titanadmin - Page 11
by titanadmin | Mar 20, 2018 | Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News |
The cybersecurity threat level is at an all time high, according to a recently published threat report from McAfee. The AV solution provider has compiled a report from data collected over the final quarter of 2017 which shows the last three months of 2017 saw record numbers of new malware samples detected – 63.4 million samples. A level never before seen.
The soaring value of Bitcoin and other cryptocurrencies in the final quarter of 2017 fueled a massive rise in cryptocurrency hijacking and the use of cryptocurrency miners over other forms of malware that were favored in previous quarters. With Bitcoin valued at $19,000 in December and cryptocurrency mining hardware costing several thousand dollars, it is no surprise that so many threat actors chose to hijack other computers and steal money from cryptocurrency wallets.
Cryptocurrency miners were being used in spam email campaigns, disguised as mobile apps, and there was a massive rise in the hijacking of websites and loading cryptocurrency mining code.
While mining cryptocurrencies has proven to be highly profitable for cybercriminals, they did not abandon the use of other malware variants. The use of ransomware continues to increase, with spam email the primary method of delivery.
McAfee reports that there was 35% ransomware growth in Q4, and 59% growth in 2017. For the fourth consecutive quarter there has been an increase in new ransomware variants, with much of the increase due to the widespread use of Ransom:Win32/Genasom. There is unlikely to be a fall in use of ransomware any time soon.
The use of spam email to deliver malware and ransomware continues to grow, with two botnets – Necurs and Gamut – responsible for delivering 97% of all spam email in Q4, with the former now the most prevalent spamming botnet.
Botnets are also being developed to exploit IoT devices, which typically lack security and often have poor passwords. Infecting the devices allows massive botnets to be easily assembled for use in DDoS and DoS attacks.
Q4 was the fourth consecutive quarter where new malware samples have continued to increase, with total malware samples now just short of 700,000,000. New Mac malware also increased for the third consecutive quarter and there are now approximately 750,000 Mac malware variants, although there was a fall in new mobile malware samples from the 2-year high in Q3.
There was a rise in new Faceliker and macro malware, although the biggest increase was PowerShell malware. Q4 saw a massive jump in new PowerShell downloaders.
While the cybersecurity threat level continues to increase, and all industries are at risk, healthcare was the most targeted industry in 2017 by some distance. Healthcare may have been the third most targeted industry sector in 2016-2017, but the first three quarters of 2017 saw more than twice as many attacks on healthcare organizations than any other industry sector.
McAfee reports that there has been a 210% increase in cybersecurity incidents reported by healthcare organizations in 2017 compared to 2016, although there was some respite in Q4, which saw a 78% quarter over quarter decline in security incidents.
McAfee suggests it is poor security practices that have contributed to the rise in healthcare data breaches and cyberattacks. Many of the reported incidents could have been prevented if cybersecurity best practices had been followed.
by titanadmin | Mar 12, 2018 | Industry News, Internet Security, Network Security |
There have been several major cyberattacks on restaurants in recent months. Organized cybercriminals gangs are using specially crafted malware to silently steal credit card data from POS systems. Not only do the initial intrusions go undetected, the presence of the malware is often not detected for several months, during which time tens of thousands of credit card details are stolen.
Last month saw another large restaurant chain suffer a major breach of payment card data. The cyberattack on Applebee’s affects more than 160 of its RMH Franchise Holdings owned and operated restaurants across 15 states.
Customers who visited one of the RMH restaurants in Alabama, Arizona, Texas, Florida, Illinois, Indiana, Kansas, Kentucky, Ohio, Mississippi, Missouri, Nebraska, Oklohoma, Pennsylvania or Wyoming between November 2017 and January 2018 and paid for their meal on a credit or debit card have potentially had their card details stolen. Customers who paid using the self-pay tabletop devices were not affected, and neither were customers who paid online. The data breach was confined to RMH-operated restaurants. Other restaurants in the Applebee’s network were unaffected.
The data theft occurred as a result of malware on its POS system. The malware had been developed to capture data such as card numbers, expiry dates, CVV codes, and cardholder names. After recording the data, the information was exfiltrated to the attacker’s command and control server.
RMH reports that it has security systems in place to prevent cyberattacks and was able to contain the incident prior to discovery of malware on February 13, 2018. One a breach was discovered, RMH conducted a thorough investigation to identify the full extent of the breach and the individuals potentially impacted. A leading computer forensics firm was contracted to assist with the investigation and help mitigate of the attack. RHM has not disclosed how the malware was installed and nether the type of malware used in the attack.
The Applebee’s cyberattack is the latest in a string of cyberattacks on restaurants and retailers. In 2017 there were similar cyberattacks on restaurants throughout the United States. Arby’s fast food restaurants experienced a POS-malware related breach that affected many of its 1,000+ corporate stores. Chipotle Mexican Grill discovered malware had been installed on its POS system, with most of its stored affected over a 1-month period last spring.
Retailers are also major targets. Earlier this year, the retailer Forever21 discovered malware has been installed on its POS system. It took the retailer 7 months to identify the breach, during which time the credit and debit card details of many thousands of its customers were stolen.
Last year, many of the 750 Kmart stores were infected with POS malware – the second major credit card breach experienced by the chain in the past three years. Buckle Inc., was also attacked, with an undisclosed number of its stores affected. The malware infection remained on its system undetected for more than 5 months.
The breaches highlight the importance of implementing layered defenses to protect the entire attack surface, from spam email defenses to web filters, next generation firewalls, and advanced intrusion detection systems. It is also essential for retailers and restaurateurs to conduct regular vulnerability scans of the entire network to identify and address security flaws, with technical solutions implemented to constantly monitor POS systems for signs of compromise.
by titanadmin | Mar 9, 2018 | Internet Security, Network Security |
A massive campaign spreading the Dofoil Trojan has been detected by Microsoft. The campaign has already seen almost half a million PCs infected with the malware in just 12 hours. The Dofoil Trojan is otherwise known as Smoke Loader – a downloader that has been active for several years.
The Dofoil Trojan is a small application which once installed on a PC is capable of downloading other forms of malware. The Dofoil Trojan has been used in various campaigns since at least 2011 to install malware, with the latest campaign used to install cryptocurrency mining malware.
More than 400,000 Dofoil Trojan Infections Detected in Just 12 Hours
The alarm was raised on March 6 when Windows Defender detected around 80,000 instances of the Trojan on PCs with the number rising rapidly to well over 400,000 in the following 12 hours. Several variants of the Dofoil Trojan were being used in the campaign which was mostly targeting devices in Russia, Ukraine, and Turkey.
The cryptocurrency mining malware is being used to mine Electroneum coins on infected devices, although the malware can mine various different cryptocurrencies.
Detecting the malware can be difficult as it uses process hollowing to create a new instance of a legitimate Windows process for malicious purposes. In this case the malware is disguised as a Windows binary file to avoid detection – wuauclt.exe. Explorer.exe is used to create a copy of the malware in the Roaming AppData folder which is renamed ditereah.exe. The Windows registry is also altered to ensure persistence, modifying an existing entry to point to the malware copy. The malware communicates with its C2 server and is also capable of installing further malware variants onto an infected device.
While Microsoft was able to detect infections, what is not known at this stage is how the malware was installed on so many devices in such as short space of time. While the malware could potentially have been distributed by spam email, another means of distribution is suspected. Microsoft notes that in several cases the malware is believed to have been spread via torrent files, which are used in P2P file sharing, often to obtain pirated movies, music, and software.
Microsoft has only reported on the number of infections it has detected via Windows Defender. The company does not have visibility into devices that do not have the anti-malware software installed. The total number of infections is therefore likely to be far greater. The 400,000+ infections are likely to be just the tip of the iceberg.
Microsoft notes that its efforts to disrupt the operation did not just stop devices from mining cryptocurrencies. Infection with the Dofoil Trojan allows the attackers to download any number of additional malicious payloads including more dangerous malware variants and ransomware.
More than 50,000 Websites Discovered to Host Cryptocurrency Mining Malware
According to a recent Bad Packets report, more than 50,000 websites have been infected with cryptocurrency mining malware which runs via browsers whenever visitors are on a compromised website. The JavaScript-based malware uses the CPUs of visitors’ computers to generate cryptocurrencies.
While many of these sites have been hijacked and loaded with the malware without the knowledge of the site owner, many sites have the JavaScript added deliberately by site owners as a further method of making money from the websites.
These sites do not result in infection with malware. Typically, the only problems experienced by website visitors is a slowing down of their computers. However, in some cases, the malware has been configured to take full advantage of visitors’ computers and some hardware damage has been caused as a result.
Since it is difficult to determine which sites have been infected or are using cryptocurrency miners, the solution for users is to use a browser extension such as minerBlock to prevent the scripts from running. Users of the Opera browser need do nothing as the browser already blocks cryptocurrency mining scripts from running.
by titanadmin | Mar 6, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam Advice, Spam News, Spam Software |
Phishing attacks in healthcare are to be expected. Healthcare providers hold vast quantities of data on patients. Hospitals typically employ hundreds or thousands of members of staff, use many third-party vendors, and historically they have had relatively poor cybersecurity defenses compared to other industry sectors. That makes them an attractive target for phishers.
Phishing is a method of gaining access to sensitive information which typically involves a malicious actor sending an email to an employee in which they attempt to get that individual to reveal their login credentials. This is achieved using social engineering techniques to make the email recipient believe the email is a genuine. For instance, a security alert could inform the email recipient that an online account has been compromised and a password change is required. They are directed to a spoofed website where they are asked to login. The site is fake but looks genuine.
Credentials are entered and passed to the attacker who uses them to gain access to that individual’s account. Phishing can also involve malware. Emails attempt to convince the recipient to open a malware-infected attachment or download a malicious file from a compromised website.
Compliance with HIPAA Rules Helps to Prevent Phishing Attacks in Healthcare
HIPAA Rules require healthcare providers to implement administrative, technical, and physical safeguards to reduce the risk of cyberattacks and phishing. HIPAA only demands a minimum standard for data security be reached, although complying with HIPAA Rules can help to prevent phishing attacks in healthcare.
HIPAA is not technologically specific on the defenses that should be used to protect patient data. Healthcare providers can choose appropriate defenses based on the results of a risk analysis.
It is possible for healthcare organizations to be compliant with HIPAA Rules but still be vulnerable to phishing attacks. If healthcare providers are to block the majority of phishing attacks and truly secure patients’ data, they must go above and beyond the requirements of HIPAA.
HHS’ Office for Civil Rights Warns of Phishing Attacks in Healthcare
Recent phishing attacks in healthcare have prompted the HHS’ Office for Civil Rights to issue a warning about the risk from phishing.
Attacks are now highly sophisticated and can be hard to detect. The emails are often free from spelling mistakes, have near perfect grammar, include brand images and logos, and appear to have been sent from genuine domains. The reasons given for taking a specific course of action are perfectly plausible as is the need for urgent action.
OCR also highlights the rise in spear phishing attacks in healthcare. These attacks involve more targeted attempts to gain access to sensitive information and can be conducted on specific individuals or groups of individuals in an organization – The payroll or HR department for instance.
These attacks often see a CEO or superiors impersonated to add legitimacy to the attack. These attacks tend to require the opening of attachments or visiting links to download malware. Spear phishing emails are also used to request bank transfers or for sensitive information to be sent via email – W2-Forms of employees for instance. Many healthcare employees have been fooled by these scams.
Recent Phishing Attacks in Healthcare
Listed below are some of the recent examples of phishing attacks in healthcare. This is just a small selection of incidents that have resulted in healthcare records being exposed or stolen. The reality is that many data breaches start with a phishing email. Security awareness training company Cofense suggests that as many as 91% of data breaches have their root in a phishing campaign.
November 2017: 1,670 patients of Forrest General Hospital have their PHI exposed following a phishing attack on business associate HORNE.
October 2017: Henry Ford Health System discovers several email accounts were compromised as a result of employees responding to phishing emails. The PHI of 18,470 patients may have been stolen.
September 2017: Employees of UPMC Susquehanna responded to phishing emails with the attackers able to gain access to the PHI of 1,200 patients.
September 2017: A phishing attack on Wisconsin-based Network Health resulted in the PHI of approximately 51,000 patients being exposed.
August 2017: Chase Brexton Health Care in Maryland experienced a phishing attack that saw several email accounts compromised along with the PHI of 16,000 patients.
July 2017: The Medical College of Wisconsin experienced a phishing attack that allowed attackers to gain access to email accounts and the PHI of 9,500 patients.
July 2017: RiverMend Health employees responded to phishing emails and their accounts were accessed by the attackers. The PHI of 1,200 patients was potentially viewed or stolen.
June 2017: A phishing attack on Elderplan Inc., saw several email accounts compromised along with the PHI of 22,000 individuals.
June 2017: MJHS Home Care experienced a phishing attack that saw email access gained by an unauthorized individual. The compromised email accounts contained the PHI of 6,000 patients.
Staff Training and Anti-Phishing Technology
HIPAA does not specifically mention spam filters, but since phishing is used to target employees via email, spam filtering can be considered essential. By filtering out the majority of spam and malicious messages there is less potential for an employee to click on a malicious link or open a malware infected email attachment.
SpamTitan is a cloud-based anti-spam service that blocks more than 99.9% of spam emails from being delivered to inboxes and has a 0.03% false positive rate. Dual antivirus engines (Bitdefender/ClamAV) ensure malicious email attachments are blocked.
Healthcare employees are the last line of defense, so it is important for them to be able to recognize email threats and anti-phishing training is a requirement of HIPAA. In July 2017, OCR issued advice to healthcare organizations on anti-phishing training in its cybersecurity newsletter.
OCR also recommends using multi-factor authentication to ensure email accounts are not compromised when a password is guessed or stolen. Software and operating systems must be kept up to date and fully patched to prevent vulnerabilities from being exploited, and anti-virus and anti-malware solutions should be deployed to prevent infection. Regular backups can also prevent data loss in the event of a malware or ransomware infection.
by titanadmin | Mar 5, 2018 | Industry News, Spam News, Spam Software |
Titan HQ has announced from March 5, 2018 all new customers signing up to use the SpamTitan cloud-based anti-spam service will benefit from leading antivirus and anti-malware protection from Bitdefender. All existing customers will similarly be protected by Bitdefender, although first they will need to upgrade to SpamTitan v7.00. v7.00 was released on March 5.
The primary AV engine used in previous versions of SpamTitan was provided by Kaspersky Lab, with ClamAV used as a secondary AV engine. SpamTitan v7.00 will also incorporate ClamAV as a secondary AV engine. Kaspersky AV will no longer be supported on SpamTitan suite of products from May 1, 2018.
The change to the new primary AV engine is due to a growing strategic relationship with Bitdefender. Further collaboration with the Romanian cybersecurity firm is planned for the future. Customers already using SpamTitan are encouraged to upgrade to the latest version of the product as soon as possible as several other updates have been incorporated into the latest version, including patches for recently discovered vulnerabilities in ClamAV.
These include the use-after-free vulnerability CVE-2017-12374; buffer overflow vulnerabilities CVE-2017-12375 and CVE-2017-12376; Mew Packet Heap Overflow vulnerability CVE-2017-12377; Buffer Overflow in messageAddArgument vulnerability CVE-2017-12379; and Null Dereference vulnerability CVE-2017-12380. TitanHQ has also included patches for openssl, openssh, php, and wget and updates have been included to resolve potential denial of service attacks.
Customers already on v6.x of the platform who have enabled prefetch of system updates will find the latest patches in the list of available updates on the System updates page. If this option is disabled, they should use the ‘Check for Updates Now’ option in the user interface.
Customers using SpamTitan v4 and v5 have been advised that support for both versions of SpamTitan will cease on May 1, 2018. An upgrade to version 7.00 will therefore be required before the deadline. It is important to note that the update process requires v4/5 to first be upgraded to v6 before installing SpamTitan v7.00. Upgrading to the new version will not change the existing configuration of the product.
Customers should allow 10-20 minutes for the installation of the new version and should read all product notes before installation.
by titanadmin | Feb 28, 2018 | Email Scams, Phishing & Email Spam, Spam News |
This month Adobe patched a critical use-after-free vulnerability in Adobe Flash Player that affects Windows 10, Mac, Chrome, and Linux operating systems. If exploited, an attacker can gain full control of an unpatched device.
Adobe reports that an exploit for the vulnerability – tracked as CVE-2018-4878 – has been identified and is being used in attacks on Windows 10 devices.
At the time that the patch was issued, only a limited number of attacks had been detected. However, researchers at Morphisec report the vulnerability is now being exploited in a massive spam email campaign that is targeting users in the United Kingdom and United States. While the spam campaign was relatively short-lived, large quantities of emails were sent and further spam campaigns can be expected.
The emails include a shortlink which, if clicked, downloads a Word document from a recently registered domain. Opening the document sees a command prompt opened that is injected with Shellcode that connects to the attackers’ C2. Once a connection is made, a DLL file is downloaded and executed using regsvr32. According to Morphisec this bypasses whitelisting solutions. A SWF Flash file is then extracted which also had a low detection rate and the vulnerability is exploited.
What makes the attack particularly dangerous is the poor detection rate by AV solutions. In a recent blog post Morphisec said in its tests, only 1/67 AV firms on VirusTotal identified the email attachment as malicious.
