Industry News
Our industry news section covers a broad range of news items of particular relevance to the cybersecurity industry and managed service providers (MSPs).
This section also included details of the latest white papers and research studies relating to malware, ransomware, phishing and data breaches. These articles provide some insight into the general state of cybersecurity, the industries currently most heavily targeted by cybercriminals, and figures and statistics for your own reports.
Hackers and scammers conduct massive spam campaigns designed to infect as many computers as possible. These attacks are random, using email addresses stolen in large data breaches such as the cyberattacks on LinkedIn, MySpace, Twitter and Yahoo. However, highly targeted attacks are increasing in frequency, with campaigns geared to specific industries. These industry-specific cyberattacks and spam and malware campaigns are detailed in this section, along with possible mitigations for reducing the risk of a successful attack.
This category is therefore of relevance to organizations in the education, healthcare, and financial services industries – the most common attacked industries according to recent security reports.
The articles contain information about current campaigns, spam email identifiers and details of the social engineering tactics used to fool end users and gain access to business networks. By following the advice in these articles, it may be possible to prevent similar attacks on your organization.

by titanadmin | Mar 13, 2019 | Industry News, Network Security, Phishing & Email Spam, Spam News, Spam Software |
This week, TitanHQ has rolled out two new features for its award-winning email security solution SpamTitan: Sandboxing and DMARC email authentication.
TitanHQ developed the technology behind its email security solution more than 20 years ago and over the past two decades SpamTitan has received many updates to improve features for end users and increase detection rates.
SpamTitan already blocks more than 99.9% of spam and malicious emails to prevent threats from reaching end users’ inboxes. The level of protection SpamTitan provides against email attacks has made it the gold standard in email security for the SMB market and managed service providers serving SMBs.
In order to provide even greater protection against increasingly sophisticated email threats, TitanHQ added a new sandboxing feature. The next-generation sandboxing feature, powered by Bitdefender, provides SpamTitan customers with a safe environment to run in-depth analyses of suspicious programs and files that have been delivered via email.
New SpamTitan Sandboxing Service
The sandbox is a powerful virtual environment totally separate from other systems. When programs are run in the sandbox, they behave as they would on an ordinary endpoint and can be assessed for suspicious behavior and malicious actions without causing harm.
Prior to being sent to the sandbox, files are first analyzed using SpamTitan’s anti-malware technologies. Only files that require further analysis make it to the sandbox where they are safely detonated. Tactics used by malware to evade detection and avoid analysis are logged and flagged. Purpose-built, advanced machine learning algorithms they assess the files and check their actions against an extensive array of known threats from a range on online repositories in a matter of minutes.
If the file is confirmed as benign, it can be released. If the file is determined to be malicious, the sandboxing service automatically sends a report to the Bitdefender’s Global Protective Network and all further instances of the threat will then be blocked globally to ensure the file does not need to be analysed again.
Email sandboxing provides advanced protection against zero-day exploits, polymorphic threats, APTs, malicious URLs, new malware samples that have yet to be identified as malicious, and new threats that have been developed for undetectable targeted attacks.
Incorporation of this feature into SpamTitan gives customers advanced emulation-based malware analysis capabilities without having to purchase a separate sandboxing solution and ensures customers are protected against rapidly evolving advanced threats.
DMARC Email Authentication Added to SpamTitan
Email spoofing is the term given to the use of a forged sender address. Email spoofing is used to increase the likelihood of an email being delivered and opened by an end user. The email address of a known contact, well known company, or government organization is usually spoofed to abuse trust in that individual, brand, or organization.
DMARC authentication is now essential for all businesses and is a powerful control to prevent spoofing attacks. DMARC is used to check email headers to provide further information about the true sender of an email. Through DMARC, the message is authenticated as having been sent from the organization that owns the domain. If authentication fails, the message is rejected.
While SPF provides a certain degree of protection against email spoofing, DMARC is far more dependable. SpamTitan now incorporates DMARC authentication to provide even greater protection against email spoofing attacks.
Both of these new features have been added in the latest update to SpamTitan and are available to users at no extra cost.
“We have listened to requests from customers to have new features added to SpamTitan, and by far the most requested improvements are anti-spoofing technology and sandboxing,” said Ronan Kavanagh, CEO, TitanHQ. “I’m delighted to say that both of these new features have now been added to provide enhanced security for customers at no extra cost.”
by titanadmin | Feb 14, 2019 | Industry News, Spam Software, Website Filtering |
TitanHQ is on the road again and has kick started a busy 2019 schedule of conferences with events on both sides of the Atlantic.
On February 14, 2019, TitanHQ Alliance Manager Patrick Regan attended the TitanHQ-sponsored Datto Roadshow in Tampa, Florida, and has been meeting with MSP partners from the region to help them with their existing and new email security, DNS filtering, and email archiving projects. TitanHQ has been working very closely with Datto MSP partners to ensure they get the most out of TitanHQ products to better support their clients.
On the other side to the pond, TitanHQ Alliance Manager Eddie Monaghan kicked off a week at the IT Nation Q1 EMEA Meeting in London and has been meeting MSP clients and finding what is going in in their world.

TitanHQ Alliance Manager, Eddie Monaghan
At both locations and in the upcoming roadshow events the TitanHQ team is available to meet with prospective MSP partners to explain about TitanHQ’s award-winning email security (SpamTitan), web security (WebTitan) and email archiving (ArcTitan) solutions and how they can easily be slotted into MSPs security stacks to better help and protect their clients. Current MSP partners will be given tips to help them get the very most out of the products.

Partner with TitanHQ
TitanHQ is the leading provider of email and web security products for MSPs serving the SMB market and now provides its products to more than 1,500 MSP partners serving clients in more than 200 countries. The combination of SpamTitan and WebTitan allows MSPs to provide their clients with superior protection against malware, ransomware, phishing and other cyber threats.
All TitanHQ products have been developed to specifically meet the needs of MSPs and save them support and engineering time by blocking cyber threats at source.
TitanHQ has developed it’s TitanShield Program to help partners in a wide range of industry sectors take advantage of TitanHQ’s suite of products. The TitanShield Program consists of four elements which meet the needs of MSP, ISP, and technology partners:
The MSP Program: Allows MSPs and resellers adopt the TitanHQ platform and security solutions to provide TitanHQ products direct to their clients.
The OEM program: TitanHQ’s entire suite of products is supplied in white-label form ready to take your company’s branding.
The Technology Alliance Program: Allows tech companies to partner with TitanHQ to offer spam filtering, web filtering, and email archiving solutions to clients alongside their own products.
The Wi-Fi Program: A program for Wi-Fi providers allowing the incorporation of TitanHQ’s cloud-based WiFi content filtering solution partners’ WiFi services.
Over the coming few months, TitanHQ will be visiting Dublin, heading across the channel to the Netherlands, and will be travelling through the UK and United States. If you are a current MSP partner or are interested in finding out how TitanHQ products could benefit your clients and be slotted into your technology stack, be sure to come and meet the team at one the following events.
We look forward to seeing you at one of the roadshow events in 2019.
TitanHQ 2019 MSP Roadshow Dates
|
February 2019
|
| Date |
Event |
Location |
| February 14, 2019 |
IT Nation (HTG) Q1 EMEA Meeting |
London, UK |
| February 14, 2019 |
Datto Roadshow |
Tampa, FL, USA |
|
March 2019
|
| Date |
Event |
Location |
| March 5, 2019 |
CompTIA UK Channel Community |
Manchester, UK |
| March 7, 2019 |
Datto Roadshow EMEA |
Dublin, IE |
| March 11, 2019 |
CompTIA Community Forum |
Chicago, IL, USA |
| March 12, 2019 |
Datto Roadshow NA |
Norwalk, CT, USA |
| March 19, 2019 |
Datto Roadshow EMEA |
London, UK |
| March 26, 2019 |
Datto Roadshow EMEA |
Houten, Netherlands |
| March 26, 2019 |
Datto Roadshow NA |
Toronto, Canada |
|
April 2019
|
| Date |
Event |
Location |
| April 25, 2019 |
Datto Roadshow |
Long Island, NY, USA |
| April 29, 2019 |
IT Nation Evolve (HTG 2) |
Dallas, TX, USA |
|
May 2019
|
| Date |
Event |
Location |
| May 6, 2019 |
Connect IT Global (Kaseya Connect) |
Las Vegas, NV, USA |
| May 13, 2019 |
IT Nation (HTG) Q1 EMEA Meeting |
Birmingham, UK |
| May 14, 2019 |
Wifi Now |
Washington DC, USA |
|
June 2019
|
| Date |
Event |
Location |
| June 17, 2019 |
DattoCon |
San Diego, CA, USA |
by titanadmin | Feb 13, 2019 | Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News, Spam Software, Website Filtering |
The 2019 Cybersecurity Survey conducted by the Healthcare Information and Management Systems Society (HIMSS) has highlighted healthcare email security weaknesses and the seriousness of the threat of phishing attacks.
HIMSS conducts the survey each year to identify attack trends, security weaknesses, and areas where healthcare organizations need to improve their cybersecurity defenses. This year’s survey confirmed that phishing remains the number one threat faced by healthcare organizations and the extent that email is involved in healthcare data breaches.
This year’s study was conducted on 166 healthcare IT leaders between November and December 2018. Respondents were asked questions about data breaches and security incidents they had experienced in the past 12 months, the causes of those breaches, and other cybersecurity matters.
Phishing attacks are pervasive in healthcare and a universal problem for healthcare providers and health plans of all sizes. 69% of significant security incidents at hospitals in the past 12 months used email as the initial point of compromise. Overall, across all healthcare organizations, email was involved in 59% of significant security incidents.
The email incidents include phishing attacks, spear phishing, whaling, business email compromise, and other email impersonation attacks. Those attacks resulted in network breaches, data theft, email account compromises, malware infections, and fraudulent wire transfers.
When asked about the categories of threat actors behind the attacks, 28% named ‘online scam artists’ and 20% negligence by insiders. Online scam artists include phishers who send hyperlinks to malicious websites via email. It was a similar story the previous year when the survey was last conducted.
Given the number of email-related breaches it is clear that anti-phishing defenses in healthcare need to be improved. HIPAA requires all healthcare employees to receive security awareness training, part of which should include training on how to identify phishing attacks. While this is a requirement for compliance, a significant percentage (18%) of healthcare organizations do not take this further and are not conducting phishing simulations, even though they have been shown to improve resilience against phishing attacks by reinforcing training and identifying weaknesses in training programs.
The continued use of out of date and unsupported software was also a major concern. Software such as Windows Server and Windows XP are still extensively used in healthcare, despite the number of vulnerabilities they contain. 69% of respondents admitted still using legacy software on at least some machines. When end users visit websites containing exploit kits, vulnerabilities on those devices can easily be exploited to download malware.
