerabilities dating from 2010 to 2018 and takes advantage of businesses with poor patch management practices, incomplete inventories of connected devices, and devices running outdated software due to issues upgrading.
Defending against email-based attacks involving multiple malware variants and vulnerability exploitation requires a multi-layered approach to security, with cybersecurity measures implemented that provide overlapping layers of protection. The first line of defense should be advanced spam filtering software to block inbound spam and phishing emails. SpamTitan from TitanHQ is an AI-driven cloud-based email filtering service that is capable of identifying and blocking spam and phishing emails and has advanced malware detection capabilities. In addition to dual antivirus engines, the SpamTitan hosted spam filter includes email sandboxing for behavioral detection of malware threats. In independent tests, SpamTitan was shown to block 99.983% of spam emails, 99.914% of phishing emails, and 99.511% of malware.
It is important to ensure that employees are made aware of the threats they are likely to encounter. Security awareness training should be provided to teach cybersecurity best practices, eradicate risky practices, and train employees to be vigilant and constantly on the lookout for signs of phishing and malware. The SafeTitan security awareness training platform makes it easy to develop and automate comprehensive training and keep employees up to date on the latest tactics used by threat actors. SafeTitan, in combination with TitanHQ’s cloud-based anti-spam service, will help to ensure that phishing and malware threats are identified and blocked.
Cybersecurity best practices should also be followed, such as implementing multi-factor authentication on accounts, ensuring patches are applied promptly, keeping software up to date, installing endpoint antivirus solutions, and network segmentation to reduce the impact of a successful attack. It is also important to ensure there is a comprehensive inventory of all devices connected to the network and conduct vulnerability scans to ensure weaknesses are detected to allow proactive steps to be taken to improve security.
by Jennifer Marsh | Apr 30, 2024 | Email Scams, Phishing & Email Spam, Security Awareness, Spam Advice |
Business Email Compromise (BEC) is one of the most financially harmful cyberattacks. BEC is an attack where a cybercriminal uses social engineering techniques or phishing to gain access to an email account with a view to tricking people into disclosing sensitive and valuable data that can be sold or used in other types of attacks or scams. The goal of many BEC attacks is to trick senior executives, budget holders, or payroll staff into making fraudulent wire transfers, changing account details for upcoming payments, or altering direct deposit information to payroll payments directed to attacker-controlled accounts. When the attack results in a fraudulent wire transfer it is often referred to as Funds Transfer Fraud (FTF).
For the past several years, the biggest cause of losses to cybercrime – based on complaints filed with the Federal Bureau of Investigation’s (FBI) Internet Crime Complaint Center (IC3) – was BEC attacks. In 2022, IC3 received reports of losses of $2.7 billion from BEC attacks and $2.9 billion in losses in 2023. A recent report from the cyber insurance provider, Coalition, explored the reasons why claims were made on policies and by far the biggest cause of claims was fraud from attacks that originated in inboxes. More than half of claims were for losses that started with emails, with 28% of claims made for BEC attacks and 28% for FTF. The number of claims related to email-based attacks makes it clear that email security is an important aspect of cyber risk management. If you want to reduce cyber risk, email security is one of the best places to start and this is an area where TitanHQ can help.
TitanHQ’s anti spam software, SpamTitan, is an advanced email security solution for businesses and managed service providers that protects against the full range of email-based attacks by blocking spam, phishing, spoofing, malware, and zero-day attacks. SpamTitan includes dual antivirus engines for detecting known malware threats, sandboxing for behavioral analysis of emails to detect zero-day threats, reputation checks, and AI algorithms to anticipate new attacks. SpamTitan is delivered as a cloud-based anti-spam service or an anti-spam gateway, and is one of the most popular MSP spam filtering solutions.
PhishTitan is a relatively new addition to the TitanHQ cybersecurity portfolio and has been developed to improve Microsoft 365 security and catch the sophisticated phishing and BEC threats that Microsoft 365 misses. PhishTitan augments EOP and Defender and detects phishing threats with unbeatable accuracy and minimal false positives, with the solution adapting to new phishing tactics through comprehensive phishing feeds curated by TitanHQ and feedback from end users. PhishTitan rewrites URLs to show their true destination, provides time-of-click protection against URLs in phishing emails, protects against malware, adds banner notifications to emails to warn end users, makes post-delivery remediation quick and easy, and provides next-generation protection against phishing and BEC attacks.