The shortened goo.gl URLs used in the emails are difficult to detect as malicious and look similar to those used in legitimate email campaigns. The number of links being opened also corresponds with standard email campaigns, with high numbers of clickthroughs as the emails hit inboxes. The figures show that many email recipients have been fooled by the campaign.
This email campaign shows why it is so important for patches to be applied promptly, especially when there are active exploits for a vulnerability in the wild. This is just one campaign, and there are likely to be many conducted using the Flash exploit.
However, despite the risks from slow patching, many companies take weeks, months, or in some cases years before patches are applied, leaving them extremely vulnerable to attack.
by titanadmin | Feb 26, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News |
A Colorado Department of Transportation ransomware attack on February 21, 2018 affected at least 21 computers preventing files from being accessed by employees. A prompt response to the ransomware attack limited the harm caused, although to prevent the spread of the ransomware more than 2,000 computers were shut down.
The attack has already caused considerable disruption, which is ongoing as the cleanup operation continues.
The DOT says it received a ransom demand which would need to be paid in order to obtain the keys to unlock encrypted files, but that the DOT has no intention of paying any money to the attackers. Instead the firm has called in an external cybersecurity firm (McAfee) to restore data on the affected workstations and ensure all devices are clean and protected from infection. All encrypted files will be recovered from backups.
Fortunately, the ransomware attack was limited to certain endpoints. Other computer systems that are used with surveillance cameras and traffic alerts were not affected.
The Colorado Department of Transportation ransomware attack is one of several high-profile attacks involving SamSam ransomware to have been reported this year. Hancock Health Hospital in Indiana was one notable victim. The hospital was issued with a ransom demand and paid the attackers for the keys to unlock the encryption, even though backups could have been used to recover files. A Bitcoin payment worth approximately $55,000 is believed to have been paid. The payment was believed to be considerably less than the cost of disruption while files were recovered from backups.
Another Indiana hospital – Adams Memorial Hospital was also attacked with a variant of SamSam ransomware, and Allscripts – an electronic health record provider – also suffered an attack that took down some of its web services.
SamSam ransomware first surfaced in 2015, and while some antivirus and antimalware solutions can detect the malware, the attackers continue to release new variants that are much better at evading detection.
Bleeping Computer reported on January 19 that one of the Bitcoin wallets used by the gang involved in SamSam ransomware campaign had already made approximately $300,000 from ransom payments, although that figure will almost certainly be higher since multiple Bitcoin wallets are believed to be used and the campaign is ongoing.
On February 15, Secureworks reported that the profits from the attacks had increased to at least $350,000, with the firm attributing the attacks to a hacking group called Gold Lowell.
It is unclear how the Colorado Department of Transportation ransomware attack occurred. Some sources report that the attack involved phishing emails, although Gold Lowell’s modus operandi is leveraging vulnerabilities in Remote Desktop Protocol (RDP) services.
With the campaign ongoing, all businesses should be alert to the threat from phishing and RDP attacks. Spam filters, such as TitanHQ’s cloud-based anti-spam service, are essential as is anti-phishing training for employees. If RDP is necessary, strong passwords should be set and controls implemented to reduce the potential for brute force attacks. Rate limiting on login attempts for example. It is also important to make sure that multiple data backups are performed to ensure files can be recovered in the event of an attack.
by titanadmin | Feb 23, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News |
A new report has been released that shows there has been a massive rise in the global cost of cybercrime, highlighting the seriousness of the threat from hackers and scammers. 2017 global cybercrime costs exceeded $600 billion, according to the McAfee report. That represents a 20% increase since 2014, when the global cybercrime costs were calculated to be around $500 billion. The current global cybercrime costs equate to 0.8% of global GDP.
The report shows that in spite of increases in cybersecurity spending, hackers and scammers are still managing to breach organizations’ defenses and gain access to sensitive data, login credentials, corporate bank accounts, and intellectual property.
Accurately Determining the Global Cost of Cybercrime
Any calculation of global cybercrime costs involves some margin of error, as the figures cannot be totally based on reported losses by businesses. Many companies do not disclose details of data breaches, and even fewer publish information of the financial impact of cyberattacks. When details about financial losses are published, typically only a fraction of the losses are reported. In many cases the losses are not known until many years after the event. It is therefore difficult to obtain a true picture of the losses due to cybercrime because of the shortage of data.
To try to gain an accurate picture of the total cost of cybercrime, McAfee had to turn to the same modelling techniques used by government agencies to determine the costs of criminal activities such as drug trafficking, prostitution, maritime piracy, and organizational crime groups.
McAfee is not the only company to make these predictions. Compared to some reports the figures from McAfee seem quite conservative. The true cost could be considerably higher.
Factors Contributing to the Increase in Losses
McAfee reports that several factors have contributed to the large increase in cybercrime costs over the past few years. The growth in popularity of ransomware has played a part. Ransomware has proved to be a particularly plump cash cow, allowing cybercriminals to rake in millions by extorting companies. The anonymity of cryptocurrencies has helped these cybercriminal gangs obtain payments without detection, while the use of TOR has helped the gangs stay under the radar of law enforcement agencies.
Ransomware-as-a-service has also boosted profits for cybercriminals. The increase in the number of individuals conducting attacks has made it possible to increase the scale of operations and distribute the malicious code more effectively. State-sponsored hacks have also increased, including attacks aimed at sabotaging businesses and critical infrastructure as well as major heists that have seen millions of dollars stolen.
McAfee cites research showing around 300,000 new malware samples are now being identified on a daily basis, while data breaches are exposing a staggering 780,000 records a day.
Personal records can sell for big bucks on darknet forums; however, one of the biggest costs is the theft of intellectual property, which McAfee estimates has resulted in at least 25% of the annual losses to cybercrime. When patented processes are obtained, the benefits of millions in research and development is lost and companies can lose their competitive advantage.
One thing is clear from the report. With global cybercrime costs rising, and the sophistication and frequency of attacks increasing, companies have little alternative than to invest more in cybersecurity and develop more sophisticated defenses.
by titanadmin | Feb 22, 2018 | Email Scams, Internet Security, Network Security, Phishing & Email Spam, Spam Advice, Spam News, Spam Software, Website Filtering |
Cybercriminal gangs operating in Nigeria have been discovered to be using phishing kits in a highly sophisticated phishing campaign that has seen millions of dollars obtained from big businesses.
The scammers are regularly fooling employees into revealing their email login credentials – The first stage of the complex scam. The ultimate goal of the attackers is to gain access to corporate bank accounts and convince accounts department employees to make sizeable transfers to their accounts.
According to research conducted by IBM, these scams have been highly successful. Fortune 500 companies are being targeted and losses have been estimated to be of the order of several million dollars.
These scams take time to pull off and considerable effort is required on the part of the scammers. However, the potential rewards are worth the effort. Bank transfers of tens or hundreds of thousands of dollars can be made and business email accounts can be plundered.
A Sophisticated Multi-Stage Phishing Scam
In order to pull off the scam, the attackers must first gain access to at least one corporate email account. Access is gained using phishing emails, with social engineering tactics used to convince employees to click on a malicious link. Those links direct the email recipients to malicious DocuSign login pages where credentials are harvested. These malicious pages have been created on multiple websites.
According to IBM, the gang behind this campaign has created more than 100 of these pages, many of which have been loaded onto genuine websites that have been compromised by the attackers.
Once access to one email account is gained, it is easy to obtain email addresses from the contact list to fool other employees. When an email account is accessed, the attackers search the account for messages involving accounts and payments. The attackers then send emails carrying on conversations between staff members, inserting themselves into conversations and continuing active discussions.
“The attackers typically took a week between the point they gained initial access to a user’s email account and the time they started setting up the infrastructure to prepare a credible ruse,” said IBM’s X-Force researchers. “During this time, they likely conducted extensive research on the target’s organizational structure, specifically focusing on the finance department’s processes and vendors.”
By setting up email rules and filters, it is possible to block genuine conversations between the employees that could uncover the scam. By doing this, all conversations take place between a specific individual and the attacker.
This method of attack allows the attackers to gain access to banking credentials and send highly convincing emails requesting transfers to their accounts. Targeted employees are unlikely to be unaware that they are not emailing a legitimate contact.
This is a manual, labor-intensive scam involving no malware. That has the advantage of allowing the attackers to evade anti-malware technologies.
How to Protect Against These Sophisticated Email Scams
While these scams are complex, they start with a simple phishing email to gain access to a corporate email account. Once access to an email account has been gained, stopping the scam becomes much harder. The easiest time to prevent such an attack is at the initial stage, by preventing the phishing emails from reaching the inboxes of employees and training employees how to identify phishing emails.
That requires an advanced spam filtering solution that can identify the common signatures of spam and scam emails. By setting aggressive filtering policies, the vast majority of spam emails will be captured and quarantined. With the SpamTitan cloud-based anti-spam service, that equates to more than 99.9% of all spam and malicious emails. SpamTitan also has a particularly low false positive rate – less than 0.03% – ensuring genuine emails are still delivered.
No spam solution can be 100% effective, so it is also important to prepare the workforce and train staff how to identify malicious emails. Security awareness and anti-phishing training allows organizations to create a ‘human firewall’ to complement technical solutions.
Spear phishing – highly targeted email attacks – are harder to block, but it is possible to implement solutions to prevent scams such as this from resulting in credentials being obtained. In this campaign, links are sent in emails. By implementing a web filtering solution, those links can be blocked. In tandem with a spam filter, organizations with a security aware workforce will be well protected from phishing attacks.
Further, the use of two-factor authentication is an important security measure to implement. This will prevent attackers from using an unknown device to access an email account.
For further information on web filters and spam filters, and the benefits of installing them at your organization, contact the TitanHQ team today and take the first step toward improving your defenses against sophisticated phishing scams.
by titanadmin | Feb 21, 2018 | Email Scams, Network Security, Phishing & Email Spam, Spam Software |
A new IRS-themed rapid ransomware email scam has been detected that uses the threat of significant financial penalties for late tax payments to fool victims into installing ransomware.
Tax season is well underway and cybercriminals have been increasing their efforts to obtain tax credentials to file fraudulent tax returns in the names of their victims. Businesses are the prime targets, as a successful scam can see the tax credentials of hundreds or thousands of employees obtained from a single response to an scam email.
However, it is not only tax fraudsters that are taking advantage of tax season. Ransomware attacks are also likely, as has been highlighted by a recently uncovered email scam that impersonates the IRS.
The purpose of this scam is to install Rapid ransomware. Rapid ransomware is a relatively new ransomware variant first detected in January 2018. In contrast to many ransomware variants that encrypt files and then terminate, rapid ransomware remains active after encryption and will encrypt any further files that are created on the infected device.
In addition to encrypting files, the ransomware deletes Windows shadow volume copies and disables automatic repair to hamper any attempts to restore files without paying the ransom. There is currently no decryptor for Rapid ransomware. Recovery will depend on backups being available or the ransom demand must be paid.
IRS Spoofed to Spread Rapid Ransomware
The Rapid ransomware email scam is similar to many other scams conducted during tax season. The emails are well written and plausible. There is urgency to encourage rapid action and a threat of financial penalties if the emails are ignored.
The emails have the subject line: ‘Please Note – IRS Urgent Message 164’ and contain a zipped notification attachment which email recipients are required to open to obtain further information.
In the body of the email, the recipient is led to believe they have significant tax arrears related to a property. The recipient is told that no action is taken by the IRS when tax arrears are cleared within 4-6 months of their due date, but since the recipient’s tax is 7 months out of date they are liable for a fine. They are told that if they do not respond to the email within one day and attempt to rectify the situation, ‘significant charges and fines may apply’. They are also told to open and study the attached document. The zip file contains a Word file containing a macro. If allowed to run, the macro downloads a PowerShell file, which in turn downloads Rapid ransomware.
Security aware individuals should be able to identify signs that the email is not genuine. First, the email is addressed ‘Dear Customer.’ In the event of the IRS contacting an individual about tax arrears, it would be likely that the email would be addressed using the individual’s name. However, such a situation would not occur. The IRS has confirmed in numerous warnings about phishing emails that it does not initiate contact about tax arrears via email. Further, tax arrears are serious, but not so serious that a response of 1 day would be given for a response.
The scammers behind this campaign have made some glaring mistakes in their campaign. The email address spoofed has the domain nottscc.gov.uk. While the email address looks official, it relates to Nottinghamshire County Council in the UK and the IRS is the American tax agency. However, many devices do not show the full domain so this may not be noticed. Another major error is the use of German language in the Word document, including instructions for enabling the macro.
Scam Highlights Need for Spam Filters and Security Awareness Training
Due to the errors made by the scammers, in particular the use of German and a UK local government email address – this email scam should be easily detected by employees and consumers, but such mistakes are not always made. The email is plausible, and otherwise it would be likely that many individuals would be fooled by such a scam.
For businesses, these scams can prove incredibly costly. In this case, there is no set ransom payment. Victims need to email the scammers to find out how to pay the ransom and how much is being charged. If the emails come from a business domain, the ransom payment would likely be increased. Further, ransomware can spread laterally within a network and result in file encryption on multiple endpoints and servers. With ransoms typically charged for each infected device, the costs can be considerable.
This Rapid ransomware email scam highlights the need for spam protections to be put in place to prevent malicious emails from being delivered. With SpamTitan implemented, more than 99.9% of spam email is blocked, preventing employees from having their phishing email identification skills tested.
It is also important to provide security awareness training to employees to teach them the skills they need to identify scams such as this. Not all email scams will be as easy to detect as this one. Training goes a long way toward ensuring that when emails slip past security defenses they are quickly identified by the workforce.
by titanadmin | Feb 19, 2018 | Email Scams, Internet Security, Network Security, Phishing & Email Spam, Spam News, Spam Software |
Saturn ransomware is a new threat recently identified by security researchers at MalwareHunterTeam. Saturn ransomware takes its name from the extension added to encrypted files (.saturn).
While it is easy to determine the ransomware variant used in an attack, this will be of little use to victims. There is currently no decryptor available to recover files.
A single infection can rapidly spread laterally, encrypting files on an infected device as well as network shares. Recovering files from backups may prove difficult. Saturn ransomware searches for and deletes shadow volume copies, clears the Windows backup catalog, and also disables Windows startup repair.
If no viable backup exists, the victim must pay a ransom payment in bitcoin of approximately $300 per infected device. If payment is not made within 7 days of infection, the ransom payment doubles.
As with many new ransomware variants, attacks can come from all angles. That is because the new ransomware variant is being offered to affiliates as ransomware-as-a-service.
Ransomware-as-a-service allows the malware developers to maximize the number of infections – and profits – by recruiting a large team of distributors to send spam emails, load the ransomware onto malicious websites, and install the malicious software by taking advantage of poor security defenses. In exchange for their efforts, affiliates are given a percentage of the ransom payments that are received.
The developers of Saturn ransomware have made it as easy as possible for affiliates. A portal has been developed that allows affiliates to obtain copies of the ransomware binaryeither embedded in exe files or Office, PDF files or other documents. To tempt individuals into using this ransomware variant instead of other RaaS offerings, the developers are offering a large percentage of the ransom payments to affiliates – 70%.
The ease of running campaigns together with the high potential rewards for infection means many affiliates are likely to start using the new ransomware variant in attacks. The new malware is already being offered on various darknet forums.
How to Block Saturn Ransomware Attacks
Spam email is the easiest way of spreading ransomware. Massive spam campaigns require little skill and there is no shortage of email addresses for sale on the dark web. We can therefore expect this new ransomware variant to be widely distributed over the coming weeks.
With spam email likely to be the main vector of attack, one of the best defenses to deploy to prevent infection is to use anti spam software such as SpamTitan. SpamTitan blocks more than 99.9% of spam email. With SpamTitan in place, emails can be blocked and will not reach end users inboxes.
However, no single defense can provide total protection from ransomware attacks. Layered defenses are required. Antivirus and antimalware solutions should be used, although signature and heuristics-based defenses will not provide total protection. Businesses should also use a technology that identifies changes to files to ensure that if infection occurs, rapid action can be taken to limit the spread of the ransomware.
Multiple copies of files should also be made to ensure that should the unthinkable happen, data will not be lost. Businesses should make at least three backups, stored on two different media, with at least one copy stored securely off-site. Good patch management policies are also required to prevent vulnerabilities from being leveraged to install the ransomware.
Technical defenses are essential, but don’t forget the human element. Ransomware spread via spam email requires some user interaction – the opening of an email attachment or the clicking of a link. Security awareness training and phishing email simulations are now a necessity to reduce user susceptibility to email-based attacks.
by titanadmin | Feb 16, 2018 | Email Scams, Network Security, Phishing & Email Spam, Spam Advice, Spam Software |
A new malware campaign has been detected that uses Microsoft Word without macros. Opening a Word document sent via email will not generate the usual warnings that macros must be enabled.
Employees may have been warned to be wary of any emails containing attachments, and never to enable macros on documents received via email. However, the use of Microsoft Word without macros means that even opening email attachments can see malware downloaded, if patches have not been applied.
The multi-stage infection process uses the CVE-2017-11822 Word vulnerability to install an information stealer. CVE-2017-11822 was patched by Microsoft last year, although companies that have not patched their systems recently will be vulnerable to this attack.
CVE-2017-11822 is a vulnerability in Office Equation Editor. The bug has been present in Microsoft Office for the past 17 years. Last year, Microsoft rated the code execution vulnerability as important rather than critical, but many security professionals disagreed and claimed the vulnerability was very dangerous as the bug could be exploited to run arbitrary code and the vulnerability was present in all Office versions.