It may take some time to phase out those legacy systems, but improving healthcare email security is a quick and easy win. HIMSS recommends improving training for all employees on the threat from phishing with the aim of decreasing click rates on phishing emails. That is best achieved through training, phishing simulations, and better monitoring of responses to phishing emails to identify repeat offenders.
At TitanHQ, we can offer two further solutions to improve healthcare email security. The first is an advanced spam filtering solution that blocks phishing emails and prevents them from being delivered to inboxes. The second is a solution that prevents employees from visiting phishing and other malicious websites such as online scams.
SpamTitan is an advanced anti-phishing solution that scans all incoming emails using a wide range of methods to identify malicious messages. The solution has a catch rate in excess of 99.9% with a false positive rate of just 0.03%. The solution also scans outbound messages for spam signatures to help identify compromised email accounts.
WebTitan Cloud is a cloud-based web filtering solution that blocks attempts by employees to visit malicious websites, either through web surfing or responses to phishing emails. Should an employee click on a link to a known malicious site, the action will be blocked before any harm is caused. WebTitan also scans websites for malicious content to identify and block previously known phishing websites and other online scams. Alongside robust security awareness training programs, these two solutions can help to significantly improve healthcare email security.
For further information on TitanHQ’s healthcare email security and anti-phishing solutions, contact TitanHQ today.
by titanadmin | Dec 19, 2018 | Industry News, Spam Software |
G2 Crowd, the trusted business software review platform, has recognized SpamTitan as a High Performer for email security. The anti-spam solution has been praised for speed of implementation, ease of use, quality of support, and its spam filtering capabilities.
Finding the right software solution can take a lot of time and effort. Even when software is carefully and painstakingly reviewed, making a purchase can be risky. G2 Crowd helps businesses find the most suitable software and services and make informed buying decisions, taking the guesswork out of software selection.
The G2 Crowd platform contains more than half a million independent, authenticated reviews from users of software solutions that give honest feedback on software solutions after having put them through their paces. The platform is trusted by businesses and its user reviews are read by more than 2 million buyers every month.
This December, G2 Crowd released its Winter Secure Email Gateway Grid℠, which ranked SpamTitan as the highest performer in the mid-market segment. According to G2 Crowd, “High Performers provide products that are highly rated by their users,” and have achieved consistently positive reviews from the people that matter – customers.
The high position is due to consistent 5-star reviews from users. 93% of user-reviewers on the site have awarded SpamTitan 5 stars out of 5, with the remaining 7% giving the solution 4 stars out of 5. SpamTitan has attracted praise across the board, notably for how easy it is to set up, use, maintain, its reporting tools, the quality of customer support, and price.
SpamTitan has also been rated as a 5-star email security solution by users of Spiceworks and has won more than 37 consecutive Virus Bulletin Spam awards.
Not only is SpamTitan an ideal solution for SMBs to block spam email, malware, and phishing threats, it has been developed to also meet the needs of managed services providers to allow them to easily add spam filtering and phishing protection to their service stacks.
SpamTitan is available with three deployment choices: SpamTitan Gateway, SpamTitan Cloud, and SpamTitan Private Cloud, to meet the needs of all businesses.
Check out the SpamTitan reviews on G2 Crowd and contact TitanHQ to schedule a product demonstration. SpamTitan is also available on a free 14-day trial to allow you to test the solution for yourself in your own environment.
by titanadmin | Dec 8, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News, Spam Software |
There has been an increase in phishing attacks on retailers, supermarket chains, and restaurants in recent weeks. The aim of the phishing attacks is to deliver remote access Trojans and remote manipulator software to gain persistent access to computers and, ultimately, obtain banking credentials and sensitive customer data on POS systems.
Several new campaigns have been detected in recent weeks targeting retail and food sector companies, both of which are well into the busiest time of the year. With employees working hard, it is likely that less care will be taken opening emails which gives cybercriminals an opportunity.
PUB Files Used in Phishing Attacks on Retailers
Over the past few weeks, security researchers have noted an uptick in phishing attacks on retailers, with one threat group switching to using.pub files to install malware. Many phishing attacks use Word documents containing malicious macros. The use of macros with .pub files is relatively uncommon. The change to this new attachment type may fool employees, as they will be less likely to associate these files with cyberattacks.
Social engineering techniques are used to fool end users into opening the files, with the .pub files masquerading as invoices. Many emails have been intercepted that appear to have been sent from within a company, which helps to make the files appear genuine.
If opened, the .pub files, via malicious macros, run Microsoft Installer (MSI) files that deliver a remote access Trojan. Since these installers will most likely be familiar to end users, they may not realize the installers are malicious. Further, the MSI files are time delayed so they do not run immediately when the .pub files are opened, increasing the probability that the RAT downloads will go unnoticed.
The TA505 threat group is using this tactic to install the FlawedAmmy remote access Trojan and other malicious payloads such as Remote Manipulator System (RMS) clients.
The phishing emails used to deliver these malicious files are targeted and tailored to a specific business to increase the likelihood of success. These targeted spear phishing attacks are now becoming the norm, as threat actors move away from the spray and pray tactics of old.
Cape Cod Community College Phishing Attack Results in Theft of More Than $800,000
Phishing attacks on retailers have increased, but other industries are also at risk. Educational institutions are also prime targets, as has been highlighted by a recent phishing attack on Cape Cod Community College.
The Cape Cod Community College phishing attack involved sophisticated messages that delivered malware capable of evading the college’s anti-virus software. The malware was used to obtain the banking credentials of the college, and once those credentials had been obtained, the hackers proceeded to make fraudulent transfers and empty bank accounts. Transfers totaling $807,130 were made, and so far, the college and its bank have only been able to recover $278,887.
All too often, fraudulent transfers are not detected quickly enough to recover any funds. Once the transfers have cleared the attacker-controlled bank accounts are emptied, after which the probability of recovering funds falls to near zero.
Defense in Depth the Key to Phishing Protection
Email is the primary vector used to phish for sensitive information and deliver malware to businesses. Regardless of whether businesses use local email systems or cloud-based email services such as Office 365, advanced spam filtering controls are required to block threats. For instance, SpamTitan blocks more than 99.9% of spam email and 100% of known malware. SpamTitan also uses heuristics, machine learning, and Bayesian analysis to identify previously unseen threats – One of the areas of weakness of Office 365’s anti-phishing defenses.
Network segmentation is also essential. Critical services must be separated to ensure that the installation of malware or ransomware on one device will not allow the attackers to gain access to the entire network. This is especially important for retailers and other businesses with POS systems. Network segmentation will help to keep POS systems and the financial data of customers secure.
Advanced endpoint protection solutions offer far greater protection than standard antivirus solutions and are less reliant on malware signatures. Standard AV solutions will only block known malware. With standard AV solutions, new malware variants can easily slip through the net.
End user security awareness training should be mandatory for all employees and training needs to be a continuous process. A once a year training session is no longer sufficient. Regular training throughout the year is required to ensure employees are made aware of the latest threats and tactics being used to gain access to login credentials and install malware.
For further information on improving email security to improve protection against phishing attacks, contact the TitanHQ team today.
by titanadmin | Oct 26, 2018 | Email Scams, Industry News, Phishing & Email Spam, Spam Advice, Spam Software |
Financial institutions, healthcare organizations and universities have seen an increase in cyberattack in recent months, but there has also been an increase in phishing attacks on publishers and literary scouting agencies.
Any business that stores sensitive information that can be monetized is at risk of cyberattacks, and publishers and literary scouting agencies are no exception. Like any employer, scouting agencies and publishers store sensitive information such as bank account numbers, credit card details, Social Security numbers, contract information, and W-2 Tax forms, all of which carry a high value on the black market. The companies also regularly make wire transfers and are therefore targets for BEC scammers.
However, in a somewhat new development, there have been several reports of phishing attacks on publishers and literary scouting agencies that attempt to gain access to unpublished manuscripts and typescripts. These are naturally extremely valuable. If an advance copy of an eagerly awaited book can be obtained before it is published, there will be no shortage of fans willing to pay top dollar for a copy. Theft of manuscripts can result in extortion attempts with ransoms demanded to prevent their publication online.
2018 has seen a significant increase in phishing attacks on publishers and literary scouting agencies. Currently, campaigns are being conducted by scammers that appear to have a good understanding of the industry. Highly realistic and plausible emails are being to publishing houses and agencies which use the correct industry terminology, which suggests they are the work of an industry insider.
One current campaign is spoofing the email account of Catherine Eccles, owner of the international literary scouting agency Eccles Fisher. Emails are being sent using Catherine Eccles’ name, and include her signature and contact information. The messages come from what appears to be her genuine email account, although the email address has been spoofed and replies are directed to an alternative account controlled by the scammer. The messages attempt to get other literary agencies to send manuscripts via email or disclose their website passwords.
An increase in phishing attacks on publishers on both sides of the Atlantic have been reported, with the threat already having prompted Penguin Random House North America to send out warnings to employees to alert them to the threat. According to a recent report in The Bookseller, several publishers have been targeted with similar phishing schemes, including Penguin Random House UK and Pan Macmillan.
Protecting against phishing attacks requires a combination of technical solutions, policies and procedures, and employee training.
Publishers and scouting agencies should deploy software solutions that can block phishing attacks and prevent malicious emails from being delivered to their employees’ inboxes.
SpamTitan is a powerful anti-phishing tool that blocks 99.97% of spam emails and 100% of known malware. DMARC email-validation is incorporated to detect email spoofing and prevent malicious emails from reaching employees’ inboxes.
End user training is also essential to raise awareness of the risks of phishing. All staff should be trained how to recognize phishing emails and other email threats to ensure they do not fall for these email scams.
If you run a publishing house or literary scouting agency and are interested in improving your cyber defenses, contact the TitanHQ team today for further information on cybersecurity solutions that can improve your security posture against phishing and other email and web-based threats.
by titanadmin | Oct 25, 2018 | Email Scams, Industry News, Phishing & Email Spam, Spam News, Spam Software, Website Filtering |
Hackers have been going back to school and entering higher education. Quite literally in fact, although not through conventional channels. Entry is gained through cyberattacks on universities, which have increased over the course of the past 12 months, according to figures recently released by Kaspersky Lab.
Cyberattacks on Universities on the Rise
Credit cards information can be sold for a few bucks, but universities have much more valuable information. As research organizations they have valuable proprietary data. The results of research studies are particularly valuable. It may not be possible to sell data as quickly as credit cards and Social Security numbers, but there are certainly buyers willing to pay top dollar for valuable research. Nation state sponsored hacking groups are targeting universities and independent hacking groups are getting in on the act and conducting cyberattacks on universities.