In addition to solutions that block spam and phishing emails, end user security awareness training is important. Email-based attacks target employees and use social engineering to trick them into disclosing sensitive information, downloading malware, and making fraudulent wire transfers. SafeTitan from TitanHQ is a comprehensive security awareness training and phishing simulation platform for training the workforce to be more security aware, showing employees how to recognize and avoid threats, and keeping them up to date on the latest tactics targeting them. The platform also includes a phishing simulator for conducting fully automated phishing simulations. SafeTitan is the only behavior-driven security awareness solution that delivers security training in real-time in response to errors, ensuring training is delivered when it will have the most impact.
Email will continue to be a major attack vector but with TitanHQ solutions in place, you will be well protected. Give the TitanHQ team a call today for more information about these and other TitanHQ security products. All three of these products are available on a free trial to allow you to test them out for yourself and see the difference they make.
by Jennifer Marsh | Apr 29, 2024 | Phishing & Email Spam, Spam Software |
Phishing typically involves impersonation of a trusted individual or brand. In email phishing, the sender’s email address is often spoofed to make it appear that the messages have been sent from a legitimate domain, the emails often include the spoofed company’s logo, the color scheme used by that company, and the messages themselves are often very similar to the official emails sent by that brand.
It stands to reason that the most commonly impersonated brands are large tech companies, as more people are familiar with those companies and use their products and services. It should not come as a surprise to hear that the most impersonated brand in Q1, 2024 was Microsoft, which was impersonated in 38% of all phishing attacks, according to data from Check Point Research, up from 30% of attacks in the previous quarter. Google was the second most impersonated brand and was impersonated in 11% of phishing attacks, up from 8% in Q4, 2023.
Phishing attacks impersonating Amazon fell from 9% in Q4, 2023 to just 3% in Q1, 2024. The fall in attacks can be explained by fewer online sales after the holiday period, with phishers favoring other brands at the start of the year. There was an increase in attacks impersonating LinkedIn to target job seekers in response to an increase in job hunting in the New Year. LinkedIn rose to third place and was impersonated in 11% of attacks. Another seasonal increase was a rise in attacks impersonating Airbnb, which made it into the top 10 most impersonated brands, likely due to the increase in holiday bookings in the New Year.
Cybercriminals often change tactics and respond to seasonal changes, such as increasing attacks impersonating delivery firms and online retailers in the run-up to the holiday season, and piggyback on the popularity of major news stories and sporting events. This year is an Olympics year, and the European Football championships will be held in Germany in June. Lures related to these events are certain to be used as interest grows over the coming weeks as the events draw closer.
What is clear from phishing data is attacks are becoming more numerous and more sophisticated. According to tracking data by the Anti-Phishing Working Group (APWG), there were more than five million phishing attempts reported in 2023, the highest total ever recorded by APWG. Attacks against social media platforms showed a marked increase as the year drew to an end and accounted for almost 43% of all phishing attacks.
QR code phishing is also increasing. QR codes are used to send traffic to malicious URLs, and they are highly effective for phishing. Email security solutions typically check embedded hyperlinks against lists of known malicious domains, with many following hyperlinks and assessing the sites that users are redirected to. Many email security solutions, however, lack the capability to read QR codes, so the messages often end up in inboxes where they can be opened by end users.
It is not only email phishing that is increasing. Vishing – voice phishing attacks continue to rise and there was a major increase in Business Email Compromise (BEC) attacks, which the APWG data shows increased by 24% compared to the previous quarter. As phishing attacks increase in number and sophistication, businesses need to ensure that their defenses are capable of blocking these threats and that their employees are trained to be on high alert and constantly look for the signs of phishing in all communications.
One of the most important protective measures for businesses is to have an effective Office 365 spam filter. The anti-spam and anti-malware protections put in place by Microsoft and included with all licenses (EOP) are effective at blocking spam and known malware, but it is not so effective at blocking zero-day phishing and malware threats, many of which land in users’ inboxes. The more advanced protection that is provided with Microsoft’s E5 premium license improves phishing detection considerably, yet even this measure does not block many sophisticated phishing attempts. As such, many businesses are keen to improve the Office 365 spam filter and look for a third-party cybersecurity solution.