Microsoft Equation Editor is an application that allows the insertion and editing of complex equations in Office documents as OLE items. Last year, security researchers were able to exploit the vulnerability to run a sequence of commands, including the downloading of files from the Internet. This campaign similarly triggers the downloading of a document – a Rich Text File (RTF) via an OLE object embedded in the Word document.
The OLE object opens the RTF file which uses the vulnerability to run a MSHTA command line, which downloads and runs an HTA file containing a VBScript. The VBScript unpacks a PowerShell script, which in turn downloads and runs the information-stealing malware. The purpose of the malware is to steal passwords from web browsers, email accounts and FTP servers.
The email campaign has been developed to target businesses. So far, four email templates have been detected by SpiderLabs researchers, although more will almost certainly be used over the coming days and weeks.
The four emails intercepted by have the subject lines:
- TNT Statement of Account
- Request for Quotation (RFQ)
- Telex Transfer Notification
- Swift Copy for Balance Payment
While a patch was released last year to address the vulnerability, Microsoft has taken further steps this Patch Tuesday by removing some of the functionality of Microsoft Equation Editor to prevent CVE-2017-11882 from being exploited.
Businesses can mitigate this attack in three main ways:
- Ensuring Office installations and operating systems are kept patched and 100% up to date
- Use of anti spam software to prevent malicious emails from being delivered to end users
- Training end users on cybersecurity best practices and the danger of opening Office documents from unknown individuals. Consider sending a warning about this campaign and the email subject lines being used
by titanadmin | Feb 14, 2018 | Email Scams, Internet Security, Network Security, Phishing & Email Spam, Spam News, Spam Software |
Every February, Valentine’s day email scams are to be expected and this year has been no different. On Monday, a massive new phishing campaign was launched. The Necurs botnet was used to deliver millions upon millions of dating, romance and Valentine’s themed emails.
Dating and Valentine’s Day Email Scams Pose Problems for Businesses
Dating scams increased significantly in January and continued in February. You have probably seen the emails already in one of your inboxes.
The emails appear to have been sent by Russian women desperate to find love. Unsolicited emails from attractive women complete with suggestive pictures and messages claiming the recipient is particularly attractive are certain to be spam, yet the emails are effective. The FBI’s figures indicate around $230 million is lost to these scams alone each year. In 2016, the FBI received around 15,000 complaints about financial losses as a result of dating and romance scams.
There were two major peaks in spam email volume between January 15 and 17 and January 29 and February 2 when around 35 million dating spam messages were delivered via the Necurs botnet. Over 230 million messages were sent in a two-week period in January. The aim of the campaign is to obtain credit card details, payments to cover flights to bring the women over to the US, but in many cases the purpose is to fool the email recipient into downloading malware.
Cybercriminals use all manner of tactics to entice users to click. Another effective technique, highlighted by security awareness training firms KnowBe4 and PhishMe, is the use of eCards, especially on Valentine’s Day. Links are sent that appear to be from legitimate eCard sites that require users to click the link to view a Valentine’s day card from a secret admirer. The purpose is to deliver malware.
Valentine’s day email scams this year also include messages alerting the recipient about the failed delivery of flowers from Interflora and email attachments claiming to be delivery receipts.
It is the likelihood of these emails being opened that makes defending against them a major headache for businesses. One single click is all it takes for malware to be installed, and since many malware variants can rapidly spread laterally, one click could be all it takes to compromise an entire network.
The Winter Olympics Scams Continue
This month has also seen plenty of Winter Olympics phishing campaigns conducted. Cybercriminals have been taking advantage of interest in the games to get their emails opened. Malicious links are used to direct users to websites that claim to have up to date news on the events, the competitors, fake news, and the results of events.
The reality is these links direct users to phishing websites, exploit kits, and sites where malware is silently downloaded. With workers unable to watch the sports live at work, these malicious emails stand a high chance of being opened.
With Valentine’s day and the Winter Olympics, February has been a busy month for scammers and with the Pyeongchang Winter Olympics still in full flow, businesses need to be on high alert.
Fortunately, there is one technology in particular that can help businesses counter these email-based threats. An advanced spam filtering solution: The most effective defense against email-based attacks. An advanced spam filter such as SpamTitan blocks more than 99.9% of spam emails, 100% of known malware, and ensures that phishing and other malicious emails do not reach inboxes.
To find out more about SpamTitan – the best spam filter for business use – contact the TitanHQ team today.
by titanadmin | Feb 12, 2018 | Industry News, Internet Security |
Last week news broke that government supercomputers in Russia had been turned into cryptocurrency miners, now comes news that many UK government websites have been infected with cryptocurrency mining code.
More than 4,200 Websites Infected with Cryptocurrency Mining Code
The latest attack affects government websites around the globe, with more than 4,200 websites turning visitors’ computers into cryptocurrency miners.
The attack involved a popular website plugin called Browsealoud. Browsealoud is used to convert written website content into audio for the blind and partially sighted. The browser plugin was compromised by hackers who altered the source code of the plugin to include cryptocurrency mining code. By altering the plugin, the malicious code runs every time a site user visits a webpage that offers the audio function using the Browsealoud plugin.
When a visitor arrived at such as webpage, the code ran and turned that user’s computer into a cryptocurrency miner, using the computer’s processing power to mine Monero. Mining is the term given to verifying cryptocurrency transfers. Mining requires a computer to solve a complex problem. Once that problem is solved, the miner is rewarded with a small payment. In this case, the individual(s) who altered the code.
Using one computer to mine cryptocurrency will only generate a small return. However, by hijacking a browser plugin on a website that is visited by many thousands of individuals, the potential returns are considerable. The processing power of millions of computers can be harnessed.
Browsealoud was developed by the British company Texthelp. According to its website, its plugin has been installed on 4,275 domains. In the United Kingdom, many government websites use the plugin, including the Financial Ombudsman Service, the Information Commissioner’s Office, the Student Loans Company, many National Health Service (NHS) websites, and local government websites including the .gov.uk sites used by Camden, Croydon, Manchester, and Newham to name but a few. Many federal and state government websites in the US have turned their visitors’ devices into cryptocurrency miners, and it is the same story in Australia, Ireland, Sweden, and beyond.
The Browsealoud plugin is understood to have been infected with cryptocurrency mining code at some point between 0300 and 1145 UTC on February 11, 2018. The code was only active for a few hours before the change was identified and Texthelp disabled the plugin.
The mining only took place while a visitor was on a webpage that used the Browsealoud plugin. As soon as the tab or browser was closed, the mining stopped. Visiting the website that had been infected with cryptocurrency mining code via the plugin would not result in a malware infection. The only noticeable effect for any visitors to the websites would have been a slowing down of their computers or the fan starting as their computer started going into overdrive.
This incident has however made it quite clear to government agencies that their websites are not secure and using third party plugins on their sites to improve services for website users introduces risk.
How to Secure Your Website Against JavaScript-Based Supply-Chain Attacks
These supply-chain attacks exploit a trusted relationship between the website owner and a third-party software/plugin supplier and the benefits for cybercriminals are clear. All it takes is for one plugin to be hacked to have malicious code run on many thousands of websites, thus targeting millions of website visitors. In this case, the damage caused was minimal, but the attack could have been much worse. The goal on this occasion was to mine cryptocurrency. The attackers could easily have inserted much more malicious code and attempted to steal login credentials.
In this case, the plugin required websites to use JavaScript in their content for the plugin to work. Wordfence has recently published details of a simple script that can be included on websites that use JavaScript from third parties that will prevent code from running if it has been modified from its original form.
Protecting sites requires the use of a security feature called Subresource Integrity (SRI). Websites that include JavaScript from an external source using the <SCRIPT> tag can include an integrity attribute to prevent modified JavaScript from running. An SRI hash for a website can be generated on here.
One problem with using this approach is any modification to the code will prevent the JavaScript from running, which means the JavaScript will also be blocked when legitimate updates are made by the plugin developer.
That means a new hash is required if the vendor does not include a version number in their updated code. However, it will ensure that attacks such as this, or worse attacks with much more malicious code, will be blocked.
by titanadmin | Feb 8, 2018 | Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam Software, Website Filtering |
Following a slew of cyber extortion attacks on schools, the FBI and the Department of Education’s Office of the Inspector General have issued a warning. Schools need to be alert to the threat of cyber extortion and must take steps to mitigate risk by addressing vulnerabilities, developing appropriate policies and procedures, and using technologies to secure their networks.
K12 schools and other educational institutions are an attractive target for cybercriminals. They hold large quantities of valuable data – The types of data that can be used to commit identity theft and tax fraud. Further, in education, security defenses are typically of a much lower standard than in other industries. Poor defenses and large volumes of valuable data mean cyberattacks are inevitable.
The warning comes after several cyber extortion attacks on schools by a group of international hackers known collectively as TheDarkOverlord. The hacking group has conducted numerous attacks on the healthcare industry the public school system since April 2016.
The modus operandi of the hacking group is to search for vulnerabilities that can be easily exploited to gain access to internal networks. Once network access is gained, sensitive data is identified and exfiltrated. A ransom demand is then issued along with the threat to publish the data if payment is not made. The hacking group does not make empty threats. Several organizations that have failed to pay have seen their data dumped online. Recent attacks have also included threats of violence against staff and students.
Access to networks is typically gained by exploiting vulnerabilities such as weak passwords, poor network security, unpatched software, and misconfigured databases and cloud storage services.
The FBI reports that the hacking group has conducted at least 69 cyber extortion attacks on schools, healthcare organizations, and businesses and has stolen more that 100 million records containing personally identifiable information. More than 200,000 of those records have been released online after ransom demands were ignored. More than 7,000 students have had their PII exposed by the hackers.
The escalation of the threats to include violence have caused panic and some schools have been temporarily closed as a result. Sensitive data has been released which has placed staff and students at risk of financial losses due to fraud. The FBI recommends not paying any ransom demand as it just encourages further criminal activity. What schools must do is take steps to mitigate risk and make it harder for their institution to be attacked. By doing so, cybercriminals are likely to continue their search for organizations that are easier to attack.
Ransomware and DDoS Attacks are Rife
TDO is not the only criminal group conducting cyber extortion attacks on schools, and these direct attacks are not the only way access to school networks is gained.
The past two years have seen a massive rise in the use of ransomware on schools. Ransomware attacks are often indiscriminate, taking advantage of vulnerabilities in human firewalls: A lack of security awareness of staff and students. These attacks commonly involve email, with malicious attachments and links used to deliver the ransomware payload.
Ransomware is malicious code that is used to search for stored files and encrypt them to prevent access. With files encrypted, organizations must either restore files from backups or pay the ransom demand to obtain the key to unlock the encryption. Since the code can also encrypt backup files, many organizations have had no alternative other than paying the ransom, since data loss is not an option.
Other cyber extortion attacks on schools do not involve data theft. DoS and DDoS attacks bombard servers with thousands or millions of requests preventing access and often damaging hardware. Cybercriminal gangs use mafia-style tactics to extort money, threatening to conduct DoS/DDoS attacks unless payment is made. Alternatively, they may conduct the attacks and demand payment to stop the attack.
The rise in cyber extortion attacks on schools means action must be taken to secure networks. A successful attack often results in educational institutions suffering major losses. The ransom payment is only a small part of the total cost. Removing ransomware, rebuilding systems, and protecting individuals whose sensitive data has been exposed can cost hundreds of thousands of dollars.
How to Protect Against Cyber Extortion Attacks on Schools
Schools and other educational institutions can develop policies and procedures and use technologies to deter cybercriminals and improve network and email security. By adhering to IT best practices and adopted a layered approach to security, it is possible to mount a robust defense and prevent cyber extortion attacks on schools.
Educational institutions should:
Implement strong passwords: Weak passwords can easily be cracked using brute force methods. Set strong passwords (Upper/lower case letters, numbers, and special characters or long 15+ digit passphrases) and use rate limiting to block access attempts after a set number of failures. Never reuse passwords for multiple accounts.
Patch promptly: Vulnerabilities in software and operating systems can easily be exploited to gain access to networks. Develop good patch management policies and ensure all software and operating systems are updated promptly.
Implement an advanced spam filter: Phishing and spam emails are commonly used to deliver ransomware and obtain login credentials. Do not rely on the spam filters of email service providers. Implement separate, advanced anti spam software or a cloud-based filtering service to block email-based threats and prevent them from reaching inboxes.
Provide security awareness training: Cybersecurity should be taught. Staff and students should be made aware of email and web-based threats and told how to identify malicious emails and potential web-based threats.
Implement a web filter: A web filter is necessary for CIPA compliance to protect students from harm caused by viewing obscene images online. A web filter is also an important cybersecurity defense that can block malware and ransomware and stop staff and students from visiting phishing websites. Web filters protect staff and students at school, but also protect devices that are taken home.
Secure remote desktop/access services: Conduct audits to determine which devices have remote access enabled. If remote access is not necessary, ensure it is disabled. If the services cannot be disabled, ensure they are secured. Use Secure Sockets Layer (SSL) Transport Layer Security for server authentication, ensure sessions are encrypted, and use strong passwords. Whitelist access is strongly recommended to ensure only authorized devices can connect.
Use two-factor authentication: Use two-factor authentication on all accounts to prevent access if a password is used on an unfamiliar device.
Limit administrator accounts: Administrator accounts should be limited. When administrator access is not required, log out from those accounts and use an account with fewer privileges.
Segment your network: Segmenting the network can limit the damage caused when malware and ransomware is installed, preventing it from spreading across the entire network.
Scan for open ports and disable: Conduct a scan to identify all open ports and ensure those open, unused ports are disabled.
Monitor audit logs: Audit logs for all remote connection protocols, check logs to ensure all accounts were intentionally created, and audit access logs to check for unauthorized activity.
Backup all data: Good backup polices are essential for recovery from ransomware attacks: Adopt a 3-2-1 approach. Make three copies of backups, store them on at least two different media, and keep one copy off site. Backups should be on air-gapped devices (not connected to the Internet or network).
by titanadmin | Jan 31, 2018 | Email Scams, Phishing & Email Spam, Spam News, Spam Software |
A new FedEx phishing scam has been detected that appears to be targeting universities and businesses. Spam emails with the subject line ‘FedEx Delivery Notification’ are sent to users that explain FedEx was unable to deliver a package. The email claims the package was over the allowable weight limit and did not qualify for free delivery.
The email recipients are informed that in order to collect the package, they must visit their local FedEx depot in person. The package will not be released unless the user presents a label to the dispatcher, which the user is required to print.
The sophisticated FedEx phishing scam involves no email attachments, only a link. However, the link does not appear to be a malicious site. The attackers are using Google Drive to distribute their malware.
This is an increasingly common tactic that abuses trust of Google. Since the website is genuine – drive.google.com – users are less likely to believe that they are being scammed. The hyperlink will direct the user to Google Drive and will trigger the download of a file called Lebal copy.exe. An executable file that if run, will install malware.
Many people know not to run executable files, although in this case the file is disguised as a PDF and has the PDF icon. If known file extensions are not configured to be displayed on the user’s computer – which is now common- they would not be aware that the file is not a PDF.
The latest scam was uncovered by researchers at Comodo, who identify the malware as a Trojan called TrojWare.Win32.Pony.IENG that steals cookies and credentials. It is capable of stealing information from FTP clients, attempts to obtain and access cryptocurrency wallets, and extracts a wide range of user data and transmits the information to its command and control server. The malware uses various tactics to avoid detection by anti-malware and anti-virus defences.
Universities and Businesses Fall for FedEx Phishing Scam
According to Comodo, so far there have been 23 businesses, several government employees, and five university employees that have fallen for the scam. Since those businesses were protected by anti-virus software that was able to block the malware they avoided infection, although many others will not be so fortunate.
Protecting against scams like this requires layered defenses and user vigilance. Spam filters should be used by businesses to detect and quarantine spam emails such as this. Links to Google Drive can be difficult to block, as Google Drive is a legitimate website. Antivirus and anti-malware defenses must therefore be in place to detect the malicious download.
Businesses should not forget the human element of the security chain. Security awareness training and phishing simulations can help users to detect a FedEx phishing scam such as this.
Netflix Users Targeted by Scammers
A new sophisticated Netflix scam has appeared in the past few days. The emails claim users will have their Netflix membership suspended due to a problem processing the most recent payment.
The email appears to have been sent from Netflix and includes all the appropriate branding, making the email look highly convincing. The subject line is ‘Suspension of your membership’.
The email says there was a problem validating the most recent payment, and a link is supplied in the email that requires the user to validate their payment and billing information.
Clicking the link directs the user to what appears to be the Netflix website where they are asked to go through a series of steps to validate their account. The validation process requires them to re-enter their payment card information. The failure to complete the step will result in the suspension of their Netflix account.
The website contains the correct branding and looks exactly like the legitimate site. The URL is different, but the website is HTTPS and has the green padlock. A casual glance at the URL may not reveal there is anything wrong with the site.
Spam filtering solutions such as SpamTitan can detect this type of scam, but users must exercise caution as not all phishing emails can be blocked.
Users should carefully check the URL of any site they visit to make sure it is legitimate before entering sensitive information. Links sent in emails should be checked by hovering the mouse arrow over the link to find out the true URL.