There are many potential attack vectors that can be used to gain access to university systems. Software vulnerabilities that have yet to be patched can be exploited, misconfigured cloud services such as unsecured S3 buckets can be accessed, and brute force attempts can be conducted to guess passwords. However, phishing attacks on universities are commonplace.
Phishing is often associated with scams to obtain credit card information or login credentials to Office 365 accounts, with businesses and healthcare organizations often targeted. Universities are also in the firing line and are being attacked.
The reason phishing is so popular is because it is often the easiest way to gain access to networks, or at least gain a foothold for further attacks. Universities are naturally careful about guarding their research and security controls are usually deployed accordingly. Phishing allows those controls to be bypassed relatively easily.
A successful phishing attack on a student may not prove to be particularly profitable, at least initially. However, once access to their email account is gained, it can be used for further phishing attacks on lecturers for example.
Spear phishing attacks on lecturers and research associates offer a more direct route. They are likely to have higher privileges and access to valuable research data. Their accounts are also likely to contain other interesting and useful information that can be used in a wide range of secondary attacks.
Email-based attacks can involve malicious attachments that deliver information stealing malware such as keyloggers, although many of the recent attacks have used links to fake university login pages. The login pages are exact copies of the genuine login pages used by universities, the only difference being the URL on which the page is located.
More than 1,000 Phishing Attacks on Universities Detected in a Year
According to Kaspersky Lab, more than 1,000 phishing attacks on universities have been detected in the past 12 months and 131 universities have been targeted. Those universities are spread across 16 countries, although 83/131 universities were in the United States.
Preventing phishing attacks on universities, staff, and students requires a multi layered approach. Technical controls must be implemented to reduce risk, such as an advanced spam filter to block the vast majority of phishing emails and stop them being delivered to end users. A web filtering solution is important for blocking access to phishing websites and web pages hosting malware. Multi-factor authentication is also essential to ensure that if account information is compromised or passwords are guessed, an additional form of authentication is required to access accounts.
As a last line of defense, staff and students should be made aware of the risk from phishing. Training should be made available to all students and cybersecurity awareness training for researchers, lecturers, and other staff should be mandatory.
by titanadmin | Oct 17, 2018 | Email Scams, Industry News, Network Security, Phishing & Email Spam |
In 2015, Anthem Inc., experienced a colossal data breach. 78.8 million health plan records were stolen. This year, the health insurer settled a class action data breach for $115 million and OCR has now agreed a $16 million Anthem data breach settlement.
It Started with a Spear Phishing Email…
The Anthem data breach came as a huge shock back in February 2015, due to the sheer scale of the breach. Healthcare data breaches were common, but the Anthem data breach in a different league.
Prior to the announcement, the unenviable record was held by Science Applications International Corporation, a vendor used by healthcare organizations, that experienced a 4.9 million record breach in 2011. The Anthem data breach was on an entirely different scale.
The hacking group behind the Anthem data breach was clearly skilled. Mandiant, the cybersecurity firm that assisted with the investigation, suspected the attack was a nation-state sponsored cyberattack. The hackers managed to gain access to Anthem’s data warehouse and exfiltrated a huge volume of data undetected. The time of the initial attack to discovery was almost a year.
While the attack was sophisticated, a foothold in the network was not gained through an elaborate hack or zero-day exploit but through phishing emails.
At least one employee responded to a spear phishing email, sent to one of Anthem’s subsidiaries, which gave the attackers the entry point they needed to launch a further attack and gain access to Anthem’s health plan member database.
The Anthem Data Breach Settlement is the Largest Ever Penalty for a Healthcare Data Breach
The U.S. Department of Health and Human Services’ Office for Civil Rights (OCR) investigates healthcare data breaches that result in the exposure or theft of 500 or more records. An in-depth investigation of the Anthem breach was therefore a certainty given its scale. A penalty for non-compliance with Health Insurance Portability and Accountability Act (HIPAA) Rules was a very likely outcome as HIPAA requires healthcare organizations to safeguard health data. The scale of the breach also made it likely that it would result in the largest ever penalty for a healthcare data breach.
Before the Anthem data breach settlement, the largest penalty for a healthcare data breach was $5.55 million, which was agreed between OCR and Advocate Health Care Network in 2016. The Anthem data breach settlement was almost three times that amount, which reflected the seriousness of the breach, the number of people impacted, and the extent to which HIPAA Rules were alleged to have been violated.
OCR alleged that Anthem Inc., had violated five provisions of HIPAA Rules, and by doing so failed to prevent the breach and limit its severity. The Anthem data breach settlement was however agreed with no admission of liability.
The regulatory fine represents a small fraction of the total cost of the Anthem data breach. On top of the Anthem data breach settlement with OCR, Anthem faced multiple lawsuits in the wake of the data breach. The consolidated class action lawsuit was settled by Anthem in January 2018 for $115 million.
The class action settlement document indicated Anthem had already paid $2.5 to consultants in the wake of the breach, $31 million was spent mailing notification letters, $115 million went on improvements to security, and $112 million was paid to provide identity theft protection and credit monitoring services to affected plan members.
With the $115 million class action settlement and the $16 million OCR settlement, that brings the total cost of the Anthem data breach to $391.5 million.
At $391.5 million, that makes this the most expensive healthcare phishing attack by some distance and the cost clearly highlights just how important it is to adopt a defense-in-depth strategy to protect against phishing attacks.
Une attaque de spear phishing donne lieu à une amende de 16 millions de dollars dans l’affaire Anthem
by titanadmin | Sep 27, 2018 | Industry News, Internet Security, Network Security, Phishing & Email Spam |
Cybercriminals have turned to cryptocurrency mining malware as an easy, low-risk way of making money although ransomware is still the main malware threat according to Europol.
While it was common for large-scale spam email campaigns to be sent to random recipients to spread ransomware, tactics used to infect devices with the file-encrypting malware are changing.
There has been a decline in the use of ‘spray and pray’ spam campaigns involving millions of messages toward targeted attacks on businesses. Organized cybercriminal gangs are researching victims and are conducting highly targeted attacks that first involve compromising a network before manually deploying ransomware.
The cybercriminal group behind SamSam ransomware has been particularly prolific. Companies that have failed to address software vulnerabilities are attacked and access is gained to their networks. The SamSam group also conducts brute force attacks on RDP to gain access to business networks. Once access is gained, ransomware is manually installed on as many computers as possible, before the encryption routine is started across all infected devices. With a large number of devices encrypted, the ransom demand can be much higher – Typically around $50,000 per company. The group has collected at least $6 million in ransom payments to date.
Europol warns that ransomware attacks will continue to be a major threat over the following years, although a new threat is emerging – cryptojacking malware. This form of malware is used to hijack computer processors to mine cryptocurrency. Europol warns that if the rise in the use of cryptojacking malware continues it may overtake ransomware and become the biggest malware threat.
Not only does cryptojacking offer considerable rewards, in many cases use of the malware is not classed as illegal, such as when it is installed on websites. This not only means that cybercriminals can generate considerable profits, but the risk involved in these types of attacks is far lower than using ransomware.
Cybercriminals are still extensively using social engineering techniques to fool consumers and employees into disclosing sensitive personal information and login credentials. Social engineering is also extensively used to trick employees into making fraudulent bank transfers. Phishing is the most common form of social engineering, although vishing – voice phishing – and smishing – SMS phishing are also used. Europol notes that social engineering is still the engine of many cybercrimes.
While exploit kits have been extensively used to silently download malware, Europol notes that the use of exploit kits continues to decline. The main attack vectors are spam email and RDP brute-forcing.
As-a-service cyberattacks continue to be a major problem. DDoS-as-a-service and ransomware-as-a-service allow low-level and relatively unskilled individuals to conduct cyberattacks. Europol recommends law enforcement should concentrate on locating and shutting down these criminal operations to make it much harder for low-level criminals to conduct cyberattacks that would otherwise be beyond their skill level.
With spam email still a major attack vector, it is essential for businesses to implement cybersecurity solutions to prevent malicious emails from being delivered to inboxes and ensure cybersecurity best practices are adopted to make them less susceptible to attack. With phishing the main form of social engineering, anti-phishing training for employees is vital.
RDP attacks are now commonplace, so steps must be taken by businesses to block this attack vector, such as disabling RDP if it is not required, using extremely strong passwords for RDP, limiting users who can login, configuring account lockouts after a set number of failed login attempts, and using RDP gateways.
by titanadmin | Sep 19, 2018 | Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News, Website Filtering |
With the largest economy, the United States is naturally a major target for cybercriminals. Various studies have been conducted on the cost of cybercrime in the United States, but little data is available on cybercrime losses in Germany – Europe’s largest economy.
The International Monetary Fund produces a list of countries with the largest economies. In 2017, Germany was ranked fourth behind the United States, China, and Japan. Its GDP of $3,68 trillion represents 4.61% of global GDP.
A recent study conducted by Germany’s federal association for Information Technology – BitKom – has placed a figure on the toll that cybercrime is taking on the German economy.
The study was conducted on security chiefs and managers at Germany’s top 503 companies in the manufacturing sector. Based on the findings of that survey, BitKom estimated cybercrime losses in Germany to be €43 billion ($50.2 billion). That represents 1.36% of the country’s GDP.
Extrapolate those cybercrime losses in Germany and it places the global cost of cybercrime at $1 trillion, substantially higher than the $600 billion figure estimate from cybersecurity firm McAfee and the Center for Strategic and International Studies (CSIS) in February 2018. That study placed the global percentage of GDP lost to cybercrime at between 0.59% and 0.80%, with GDP losses to cybercrime across Europe estimated to be between 0.79 to 0.89% of GDP.
Small to Medium Sized Businesses Most at Risk
While cyberattacks on large enterprises have potential to be highly profitable for cybercriminals, those firms tend to have the resources available to invest heavily in cybersecurity. Attacks on large enterprises are therefore much more difficult and time consuming. It is far easier to target smaller companies with less robust cybersecurity defenses.
Small to medium sized businesses (SMBs) often lack the resources to invest heavily in cybersecurity, and consequently are far easier to attack. The BitKom study confirmed that these companies, which form the backbone of the economy in Germany, are particularly vulnerable to cyberattacks and have been extensively targeted by cybercriminals.
It is not only organized cybercriminal groups that are conducting these attacks. Security officials in Germany have long been concerned about attacks by well-resourced foreign spy agencies. Those agencies are using cyberattacks to gain access to the advanced manufacturing techniques developed by German firms that give them a competitive advantage. Germany is one of the world’s leading manufacturing nations, so it stands to reason that the German firms are an attractive target.
Cybercriminals are extorting money from German firms and selling stolen data on the black market and nation-state sponsored hackers are stealing proprietary data and technology to advance manufacturing in their own countries. According to the survey, one third of companies have had mobile phones stolen and sensitive digital data has been lost by a quarter of German firms. 11% of German firms report that their communications systems have been tapped.