An increasing number of businesses are signing up for advanced AI- and machine learning-driven protection from TitanHQ to improve protection for Microsoft 365 environments. The engine that powers two of TitanHQ’s most popular cybersecurity solutions – SpamTitan and PhishTitan- has VBSpam+ certification from Virus Bulletin and in Q1, 2024 tests, was found to have a spam catch rate of 99.983%, a phishing catch rate of 99.914%, a malware catch rate of 99.51%, and a false positive rate of 0.00%. Overall, the engine got a 99.983% overall score.
SpamTitan is a cost-effective, easy-to-use email security solution for stopping phishing attacks, spam, malware, and ransomware. The solution features AI-based phishing protection via the newest zero-day threat intelligence, double malware protection with two antivirus engines, a next-generation sandbox for analyzing the behavior of messages to identify zero-day threats, and the solution is easy to integrate with Microsoft 365 to improve protection.
PhishTitan is a cloud-based, next-generation phishing protection and remediation solution that has been developed for use with Microsoft 365 that can identify and block the advanced phishing threats that Microsoft misses. PhishTitan has a high detection accuracy and uses AI to assess the content, tone, and meaning of emails to identify unusual, suspicious, and malicious messages. The solution also adapts to constantly evolving phishing tactics.
URLs in phishing emails are rewritten to identify their true destination, are compared to an extensive range of intelligence feeds, and the solution provides time-of-click protection against malicious links in emails. The solution also learns from user feedback to further improve accuracy and applies banners to emails warning about potentially malicious content and can be used by IT teams to automate the remediation of phishing emails from inboxes.
Phishing attacks are getting more sophisticated and tactics are constantly changing, but with the advanced protection provided by SpamTitan and PhishTitan that significantly improves the Microsoft 365 spam filter, businesses will be prepared. Give the TitanHQ team a call for more information, to arrange a product demonstration, or to sign up for a free trial to put the solutions to the test.
by Jennifer Marsh | Apr 25, 2024 | Email Scams, Phishing & Email Spam |
Many phishing campaigns involve indiscriminate emails that are sent in high volume in the hope that some recipients will respond. These campaigns tend to involve lures that are likely to be opened by as many users as possible such as missed deliveries, security warnings about unauthorized account access, and payments that will soon be applied to accounts. This spray-and-pray tactic is not nearly as effective as more tailored campaigns targeting specific types of users, and to make up for this, the campaigns involve huge volumes of messages. These campaigns are relatively easy for email security solutions to detect.
Phishing campaigns that target employees in a single organization can be much harder to identify. The threat actor tailors the message to the organization being targeted, and even to specific employees in the organization. These campaigns often use compromised vendor email accounts, with the emails being sent from trusted domains. There is a much greater chance of these emails landing in inboxes and the emails being opened by employees. Campaigns such as this can be highly effective and often result in many email accounts in the organization being compromised.
A recent example of this type of attack and the impact it can have comes from California. The Los Angeles County Department of Health Services, an integrated health system that operates public hospitals and clinics in L.A. County, was targeted in a phishing campaign between February 19, 2024, and February 20, 2024. The emails appeared to have been sent by a trusted sender, landed in inboxes, and were opened by many employees. The emails contained a hyperlink that directed users to a website where they were told they needed to enter their login credentials. 23 employees fell for the scam and entered their credentials.
The credentials were captured, and the threat actor was able to access the employees’ email accounts, which contained sensitive patient data such as names, dates of birth, contact information, medical record numbers, dates of service, medical information, and health plan information. While the information exposed in the attack could not be used for identity theft – Social Security numbers were not compromised – the attacker gained access to information that could be used for medical identity theft. The patients affected could also be targeted in very convincing phishing campaigns to obtain further information such as Social Security numbers. Similar attacks have been reported by other healthcare organizations where the email accounts contained vast amounts of data, including tens of thousands of Social Security numbers and sensitive financial information.
After attacks such as this, additional security awareness training is provided to the workforce to raise awareness of the threat from phishing; however, the provision of comprehensive training regularly throughout the year will go a long way toward ensuring that attacks such as this do not succeed and that if they do, the resultant data breach is far less severe.
TitanHQ’s SafeTitan security awareness training platform allows organizations to conduct comprehensive training continuously, and since each training module is a maximum of 10 minutes, it is easy to fit the training into busy workflows. The training platform has a huge range of content, covering a broad range of threats, and when programs are run continuously and employees complete a few training modules a month, susceptibility to phishing drops considerably, especially when the SafeTitan phishing simulator is also used. The simulator includes templates taken from recent real-world phishing campaigns. If a user responds to one of these simulations, they are immediately told where they went wrong and are required to complete a training module relevant to that threat.