An email such as this should prompt the user to visit Netflix using their usual bookmark or by typing in the URL into their browser, rather than visiting any links in the email.
by titanadmin | Jan 30, 2018 | Email Scams, Internet Security, Network Security, Phishing & Email Spam, Spam News, Spam Software |
Phishing emails cost a North Carolina school district $314,000 to resolve and caused considerable disruption while the infection was removed.
The high cost of resolving the attack was due to a particularly nasty and difficult to remove malware variant called Emotet malware which had been installed on endpoints and servers after employees responded to phishing emails.
The Rockingham County School District was attacked in late November. Numerous employees of the school district received a phishing email in their inboxes which appeared to be an incorrect invoice from their anti-virus provider. The emails contained an attachment and asked users to open the file to confirm. Doing so triggered the infection process, that resulted in the Emotet virus being downloaded.
The purpose of the malware is to obtain banking credentials. To ensure the maximum number of credentials are stolen, the virus is able to spread to other users. It was the attempt to spread that saw the infection detected. Some employees of the school district discovered their Google email accounts had been disabled as a result of spamming, which prompted an investigation. Internet access through web browsers was also impacted, suggesting a widespread malware infection.
While a malware infection was confirmed, removing the virus was not an easy task. There is no anti-virus software program that can remove the virus and prevent infection. The school district was able to clean and reimage some infected devices, but they were subsequently reinfected.
Unable to resolve the malware infection internally, the school district was forced to bring in external security consultants. In total, approximately a dozen infected servers had to be rebuilt to remove the infection. The school district also had to cover the cost of reimaging 3,000 workstations. The recovery is expected to involve some 1,200 on-site hours by IT staff and the process is expected to take up to a month.
During that time, the school district has had limited access to computers and had to loan around 200 Windows devices for key personnel. In order to cover the cost of the phishing attack, the school district took $314,000 in funds from its coffers.
“We feel like the $314,000 will get us back to where we were before we had the virus,” said school district Superintendent Rodney Shotwell.
The high cost of the phishing attack and the disruption caused shows just how important it is to deploy an advanced anti spam software solution to prevent malicious emails from reaching inboxes, and the importance of providing security awareness training to all employees to help them identify potential phishing attacks.
by titanadmin | Jan 29, 2018 | Email Scams, Phishing & Email Spam, Spam News, Spam Software |
What industries are the most susceptible to phishing scams? What industries must do more to prevent phishing attacks on their employees?
Recent research shows organizations that fail to implement technological defenses to block phishing emails and do not provide phishing awareness training to their employees are likely to suffer costly data breaches.
This year’s cost of a data breach study conducted by the Ponemon Institute suggests the average cost of mitigating a data breach is $3.62 million, while the FBI’s figures show that between 2013 and 2016, more than $1.6 billion was lost to phishing scams – Approximately $500 million a year. Phishing attacks on organizations have also been increasing year on year.
Unfortunately, while public awareness of the threat from phishing has improved considerably in recent years, an alarming number of employees continue to fall for phishing scams. A recent survey conducted by the phishing awareness training company Knowbe4 showed an astonishing 27% of employees clicked on a potentially malicious link or opened an email attachment sent via its phishing simulation tests. In some industry sectors, more than a third of employees failed the phishing simulations.
The Industries Most Susceptible to Phishing
Many studies produce questionable results due to a low sample size. However, the Knowbe4 study used data from 11,000 organizations and 6 million users. The results of the study therefore paint an accurate picture of just how susceptible employees are to phishing attacks.
Phishing simulations were run prior to the provision of security awareness training to obtain a baseline of the susceptibility of employees to phishing attacks. The results showed the industries most susceptible to phishing were insurance, manufacturing, retail, and non-profits. In the 1-249 employee category, 35.46% of insurance employees failed phishing tests, and 33.32% of employees failed the tests in the 250-999 employee category – The highest level of susceptibility of any industry sector in both categories.
Manufacturing was second worse in the 1-249 employee category with a failure rate of 33.21% followed by not-for-profits on 32.63%. In the 250-999 employee category, manufacturing (31.06) and business services (31.01%) were second and third.
The 1000+ employee category showed much reduced phishing susceptibility rates, ranging from business services on 19.40% to not-for-profits on 30.97%. Even the best performing industry sector saw almost 2 out of 10 employees fail phishing tests.
90 days after implementing a phishing awareness program, susceptibility to phishing was dramatically reduced. In the insurance sector, susceptibility rates fell from 35% and 33% in the small and medium sized business categories to 13% and 16%. A massive improvement. Overall, after a year – once phishing awareness training programs had matured – the overall susceptibility rates fell to a level of around 1% to 2%, with the highest percentages at the 5% level.
The survey shows just how important it is to provide ongoing training for the workforce to improve security awareness and the clear benefits of doing so.
It will never be possible to reduce phishing susceptibility to zero, therefore organizations should ensure that phishing emails are not delivered inboxes in the first place, and for that, an advanced anti spam software solution such as SpamTitan is required.
by titanadmin | Jan 26, 2018 | Email Scams, Network Security, Phishing & Email Spam, Spam Advice, Spam News |
The exponential growth in the price of cryptocurrencies has been accompanied by similar growth in email campaigns spreading cryptocurrency mining malware. There has also been a big rise in new mining malware variants, with three new malware variants detected in the past week. Conservative estimates suggest one malware variant has already been installed on at least 15 million systems, although the true figure could well be closer to 30 million.
The data comes from the cybersecurity firm Palo Alto Networks, which performed an analysis of the URLs used in the campaign using Bitly telemetry. It is difficult to determine how many systems have been affected since Bitly is not the only URL shortening service being used in the campaign. AdFly is also in use, which suggests the number of infected systems could well be twice as high.
The malicious links for this campaign are being sent in spam email. Clicking the links will direct the user to a malicious website containing executable files that install the Monero mining application XMRig using VBS scripts. The popularity of Monero mining is due to the lower processor demands than cryptocurrencies such as Bitcoin. Monero mining can take place on less powerful computers such as those typically at home. In addition to spam email campaigns, the malicious executable files are being loaded to popular file sharing websites
Symantec reports there has been a rise in browser-based cryptocurrency mining. Websites owners are loading cryptocurrency miners onto their websites that is implemented using a scripting language. The ease of access to JavaScript APIs that can be used for this purpose has increased the popularity of this mining technique. Symantec also reports there has been a 34% rise in mobile applications containing cryptocurrency mining code.
Cryptocurrency mining malware does not pose such a big threat to organizations as other forms of malware and ransomware, but there are implications for businesses. The malware does require a considerable amount of processing power, so there will be an impact on performance on infected machines. Infection will see applications slow considerably, and that will have an impact on productivity.
Campaigns are also being conducted that target businesses. The aim is to installing cryptocurrency mining malware on business servers. These attacks are not email-based, instead vulnerabilities are identified and exploited to install the malware, with Apache Struts (CVE-2017-5638) and DotNetNuke (CVE-2017-9822) vulnerabilities commonly exploited.
Preventing Infection with Cryptocurrency Mining Malware
Businesses can prevent cryptocurrency mining malware from being installed on their servers by ensuring all applications are patched and kept up to date. The patch to fix the Apache Struts vulnerability was released in September 2017, yet many businesses have not applied the patch. The DNN vulnerability has also been patched.
The risk of infections on employee and home computers requires antivirus and antimalware software and an advanced spam filter to prevent malicious messages from reaching inboxes. Businesses should also be training their staff how to recognize malicious emails. Training programs and phishing email simulations have been shown to help reduce susceptibility to email-based attacks by up to 95%.
The past few months have also seen a rise in cryptocurrency mining malware infections via unsecured WiFi networks, with cybercriminals performing man-in-the-middle attacks that hack the WiFi sessions of any user connected to one of the rogue WiFi access points. Unsecured public WiFi hotspots should be avoided, or VPNs used.
by titanadmin | Jan 24, 2018 | Email Scams, Network Security, Phishing & Email Spam, Spam Advice, Spam Software |
In this post we explain two of the most important strategies to adopt to block phishing and ransomware attacks.
Ensure Malicious Messages Do Not Reach Inboxes
Last year, Netwrix released a report based on a survey that showed 100% of government IT workers believed employees were the biggest threat to security. While those figures are the highest of many such surveys, the common theme throughout all of the research is employees are the most likely cause of a data breach.
One of the biggest areas of weakness is email-based attacks. Research conducted by the Friedrich Alexander University in Germany suggests half of users click links in emails from unknown senders. Those links often lead employees to phishing and malware-laced websites. With such high click rates, it is no surprise that so many IT workers believe employees are the weakest link in their security defenses.
Stopping employees from taking risky actions is difficult, so organizations must do all they can to ensure malicious emails are not delivered to inboxes. Only then, can IT workers be sure that employees will not click links or open dangerous email attachments.
How Does SpamTitan Work?
TitanHQ is a leading provider of
spam filtering solutions for enterprises. SpamTitan ensures the vast majority of spam and malicious emails are identified and quarantined and are not delivered to inboxes. SpamTitan has been independently tested and shown to block 99.97% of spam emails, ensuring end users are protected. But what can organizations do to protect their employees from the 0.03% of emails that are delivered to inboxes?
There is No Silver Bullet That Will Block Phishing and Ransomware Threats 100% of the Time
No business can no survive without email and unfortunately, no spam filtering solution can block 100% of all spam emails, 100% of the time. At least not without also blocking many genuine messages. Organizations cannot rely on a spam filter to block phishing and ransomware threats. It is just one important layer of security. Several other layers are required.
Anti-virus and anti-malware solutions are essential for detecting malicious software, but these signature-based security controls are proving less and less effective as years go by. For instance, the solutions are not particularly good at detecting fileless malware.
Most businesses further reduce risk by implementing endpoint protection systems that can detect anomalies and unnatural behavior on endpoints, indicative of an intrusion, malware activity, or ransomware scanning for files and making changes.
However, AV software and endpoint detection systems only detect phishing and ransomware attacks when they are occurring. If you want to block phishing and ransomware attacks, the most effective solution is a human firewall.
IT departments can blame employees for being the weakest link when it comes to security, but if employees are not trained and shown how to recognize malicious emails, they will remain the biggest security threat to an organization.
The Human Firewall – The Best Defense Against Phishing, Malware, and Ransomware Emails
A firewall is the first line of defense, and anti spam software will help to keep inboxes free from malicious messages. The rear guard is made up of your employees. To ensure you have a strong defensive backline, you must provide security awareness training. Many employees do not know that they are taking big risks that could compromise the network. It is up to organizations to ensure that those risks are explained.
Most malware and ransomware attacks involve at least some user interaction: The clicking of a link, the opening of a malicious document, or the enabling of a macro. Employees must be told this is how malware is installed and how access to email accounts and networks is gained. By training the workforce to be more security aware, employees can be turned into a formidable last line of defense.
Security Awareness Training Should Be Continuous
While it was once possible to provide annual security training and be reasonably confident that employees would be able to recognize malicious emails, that is no longer the case. Email-based cyberattacks are now far more sophisticated, and cybercriminals are investing considerably more time in developing highly convincing campaigns. Cybercriminals’ tactics are constantly changing. Training programs must reflect that.
To develop a strong human firewall, training should be ongoing. An annual classroom-based training session should be accompanied by regular CBT training sessions, provided in bite-sized chunks. Cybersecurity should be kept fresh in the mind with monthly email bulletins, as well as ad hoc alerts about new threats.
Research conducted by several security awareness training companies shows, training is very effective. PhishMe, Wombat Security Technologies, and Knowbe4 all suggest that with regular training it is possible to reduce susceptibility to email-based attacks by up to 95%.
Test the Effectiveness of Security Awareness Training with Phishing Simulations
You can backup all your data to ensure you can recover files in the event of a disaster, but if your backups are never tested you can never be sure file recovery is possible.
Similarly, providing security awareness training to employees will not guarantee you have created a strong human firewall. Your firewall must be tested. By sending phishing simulations to your workforce you can find out just how effective your training has been. You can identify weak links – employees that have not grasped the concept of phishing and email security and those individuals can be scheduled additional training. Phishing simulation exercises also help to reinforce training. When a test is failed, it can be turned into a learning opportunity, which helps to improve knowledge retention.
Implement technological solutions to block phishing and ransomware attacks and train your employees and test them on all manner of email-based attacks. When the real deal arrives in an inbox they will be prepared and deal with it appropriately. Fail to block emails or provide high quality training, and your company is likely to have to deal with a costly, and potentially disastrous, email-based attack.
Lire cet article en français.
by titanadmin | Jan 23, 2018 | Email Scams, Phishing & Email Spam, Spam Advice, Spam News, Spam Software |
Tax season is open season for cybercriminals and phishers, who increase their efforts to obtain personal information and Social Security numbers in the run up to – and during – tax season. Until April, we can expect many W2 phishing attacks. Make sure you are prepared and do not fall for a scam.
Anatomy of a W2 Phishing Attack
The most common method of stealing the information needed to file fraudulent tax returns is phishing. Phishing emails are sent in the millions to individuals in an effort to obtain their sensitive information. Individuals must be on high alert for malicious emails during tax season, but it is businesses that are most likely to be targeted.
Payroll employees have access to the W2 forms of the entire workforce. If a single worker can be convinced to email the data, the attacker can file thousands of fraudulent tax returns in the names of employees.
The way cybercriminals get payroll staff to part with sensitive data is by impersonating the CEO or CFO in what is referred to as a Business Email Compromise Scam – otherwise known as a BEC attack or CEO fraud.
The most successful attacks require access to the CEO or CFO’s email account to be gained. That means the CEO or CFO must first be targeted with a spear phishing email and lured into parting with his/her login credentials. Once access to the email account is gained, the impostor can craft an email and send it to a select group of individuals in the company: Payroll and accounts department employees.
The company is researched, individuals likely to have access to W2 forms are identified, and emails are sent. A request is made to attach the W2 forms of all employees who worked for the company in the past year, or for a specific group of employees. A series of emails may be sent, rather than asking for the information straight away.
Since the attacker has access to the CEO’s or CFO’s email account, they can delete sent emails and replies before they are seen by the account holder.
An alternative way of conducting BEC attacks is to spoof an email address. The CFO or CEO is identified from social media sites or LinkedIn, the email address is obtained or guessed based on the format used by the company, and the email is made to appear as if it has come from that email account. An alternative is for the attacker to purchase a similar domain to that used by the company, with two transposed letters for instance. Enough to fool an inattentive worker.
Oftentimes, W2 phishing attacks are not detected until days or weeks after the W2 forms have been sent, by which times IRS tax refund checks have been received and cashed.
How to Defend Against W2 Phishing Attacks
There are several methods that can be used to block W2 phishing attacks. A software or cloud-based anti-spam service should be used to block attacks that come from outside the company. Configured correctly, the spam filter should block spoofed emails and emails sent from similar domains to that used by the company. However, a spam filter will not block emails that come from the CFO or CEOs account.
Multi-factor authentication should be set up on all email accounts to help prevent the first phish that gives the attacker access to a C-suite email address. W2 phishing attacks using spoofed email addresses are much easier to identify and block.
It is therefore important to raise awareness of the threat of W2 phishing attacks with accounts and payroll staff, and anyone else with access to W2 forms. Training can greatly reduce susceptibility to W2 phishing attacks. Training should also be provided to the C-suite, not just employees.
The number of staff who have access to W2 forms should be restricted as far as is possible. Policies should also be introduced that require any request for W2 data to be verified. At a minimum, a request for the data should be checked by a supervisor. Ideally, the request should be confirmed face to face with the sender of the email, or with a quick phone call. The scammers rely on this check not taking place.
by titanadmin | Jan 20, 2018 | Email Scams, Phishing & Email Spam, Spam News, Spam Software |
The insurance, telecoms, and financial service sectors are being targeted by malicious actors spreading Zyklon malware. A large-scale spam email campaign has been detected that leverages three separate Microsoft Office vulnerabilities to download the malicious payload.
Zyklon malware is not a new threat. The malware variant was first detected at the start of 2016, but it stopped being detected soon after and was not extensively used until the start of 2017.
Zyklon malware is a backdoor with a wide range of malicious functions. The malware acts as a password harvester, keylogger, and data scraper, obtaining sensitive information and stealing credentials for further attacks. The malware can also be used to conduct DoS attacks and mine cryptocurrency.
The latest variant of Zyklon malware can download and run various plugins and additional malware variants. It can identify, decrypt, and steal serial keys and license numbers from more than 200 software packages and can also hijack Bitcoin addresses. All told, this is a powerful and particularly nasty and damaging malware variant that is best avoided.
While the latest campaign uses spam email, the malware is not included as an attachment. A zip file is attached to the email that contains a Word document. If the document is extracted, opened, and the embedded OLE object executed, it will trigger the download of a PowerShell script, using one of three Microsoft Office vulnerabilities.
The first vulnerability is CVE-2017-8759: A Microsoft NET vulnerability that was patched by Microsoft in October.
The second ‘vulnerability’ is Dynamic Data Exchange (DDE) – a protocol part of Office that allows data to be shared through shared memory. This protocol is leveraged to deliver a dropper that will download the malware payload. This vulnerability has not been patched, although Microsoft has released guidance on how to disable the feature to prevent exploitation by hackers.
The third vulnerability is far older. CVE-2017-11882 is a remote code execution flaw in Microsoft Equation Editor that has been around for 17 years. The flaw was only recently identified and patched by Microsoft in November.
The second stage of infection – The PowerShell script – serves as a dropper for the Zyklon malware payload.