Attacks are also being conducted to sabotage German firms. According to the study, almost one in five German firms (19%) have had their IT and production systems sabotaged through cyberattacks.
Businesses Must Improve Their Defenses Against Cyberattacks
“With its worldwide market leaders, German industry is particularly interesting for criminals,” said Achim Berg, head of BitKom. Companies, SMBs in particular, therefore need to take cybersecurity much more seriously and invest commensurately in cybersecurity solutions to prevent cybercriminals from gaining access to their systems and data.
According to Thomas Haldenweg, deputy president of the BfV domestic intelligence agency, “Illegal knowledge and technology transfer … is a mass phenomenon.”
Preventing cyberattacks is not straightforward. There is no single solution that can protect against all attacks. Only defense-in-depth will ensure that cybercriminals and nation-state sponsored hacking groups are prevented from gaining access to sensitive information.
Companies need to conduct regular, comprehensive organization-wide risk analyses to identify all threats to the confidentiality, integrity, and availability of their data and systems. All identified risks must then be addressed through a robust risk management process and layered defenses implemented to thwart attackers.
One of the main vectors for attack is email. Figures from Cofense suggest that 91% of all cyberattacks start with a malicious email. It stands to reason that improving email security should be a key priority for German firms. This is an area where TitanHQ can help.
TitanHQ is a provider of world-class cybersecurity solutions for SMBs and enterprises that block the most commonly used attack vectors. To find out more about how TitanHQ’s cybersecurity solutions can help to improve the security posture of your company and block email and web-based attacks, contact the TitanHQ sales team today.
by titanadmin | Sep 17, 2018 | Industry News, Internet Security, Network Security, Spam Software, Website Filtering |
Managed service providers (MSPs) are discovering the huge potential for profit from offering security-as-a-service to their clients. Managed security services are now the biggest growth area for the majority of leading MSPs, with security-as-a-service well ahead of cloud migration, cloud management, and managed Office 365 services according to a recent survey conducted by Channel Futures.
Channel Futures conducted the survey as part of its annual MSP 501 ranking initiative, which ranks MSPs based on their ability to act on current trends and ensure they remain competitive in the fast-evolving IT channel market. The survey evaluated MSP revenue growth, hiring trends, workforce dynamics, service deliverables, business models, and business strategies.
The survey revealed that by far the biggest growth area is managed security services. Security-as-a-service was rated the biggest growth area by 73% of MSPs. 55% of MSPs said professional services were a major growth area, 52% said Office 365, and 51% said consulting services.
It is no surprise that security-as-a-service is proving so popular as the volume of attacks on enterprises and SMBs has soared. Cybercriminals are attacking enterprises and SMBs trying to gain access to sensitive data to sell on the black market. Attacks are conducted to sabotage competitors, nation-state-sponsored hackers are attempting to disrupt critical infrastructure, and data is being encrypted to extort money. There is also a thriving market for proprietary data and corporate secrets.
The cost of mitigating attacks when they succeed is considerable. For enterprises, the attacks can make a significant dent in profits, but cyberattacks on SMBs can be catastrophic. A study conducted by the National Cyber Security Alliance suggests as many as 60% of SMBs go out of business in the 6 months following a hacking incident.
Enterprises and SMBs alike have had to respond to the increased threat by investing heavily in security, but simply throwing money at security will not necessarily mean all security breaches are prevented. Companies need to employee skilled IT security professionals to implement, monitor and maintain those cybersecurity solutions, conduct vulnerability scans, and identify and address security gaps. Unfortunately, there is a major shortage of skilled staff and attracting the right talent can be next to impossible. Faced with major challenges, many firms have turned to MSPs to and have signed up for security-as-service offerings.
Forward-thinking MSPs have seized the opportunity and are now providing a comprehensive range of managed security services to meet the needs of their clients. They are offering a wide range of tools and services from phishing protection to breach mitigation services; however, for many MSPs, developing such a package is not straightforward.
Security-as-a-service is in high demand, but MSPs must be able to package the right services to meet customers’ needs and have a platform that can handle the business end. They too must attract the staff who can implement, monitor, and manage those services for their clients.
When devising a security-as-a-service offering, one option is to use a common security architecture for all clients and provide them with a range of solutions from the same provider. Many companies have implemented a slew of different security tools from multiple providers, only to discover they are still experiencing breaches. It is a relatively easy sell to get them to move over to a system where all the component parts are seamlessly integrated and to benefit from an MSP’s expertise in managing those solutions. There is a risk of course that clients will just choose to go direct rather than obtain those services from an MSP. This single platform strategy has been adopted by Liberty Technology – ranked 242 in the MSP 501 list – and is working well, especially for clients that have fewer than 1,000 employees.
At the other end of the spectrum is Valiant Technologies, ranked 206 in the MSP 501 list. Valiant has chosen a wide range of products from multiple cybersecurity solution providers and has built a unique package of products for its security service.
The products were chosen for the level of protection they offered and how well they work together. This approach has been a success for the firm. “Providing a bundle of offerings from different vendors that work well together is the most effective way for an MSP to retain its role as a trusted adviser,” said the firm’s CEO Tom Clancy. The security service has been added to other business services provided by the MSP and has proved to be an easy sell to clients.
ComTec Solutions, which ranked in position 248 in the MSP 501 list, is still deciding on the best way forward. The provision of security-as-a-service is a no brainer, but the company is currently assessing whether it is worthwhile building a security operations center (SOC) and becoming a managed security service provider (MSSP) or outsourcing the SOC service.
There are several different approaches to take when developing a managed security service offering. What is vital is that such a service is provided. The MSP 501 survey has shown that the most successful MSPs have responded to demand and are now helping their clients secure their networks through their security-as-a-service offerings. Those MSPs are clearly reaping the rewards.
If you are an MSP that is considering developing a security-as-a-service offering, be sure to speak to TitanHQ about its world-class cloud-based security solutions for MSPs – WebTitan and SpamTitan – and find out how they can be integrated into your security stack.
by titanadmin | Aug 15, 2018 | Email Scams, Industry News, Network Security |
Two factor authentication flaws have been identified that allow accounts to be accessed even when protected by a password and second authentication factor.
Two-factor authentication is an important safeguard to secure accounts. In the event of login credentials being guessed or otherwise obtained by a third party, an additional method of authentication is required to gain access to the account. Without that second factor, access to the account is blocked. But not always. Multiple two-factor authentication flaws have been identified.
Two Factor Authentication Flaws Exploited in Reddit, LinkedIn and Yahoo Cyberattacks
Two-factor authentication is not infallible. Recently, Reddit disclosed that it had suffered a data breach even though two factor authentication had been implemented. Rather than use a token, Reddit used SMS messages to a mobile phone owned by the account holder as the second authentication factor. As Reddit discovered, SMS messages can be intercepted. The attacker was able to intercept a 2FA SMS message and gain access to an employee’s account, through which it was possible to access to an old database of user credentials.
Two-factor authentication was also in place at Yahoo in 2013, yet the company still experienced a massive data breach that resulted in all three billion of its users having their information obtained by hackers. Go back a year and there was the massive 167 million record data breach at LinkedIn, which had also implemented two-factor authentication.
A phone call or text message to a phone owned by the account holder does not necessarily prevent access to the account from being gained by a third party. In August last year, a Bitcoin investor had $150,000 of cryptocurrency stolen from his wallet after it was accessed by a third party. In that case, the investor’s second factor phone number had been re-routed to a device owned by the attacker after the phone company was duped.
Any second factor that uses the phone system of SMS messages provides an additional layer of protection, but it is not enough to protect against a determined skilled hacker.
Two Factor Authentication Flaws Discovered in Microsoft’s Active Directory Federation Services
A major two-factor authentication vulnerability was recently discovered by a security researcher at Okta. Okta, like many companies, uses Microsoft’s Active Directory Federation Services (ADFS) to provide multi-factor authentication.
Okta security researcher Andrew Lee discovered the system have a serious vulnerability that was not only straightforward to exploit, doing so would render an organization’s multi-factor authentication controls virtually useless.
Lee discovered that someone with a username, password, and a valid 2-factor token for one account could use the same token to gain access to any other account in the organization in AD with only a username and password. Any employee who is given an account and specified their own second factor could use it to access other accounts. Essentially the token was like a hotel room key card that opens all rooms in the hotel.
Obtaining another employee’s login credentials would only require a phishing campaign to be conducted. If an individual responded and disclosed their credentials, their account could be accessed without the need for a second factor.
The vulnerability in question, which was patched by Microsoft on August 14 in its August Patch Tuesday updates, was present in how ADFA communicates. When a user tries to login, an encrypted context log is sent by the server which contains the second factor token but not the username. This flaw could be exploited to fool the system into thinking the correct token had been supplied, as no check was made to determine whether the correct token had been supplied for a specific user’s account. As long as one valid username, password and 2FA token combo was owned, the 2FA system could be bypassed.
Two factor Authentication is Not a Silver Bullet
These two factor authentication flaws show that while 2-factor authentication is an important control to implement, businesses should not rely on the system to prevent unauthorized accessing of accounts. The two-factor authentication flaws discussed here are unlikely to be the last to be uncovered.
2-factor authentication should be just one element of an organization’s defenses against phishing and hacking, along with spam filters web filters, firewalls, intrusion detection systems, antivirus solutions, network segmentation, and employee security awareness training. 2FA should not be viewed as a silver bullet to prevent unauthorized account access.
by titanadmin | Aug 3, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam Advice, Spam News, Spam Software |
The past year has seen a steady increase in the number of reported email account compromises, with the healthcare industry one of the main targets for hackers.
Some of those breaches have seen the protected health information of thousands of patients compromised, with the largest phishing attack in 2018 – The phishing attack on Boys Town National Research Hospital – seeing more than 105,000 patients’ healthcare information exposed. Due to reporting requirements under HIPAA, healthcare phishing attacks are highly visible, although email account compromises are occurring across all industry sectors and the problem is getting worse.
284% Increase in Email Account Compromises in a Year
The increase in successful phishing attacks has been tracked by Beazley, a provider of specialist insurance services. The company’s research shows the number of reported phishing attacks increased every quarter since Q1, 2017 when there were 45 reported breaches that involved email accounts being compromised. In Q2, 2018, there were 184 email account compromises reported. Between Q1, 2017 and Q1, 2018, the number of reported data breaches involving compromised email accounts increased by 284%.
Why are email account compromises increasing? What do hackers gain from accessing email accounts rather than say, gaining access to networks which store vast amounts of data?
It can take a significant amount of time and effort to identify a vulnerability such a missed patch, an exposed S3 bucket, or an unsecured medical device, and exploit it.