End-user security awareness training is an important part of your cybersecurity arsenal, but it is also vital to block as many phishing emails as possible. TitanHQ’s SpamTitan email security is an advanced, AI and machine learning-driven anti-spam solution that blocks more than 99.9% of spam email and phishing threats. The solution includes twin antivirus engines for blocking known malware, and sandboxing for blocking zero-day threats, and is a highly effective spam filter for Office 365. With SafeTitan security awareness training and an advanced Microsoft 365 spam filter from TitanHQ, businesses will be well protected from phishing threats.
All TitanHQ solutions are intuitive, easy to use, and can be set up in just a few minutes and are available on a free trial to allow you to test them out for yourself before making a purchase decision. Independent reviews from genuine users of TitanHQ solutions show SpamTitan is much loved by users. On G2 reviews, SpamTitan is consistently given 5-star reviews by end users, who rate it the best spam filter for Outlook due to its effectiveness, low cost, ease of use, and the excellent customer service from the TitanHQ team.
SafeTitan and SpamTitan are available on a free trial to allow you to test them out for yourself before making a purchase decision. Give the TitanHQ team a call today to take the first step toward improving your phishing defenses.
by Jennifer Marsh | Apr 24, 2024 | Phishing & Email Spam |
Cybercriminals are constantly evolving their tactics for delivering malware and one of the most recent changes concerns the Remcos RAT. Remcos was developed by Breaking Security as a legitimate remote administration tool that can be used for network maintenance, system monitoring, surveillance, and penetration testing; however, the tool has been weaponized to create the Remcos Remote Access Trojan (RAT).
The Remocos RAT has extensive capabilities and has been used by cybercriminals since 2016. The malware allows threat actors to take control of systems and maintain persistent, highly privileged remote access. The malware can be used for a range of purposes, with threat actors commonly using it for credential theft, man-in-the-middle internet connections, and to create botnets of infected devices that can be used for distributed denial of service attacks (DDoS).
The Remcos RAT is distributed in spam email campaigns. Since 2016, the most common method for distributing the malware used spam emails with malicious Office attachments. Social engineering techniques were used to trick users into opening the files and enabling macros; however, campaigns have recently been detected that deliver the malware via weaponized virtual hard disk (VHD) files.
Security awareness training often focuses on teaching users to be careful when opening Office files and other file types commonly associated with malware distribution. The change to a more unusual file type could result in the file being opened, and VHD files are less likely to be identified as malicious by email security solutions.
An analysis of the extracted VHD files revealed a shortcut file that contained a PowerShell command line that executed a malicious script that ultimately delivered the Remcos RAT via a sophisticated multi-stage delivery method designed to evade security solutions. Once installed, the malware can log keystrokes, take screenshots, and exfiltrate data to its command-and-control server. The malware also has mass-mailer capabilities and can send copies of itself via email from an infected device. According to Check Point, the Remcos RAT rose to the 4th most prevalent malware threat in March 2024.
The constantly changing tactics for distributing malware mean network defenders need cybersecurity solutions that can adapt and detect zero-day threats. SpamTitan is an advanced email filtering service with AI and machine learning-driven threat detection which is capable of identifying and blocking novel phishing and malware distribution methods. The machine learning algorithm uses predictive technology to identify previously unseen attacks, emails are scanned using twin antivirus engines, and suspicious file types are sent to a next-generation sandbox for behavioral analysis, ensuring even previously unseen malware variants can be identified and blocked.
SpamTitan scans all inbound emails and also includes an outbound email filter to identify malicious emails that are sent from compromised email accounts and by malicious insiders. SpamTitan also has data loss protection capabilities, allowing IT teams to detect and block internal data loss. If your corporate email filter does not include advanced threat protection including AI-driven detection and sandboxing, or if you rely on Microsoft’s anti-spam and anti-phishing protection, sophisticated threats such as zero-day attacks are unlikely to be blocked and your business will be at risk.
Give the TitanHQ team a call today to find out more about SpamTitan. SpamTitan is delivered as a cloud-based anti-spam service that integrates seamlessly with Microsoft 365 to improve protection, or as a gateway solution for on-premises protection, which can be installed on existing hardware as a virtual anti-spam appliance.