According to the FireEye researchers who identified the campaign, the malware can remain undetected by hiding communications with its C2 using the Tor network. “The Zyklon executable contains another encrypted file in its .Net resource section named tor. This file is decrypted and injected into an instance of InstallUtiil.exe, and functions as a Tor anonymizer.”
Campaigns such as this highlight the importance of applying patches promptly. Two of the vulnerabilities were patched in the fall of 2017, yet many organizations have yet to apply the patches and remain vulnerable. If patches are not applied, it will only be a matter of time before vulnerabilities are exploited.
FireEye researchers have warned that while the campaign is currently only targeting three industry sectors, it is probable that the campaign will be widened to target other industry sectors in the near future.
The advice is to implement an advanced cloud-based anti-spam service such as SpamTitan to identify and quarantine malicious emails, and ensure that operating systems and software is kept up to date.
by titanadmin | Jan 16, 2018 | Internet Security, Phishing & Email Spam, Spam Advice |
More than 60 apps have now been removed from Google Play Store that were laced with AdultSwine Malware – A malware variant that displays pornographic adverts on users’ devices. Many of the apps that contained the malware were aimed at children, including Drawing Lessons Lego Star Wars, Mcqueen Car Racing Game, and Spinner Toy for Slither. The apps had been downloaded by between 3.5 and 7 million users before they were identified and removed.
While the malicious apps have been removed, users who have already downloaded the infected apps onto their devices must uninstall the apps to remove the malware. Simply deleting the apps from the Play Store only prevents more users from being infected. Google has said that it will display warnings on Android phones that have the malicious apps installed to alert users to the malware infection. It will be up to users to then uninstall those apps to remove the AdultSwine malware infection.
Apps Infected with AdultSwine Malware
- Addon GTA for Minecraft PE
- Addon Pixelmon for MCPE
- Addon Sponge Bob for MCPE
- AnimePictures
- Blockcraft 3D
- CoolCraft PE
- DiadelosMuertos
- Dragon Shell for Super Slither
- Draw Kawaii
- Draw X-Men
- Drawing Lessons Angry Birds
- Drawing Lessons Chibi
- Drawing Lessons Lego Chima
- Drawing Lessons Lego Ninjago
- Drawing Lessons Lego Star Wars
- Drawing Lessons Subway Surfers
- Easy Draw Octonauts
- Exploration Lite: Wintercraft
- Exploration Pro WorldCraft
- fidgetspinnerforminecraft
- Fire Skin for Slither IO app
- Five Nights Survival Craft
- Flash Skin for Slither IO app
- Flash Slither Skin IO
- Girls Exploration Lite
- Guide Clash IO
- Guide Vikings Hunters
- HalloweenMakeUp
- halloweenskinsforminecraft
- How to Draw Animal World of The Nut Job 2
- How to Draw Batman Legends in Lego Style
- How to Draw Coco and The Land of the Dead
- How to Draw Dangerous Snakes and Lizards Species
- How to Draw Real Monster Trucks and Cars
- Invisible Skin for Slither IO app
- Invisible Slither Skin IO
- Jungle Survival Craft 1.0
- Jurassic Survival Craft Game
- Mcqueen Car Racing Game
- Mine Craft Slither Skin IO
- Moviesskinsforminecraft
- Pack of Super Skins for Slither
- Paw Puppy Run Subway Surf
- Pixel Survival – Zombie Apocalypse
- Players Unknown Battle Ground
- San Andreas City Craft
- San Andreas Gangster Crime
- Shin Hero Boy Adventure Game
- skinsyoutubersmineworld
- Spinner Toy for Slither
- Stickman Fighter 2018
- Subway Banana Run Surf
- Subway Bendy Ink Machine Game
- Subway Run Surf
- Temple Bandicoot Jungle Run
- Temple Crash Jungle Bandicoot
- Temple Runner Castle Rush
- ThanksgivingDay
- ThanksgivingDay2
- Virtual Family – Baby Craft
- Woody Pecker
- youtubersskins
- Zombie Island Craft Survival
Malicious Activities of AdultSwine Malware
AdultSwine malware, and the apps that infect users, were identified and analyzed by security researchers at CheckPoint. The researchers note that once downloaded onto a device, the malware sends information about the user to its command and control server and performs three malicious activities: Displaying advertisements, signing up users to premium services, and installing scareware to fool victims into paying for security software that is not necessary. Information is also stolen from the infected device which can potentially be used for a variety of malicious purposes.
The advertisements are displayed when users are playing games or browsing the Internet, with the adverts coming from legitimate ad networks and the AdultSwine library. The AdultSwine malware library includes extreme adverts containing hardcore pornographic images. Those images appear on screen without warning.
The scareware claims the victim’s device has been infected with a virus that requires the download of an anti-malware app from the Google Play Store, although the virus removal tool is a fake app. Users are told that their phone will be rendered unusable if the app is not downloaded, with a countdown timer used to add urgency.
Registering for premium services requires the user to supply further information, which is done through pop-up phishing adverts. The user is told they have won a prize, but that they must answer four questions to claim their prize. The information they supply is used to register for premium services.
Preventing Infection of Mobile Devices
Generally, users can reduce the risk of a malware infection by only downloading apps from official app stores, although this latest malware campaign has shown that even official stores can be compromised and have malicious apps uploaded.
Google does scan all apps for malware, but new forms of malware can be sneaked into Google Play Store on occasion. Google has announced that from the end of January it will be rolling out a new service called Google Play Protect that is capable of scanning previously downloaded apps to ensure they are still safe to use.
Google recommends only downloading apps for children that have been verified by Google as being ‘Designed for Families’. Those apps may contain adverts, but they have been vetted and strict rules apply covering the advertisements that can be displayed.
It is also important to install some form of anti-malware solution – from a reputable and well-known company – that will scan downloaded content and apps for malware.
by titanadmin | Jan 5, 2018 | Industry News, Internet Security, Network Security |
It has been pretty difficult to avoid the news of Meltdown and Spectre – Two vulnerabilities recently discovered that could potentially be exploited to gain access to sensitive information on PCs, Macs, servers, and smartphones. Meltdown and Spectre affect virtually all devices that contain CPUs, which amounts to billions of devices worldwide.
What are Meltdown and Spectre?
Meltdown and Spectre are two separate vulnerabilities affecting CPUs – central processing units. The chips that power a wide range of electronic devices. The flaws make devices vulnerable to side-channel attacks, in which it is possible to extract information from instructions that have been run on CPUs, using the CPU cache as a side channel.
There are three types of attacks, two for Spectre and one for Meltdown. Spectre Variant 1 – tracked as CVE-2017-5753- is a bounds check bypass, while Spectre variant 2 – tracked as CVE-2017-5715 – is a branch target injection. Variant 3, termed Meltdown – tracked as CVE-2017-5754 – is a rogue data cache load, memory access permission check that is performed after kernel memory read.
The less technical explanation is the attacks leverage the prediction capabilities of the CPU. The CPU will predict processes, load them to an easily accessible, fast sector of the memory to save time and ensure fast performance. Spectre allows data to be read from the memory, but also for information to be loaded into the memory and read that would otherwise not be possible.
Meltdown also reads information from the memory, stealing information from memory used by the kernel that would not normally be possible.
What Devices are Affected by Meltdown and Spectre?
US-CERT has warned that the following vendors have been affected by Meltdown and Spectre: AMD, Apple, Arm, Google, Intel, Linux Kernel, Microsoft, and Mozilla. Apple has said that virtually all of its Macs, iPhones, and iPads are affected. PCs and laptops with Intel, Arm, and AMD chips are affected by Spectre, as are Android smartphones. while Meltdown affects desktops, laptops, and servers with Intel chips. Since servers are affected, that has major implications for cloud service providers.
How Serious are Meltdown and Spectre?
How serious are Meltdown and Spectre? Serious enough for the Intel chief executive officer, Brian Krzanich, to sell $25 million of his shares in the company prior to the announcement of the flaws, although he maintains there was no impropriety and the sale of the shares was unrelated to the announcement of the flaws a little over a month later.
For users of virtually all devices that contain CPUs, the flaws are certainly serious. They could potentially be exploited by malicious actors to gain access to highly sensitive data stored in the memory, which can include passwords and credit card data.
What makes these flaws especially serious is the number of devices that are affected – billions of devices. Since one of the flaws affects the hardware itself, which cannot be easily corrected without a redesign of the chips, resolving the problem will take a considerable amount of time. Some security experts have predicted it could take decades before the flaws are totally eradicated.
Fortunately, companies have been scrambling to develop patches that can at least reduce the risk of the flaws being exploited. For example, Chrome and Firefox have already released updates that will prevent attacks from occurring via browsers. Since the attacks can be performed using JavaScript, securing web browsers is essential.
At present, it would appear that the flaws have not been exploited in the wild, although now the news has broken, there will certainly be no shortage of individuals attempting to exploit the flaws. Whether they are able to do so remains to be seen.
What Can You do to Prevent Meltdown and Spectre Attacks?
As is the case when any vulnerability is identified, protecting against Meltdown and Spectre requires patches to be applied. All software should be updated to the latest versions, including operating systems, software packages, and browsers. Keeping your systems 100% up to date is the best protection against these and other attacks.
Some third-party antivirus software will prevent Windows patches from being installed, so before Windows can be updated, antivirus must be updated. Ensure that your AV program is kept up to date, and if you have automatic updates configured for Windows, as soon as your system is ready for the update it will be installed.
Chrome and Firefox have already been updated, Microsoft will be rolling out a patch for Windows 10 on Thursday, and over the next few days, updates will be released for Windows 7 and 8. Apple has already updated MacOS version 10.13.2, with earlier versions due to receive an update soon.
Google has already issued updates for Android phones, although only Google devices have so far been updated, with other manufactures due to roll out the updates shortly. Google has already updates its Cloud Platform, and Amazon Web Services has also reportedly been updated. Linux updates will also be issued shortly.
Fixes for Meltdown are easier to implement, while Spectre will be harder as true mitigations would require major changes to the way the chips work. It is unlikely, certainly in the short term, for Intel to attempt that. Instead, mitigations will focus on how programs interact with the CPUs. As US-CERT has warned, “[The] Underlying vulnerability is caused by CPU architecture design choices. Fully removing the vulnerability requires replacing vulnerable CPU hardware,” although that advice is no longer detailed in its updated vulnerability warning.
Applying patches will help to keep computers protected, but that may come at a cost. For example, the fix for the Meltdown vulnerability changes the way the computer works, which means the processor will have to work harder as it has to repeatedly access information from the memory – tasks that would otherwise not normally need to be performed.
That will undoubtedly have an impact on the performance of the machine. How much of a dip in performance can be expected? Some experts predict the changes could slow computers down by as much as 30%, which would certainly be noticed at times when processor activity is particularly high.
by titanadmin | Jan 4, 2018 | Industry News, Internet Security, Network Security |
A recently discovered Forever 21 POS malware attack has seen customers’ credit card data compromised. While malware attacks on retail POS systems are now commonplace, in the case of the Forever 21 POS malware attack, the security breach stands out due to the length of time malware was present on its systems. Attackers first gained access to its POS system seven months before the infection was discovered.
The Forever 21 POS malware infections were first identified in October, when a third-party linked credit card fraud to customers who had previously visited Forever 21 stores. The potential malware infections were investigated and a third-party cybersecurity firm was called in to assist.
Forever 21 first made the announcement about a data breach in November, although the investigation has been ongoing and now new details about the attack have been released.
The investigation has revealed the attack was extensive and affected many POS devices used in its U.S. stores. The Forever 21 POS malware attack started on April 3, 2017, with further devices compromised over the following 7 months until action was taken to secure its systems on November 18, 2017. Forever 21 reports that some POS devices in its stores were only compromised for a few days, others for a few weeks, while some were compromised for the entire timeframe.
In response to the increased threat of cyberattacks on retailers, Forever 21 started using encryption technology on its payment processing systems in 2015; however, the investigation revealed the encryption technology was not always active.
While the encryption technology was active, the attackers would have been prevented from obtaining the credit card details of its customers, although the information could be stolen at times when the encryption technology was turned off.
Further, some devices that were compromised by the malware maintained logs of completed credit card transactions. When the encryption technology was not active, details of completed transactions were stored in the logs and could therefore be read by the attackers. Since those logs contained details of transactions prior to the malware infections, it is possible that customers who visited affected Forever 21 stores prior to April 3, 2017 may also have had their credit card details stolen.
Each store uses multiple POS devices to take payments from consumers, and in most cases only one device per store was compromised. The attackers concentrated their efforts on stores where POS devices did not have encryption enabled. Further, the attackers main aim appeared to be to find and infect devices that maintained logs of transactions.
On most POS devices, the attackers searched for track data read from payment cards, and in most cases, while the number, expiry date and CVV code was obtained, the name of the card holder was not.
The investigation into the Forever 21 POS malware attack is ongoing, and at present it is unclear exactly how many of the company’s 700+ stores have been affected, how many devices were infected, and how many customers have had their credit and debit card details stolen. However, it is fair to assume that an attack of this duration will have affected many thousands of customers.
The type of malware used in the attack is not known, and no reports have been released that indicate how the attackers gained access to its systems. It is not yet known if stores outside the US have been affected.
by titanadmin | Dec 31, 2017 | Internet Security, Network Security |
2017 has been a bad year for data breaches, but what were the worst data breaches of 2017? We have compiled a list of the largest and most serious cyberattacks that came to light this year.
The Worst Data Breaches of 2017
Equifax – 143 Million Records
The Equifax data breach was discovered in September and ranks first in our list of the worst data breaches of 2017, not just for the size of the breach, but also due to the nature of data stolen by the attackers. Equifax reports that the breach impacted as many as 143 million consumers – That’s 44% of the population of the United States.
The data stolen in the attack including highly sensitive information – the types of data cybercriminals seek in order to commit identity theft and fraud. Social Security numbers and driver’s license numbers were stolen along with names, addresses, dates of birth, and credit card numbers. The breach was the result of an unpatched software vulnerability.
Deep Root Analytics – 198 Million Records
The data breach at Deep Root Analytics was massive, involving almost 200 million records. Deep Root Analytics is a marketing firm that was contracted by the Republican National Convention to gather political information on U.S voters.
The data were stored in an Amazon AWS S3 bucket that could be accessed without the need for a password for two weeks before the lack of protection was discovered. During that time, voter records could be accessed, including names, addresses, dates of birth, and phone numbers.
Uber – 57 Million Records
The Uber data breach may not have been the most severe in terms of the types of data exposed, but it certainly ranks as one of the worst data breaches of 2017, affecting some 57 million riders and drivers.
What really makes this one of the worst breaches of 2017 is the discovery that Uber attempted to keep the breach quiet. Uber paid the attacker $100,000 to keep quiet and not publish the data, which included names, addresses, email addresses, and in some cases, driver’s license numbers. The breach occurred in October 2016, but it was not disclosed for more than a year.
Verizon – 14 Million Records
As with many other data breaches in 2017, this security breach was due to an unsecured Amazon AWS S3 bucket that was controlled by NICE systems – A partner of Verizon. It is unclear whether Verizon customer data was stolen, but the records of 14 million customers were exposed. Those records included names, PIN numbers, and phone numbers in the form of logs from Verizon customers that had called its customer service department. Potentially, the information could be used to access customers’ accounts. The data were stored in an unprotected Amazon AWS S3 bucket
Dun & Bradstreet – 33.7 Million Records
The data analytics firm Dun & Bradstreet created a marketing database containing 52 GB of data, including 33.7 million email addresses and contact information. While Dun & Bradstreet maintains its systems were not compromised, one of the companies that the database was sold to certainly was. The database contained the records of millions of employees of major companies including Wal-Mart and CVS Health, as well as the U.S Postal Service and the Department of Defense.
America’s JobLink – 4.8 Million Records
A misconfigured application was exploited by a hacker to gain access to the records of 4.8 million individuals. The data were maintained by America’s JobLink – a firm that connects employers and job seekers
The breach was detected in March 2017, although an analysis revealed the code error was introduced in October 2016. The hacker exploited the vulnerability in February and had access to the data for a month.
The breach was particularly bad as it involved names, dates of birth and Social Security numbers, placing the breach victims at a high risk of identity theft and fraud. It is unclear whether the hacker managed to steal all 4.8 million records.
Deloitte – 350+ records
In the list of the largest data breaches of 2017, the Deloitte breach would come in very close to the bottom; however, in terms of the potential severity of the breach it ranks near the top. An estimated 350 clients were impacted when a hacker gained access to Deloitte’s email server and email conversations between the firm and its clients. Those clients included government departments – including Homeland Security and the Department of Defense – the National Institutes of Health, FIFA, and the U.S Postal Service.
The breach was discovered this year, although the hackers reportedly had access to its systems for several months. The email server was breached using an admin account, with the breach preventable had two-factor authentication been used.
River City Media – 1.4 Billion Records
A massive illegal spam operation run by River City Media was uncovered this year by security researchers, who discovered more than 1.4 billion records had been left exposed online. An analysis of the data showed there were 393 million unique email addresses in the database, along with names, IP addresses, and real addresses.
The investigation into River City Media revealed the group was sending as many as a billion emails a day, and was masquerading as a legitimate marketing company. The files were exposed due to poor RSync backup practices, which ensured a disaster would not result in data loss, but the firm inadvertently left its data exposed online.