By comparison, gaining access to an email account is relatively easy. Once access is gained, accessing further email accounts becomes easier still. If a hacker can gain access to an email account with the right level of administrative privileges, it may be possible for the entire mail system of an organization to be accessed.
If a hacker can gain access to a single email account, the messages in the account can be studied to gain valuable information about a company, its employees, and vendors. The hackers can identify further targets within an organization for spear phishing campaigns – termed Business Email Compromise (BEC) attacks – and attacks on contractors and suppliers.
Once One Account is Breached, Others Will Follow
If an executive’s email account is compromised, it can be used to send requests for wire transfers to the accounts department, HR can be emailed requesting W2-Forms that contain all the information necessary for filing fake tax returns and for identity theft. Requests can be sent via email to redirect employees’ paychecks and phishing emails can be sent to other employees directing them to websites where they have to divulge their email credentials.
Figures from the FBI show just how lucrative these Business Email Compromise (BEC) phishing attacks can be. Since October 2013, more than $12.5 billion has been lost to BEC attacks, up from $5.3 billion in December 2016.
Once access to the email system is gained, it is much easier to craft highly convincing spear phishing emails. Past email conversations can be studied, and an individual’s style of writing emails can be copied to avoid raising any red flags.
Email Account Compromises Are Costly to Resolve
Beazley also notes that email account compromises are some of the costliest breaches to resolve, requiring many hours of painstaking work to manually checking each email in a compromised account for PII and PHI. One example provided involved a programmatic search of compromised email accounts to identify PHI, yet that search uncovered 350,000 documents that required a manual check. The cost of checking those documents alone was $800,000.
Beazley also notes that when investigating breaches, the breached entity often discovers that only half of the compromised email accounts have been identified. The data breaches are usually much more extensive than was initially thought.
Unfortunately, once access to a single email account is gained, it is much harder to prevent further email compromises as technological controls are not so effective at identifying emails sent from within a company. However, it is relatively easy to block the initial phishing attempt.
How to Prevent Email Account Compromises
Many companies fail to implement basic controls to block phishing attacks. Even when a phishing-related breach is experienced, companies often remain susceptible to further breaches. The Ponemon Institute/IBM Security Cost of a Data Breach study showed there is a 27.9% probability of a company experiencing a further breach in the 24 months following a data breach.
To prevent phishing attacks, companies need to:
- Deploy an advanced spam filtering solution that blocks the vast majority of malicious messages
- Provide ongoing security awareness training to all staff and teach employees how to identify phishing emails
- Conduct regular phishing simulation exercises to reinforce training and condition employees to be more security aware
- Implement two-factor authentication to prevent attempts to access email accounts remotely
- Implement a web filter as an additional control to block the accessing of phishing websites
- Use strong, unique passwords or passphrases to make brute force and dictionary attacks harder
- Limit or prevent third party applications from connecting to Office 365 accounts, which makes it harder for PowerShell to be used to access email accounts for reconnaissance.
by titanadmin | Jul 31, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News, Spam Software |
In recent weeks, several large healthcare data breaches have been reported that have seen cybercriminals gain access to employees’ email accounts and sensitive data, although the recently disclosed UnityPoint Health phishing attack stands out due to the huge number of individuals that have been impacted and the extent of sensitive data exposed.
UnityPoint Health is one of the largest healthcare systems serving Iowa residents. The Des Moines-based healthcare provider recently discovered that its employees have been targeted in a phishing campaign that has seen several email accounts compromised. Those email accounts contained the sensitive information of approximately 1.4 million patients.
That not only makes this the largest phishing incident to have been suffered by a U.S. healthcare provider in 2018, it is also the largest healthcare data breach of 2018 and one of the most serious phishing attacks and data breaches ever reported.
The UnityPoint Health phishing attack has seen highly sensitive data compromised, including names, addresses, health insurance information, medical record numbers, diagnoses, treatment information, lab test results, medications, providers, dates of service, Social Security numbers, driver’s license numbers and, for a limited number of patients, their payment card information.
The phishing emails were sent to employees between March 14 and April 3, 2018, although the breach was not detected until May 31. As is common in phishing attacks on businesses, access to email accounts was gained through the impersonation of a senior executive.
A series of spoofed emails were sent to employees that appeared to have come from a trusted executive’s email account. Employees who opened the email were instructed to click a link that required them to enter their email login information. That information was captured by the attackers who were then able to gain access to the employees’ email accounts.
The UnityPoint Health phishing attack potentially gave the hackers access to all the information stored in the compromised email accounts – Information that could be used for identity theft and fraud. It is unclear whether mailboxes were downloaded, although UnityPoint Health said its forensic investigation suggests that the primary goal was to divert payroll payments and to use account access to fool accounts department staff into making fraudulent wire transfers. It is unclear if any of those attempts succeeded.
This is also not the only UnityPoint Health phishing attack to be reported this year. In March, UnityPoint Health announced that 16,400 patients had been affected by a separate phishing attack that saw multiple email accounts compromised.
The latest incident has prompted the healthcare provider to implement new technology to detect phishing and BEC attacks, multi-factor authentication has been implemented, and additional security awareness training has been provided to employees. Credit monitoring and identify theft monitoring services have been offered to patients whose driver’s license or Social Security number has been exposed, and all patients have been notified by mail.
As the Ponemon Institute’s 2018 Cost of a Data Breach Study showed, the cost of these million-record+ data breaches is considerable. The average cost of such a breach was estimated to be around $40 million.
by titanadmin | Jul 26, 2018 | Email Scams, Industry News, Network Security, Phishing & Email Spam, Spam Software, Website Filtering |
One of the world’s biggest shipping firms – Cosco – has experienced a ransomware attack that has seen its local email system and network telephone in the Americas taken out of action as the result of widespread file encryption.
The Cosco ransomware attack is believed to have been contained in the Americas region. As a precaution and to prevent further spread to other systems, connections to all other regions have been disabled pending a full investigation. A warning has also been issued to all other regions warning of the threat of attack by email, with the firm telling its staff not to open any suspicious email communications. IT staff in other regions have also been advised to conduct scans of their network with antivirus software as a precaution.
The attack started on Tuesday, July 24, and its IT infrastructure remains down; however, the firm has confirmed that that attack has not affected any of its vessels which continue to operate as normal. Its main business systems are still operational, although the operators of terminals at some U.S ports are experiencing delays processing documentation and delivery orders.
It would appear that the Cosco ransomware attack is nowhere near the scale of the attack on the world’s biggest shipping firm A.P. Møller-Maersk, which like many other firms, fell victim to the NotPetya attacks last year. In that case, while the malware appeared to be ransomware, it was actually a wiper with no chance of file recovery.
The attack, which affected more than 45,000 endpoints and 4,000 servers, is estimated to have cost the shipping company between $250 million and $350 million to resolve. All servers and endpoints needed to be rebuilt, and the firm was crippled for 10 days. In that case, the attack was possible due to an unpatched vulnerability.
Another major ransomware attack was reported last week in the United States. LabCorp, one of the leading networks of clinical testing laboratories in the United States, experienced a ransomware attack involving a suspected variant of SamSam ransomware. While the variant of ransomware has not been confirmed, LabCorp did confirm the ransomware was installed as a result of a brute force attack on Remote Desktop Protocol (RDP).
Labcorp was both quick to detect the attack and contain it, responding within 50 minutes, although 7,000 systems and 1,900 servers are understood to have been affected. It has taken several days for the systems to be brought back online, during which time customers have been experiencing delays obtaining their lab test results.
Several cybersecurity firms have reported that ransomware attacks are in decline, with cryptocurrency mining offering better rewards, although the threat from ransomware is still ever present and attacks are occurring through a variety of attack vectors – exploitation of vulnerabilities, brute force attacks, exploit kit downloads, and, commonly, through spam and phishing emails.
To protect against ransomware attacks, companies must ensure security best practices are followed. Patches must be applied promptly on all networks, endpoints, applications, and databases, spam filtering software should be used to prevent malicious messages from reaching inboxes, web filters used to prevent downloads of ransomware from malicious websites, and all staff should receive ongoing cybersecurity awareness training.
Additionally, systems should be implemented to detect anomalies such as excessing file renaming, and networks should be segmented to prevent lateral movement in the event that ransomware is deployed.
Naturally, it is also essential that data are backed up regularly to ensure recovery is possible without having to resort to paying the ransom demand. As the NotPetya attacks showed, paying a ransom to recover files may not be an option.
by titanadmin | Jul 19, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam |
In 2017, data breach mitigation costs fell year-on year; however, that appears to be a blip. The 2018 Cost of a Data Breach Study conducted by the Ponemon Institute (on behalf of IBM Security) has revealed data breach mitigation costs have risen once again.
The Ponemon Institute conducts the Cost of a Data Breach Study every year. For the 2018 study, the Ponemon Institute conducted interviews with 2,200 IT, data security, and compliance professionals from 477 companies in 15 countries, including the United States, United Kingdom, Germany, France, Canada, Brazil, Japan and Australia. The companies represented in the study came from a wide range of industry sectors. Each of those companies had experienced a data breach in the past 12 months.
Naturally, the larger the breach, the higher the cost of mitigation is likely to be. Breaches involving millions of records would naturally cost more to resolve than breaches of 50,000 records. Catastrophic data breaches – those involving millions of records – are not normally included in the study. This year was the first time that mega data breaches – those involving more than 1,000,000 records – were included, although they were treated separately.
The analysis of the main part of the study involved breaches ranging from 2,500 records to a little over 100,000 records. The average breach size was 24,615 records globally, 31,465 records in the United States, 22,800 records in the UK, and 19,200 records in Japan.
The costs associated with those data breaches was analyzed using the activity-based costing (ABC) methodology. The ABC methodology identified four process-related activities and assigned costs based on actual use. Those activities were Detection and Escalation, Post Data Breach Response, Breach Notifications, and Lost Business Cost. The analysis identified the average total cost of a data breach taking all four activity areas into account.
The study also revealed measures taken prior to the breach, during, and after, that can limit losses or increase data breach mitigation costs.
Average Data Breach Mitigation Costs Have Reached $3.86 Million
A data breach now costs an average of $3.86 million to revolve. Last year, the average cost of a data breach was $3.62 million. Data breach costs have therefore increased by 6.4% in the space of a year.
On average, per capita data breach mitigation costs rose by 4.8%, with a data breach costing, on average, $148 per record. Last year, the global average was $141 per record.
In addition to the rising cost, the severity of the breaches also increased, with the data breaches in this year’s sample impacting 2.2% more individuals on average.
Data breaches cost more to resolve in the United States than any other country. The average data breach mitigation costs in the United States is $7.91 million per breach. The lowest costs were in India, where the average breach cost was $1.77 million. The highest per capita costs were also in the United States at £233 per record.