Onliner Spambot – 711 Million Records
Another massive data breach to affect spammers involved the operator of the onliner spambot, which harvested email addresses to send spam emails. A database of some 711 million email addresses was left exposed online after the server on which the data were stored had been left unprotected. It is unknown how many people discovered the database and are now using it to plague those 711 million individuals with email more spam email. The breach was largely limited to email addresses, but in terms of size, it certainly ranks as one of the worst data breaches of 2017.
by titanadmin | Dec 29, 2017 | Internet Security, Network Security |
Every December, a list of terrible passwords is published by SplashData, and this year the list of the worst passwords of 2017 contains the same horrors as years gone by. Passwords that not only would take a hacker next to no time to guess, but in many cases, could be cracked at the first attempt.
The list of the worst passwords of 2017 is compiled from databases of leaked and stolen passwords that have been published online throughout 2017. This year, SplashData compiled its list from more than 5 million leaked passwords.
The minimum password length on many websites has now been increased to eight characters; however, it is still possible to use passwords of six characters in many places. This year, the worst password is six characters long and is the extremely unimaginative: 123456. A password so easy to guess, it is barely worth setting a password at all.
In second place is an eight-character password, which is similarly not worth using at all: password. In third place is 12345678. Those three passwords retained the same positions as last year.
Each year, the same passwords appear on the list, with slight fluctuations in their positions in the list. However, there are some new entries this year. The rebooting of the Star Wars saga has spurred many people to choose Star Wars related passwords, with starwars featuring in 16th position on the list.
An interesting entry makes it into 25th place – trustno1. Good advice, but even with the addition of a number, it is still a poor password choice. At first glance, number 24 in the list appears to be reasonable, but qazwsx is the first six characters on the left-hand side of the keyboard.
Using the passwords letmein, passw0rd, admin, master, and whatever, are all equally bad. All of those words make the top 25 in the list of the worst passwords of 2017.
Top 25 Worst Passwords of 2017
- 123456
- password
- 12345678
- qwerty
- 12345
- 123456789
- letmein
- 1234567
- football
- iloveyou
- admin
- welcome
- monkey
- login
- abc123
- starwars
- 123123
- dragon
- passw0rd
- master
- hello
- whatever
- qazwsx
- trustno1
The list of the worst passwords of 2017 reveals many people are extremely unimaginative when choosing a password to secure their email, social media, and online accounts.
SplashData estimates 3% of people have used the worst password on the list, while 10% have used one of the first 25 passwords to “secure” at least one online account.
Most people know that strings of consecutive numbers are bad, as is any variation of the word password, but changing to a dictionary word or a pop culture reference is just as bad, as Morgan Slain, CEO of SplashData, Inc., explained, “Hackers are using common terms from pop culture and sports to break into accounts online because they know many people are using those easy-to-remember words.”
That means using football (or any other sport) or starwars will not prevent a hacker from gaining access to an account for very long.
What Makes a Bad Password?
Brute force attacks, those where repeated attempts are made to guess passwords, does not involve a hacker sitting at a computer typing bad passwords until the correct one is guessed. Those attacks are performed by bots, and it doesn’t take long for a bot to guess a poor password.
Without rate limiting – setting a maximum number of failed attempts before access is temporarily blocked – to slow down the process, the bots can cycle through the list of the worst passwords of 2017 quickly, followed by those used in other years and other dictionary words.
Hackers also know the tricks that people use to keep passwords easy to remember, while meeting the strong password requirements set by IT departments, such as adding an explanation mark to the end of an easy to remember word or replacing certain letters with their numerical equivalent: An A with a 4, or an O with a zero for instance.
What Makes a Good Password?
A good password should contain upper and lowercase letters, numbers, and special characters, and should preferably be a random string of 10 or more characters. That of course makes passwords very difficult to remember. Writing the password down so you don’t forget it is also a very bad idea, as is reusing passwords on multiple sites and recycling old passwords.
In 2017, NIST revised its advice on choosing passwords as its research showed that forcing people to choose upper and lower-case passwords and special characters did not always ensure people chose strong passwords. Instead, they get around the technology by simply changing the first letter to a capital letter and adding a special character and number to the end, for instance.
Instead, NIST recommended using a passphrase rather than a password. A phrase that only you would know.
A list of four or five unrelated words would work well. Dogforkliftmonkeyhousecar would be a strong password phrase to use (other than the fact it has now been published online). It would be difficult to crack but easy to remember with a mnemonic.
To keep your accounts secure, make sure you choose strong and complex passwords, ideally long passwords of at least 15 characters. However, remembering the 20 or so unique passwords you are likely to need will still be hard.
The solution is to use a password manager, and to secure that account with a strong hard to guess password. Then only one complex password must be remembered.
by titanadmin | Dec 27, 2017 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam Advice |
Digimine malware is a new threat that was first identified from a campaign in South Korea; however, the attacks have now gone global.
Ransomware is still a popular tool that allows cybercriminals to earn a quick payout, but raised awareness of the threat means more companies are taking precautions. Ransomware defenses are being improved and frequent backups are made to ensure files can be recovered without paying the ransom. Not only is it now much harder to infect systems with ransomware, rapid detection means large-scale attacks on companies are prevented. It’s harder to get a big payday and the ability to restore files from backups mean fewer organizations are paying up.
The surge in popularity of cryptocurrency, and its meteoric rise in value, have presented cybercriminals with another lucrative opportunity. Rather than spread ransomware, they are developing and distributing cryptocurrency miners. By infecting a computer with a cryptocurrency miner, attackers do not need to rely on a victim paying a ransom.
Rather than locking devices and encrypting files, malware is installed that starts mining (creating) the cryptocurrency Monero, an alternative to Bitcoin. Mining cryptocurrency is the verification of cryptocurrency transactions for digital exchanges, which involves using computers to solve complex numeric problems. For verifying transactions, cryptocurrency miners are rewarded with coins, but cryptocurrency mining requires a great deal of processing power. To make it profitable, it must be performed on an industrial scale.
The processing power of hundreds of thousands of devices would make the operation highly profitable for cybercriminals, a fact that has certainly not been lost on the creators of Digimine malware.
Infection with Digimine malware will see the victim’s device slowed, as its processing power is being taken up mining Monero. However, that is not all. The campaign spreading this malware variant works via Facebook Messenger, and infection can see the victim’s contacts targeted, and could potentially result in the victim’s Facebook account being hijacked.
The Digimine malware campaign is being spread through the Desktop version of Facebook Messenger, via Google Chrome rather than the mobile app. Once a victim is infected, if their Facebook account is set to login automatically, the malware will send links to the victim’s contact list. Clicking those links will result in a download of the malware, the generation of more messages to contacts and more infections, building up an army of hijacked devices for mining Monero.
Infections were first identified in South Korea; however, they have now spread throughout east and south-east Asia, and beyond to Vietnam, Thailand, Philippines, Azerbaijan, Ukraine, and Venezuela, according to Trend Micro.
A similar campaign has also been detected by FortiGuard Labs. That campaign is being conducted by the actors behind the ransomware VenusLocker, who have similarly switched to Monero mining malware. That campaign also started in South Korea and is spreading rapidly. Rather than use Facebook Messenger, the VenusLocker gang is using phishing emails.
Phishing emails for this campaign contain infected email attachments that download the miner. One of the emails claims the victim’s credentials have been accidentally exposed in a data breach, with the attachment containing details of the attack and instructions to follow to mitigate risk.
These attacks appear to mark a new trend and as ransomware defenses continue to improve, it is likely that even more gangs will change tactics and switch to cryptocurrency mining.
by titanadmin | Dec 20, 2017 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News |
A Q3 malware threat report from McAfee charts the continued rise in malware threats throughout the year. Malware variants have now reached an all time high, with the volume of threats having risen each quarter in 2017.
In 2016, there were high levels of malware in Q1, rising slightly in Q2 before tailing off in Q3 and A4. That trend has not been seen this year. The malware threat report shows Q1 figures were higher than the previous two quarters, with a massive rise in Q3 and a continued increase in Q3. Malware threats rose 10% quarter over quarter, rising to a quarterly total of 57.6 million new samples of malware: The highest quarterly total detected by McAfee. That averages out at a new malware sample detected every quarter of a second!
The ransomware epidemic has also got worse in Q3, with new ransomware variants increasing by 36% last quarter, fueled by a sharp increase in Android screen lockers. In total, new mobile malware variants increased by 60% in Q3.
In its Q3 Malware Threat Report, McAfee noted that attackers were continuing to rely on spam email to distribute malware, with the Gamut botnet the most prevalent spamming botnet in Q3, closely followed by the Necurs botnet. The latter was used to spread ransomware variants such as Locky. Mac malware rose by 7% in Q3, and macro malware increased by 8%.
Technologies such as PowerShell are still commonly used to install malware, along with Office macros. New PowerShell malware variants doubled in Q3, 2017, and while new JavaScript malware declined by 26% quarter over quarter, the level of new JavaScript malware is still substantially higher than the level seen in 2016.
Vulnerabilities in software and operating systems were also extensively exploited, even though patches to address those vulnerabilities were released promptly.
McAfee notes that employees and organizations are making it far too easy for attackers. Employees are responding to phishing emails, are visiting malicious links and are opening attachments and enabling the content. Employers are no better. Patches are released, yet they are not being applied promptly, opening the door to attackers. In many cases, patches have still not been applied several months after they have been released.
One of the most commonly exploited vulnerabilities in Q3, 2017 was CVE-2017-0199 which affected WordPad and Microsoft Office. An exploit for the vulnerability was made available through GitHub, making remote code execution attacks easy; provided employees could be convinced to open specially crafted files. Many employees fell for the scam emails.
The McAfee Q3 Malware Threat Report highlighted several continuing malware trends, including the increase in the use of fileless malware. PowerShell malware increased by 119% in Q3 alone.
Q3 saw a new Locky variant released – Lukitus. Lukitus was spread via spam email, with more than 23 million messages delivered in the first 24 hours since its release. That, combined with other new ransomware threats, have contributed to a 44% increase in ransomware samples in the past 12 months.
Q3 also saw the release of a new variant of the Trickbot Trojan, which incorporated the EternalBlue exploit that was also used in the WannaCry and NotPetya attacks.
While no industry is immune to attack, it is the healthcare and public sectors that are taking the brunt of the attacks, accounting for 40% of all reported security incidents in Q3. In the United States, healthcare was the most commonly attacked industry.
The extensive use of spam and phishing emails to spread malware highlights the importance of using an advanced spam filtering solution such as SpamTitan, especially considering how employees are still struggling to identify malicious emails. Blocking these threats and preventing malicious messages from being delivered will help organizations prevent costly data breaches.
The high level of infections that occurred as a result of exploited vulnerabilities also shows how important it is to apply patches promptly. McAfee notes that many of the exploited vulnerabilities in Q3 were patched as early as January. If patches are not applied promptly, they will be exploited by cybercriminals to install malware.
by titanadmin | Dec 19, 2017 | Industry News, Network Security, Spam Advice, Spam Software |
In this article we explore the cost of HIPAA noncompliance for healthcare organizations, including the financial penalties and data breach costs, and one of the most important technologies to deploy to prevent healthcare data breaches.
The Health Insurance Portability and Accountability Act (HIPAA)
In the United States, healthcare organizations that transmit health information electronically are required to comply with the Health Insurance Portability and Accountability Act (HIPAA). HIPAA was introduced in 1996 with the primary aim of improving healthcare coverage for employees between jobs, although it has since been expanded to include many privacy and security provisions following the introduction of the HIPAA Privacy and Security Rules.
These rules require HIPAA-covered entities – health plans, healthcare providers, healthcare clearinghouses and business associates – to implement a range of safeguards to ensure the confidentiality, integrity, and availability of protected health information (PHI). Those safeguards include protections for stored PHI and PHI in transit.
HIPAA is not technology specific, if that were the case, the legislation would need to be frequently updated to include new protections and the removal of outdated technologies that are discovered not to be as secure as was initially thought. Instead, HIPAA leaves the actual technologies to the discretion of each covered entity.
In order to determine what technologies are required to keep PHI secure, covered entities must first conduct a risk analysis: A comprehensive, organization-wide analysis of all risks to the confidentiality, integrity, and availability of PHI. All risks identified must be managed and reduced to an appropriate and acceptable level.
The risk analysis is one of the most common areas where healthcare organizations fall afoul of HIPAA Rules. Healthcare organizations have been discovered not to have included all systems, hardware and software in the risk analysis, or fail to conduct the analysis on the entire organization. Vulnerabilities are missed and gaps remain in security controls. Those gaps allow hackers to take advantage and gain access to computers, servers, and databases.
When vulnerabilities are exploited, and a data breach occurs, HIPAA-covered entities must report the security breach to the Department of Health and Human Services’ Office for Civil Rights (OCR): The main enforcer of HIPAA Rules. OCR investigates data breaches to determine whether they could realistically have been prevented and if HIPAA Rules have been violated.
What is the Cost of HIPAA Noncompliance?
When healthcare organizations are discovered not to have complied with HIPAA Rules, financial penalties are often issued. Fines of up to $1.5 million per violation category (per year that the violation has been allowed to persist) can be issued by OCR. The cost of HIPAA noncompliance can therefore be severe. Multi-million-dollar fines can, and are, issued.
The cost of HIPAA noncompliance is far more than any financial penalty issued by OCR, or state attorneys general, who are also permitted to issue fines for noncompliance. HIPAA requires covered entities to notify individuals impacted by a data breach. The breach notification costs can be considerable if the breach has impacted hundreds of thousands of patients. Each patient will need to be notified by mail. If Social Security numbers or other highly sensitive information is exposed, identity theft protection services should be offered to all breach victims.
Forensic investigations must be conducted to determine how access to data was gained, and to establish whether all malware and backdoors have been removed. Security must then be enhanced to prevent similar breaches from occurring in the future.
A data breach often sees multiple lawsuits filed by the victims, who seek damages for the exposure of their information. Data breaches have a major negative impact on brand image and increase patient churn rate. Patients often switch providers after their sensitive information is stolen.
On average, a data breach of less than 50,000 records costs $4.5 million to resolve according to the Ponemon Institute and has an average organizational cost of $7.35 million.
The 78.8 million-record breach experienced by Anthem Inc. in 2015 is expected to have cost the insurer upwards of $200 million. That figure does not include lost brand value and reputation damage, and neither a HIPAA fine from OCR.
A summary of the cost of HIPAA noncompliance, including recent fines issued by attorneys general and OCR has been detailed in the infographic below.
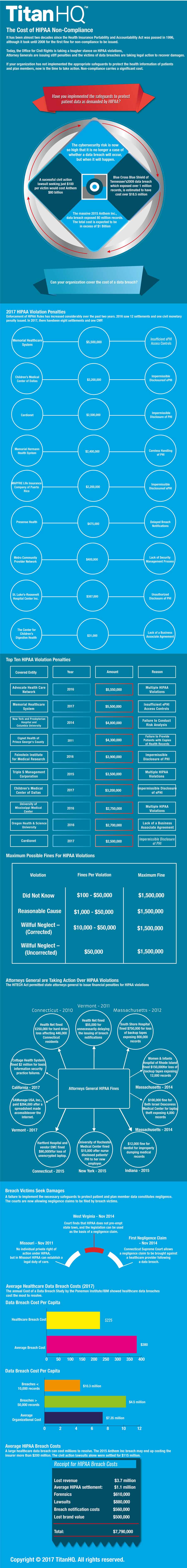
The Importance of Protecting Email Accounts
There are many ways that unauthorized individuals can gain access to protected health information – via remote desktop applications, by exploiting vulnerabilities that have not been patched, accessing databases that have been left exposed on the Internet, or when devices containing unencrypted PHI are stolen. However, the biggest single threat to healthcare data comes from phishing.
Research from PhishMe indicates more than 90% of data breaches start with a phishing email, and a recent HIMSS Analytics survey confirmed that phishing is the biggest threat, with email ranked as the most likely source of a healthcare data breach.
Protecting email accounts is therefore an essential part of HIPAA compliance. OCR has already fined healthcare organizations for data breaches that have resulted from phishing emails.
Healthcare organizations should implement a solution that blocks malicious emails and scans for malware and ransomware. In addition to technology, employees must also be trained how to identify malicious emails and taught to be more security aware.
How TitanHQ Can Help with HIPAA Compliance
TitanHQ developed SpamTitan to keep inboxes secure and prevent email spam, phishing messages, and malware from being delivered to inboxes. SpamTitan blocks more than 99.9% of spam email, and dual anti-virus engines ensure emails with malicious attachments are identified and quarantined. With SpamTitan, your organization’s email accounts will be protected – an essential part of HIPAA compliance.
WebTitan compliments SpamTitan and offers an additional layer of protection. WebTitan is a web filtering solution that allows you to carefully control the websites that your employees visit. WebTitan will prevent employees from visiting malicious websites via emailed hyperlinks, general web browsing, malvertising or redirects, protecting your organization from web-based attacks, drive by downloads of ransomware and malware, and exploit kit attacks.
For more information on TitanHQ’s cybersecurity solutions for healthcare, contact the TitanHQ team today.
by titanadmin | Dec 15, 2017 | Email Scams, Network Security, Phishing & Email Spam, Spam News, Spam Software |
Antivirus software vendor Symantec has detected a massive spam email campaign that is spreading Adwind RAT variants. While the Adwind RAT may sound like relatively harmless adware, that could not be further from the truth.
The latest Adwind RAT variants have a wide range of malicious functions, and serve as keyloggers that can record login credentials and monitor user activity, take screenshots, hijack the microphone and webcam to record audio and video, and as if that was not enough, the Adwind RAT allows the attacker to download further malicious files.
As is now the norm, the emails spreading Adwind RAT variants are convincing and appear to be genuine communications from legitimate firms. At a time when parcels are likely to arrive in the mail, the attackers have chosen a particularly relevant ploy to maximize the chance of emails being opened. Notifications about parcels that could not be delivered.
Businesses are also being targeted with malicious attachments claiming to be account statements, invoices, purchase orders, and payment receipts. The emails are well written and appear to have been sent from legitimate firms.
The spam emails include two malicious email attachments, a JAR file and what appears to be a PDF file. In the case of the latter, it has a double file extension, which will appear as a PDF file if file extensions are not displayed. In reality, it is another JAR file. The files contain layers of obfuscation in an attempt to bypass antivirus controls.
If the JAR files are executed, they drop a further JAR file and run VBS scripts which launch legitimate Windows tools to investigate the environment, identify the firewall in use, and other security products installed on the device. They then set about disabling monitoring controls.
The timing of this Adwind RAT campaign is ideal to catch out as many people as possible. The festive period is a busy time, and the rush to find bargains and purchase presents online sees many Internet users let their guard down. Further, as many businesses close over the festive period it gives the attackers more time to explore networks.
Infection with the Adwind RAT can see sensitive data stolen, and login credentials obtained, email accounts to be pilfered and abused and access to be gained to corporate bank accounts. A single successful installation of the Adwind RAT can be devastating.
The AdWind RAT is one of 360,000 New Daily Threats
Of course, the Adwind RAT spam email campaign is just one example of a malicious actor spreading malware. One example from tens of thousands, each spreading different malware and ransomware variants.
Each day new campaigns are launched. Figures from Kaspersky Lab indicate 2017 has seen an astonishing 360,000 new malicious files detected each day.
While consumers must be alert to the threat from spam email, the threat to businesses is far greater. The threat is multiplied by the number of employees who have a work email account.
A single computer infected with malware is serious, although once a foothold has been gained, the infection can spread rapidly. Recent research by SafeBreach, published in the Hacker’s Playbook Findings Report, suggests that 70% of the time, hackers are able to navigate the network and move laterally once access has been gained. A single malware attack can turn into an organization-wide nightmare infection.
The recent ransomware attacks in the United States are a good example. A ransomware attack on the Mecklenburg County government in South Carolina resulted in 48 servers being taken out of action, and that attack was identified rapidly. The Texas Department of Agriculture experienced a similar attack that impacted 39 schools via its network connections.
It is now essential to implement a host of defenses to prevent malware attacks. One of the most effective defenses is to upgrade your spam filter to an advanced solution such as SpamTitan.
SpamTitan blocks more than 99.9% of spam emails and detects and blocks malware using dual anti-virus engines. SpamTitan not only scans messages for the presence of malware and malware downloaders, but also message content for the common signatures of spam and malicious links. When threats are detected, the emails are quarantined before they can do any harm.
If you have a spam filter, yet have still experienced an email-based malware or ransomware attack, now is the ideal time to switch providers and discover the difference SpamTitan can make. If you have yet to install a third-party spam filter, there is no time to lose. Take advantage of the free trial and start protecting your organization from email spam and malware attacks.
Call the TitanHQ team today for further information on SpamTitan, details of pricing, and for further details on how you can sign up for the no-obligation free trial. The knowledgeable sales team will be able to answer any questions you have.
by titanadmin | Dec 13, 2017 | Email Scams, Internet Security, Network Security, Phishing & Email Spam, Spam News, Spam Software |
A particularly nasty new threat has emerged: Spider ransomware. The new crypto-ransomware variant was discovered by security researchers at Netskope on December 10, and the campaign is ongoing.
While many ransomware variants give victims a week to make contact and pay the ransom, the actors behind Spider ransomware are far less patient. If the ransom payment is not made within 96 hours of infection, the key to unlock files will be blocked and files will be permanently encrypted. Further, victims are warned “do not try anything stupid, the program has several security measures to delete all your files and cause damage to your PC.”
Naturally, that something stupid is not attempting to recover files from backups. If viable backups exist, victims will be able to recover their files without paying the ransom, but the warning may put off some victims from trying.
Such a short window for payment does not give victims much time. Many ransomware attacks occur on a Friday, and are only discovered when employees return to work on a Monday. Discovering a Spider ransomware attack in this scenario means businesses will have to act particularly quickly in order to avoid file loss.
While the threat is severe, the attackers have made it as easy as possible for victims to pay by providing a detailed help section. Payment must be made in Bitcoin via the Tor browser and detailed instructions are provided. The attackers say in the ransom note, “This all may seem complicated to you, actually it’s really easy.” They even provide a video tutorial showing victims how to pay the ransom and unlock their files. They also point out that the process of unlocking files is similarly easy. Pasting the encryption key and clicking on a button to start the decryption process is all that is required.
As with the majority of crypto-ransomware variants, Spider ransomware is being distributed by spam email. The emails use the hook of ‘Debt Collection’ to encourage recipients of the email to open the attachment. That attachment is a Microsoft Office document containing an obfuscated macro. If allowed to run, the macro will trigger the download of the malicious payload via a PowerShell script.
The latest Spider ransomware campaign is being used to attack organizations in Croatia and Bosnia and Herzegovina, with the ransom note and instructions written in Croatian and English. It is possible that attacks will spread to other geographical areas.
There is currently no free decryptor for spider ransomware. Protecting against this latest ransomware threat requires technological solutions to block the attack vector. If spam emails are not delivered to end user’s inboxes, the threat is mitigated.
Using an advanced cloud-based anti-spam service such as SpamTitan is strongly advisable. SpamTitan blocks more than 99.9% of spam emails ensuring malicious email messages are not delivered.
As an additional protection against ransomware and malware threats such as this, organizations should disable macros to prevent them from running automatically if a malicious attachment is opened. IT teams should also enable the ‘view known file extensions’ option on Windows PCs to prevent attacks using double file extensions.
End users should also receive security awareness training to teach them not to engage in risky behaviors. They should be taught never to enable macros on emailed documents, told how to recognize a phishing or ransomware emails, and instructed to forward messages on to the security team if they are received. This will allow spam filter rules to be updated and the threat to be mitigated.
It is also essential for regular backups to be performed, with multiple copies stored on at least two different media, with one copy kept on an air-gapped device. Backups are the only way of recovering from most ransomware attacks without paying the ransom.
by titanadmin | Dec 11, 2017 | Email Scams, Network Security, Phishing & Email Spam, Spam News, Spam Software |
A large-scale North Carolina ransomware attack has encrypted data on 48 servers used by the Mecklenburg County government, causing considerable disruption to the county government’s activities – disruption that is likely to continue for several days while the ransomware is removed and the servers are rebuilt.
This North Carolina ransomware attack is one of the most serious ransomware attacks to have been reported this year. The attack is believed to have been conducted by individuals operating out of Ukraine or Iran and the attack is understood to have involved a ransomware variant called LockCrypt.
The attack started when a county employee opened an email attachment containing a ransomware downloader. As is now common, the email appeared to have been sent from another employee’s email account. It is unclear whether that email account was compromised, or if the attacker simply spoofed the email address.
Opening the email and malicious attachment resulted in the installation of ransomware. The infection then spread to 48 of the 500 servers used by the county. A ransom demand of $23,000 was issued by the attackers, the payment of which would see keys supplied to unlock the encryption.
While many businesses pay the ransom demands to allow them to recover files quickly and limit disruption, Mecklenburg County refused to give in to the extortionist’s demands.
After the deadline for paying the ransom passed, the individuals behind the attack attempted another email-based attack on county employees although those attempts failed.
Recovery from the attack is possible without data loss as the county has backup files that were not encrypted in the attack; however, restoring data on all the affected servers will be a slow and laborious task and the county will continue to experience severe disruption to its services.
A similarly large-scale ransomware attack hit Texas school districts in October. The attack occurred at the Texas Department of Agriculture. The Texas Department of Agriculture overseas breakfast and lunch programs at Texas Schools and has access to computer networks used by Texas school districts.
Similarly, the attack involved a single employee being fooled into downloading ransomware by a phishing email. The ransomware spread across the network affecting 39 independent Texas schools, and potentially resulting in the exposure of hundreds of student records.
Such extensive ransomware attacks are becoming much more common. Rather than simply infecting one device, ransomware is now capable of scanning networks for other vulnerable devices and rapidly spreading laterally to affect multiple computers. In the case of the Texas Department of Agriculture ransomware attack, it was rapidly identified, but not in time to prevent it spreading across the network.
As these incidents show, all it takes is for a single employee to open a malicious email attachment for an entire network of computers and servers to be taken out of action. Even if the ransom demand is paid, recovery can be a slow and costly process.
Ransomware attacks are increasing, as is the sophistication of both the ransomware and the scams that fool employees into downloading the malicious software. Fortunately, it is possible to implement defenses against these attacks.
Both of these attacks could have easily been prevented with basic security measures – An advanced and effective spam filter to prevent malicious emails from being delivered to employees and an effective security awareness training program to raise awareness of the threat from ransomware and phishing emails.
Security awareness training and phishing email simulations can reduce susceptibility to email-based cyberattacks by up to 95% according to several anti-phishing training firms, while a spam filter such as SpamTitan can ensure that employees are not tested. SpamTitan blocks more than 99.9% of spam emails, ensuring ransomware and other malware-laced emails are quarantined so they can cause no harm.
To find out more about SpamTitan and how you can secure your organization and mount an impressive defense against email and web-based threats, call the TitanHQ team today.
by titanadmin | Nov 30, 2017 | Email Scams, Phishing & Email Spam, Spam Advice, Spam News, Spam Software, Website Filtering |
Black Friday deals and Cyber Monday discounts see consumers head online in droves looking for bargain Christmas presents, but each year many thousands of consumers are fooled by holiday season email scams. This year will be no different. Scammers are already hard at work developing new ruses to fool unwary online shoppers into parting with their credentials or installing malware.
In the rush to purchase at discounted rates, security awareness often goes out the window and cybercriminals are waiting to take advantage. Hidden among the countless emails sent by retailers to advise past customers of the latest special offers and deals are a great many holiday season email scams. To an untrained eye, these scam emails appear to be no different from those sent by legitimate retailers. Then there are the phishing websites that capture credentials and credit card numbers and websites hosting exploit kits that silently download malware. It is a dangerous time to be online.
Fortunately, if you take care, you can avoid holiday season email scams, phishing websites, and malware this holiday period. To help you stay safe, we have compiled some tips to avoid holiday season email scams, phishing websites and malware this festive period.
Tips to Keep You Safe This Holiday Season
In the run up to Christmas there will be scams aplenty. To stay safe online, consider the following:
Always carefully check the URL of websites before parting with your card details
Spoofed websites often look exactly like the genuine sites that they mimic. They use the same layouts, the same imagery, and the same branding as retail sites. The only thing different is the URL. Before entering your card details or parting with any sensitive information, double check the URL of the site and make sure you are not on a scam website.
Never allow retailers to store your card details for future purchases
It is a service that makes for quick purchases. Sure, it is a pain to have to enter your card details each time you want to make a purchase, but by taking an extra minute to enter your card details each time you will reduce the risk of your account being emptied by scammers. Cyberattacks on retailers are rife, and SQL injection attacks can give attackers access to retailer’s websites – and a treasure trove of stored card numbers.
Holiday season email scams are rife – Be extra vigilant during holiday season
While holiday season email scams used to be easy to detect, phishers and scammers have become a lot better at crafting highly convincing emails. It is now difficult to distinguish between a genuine offer and a scam email. Emails contain images and company branding, are free from spelling and grammatical errors, and the email requests are highly convincing. Be wary of unsolicited emails, never open email attachments from unknown senders, and check the destination URL of any links before clicking.
If a deal sounds too good to be true, it probably is
What better time than holiday season to discover you have won a PlayStation 4 or the latest iPhone in a prize draw. While it is possible that you may have won a prize, it is very unlikely if you haven’t actually entered a prize draw. Similarly, if you are offered a 50% discount on a purchase via email, there is a high chance it is a scam. Scammers take advantage of the fact that everyone loves a bargain, and never more so than during holiday season.
If you buy online, use your credit card
Avoid the holiday season crowds and buy presents online, but use your credit card for purchases rather than a debit card. If you have been fooled by a holiday season scam or your debit card details are stolen from a retailer, it is highly unlikely that you be able to recover stolen funds. With a credit card, you have better protections and getting a refund is much more likely.
Avoid HTTP sites
Websites secured by the SSL protocol are safer. If a website starts with HTTPS it means the connection between your browser and the website is encrypted. It makes it much harder for sensitive information to be intercepted. Never give out your credit card details on a website that does not start with HTTPS.
Beware of order and delivery confirmations
If you order online, you will no doubt want to check the status of your order and find out when your purchases will be delivered. If you recent an email with tracking information or a delivery confirmation, treat the email as potentially malicious. Always visit the delivery company’s website by entering in the URL into your browser, rather than clicking links sent via email. Fake delivery confirmations and parcel tracking links are common. The links can direct you to phishing websites and sites that download malware, while email attachments often contain malware and ransomware downloaders.
Holiday season is a busy, but take your time online
One of the main reason that holiday season email scams are successful is because people are in a rush and fail to take the time to read emails carefully and check attachments and links are genuine. Scammers take advantage of busy people. Check the destination URL of any email link before you click. Take time to think before you take any action online or respond to an email request.
Don’t use the same password on multiple websites
You may choose to buy all of your Christmas gifts on Amazon, but if you need to register on multiple sites, never reuse your password. Password reuse is one of the easiest ways that hackers can gain access to your social media networks and bank accounts. If there is a data breach at one retailer and your password is stolen, hackers will attempt to use that password on other websites.
Holiday season is a time for giving, but take care online and when responding to emails to make sure your hard-earned cash is not given to scammers.
by titanadmin | Nov 30, 2017 | Email Scams, Network Security, Phishing & Email Spam, Spam News |
A spam email campaign has been detected that is distributing a form of Cobalt malware. The attackers use the Cobalt Strike penetration testing tool to take full control of an infected device. The attack uses an exploit for a recently patched Microsoft Office vulnerability.
The spam emails appear to have been sent by Visa, informing the recipient about recent changes to its payWave service. The emails contain a compressed file attachment that is password-protected. The password required to extract the contents of the zip file is contained in the body of the email.
This is an apparent attempt to make email recipients believe Visa had included security controls to prevent unauthorized individuals from viewing the information in the email – a reasonable security measure for a financial communication. Also contained in the email is a RTF file that is not password protected. Opening that file will launch a PowerShell script that will download a Cobalt Strike client that will ultimately give the attackers full control of the infected device.
The attackers leverage a vulnerability in Microsoft Office – CVE-2017-11882 – which was patched by Microsoft earlier this month. The attackers use legitimate Windows tools to execute a wide range of commands and spread laterally across a network.
The campaign was detected by researchers at Fortinet, who report that by exploiting the Office flaw, the attackers download a Cobalt Strike client and multiple stages of scripts which are then used to download the main malware payload.
The flaw has existed in Office products for 17 years, although it was only recently detected by Microsoft. Within a few days of the vulnerability being detected, Microsoft issued a patch to correct the flaw. Within a few days of the patch being released, threat actors started leveraging the vulnerability. Any device that has a vulnerable version of Office installed is vulnerable to attack.
This campaign shows just how important it is for patches to be applied promptly. As soon as a vulnerability is disclosed, malicious actors will use the vulnerability in attacks. When patches are released, malicious actors get straight to work and reverse engineer the patch, allowing them to identify and exploit vulnerabilities. As these attacks show, it may only take a few hours or days before vulnerabilities are exploited.
The recent WannaCry and NotPetya malware attacks showed just how easy it is for vulnerable systems to be exploited. Both of those attacks leveraged a vulnerability in Windows Server Message Block to gain access to systems. A patch had been released to address the vulnerability two months before the WannaCry ransomware attacks occurred. Had patches been applied promptly, it would not have been possible to install the ransomware.
Protecting against this Cobalt malware campaign is straightforward. Users simply need to apply the Microsoft patch to prevent the vulnerability from being exploited. Using a spam filter such as SpamTitan is also recommended, to prevent malicious emails from reaching end users’ inboxes.
by titanadmin | Nov 29, 2017 | Email Scams, Network Security, Phishing & Email Spam, Spam News |
Millions of spam emails containing Scarab ransomware have been detected over the past few days. The massive spam campaign is being conducted using the Necurs botnet – one of the largest botnets currently in use.
The Necurs botnet has been active for at least five years and now contains more than 6 million zombie computers that are used to send masses of spam emails. Necurs has previously been used to send banking Trojans and many other forms of malware, although recently, the operators of the botnet have turned to spreading ransomware, including Locky.
The latest campaign saw the Necurs botnet send out spam emails to more than 12.5 million email accounts in the space of just 6 hours, with individuals in the United States, France, Germany, Australia, and the UK targeted.
The emails were typical of other phishing campaigns conducted in recent months. The emails appear to have been sent from well known, trusted brands to increase the likelihood of the malicious attachments being opened. This campaign spoofs printer manufacturers such as HP, Canon, Lexmark and Epson.