Hackers and malicious insiders caused the most breaches and they were also the costliest to resolve at $157 per record. System glitches cost an average of £131 per record and breaches caused by human error cost the least at $128 per record.
Data breach costs varied considerably by industry sector, with healthcare data breach mitigation costs the highest by some distance at an average of $408 per record, followed by financial services breaches at $206 per record, services at $181 per record, and pharmaceutical industry breaches at $174 per record. Breaches in the education sector cost an average of $166 per record, retail industry breaches were $116 per record, and the lowest data breach mitigation costs were in the public sector at $75 per record.
The study of mega data breaches revealed a breach of 1 million records costs an estimated $39.49 million to resolve, while a breach of 50 million records costs an estimated $350 million. Since there were only 11 breaches of more than 1 million records in the sample it was not possible to accurately calculate the average cost of these breaches.
What Factors Affect Data Breach Mitigation Costs the Most?
For the study, 22 different factors were assessed to determine how they affected data breach mitigation costs. The most important cost saving measures that can be taken to reduce the cost of a data breach are having an incident response team ($14 less per record), widespread use of encryption ($13.1 less per record), BCM involvement ($9.3 less per record), employee training ($9.3 less per record), participation in threat sharing ($8.7 less per record) and use of an artificial intelligence platform ($8.2 less per record).
The main factors that increased data breach mitigation costs were third party involvement ($13.4 more per record), extensive cloud migration at the time of the breach ($11.9 more per record), compliance failures ($11.9 more per record), extensive use of mobile platforms ($10.0 more per record), lost or stolen devices ($6.5 more per record), and extensive use of IoT devices ($5.4 more per record).
With the cost of data breaches rising, more cyberattacks being conducted, and the likelihood of a breach being experienced now higher, it is essential not only for companies to implement layered security defenses, but also to make sure they are prepared for the worst.
Companies need to assume a breach will be experienced and policies and procedures need to be developed to deal with the breach when it happens. An incident response team should be prepared to spring into action to ensure everyone known what needs to be done when disaster strikes. The sooner a breach is identified and mitigated, the lower the breach mitigation costs will be.
by titanadmin | Jun 26, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News, Spam Software |
The FBI has published its 2017 Internet Crime Report, which details the main types of online crime reported to its Internet Crime Complaint Center (IC3).
In 2017, businesses and consumers reported 301,580 incidents to IC3 and more than $1.4 billion was lost to cybercriminals. Of course, these are only reported losses. Many Internet crimes go unreported, so the true losses are likely to be substantially higher.
2017 saw more complaints of Internet crime than any other year since 2013 when the reports first started to be published.
Identity theft and corporate data breaches often make the headlines, although by far the biggest area of criminal activity are business email compromise (BEC) scams – or email account compromise (EAC) when the scams target individuals.
Business Email Compromise Scams – The Main Cause of Losses in 2017
More than three times as much money was lost to BEC and EAC scams than the next highest cause of losses: confidence fraud/romance scams. In 2017, the reported losses from BEC/EAC scams was $676,151,185.
Business email compromise and email account compromise scams involve the use of a compromised email account to convince individuals to make transfers of funds to accounts controlled by criminals or to send sensitive data via email.
BEC scams usually start with compromising the email account of the CEO, CFO or another board member – which is why this type of scam is also known as CEO fraud. Access to the executive’s email account is gained via brute force guessing of passwords or, most commonly, social engineering techniques and phishing scams.
Once access to the email account is gained, an email conversation is initiated with another member of the workforce, typically an individual responsible for making wire transfers. That individual is instructed to make a transfer to a new bank account – that of the attacker. Alternatively, the data of employees is requested – W2 Forms – or other sensitive company information. These scams often involve large transfers of funds. In 2017 there were 15,690 such scams reported to IC3, making the average loss $43,094.
Phishing Extensively Used in Internet Crime
Phishing, vishing, smishing and pharming were grouped together. They ‘only’ resulted in losses of $29,703,421, although the losses from these crimes are difficult to calculate accurately. The losses associated with phishing are grouped in many other categories. BEC scams often start with a phishing attack and research from Cofense suggests 91% of corporate data breaches start with a phishing email.
The 2017 Internet Crime Report reveals the extent to which phishing is used in cyberattacks. There were 25,344 phishing incidents reported to IC3 in 2017 – the third highest category of Internet crime behind non-payment/non-delivery and personal data breaches. Many personal data breaches start with a phishing email.
Ransomware Attack Mitigation Proves Expensive
In addition to the threat of BEC attacks, the FBI’s 2017 Internet Crime Report warns of the threat from ransomware. Ransomware only resulted in reported losses of $2.3 million and attracted 1,783 complaints, although it is worthy of a mention due to the considerable disruption that attacks can cause. The reported losses – in terms of the ransoms paid – may be low, but actual losses are substantially higher. The ransomware attack on the City of Atlanta in April 2018 saw a ransom demand of $52,000 issued, although the actual cost of mitigating the attack was reported to be at least $2.7 million in April. However, in June 2018, city Information Management head Daphney Rackley indicated a further $9.5 million may be required over the coming year to cover the cost of mitigating the attack.
Tech Support Fraud Losses Increased by 90%
Another hot topic detailed in the 2017 Internet Crime Report is tech support fraud – This is a widespread scam where individuals are fooled into thinking they have a computer problem such as a virus or malware installed, when they do not. Calls are made warning of detected malware, and users are directed to malicious websites via phishing emails where pop-up warnings are displayed, or screen lockers are used.
These scams usually require the victim to pay the scammer to remove a fictitious infection and provide them with remote access to a computer. In addition to the scammers charge for removing the infection, sensitive data such as usernames, passwords, Social Security numbers, and bank account information are often stolen. 2017 saw a 90% increase in losses from tech support scams.
Protecting Against Internet Crime
One of the most important defenses for businesses to implement to protect against the leading cause of financial losses is an advanced spam filtering solution. Business email compromise scams often start with a phishing email and effective spam filtering will reduce the potential for email accounts to be compromised. Ransomware and malware are also primarily distributed via email. An advanced spam filter such as SpamTitan will block 100% of all known malware and prevent malicious messages from being delivered to inboxes.
Security awareness training is also essential. Malicious messages will make it past spam filtering solutions on occasion, so it is important for all end users to be prepared for malicious messages and taught security best practices. Training should be provided to every individual in the company with a corporate email account or access to an Internet facing computer, including board members.
A web filtering solution is also an important consideration. A web filter is an additional anti-malware control that can be used to prevent employees from visiting malicious websites – either via links in emails, redirects, or through general web browsing. A web filter, such as WebTitan, will block ransomware and malware downloads and prevent end users from accessing the types of phishing websites used to initiate BEC attacks.
These three cybersecurity measures should be part of all organizations’ cybersecurity defenses. They will help to prevent businesses from being included in next year’s FBI Internet Crime Report.
by titanadmin | May 28, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam Software |
The UK Government’s Department for Digital, Culture, Media, & Sport has published its Cybersecurity Breaches Survey for 2018. The survey, conducted by Ipsos MORI, was a quantitative and qualitative survey conducted in the winter of 2017 on 1,519 UK businesses and 569 UK registered charities.
The purpose of the cybersecurity breaches survey was to identify the nature and significance of cyberthreats, determine how prevalent cyberattacks are, and what is being done to prevent such attacks.
The cybersecurity breaches survey revealed UK businesses and charities are being targeted by cybercriminals intent on gaining access to sensitive information, email accounts, corporate networks, and bank accounts and attacks are on the rise.
43% of businesses and 19% of charities experienced a cybersecurity breach or cyberattack in the past 12 months with large businesses and charities more likely to be attacked. 72% of large businesses – those with more than 250 employees – and 73% of large charities – with incomes over £5 million – experienced a cyberattack in the past year.
While not all security breaches result in material losses such as theft of data or personal information, when there is a material outcome the costs can be significant. The average costs of breaches with a material outcome is £3,100 for businesses and £1,030 for charities, although the larger the business, the greater the cost. Medium sized businesses have average costs of £16,100 and large businesses have an average breach cost of £22,300.
The high probability of a breach occurring and the high cost of remediating breaches has seen cybersecurity become a priority for senior managers. The percentage of businesses (74%) and charities (53%) that say cybersecurity is a high priority has risen year on year and the percentage of businesses (30%) and charities (24%) that say cybersecurity is a low priority has fallen once again. Cybersecurity is also now a high priority for many small businesses (42%) having risen from 33% last year when the survey was conducted. Cybersecurity may be a high priority, but just 3 out of 10 businesses and under a quarter of charities have board members with a responsibility for cybersecurity.
The most common type of breaches and cyberattacks involve fraudulent emails directing employees to malicious websites. 75% of UK businesses and 74% of UK charities that experienced a breach in the past year experienced these types of attacks. Email impersonation attacks were the second most common breach type with 28% of UK businesses and 27% of UK charities saying they had experienced these types of incidents in the past 12 months.
Not only are these types of attacks common, they also cause the most disruption. 48% of UK businesses and charities said fraudulent emails and being directed to malicious websites caused the most disruption out of all cybersecurity breaches experienced, well ahead of malware infections which were rated as the most disruptive cyberattacks by 13% of UK businesses and 12% of UK charities.
The cybersecurity breaches survey clearly highlights the importance of implementing robust defenses to prevent malicious emails from being delivered to employees’ inboxes and to ensure staff are well trained and taught how to identify malicious emails.
TitanHQ offers two cybersecurity solutions that can help UK businesses block the most common and most disruptive types of cyberattack. SpamTitan is a powerful spam filtering solution that blocks more than 99.97% of spam emails and 100% of known malware from being delivered to end users’ inboxes.
WebTitan is a cloud-based web filtering solution that prevents employees from visiting malicious websites, such as those used in phishing emails to steal credentials and spread malware. Implementing these solutions is far cheaper than having to cover the cost of remediating cyberattacks.
There is also clearly a problem with training in the UK. Only 20% of UK businesses and 15% of UK charities have had staff attend internal or external cybersecurity training in the past year, even though security awareness training has clearly been shown to be effective at reducing susceptibility to email-based attacks.
by titanadmin | May 25, 2018 | Industry News, Internet Security, Network Security |
Data breach costs have risen considerably in the past year, according to a recent study of corporate IT security risks by Kaspersky Lab. Compared to 2016, the cost of a data breach for enterprises increased by 24% in 2017, and by even more for SMBs, who saw data breach costs rise by 36% in 2017.
The average cost of data breach recovery for an average-sized enterprise is now $1.23 million per data breach, while the cost for SMBs is now $120,000 per incident.
For the study, Kaspersky Lab surveyed 6,614 business decision makers. Respondents were asked about the main threats they have to deal with, cybersecurity incidents they have experienced in the past year, how much they spent resolving those incidents, and how that money was spent.
When a data breach is experienced, the costs can quickly mount. Enterprises and SMBs must contain the attack, scan systems for malware and backdoors, and pay for improvements to security and infrastructure to prevent similar attacks from occurring in the future. Staff need to receive additional training, new staff often need to be brought in, and third-parties hired to assist with recovery and security assessments.
Data breach recovery can take time and considerable effort. Additional wages have to be paid to staff assisting in the recovery process, there can be losses due to system downtime, repairing damage to a brand prove costly, credit monitoring and identity theft recovery services may have to be provided to breach victims, insurance premiums rise, credit ratings drop, and there may also be regulatory fines to cover.
The largest component of data breach costs is making emergency improvements to security and infrastructure to prevent further attacks, which is around $193,000 per breach for enterprises, the second biggest cost for enterprises is repairing reputation damage, which causes major increases in insurance costs and can severely damage credit ratings. On average, this costs enterprises $180,000. Providing after-the-event security awareness training to the workforce was the third biggest cost for enterprises at $137,000.
It is a similar story for SMBs who typically pay around $15,000 for each of the above three cost categories. A lack of inhouse expertise means SMBs often have to call in cybersecurity experts to assist with making improvements to security and for forensic analyses to determine how access to data was gained.
Data breaches affecting third-party hosted infrastructure are the costliest for SMBs, followed by attacks on non-computing connected devices, third party cloud services, and targeted attacks. For enterprises, the costliest data breaches are targeted attacks followed by attacks on third-party infrastructure, attacks on non-computing connected devices, third party cloud services, and leaks from internal systems.
The high cost of recovering from a data breach means a successful cyberattack on an SMB could be catastrophic, forcing the company to permanently shut its doors. It is therefore no surprise that businesses are allocating more of their IT budgets to improving their security defenses. Enterprises are now spending an average of $8.9 million on cybersecurity each year, while SMBs spend an average of $246,000. Even though the cost of additional cybersecurity defenses is high, it is still far lower than the cost of recovering from data breaches.
While data breach prevention is a key driver for greater investment in cybersecurity, that is far from the only reason for devoting a higher percentage of IT budgets to security. The main drivers for increasing security spending are the increasing complexity of IT infrastructure (34%), improving the level of security expertise (34%), and management wanting to improve security defenses (29%).
by titanadmin | May 2, 2018 | Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam Software, Website Filtering |
Another school district has fallen victim to a ransomware attack, which has seen files encrypted and systems taken out of action for two weeks. The Leominster school district ransomware attack saw a ransom demand of approximately $10,000 in Bitcoin was issued for the keys to unlock the encrypted files, which includes the school’s entire student database.
School districts attacked with ransomware often face a difficult decision when ransomware is installed. Attempt to restore systems and recover lost data from backups or pay the ransom demand. The first option is time consuming, costly, and can see systems remain out of action for several days. The second option includes no guarantees that the attackers will make good on their promise and will supply valid keys to unlock the encryption. The keys may not be held, it may not be possible to unlock files, or a further ransom demand could be issued. There have been many examples of all three of those scenarios.
The decision not to pay the ransom demand may be the costlier option. The recent ransomware attack on the City of Atlanta saw a ransom demand issued in the region of $50,000. The cost of recovering from the attack was $2.6 million, although that figure does include the cost of improvements to its security systems to prevent further attacks.
School districts are often targeted by cybercriminals and ransomware offers a quick and easy way to make money. The attackers know all too well that data can most likely be recovered from backups and that the ransom does not need to be paid, but the cost of recovery is considerable. Ransom demands are set accordingly – high enough for the attackers to make a worthwhile amount, but low enough to tempt the victims into paying.
In the case of the Leominster ransomware attack, the second option was chosen and the ransom demand of was paid. That decision was taken after carefully weighing up both options. The risk that no keys would be supplied was accepted. In this case, they were supplied, and efforts are well underway to restore files and implement further protections to ensure similar incidents do not occur in the future.
Even though the ransom was paid, the school district was still without access to its database and some of its computer systems two weeks after the attack. Files were encrypted on April 14, but systems were not brought back online until May 1.
Unfortunately for the Leominster School District, ransom payments are not covered by its cyberinsurance policy, so the payment had to come from its general fund.
There is no simple way to defend against ransomware attacks, as no single cybersecurity solution will prove to be 100% effective at blocking the threat. Multiple attack vectors are used, and it is up to school districts to implement defenses to protect the entire attack surface. The solution is to defend in numbers – use multiple security solutions to create layered defenses.
Some of the most important defenses include:
- An advanced firewall to defend the network perimeter
- Antivirus and anti-malware solutions on all endpoints/servers
- Vulnerability scanning and good patch management policies. All software, systems, websites, applications, and operating systems should be kept up to date with patches applied promptly
- An advanced spam filtering solution to prevent malicious emails from being delivered to end users. The solution should block all executable files
- Disable RDP if it is not required
- Provide security awareness training for employees and teach staff and students the skills to enable them to identify malicious emails and stop risky behaviors
- A web filtering solution capable of blocking access to malicious websites
The cost of implementing these solutions is likely to be far lower than the cost of a ransom payment and certainly lower than the cost of mitigating a ransomware attack.
by titanadmin | Apr 27, 2018 | Industry News, Internet Security, Network Security |
The cost of the Equifax data breach has risen to more than $242 million, and that figure will continue to rise and could even double.
According to the Equifax financial report for the first quarter of 2018, the total spent on mitigation and preventative measures to avoid a further security breach is now $242.7 million.
The breach, which was made public in September 2017, affected 147.9 million customers, making it one of the largest data breaches ever discovered and certainly one of the most serious considering the types of data involved. Yahoo may have experienced much larger breaches, but the data exposed in those incidents was far less sensitive.
Fortunately for Equifax, it holds a sizable insurance policy against cybersecurity incidents. The policy will cover up to $125 million of the cost, minus a $7.5 million deductible. That insurance policy has already paid out $60 million, with $10 million in payments received in the first quarter of 2018.
The breakdown of cost of the Equifax data breach so far for Q1, 2018 is:
- $45.7 million on IT security
- $28.9 million on legal fees and investigation of the breach
- $4.1 million on product liability
- $10 million has been recovered from an insurance payout.
The net expenses from the breach in the first quarter of 2018 was $68.7 million. That is on top of the $114 million spent in the final quarter of 2017, which is broken down as $64.6 million on product costs and customer support, $99.4 million on professional fees, minus $50 million that was paid by its insurance carrier. The net spend so far for Q4, 2017 and Q1, 2018 is $140.5 million, although Equifax reports that the total costs related to the cybersecurity incident and incremental IT and data security costs has been $242.7 million.
Equifax has also reported that throughout 2018 and 2019 the firm will be investing heavily in IT and is committed to building an industry-leading data security system, although the firm has not disclosed how much it is expecting to spend, as the company does not have visibility into costs past 2018.
Equifax has predicted that there will be at least a further $275 million in expenses related to the cyberattack which must still be covered, although a further $57.5 million should be covered by its insurance policy.
While considerable costs have been incurred so far, the firm has done little to repair the reputational damage suffered as a result of the breach and has yet to hire many of the new staff it plans to bring in to help with the breach recovery, including a new CTO. The firm has said that it is taking a very aggressive approach in attracting the top talent in both IT and data security.
The high cost of the Equifax data breach to date, and the ongoing costs, is likely to make this the most expensive data breach of all time.
by titanadmin | Apr 25, 2018 | Industry News, Network Security |
A warning has been issued to the healthcare industry over an extensive campaign of targeted cyberattacks by the Orangeworm threat group. The Orangeworm threat group has been operating since 2015, but activity has been largely under the radar. It is only recently that the group’s activities have been identified and disclosed.
Attacks have been conducted on a range of industries, although the primary targets appear to be large healthcare organizations. 39% of confirmed attacks by the Orangeworm threat group have been on organizations in the healthcare industry, including large healthcare providers and pharmaceutical firms. IT service providers, manufacturers, and logistics firms have also been attacked, many of which have links to the healthcare industry.
Some of the IT service providers discovered to have been attacked have contracts with healthcare organizations, while logistics firms have been attacked that deliver medical equipment, as have manufacturers of medical devices. The aim appears to be to infect and investigate the infrastructure of the entire supply chain.
The Orangeworm threat group is using a custom backdoor, which is deployed once access to a network is gained. First the backdoor is deployed on one device, giving the Orangeworm threat group full control of that device. The backdoor is then aggressively spread laterally within a network via unprotected network shares to infect as many devices as possible with the Kwampirs backdoor. While some steps have been taken by the group to avoid detection, this lateral worm-like movement is noisy and easily detected. The threat group does not seem to be overly concerned about hiding its activity.
This attack method works best on legacy operating systems such as Windows XP. Windows XP is no longer supported, and even though the continued use of the operating system is risky and in breach of industry regulations, many healthcare organizations still have many devices operating on Windows XP, especially machines connected to imaging equipment such as MRI and X-Ray machines. It is these machines that have been discovered to have been infected with the Kwampirs backdoor.
Once access is gained, the group is spending a considerable amount of time exploring networks and collecting information. While the theft of patient health information is possible, this does not appear to be a financially motivated attack and systems are not sabotaged.
Symantec, which identified a signature which has allowed the identification of the backdoor and raised the alert about the Orangeworm threat group, believes this is a large-scale espionage campaign with the aim of learning as much as possible about the targets’ systems. What the ultimate goal of the threat group is, no one knows.
The method of spreading the backdoor does not have the hallmarks of nation-state sponsored attacks, which tend to use quieter methods of spreading malware to avoid detection. However, the attacks are anything but random. The companies that have been attacked appear to have been targeted and well researched before the attacks have taken place.
That suggests the Orangeworm threat group is a cybercriminal gang or small collective of hackers, but the group is clearly organized, committed to its goals, and is capable of developing quite sophisticated malware. However, even though the group is clearly capable, and has operated under the radar for three years, during that time no updates have been made to their backdoor. That suggests the group has been confident that they would not be detected, or that they simply didn’t see the need to make any updates when their campaign was working so well.
While espionage may be the ultimate aim, the Orangeworm threat group could easily turn to more malicious and damaging attacks. Once the backdoor has been installed on multiple devices, they would be under full control of the hackers. The group has the capability to deploy malware such as wipers and ransomware and cause considerable damage or financial harm.
The ease at which networks can be infiltrated and the backdoor spread should be of major concern for the healthcare industry. The attacks show just how vulnerable the industry is and how poorly protected many organizations are.
The continued use of outdated and unsupported operating systems, a lack of network segmentation to prevent lateral movement once access has been gained, the failure to protect network shares, and poor visibility of the entire network make these attacks far too easy. In fact, simply following security best practices will prevent such attacks.