The emails contain a 7zip file attachment which claims to be a scanned document, with the subject line “Scanned from [Printer company]. The zip file contains a VBScript which, if run, will download Scarab ransomware.
Scarab ransomware is a relatively new ransomware variant, first detected over the summer. While most ransomware variants have a fixed price for obtaining the key to unlock the encryption, the authors of Scarab ransomware do not ask for a specific amount. Instead, the ransom payment depends on how quickly the victim responds.
As with the NotPetya wiper, users are required to make contact with the attackers via email. This method of communication has caused problems for victims in the past, as if the domain is taken down, victims have no method of contacting the attackers. In this case, an alternative contact method is provided – victims can also contact the attackers via BitMessage.
Even though Scarab ransomware is unsophisticated, it is effective. There is no free decryptor available to recover files encrypted by Scarab ransomware. Recovery without paying the ransom is only possible if backups of the encrypted files exist, and if the backup has not also been encrypted.
Scarab ransomware is believed to be the work of relatively small players in the ransomware arena. However, the scale of the campaign and the speed at which the spam emails are being sent shows that even small players can conduct massive, global ransomware campaigns by teaming up with the operators of botnets.
By using ransomware-as-a-service, anyone can conduct a ransomware campaign. Ransomware can be hired on darknet forums for next to nothing and used to extort money from businesses. More players mean more ransomware attacks, and the ease of conducting campaigns and the fact that many victims pay up, mean ransomware is still highly profitable.
Security experts are predicting that 2018 will see even more ransomware attacks. AV firm McAfee has predicted that next year will see cybercriminal gangs step up their attacks and target high-net worth individuals and small businesses, while the campaigns will become more sophisticated.
With the threat likely to increase, businesses need to ensure that they have solutions in place to prevent ransomware from being delivered to end users. By implementing an advanced spam filtering solution, businesses can ensure that phishing and spam emails do not get delivered to end users, mitigating the threat from ransomware. Fail to block malicious emails, and it will only be a matter of time before an employee responds, opens an infected email attachment, and installs ransomware on the network.
If you are looking for the best spam filter for business use, contact the TitanHQ team today for further information on SpamTitan.
by titanadmin | Nov 20, 2017 | Email Scams, Internet Security, Network Security, Phishing & Email Spam, Spam Advice, Spam Software |
All organizations should take steps to mitigate the risk of phishing, and one of those steps should be training employees how to spot a phishing email. Employees will frequently have their phishing email identification skills put to the test.
Since all it takes is for one employee to fall for a phishing scam to compromise a network, not only is it essential that all employees are trained how to spot a phishing email, their skills should assessed post-training, otherwise organizations will not know how effective the training has been.
How Common are Phishing Attacks?
Phishing is now the number one security threat faced by businesses in all sectors. Research conducted by the security awareness training company PhishMe suggests that more than 90% of cyberattacks start with a phishing or spear phishing email. While all industry sectors have to deal with the threat from phishing, the education and healthcare industries are particularly at risk. They are commonly targeted by scammers and spammers, and all too often those phishing attacks are successful.
The Intermedia 2017 Data Vulnerability Report showed just how common phishing attacks succeed. Workers were quizzed on security awareness training and successful phishing attacks at their organizations. 34% of high level execs admitted falling for a phishing scam, as did 25% of IT professionals – Individuals who should, in theory, be the best in an organization at identifying phishing scams. The same study revealed 30% of office workers do not receive regular security awareness training. 11% said they were given no training whatsoever and have not been taught how to spot a phishing email.
Overconfidence in Phishing Detection Capabilities Results in Data Breaches
Studies on data breaches and cybersecurity defenses often reveal that many organizations are confident in their phishing defenses. However, many of those companies still suffer data breaches and fall for phishing attacks. Overconfidence in phishing detection and prevention leaves many companies at risk. This was recently highlighted by a study conducted by H.R. Rao at the University of Texas at San Antonio. Rao explained that many people believe they are smarter than phishers and scammers, which plays into the scammers’ hands.
Training Should be Put to The Test
You can train employees how to spot a phishing email, but how can you tell how effective your training has been? If you do not conduct phishing simulation exercises, you cannot be sure that your training has been effective. There will always be some employees that require more training than others and employees that do not pay attention during training. You need to find these weak links. The best way to do that is with phishing simulation exercises.
Conduct dummy phishing exercises and see whether your employees are routinely putting their training into action. If an employee fails a phishing test, you can single them out to receive further training. Each failed simulation can be taken as a training opportunity. With practice, phishing email identification skills will improve.
How to Spot a Phishing Email
Most employees receive phishing emails on a daily basis. Some are easy to identify, others less so. Fortunately spam filters catch most of these emails, but not all of them. It is therefore essential to train employees how to spot a phishing email and to conduct regular training sessions. One training session a year is no longer sufficient. Scammers are constantly changing tactics. It is important to ensure employees are kept up to speed on the latest threats.
During your regular training sessions, show your employees how to spot a phishing email and what to do when they receive suspicious messages. In particular, warn them about the following tactics:
Spoofed Display Names
The 2017 Spear Phishing Report from GreatHorn indicates 91% of spear phishing attacks spoof display names. This tactic makes the recipient believe the email has been sent from a trusted colleague, friend, family member or company. This is one of the most important ways to spot a phishing email.
Mitigation: Train employees to hover their mouse arrow over the sender to display the true email address. Train employees to forward emails rather than reply. The true email address will be displayed.
Email Account Compromises
This year, business email compromise (BEC) scams have soared. These scams were extensively used to obtain W-2 Form tax information during tax season. This attack method involves the use of real email accounts – typically those of the CEO or senior executives – to send requests to employees to make bank transfers and send sensitive data.
Mitigation: Implement policies that require any email requests for sensitive information to be verified over the phone, and for all new bank transfer requests and account changes to be verified.
Hyperlinks to Phishing Websites
The Proofpoint Quarterly Threat Report for Q3 showed there was a 600% increase in the use of malicious URLs in phishing emails quarter over quarter, and a 2,200% increase from this time last year. These URLs usually direct users to sites where they are asked to login using their email credentials. Oftentimes they link to sites where malware is silently downloaded.
Mitigation: Train employees to hover their mouse arrow over the URL to display the true URL. Encourage employees to visit websites by entering the URL manually, rather than using embedded links.
Security Alerts and Other Urgent Situations
Scammers want email recipients to take action quickly. The faster the response the better. If employees stop and think about the request, or check the email carefully, there is a high chance the scam will be detected. Phishing emails often include some urgent request or immediate need for action. “Your account will be closed,” “You will lose your credit,” “Your parcel will not be delivered,” “Your computer is at risk,” Etc.
Mitigation: Train employees to stop and think. An email request may seem urgent and contain a threat, but this tactic is commonly used to get people to take quick action without engaging their brains.
Look for Spelling Mistakes and Grammatical Errors
Many phishing scams come from African countries, Eastern Europe and Russia – Places where English is not the main language. While phishing scams are becoming more sophisticated, and more care is taken crafting emails, spelling mistakes and poor grammar are still common and are a key indicator that emails are not genuine.
Mitigation: Train employees to look for spelling mistakes and grammatical errors. Companies check their emails carefully before sending them.
Why a Spam Filter is Now Essential
Training employees how to spot a phishing email should be included in your cybersecurity strategy, but training alone will not prevent all phishing-related data breaches. There may be a security culture at your organizations, and employees skilled phish detectors, but every employee can have an off day from time to time. It is therefore important to make sure as few phishing emails as possible reach employees’ inboxes, and for that to happen, you need an advanced spam filtering solution.
SpamTitan blocks more than 99.9% of spam email and includes dual anti-virus engines to ensure malicious messages are blocked. The low false positive rate also ensures genuine emails do not trigger the spam filter and are delivered.
If you want to improve your security defenses, train employees how to spot a phishing email and implement SpamTitan to stop phishing emails from reaching inboxes. With technological and human solutions you will be better protected.
Handy Infographic to Help Train Staff How to Spot a Phishing Email
We have compiled a useful infographic to highlight how important it is to train staff how to spot a phishing email and some of the common identifiers that an email is not genuine:
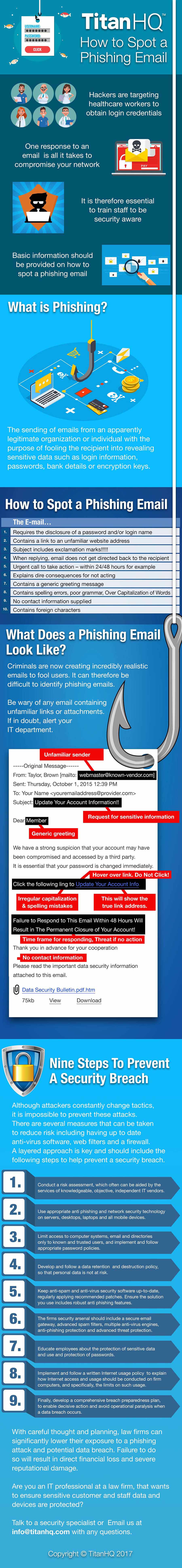
by titanadmin | Nov 17, 2017 | Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News |
The Ponemon Institute has published the findings of a new report on endpoint security risk, which shows that ransomware attacks have occurred at most companies, the risk of fileless malware attacks has increased significantly, and successful cyberattacks are resulting in average losses of more than $5 million.
For the Barkly-sponsored endpoint security risk study, the Ponemon Institute surveyed 665 IT security professionals that were responsible for the management of their organization’s security risk.
7 out of ten respondents claimed endpoint security risk was significantly higher this year than in 2016, and one of the biggest threats was now fileless malware. Companies are still using traditional anti-virus and anti-malware solutions, although they are not effective at preventing fileless malware attacks.
Fileless malware is not detected by most anti-virus solutions since no files are written to the hard drive. Instead, fileless malware remains in the memory, oftentimes leveraging legitimate system tools to gain persistence and spread to other devices on the network.
These fileless malware attacks are occurring far more frequently, with respondents estimating a 20% rise in attacks in 2017. 29% of all cyberattacks in 2017 involved fileless malware, and the threat is expected to continue to increase, and will account for more than a third of all attacks in 2018.
The switch from file-based malware to fileless malware is understandable. The attacks are often successful. 54% of companies surveyed said they had experienced at least one cyberattack that resulted in data being compromised, and 77% of those attacks involved exploits or fileless malware. 42% of respondents said they had experienced a fileless malware attack that resulted in systems or data being compromised in 2017.
Fileless malware attacks are increasing, but so are ransomware attacks. Over half of companies that took part in the endpoint security risk study said they had experienced at least one ransomware attack in 2017, while four out of ten firms experienced multiple ransomware attacks. Even though most companies backup their files, 65% of respondents said they had paid a ransom to recover their data, with the average amount being $3,675. The primary method of ransomware delivery is email.
While the ransom payments may be relatively low, that represents only a small proportion of the costs of such attacks. For the endpoint security risk study, firms were asked to estimate the total cost of cyberattacks – On average, each successful attack on endpoints cost an average of $5,010,600 to resolve – $301 per employee.
Protect Against Malware Attacks by Blocking the Primary Delivery Vector
Email is the primary method for distributing malware. Implementing a spam filtering solution, preferably a gateway solution, can keep an organization protected from malicious emails and will prevent malicious messages from being delivered to end users, and is important for helping organizations manage endpoint security risk.
Many companies opt for an email gateway filtering appliance – an appliance located between the firewall and email server. These solutions are powerful, but they come at a cost since the appliance must be purchased. These appliance-based solutions also lack scalability.
If you want the power of an appliance, but want to keep costs to a minimum, consider a solution such as SpamTitan. SpamTitan offers the same power as a dedicated appliance, without the need to purchase any additional hardware. SpamTitan can be deployed as a virtual appliance on existing hardware, offering the same level of protection as an email gateway filtering appliance at a fraction of the cost.
Don’t Forget to Train Your Employees to be More Security Conscious
A recent InfoBlox survey on healthcare organizations in the United States and United Kingdom revealed that companies in this sector are realizing the benefits of training employees to be more security aware, although only 35% of firms currently provide training to employees.
No matter what email filtering solution you use, there will be times when spammers succeed, and messages are delivered. It is therefore important that staff are trained how to identify and respond to suspicious emails. If end users are not aware of the threats, and do not know how to recognize potential phishing emails, there is a higher chance of them engaging in risky behavior and compromising their device and the network.
by titanadmin | Nov 17, 2017 | Industry News, Network Security, Phishing & Email Spam, Spam Advice, Spam News |
A serious MS Office remote code execution vulnerability has been patched by Microsoft – One that would allow malware to be installed remotely with no user interaction required. The flaw has been present in MS Office for the past 17 years.
The flaw, which was discovered by researchers at Embedi, is being tracked as CVE-2017-11882. The vulnerability is in the Microsoft Equation Editor, a part of MS Office that is used for inserting and editing equations – OLE objects – in documents: Specifically, the vulnerability is in the executable file EQNEDT32.exe.
The memory corruption vulnerability allows remote code execution on a targeted computer, and would allow an attacker to take full control of the system, if used with Windows Kernel privilege exploits. The flaw can be exploited on all Windows operating systems, including unpatched systems with the Windows 10 Creators Update.
Microsoft addressed the vulnerability in its November round of security updates. Any unpatched system is vulnerable to attack, so it is strongly advisable to apply the patch promptly. While the vulnerability could potentially have been exploited at any point in the past 17 years, attacks exploiting this MS Office remote code execution vulnerability are much more likely now that a patch has been released.
The flaw does not require the use of macros, only for the victim to open a specially crafted malicious Office document. Malicious documents designed to exploit the vulnerability would likely arrive via spam email, highlighting the importance of implementing a spam filtering solution such as SpamTitan to block the threat.
End users who are fooled into opening a malicious document can prevent infection by closing the document without enabling macros. In this case, malware would be installed simply by opening the document.
Microsoft has rated the vulnerability as important, rather than critical, although researchers at Embedi say this flaw is “extremely dangerous.” Embedi has developed a proof of concept attack that allowed them to successfully exploit the vulnerability. The researchers said, “By inserting several OLEs that exploited the described vulnerability, it was possible to execute an arbitrary sequence of commands (e.g. to download an arbitrary file from the Internet and execute it),”
EQNEDT32.exe is run outside of the Microsoft Office environment, so it is therefore not subject to Office and many Windows 10 protections. In addition to applying the patch, security researchers at Embedi recommend disabling EQNEDT32.EXE in the registry, as even with the patch applied, the executable still has a number of other vulnerabilities. Disabling the executable will not impact users since this is a feature of Office that is never needed by most users.
by titanadmin | Nov 15, 2017 | Email Scams, Network Security, Phishing & Email Spam, Spam News |
Ordinypt malware is currently being used in targeted attacks on companies in Germany. While Ordinypt malware appears to victims to be ransomware, the malware is actually a wiper.
Infection sees files made inaccessible, and as with ransomware, a ransom demand is issued. The attackers ask for 0.12 Bitcoin – around $836 – to restore files.
Ordinypt malware does not encrypt files – it simply deletes the original file name and replaces it with a random string of letters and numbers. The contents of files are also replaced with random letters and numbers.
Even if the ransom demand is paid, the attackers do not have a mechanism to allow victims to recover their original files. The only sure-fire way to recover files is to restore them from a backup. In contrast to many ransomware variants that make it difficult to recover files by deleting Windows Shadow Volume copies, those are left intact, so it may be possible for users to recover some of their files.
Ordinypt malware – or HSDFSDCrypt as it was originally known – was discovered by Michael Gillespie. A sample of the malware was obtained and analyzed by German security researcher Karsten Hahn from G Data Security. G Data Security renamed the malware Ordinypt.
Hahn notes that Ordinypt malware is poorly written with a bad coding style, indicating this is not the work of a skilled hacker. Hahn said, this is “A stupid malware that destroy information of enterprises and innocent people and try steal money.”
The attackers are using a common technique to maximize the number of infections. The malware is disguised as PDF files which are distributed via spam email. The messages claim to be applications in reply to job adverts. Two files are included in a zip file attachment, which appear to be a resume and a CV.
While the files appear to be PDFs, and are displayed as such, they actually have a double extension. If the user’s computer has file extensions hidden, all that will be displayed is filename.pdf, when in actual fact the file is filename.pdf.exe. Clicking on either of the files will run the executable and launch Ordinypt malware.
In recent months there have been several wiper malware variants detected that pretend to be ransomware. The attackers are taking advantage of the publicity surrounding ransomware attacks, and are fooling end users into paying a ransom, when there is no way of recovering files. It is not clear whether the reason for the attacks is to make money. It is possible that these attacks are simply intended to cause disruption to businesses, as was the case with the NotPetya wiper attacks.
Regardless of how poorly written this malware is, it is still effective and can cause significant disruption to businesses. Protecting against this, and other email-based malware threats, requires a combination of end user training and technology.
End users should be informed of the risks of opening attachments from unknown senders and should assume that all such emails could be malicious. In this case, the malware is poorly written but the emails are not. They use perfect German and are highly believable. HR employees could be easily fooled by a ruse such as this.
The best protection against threats such as these is an advanced spam filter such as SpamTitan. Preventing these emails from reaching inboxes is the best defense.
By configuring the spam filter to block executable files, the messages will be rerouted to a quarantine folder rather than being delivered, mitigating the threat.
For further information on how a spam filter can help to block email-based threats and to register for a free trial of SpamTitan for your business, contact the TitanHQ team today.