The attacks by the Orangeworm threat group should serve as a wakeup call to the industry. The next wave of attacks could be far, far worse.
by titanadmin | Apr 19, 2018 | Industry News, Internet Security, Network Security |
What is the future of the system administrator? What can sysadmins expect over the coming months and years and how are their jobs likely to change? Our predictions on what is likely to happen to the role in the foreseeable future.
What Does the Future of the System Administrator Have in Store?
The system administrator is an important role in any organization. Without sysadmins to deal with the day to day IT problems faced by organizations, the business would grind to a halt. Sysadmins also play an essential role in ensuring the security of the network by taking proactive steps to keep systems secure as well as responding to threats before they result in a data breach. With more cyberattacks occurring, increasingly complex IT systems being installed, and the fast pace of technological development, one thing is for sure: The future of the system administrator is likely to continue to involve long hours and hard work.
It is also easy to predict that the future of the system administrator will involve major changes to job descriptions. That has always been the case and never more so than now. There will be a continued need for on the job training and new systems and processes must continue to be learned. Being a System administrator is therefore unlikely to be boring.
According to data from the US Bureau of Labor Statistics, there is likely to be sustained growth in the profession for the next two years. While the forecast was previously 12% growth, this has now been reduced to 6% – similar to other occupations. The increased automation of many sysadmin tasks is partly responsible for this decline in growth, since businesses are likely to need less staff as manual processes are reduced. That said, the figures indicate demand for IT workers will remain high. Even with newer, faster technology being implemented, staff are still required to keep everything running smoothly.
XaaS, the Cloud, Virtualization, and VoIP Use to Grow
Unfortunately, while automation means greater efficiency, it can entail many hidden costs. For a start, with more automation it can become harder to determine the source of a problem when something goes wrong. Increased automation also means the system administrator must become even more knowledgeable. Automation typically involves scripting in various languages, so while you may have been able to get away with knowing Python or Windows PowerShell, you will probably need to become proficient in both, and maybe more.
If you are considering becoming a system administrator, now is the time to learn your first scripting language, as it will make it easier to learn others on the job if you understand the basics. It will also help you to get the job in the first place. The more you know, the better.
Use of the cloud is increasing, especially for backup and archiving, which in turn has reduced the need for server-centered tasks. While there has been a reduction in labor-intensive routine data operations, there has been a rise in the need to become proficient in the use of Application Programming Interfaces (APIs).
While many functions are now being outsourced through XaaS, it is still important to understand those functions. The future of the system administrator is likely to require XaaS to be screened and assessed to make sure those services match the IT needs of the organization. Sales staff will likely say their XaaS meets all business needs. Having an SA that understands the functions, the technology, and the needs of the business will be invaluable for screening out the services that are unsuitable.
To cut costs, many businesses are turning to VoIP. While this does offer considerable cost savings, businesses cannot tolerate less than the 99.999% of uptime offered by phone companies. The future of the system administrator is therefore likely to involve a thorough understanding of the dynamics of network load.
Virtualization has also increased, with a myriad of virtual networks making the SA’s job more complex. That means knowledge of switching and routing will have to improve.
Communication, Collaboration, and Negotiation Skills Required
The SA’s job no longer just involves studying manuals and learning new systems. SAs are now expected to be able to communicate more effectively, understand the business, and collaborate with others. SAs will need strong communication skills, must become excellent collaborators, and also be skilled at negotiation. Fortunately, there are many courses available that can help SAs improve in these areas.
by titanadmin | Apr 13, 2018 | Industry News, Internet Security, Network Security |
The SamSam ransomware attacks are continuing and the threat actors behind the campaign are showing no sign of stopping. So far in 2018 there have been at least 10 attacks in the United States, although many more may have gone unreported. Most of the known attacks have hit government agencies, municipalities, and healthcare organizations – all of whom are required to disclose attacks.
The attacks have caused massive disruption, taking computers, servers, and information systems out of action for several days to several weeks. Faced with the prospect of continued disruption to essential business processes, some organizations have chosen to pay the ransom – a risky strategy since there is no guarantee that the keys to unlock the encryption will work or even be supplied.
Others have refused to be extorted, often at great cost. One U.S. healthcare provider, Erie County Medical Center, took six weeks to fully recover from the attack. Mitigating the attack has cost several million dollars.
Multiple SamSam ransomware attacks are possible as the Colorado Department of Transportation discovered. After recovering from an attack in February, a second attack occurred in March.
It is not only financial harm that is caused by the attacks. Another hospital was attacked, and its outpatient clinic and three physician hospitals were unable to view histories or schedule appointments. The ransomware attack on the electronic medical record provider AllScripts saw its EMR systems taken out of action for several days. During that time, around 1,500 medical centers were unable to access patient health records resulting in many cancellations of non-critical medical appointments.
The March SamSam ransomware attack on the City of Atlanta brought many government services to a grinding halt. The extensive attack forced the shutdown of many systems, many of which remained inaccessible for six days. Bills and parking tickets couldn’t be paid and court proceedings had to be cancelled. The huge backlog of work continued to cause delays when systems were restored.
While the SamSam ransomware attacks have been concentrated on just a few industry sectors, the attacks are not necessarily targeted. What the victims have in common is they have been found to have easily exploitable vulnerabilities on public facing servers. They were attacked because mistakes had been made, vulnerabilities had not been patched promptly, and weak passwords had been set.
The threat actors behind the latest SamSam ransomware attacks have not been confirmed, although researchers at Secureworks believe the attacks are being conducted by the Gold LOWELL threat group. It is not known whether they are a defined group or a network of closely affiliated threat actors. What is known, whether it is GOLD LOWELL or other group, is they are largely staying under the radar.
What is more certain is the SamSam ransomware attacks will continue. In the first four weeks of January, the Bitcoin wallet used by the attackers showed $325,000 of ransom payments had been paid. The total in April is likely to be substantially higher. Hancock Health, one of two Indiana hospitals attacked this year, has confirmed that it paid a ransom demand of approximately $55,000 for the keys to unlock the encryption. As long as the attacks remain profitable and the threat actors can stay under the radar, there is no incentive to stop.
In contrast to many threat actors that use phishing emails and spam messages to deliver ransomware downloaders, this group exploits vulnerabilities on public-facing servers. Access is gained to the network, the attackers spend time navigating the network and moving laterally, before the ransomware payload is finally deployed. Detecting network intrusions quickly may prevent file encryption, or at least limit the damage caused.
The ongoing campaign has now prompted the U.S. Department of Health and Human Services’ Healthcare Cybersecurity Integration and Communications Center (HCCIC) to issue a warning to healthcare organizations about the continued threat of attacks. Healthcare organizations should heed the advice of the HCCIC and not only implement defences to block attacks but also to prepare for the worst. If contingency plans are made and incident response procedures are developed in advance, disruption and cost will be kept to a minimum.
That advice from the HCCIC to prevent SamSam ransomware attacks is:
- Conduct vulnerability scans and risk assessments to identify potential vulnerabilities
- Ensure those vulnerabilities are remediated
- Ensure patches are applied promptly
- Use strong usernames and passwords and two-factor authentication
- Limit the number of users who can login to remote desktop solutions
- Restrict access to RDP behind firewalls and use a VPN or RDP gateway
- Use rate limiting to stop brute force attacks
- Ensure backups are made for all data to allow recovery without paying the ransom and make sure those backups are secured
- Develop a contingency plan to ensure that the business can continue to function while the attack is mitigated
- Develop procedures that can easily be followed in the event of a ransomware attack
- Implement defenses capable of detecting attacks quickly when they occur
- Conduct annual penetration tests to identify vulnerabilities and ensure those vulnerabilities are rapidly addressed
by titanadmin | Mar 28, 2018 | Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam Advice |
A city of Atlanta ransomware attack has been causing havoc for city officials and Atlanta residents alike. Computer systems have been taken out of action for several days, with city workers forced to work on pen and paper. Many government services have ground to a halt as a result of the attack.
The attack, like many that have been conducted on the healthcare industry, involved a variant of ransomware known as SamSam.
The criminal group behind the attack is well known for conducting attacks on major targets. SamSam ransomware campaigns have been conducted on large healthcare providers, major educational institutions, and government organizations.
Large targets are chosen and targeted as they have deep pockets and it is believed the massive disruption caused by the attacks will see the victims pay the ransom. Those ransom payments are considerable. Demands of $50,000 or more are the norm for this group. The City of Atlanta ransomware attack saw a ransom demand issued for 6 Bitcoin – Approximately $51,000. In exchange for that sum, the gang behind the attack has offered the keys to unlock the encryption.
SamSam ransomware attacks in 2018 include the cyberattack on the electronic health record system provider Allscripts. The Allscripts ransomware attack saw its systems crippled, with many of its online services taken out of action for several days preventing some healthcare organizations from accessing health records. The Colorado Department of Transportation was also attacked with SamSam ransomware.
SamSam ransomware was also used in an attack on Adams Memorial Hospital and Hancock Health Hospital in Indiana, although a different variant of the ransomware was used in those attacks.
A copy of the ransom note from the city of Atlanta ransomware attack was shared with the media which shows the same Bitcoin wallet was used as other major attacks, tying this attack to the same group.
SecureWorks, the cybersecurity firm called in to help the City of Atlanta recover from the attack, has been tracking the SamSam ransomware campaigns over the past few months and attributes the attacks to a cybercriminal group known as GOLD LOWELL, which has been using ransomware in attacks since 2015.
While many ransomware attacks occur via spam email with downloaders sent as attachments, the GOLD LOWELL group is known for leveraging vulnerabilities in software to install ransomware. The gang has exploited vulnerabilities in JBoss in past attacks on healthcare organizations and the education sector. Flaws in VPNs and remote desktop protocol are also exploited.
The ransomware is typically deployed after access to a network has been gained. SecureWorks tracked one campaign in late 2017 and early 2018 that netted the gang $350,000 in ransom payments. The earnings for the group have now been estimated to be in the region of $850,000.
Payment of the ransom is never wise, as this encourages further attacks, although many organizations have no choice. For some, it is not a case of not having backups. Backups of all data are made, but the time taken to restore files across multiple servers and end points is considerable. The disruption caused while that process takes place and the losses suffered as a result are often far higher than any ransom payment. A decision is therefore made to pay the ransom and recover from the attack more quickly. However, the GOLD LOWELL gang has been known to ask for additional payments when the ransom has been paid.
The city of Atlanta ransomware attack commenced on Thursday March 22, and with the gang typically giving victims 7 days to make the payment. The city of Atlanta only has until today to make that decision before the keys to unlock the encryption are permanently deleted.
However, yesterday there were signs that certain systems had been restored and the ransomware had been eradicated. City employees were advised that they could turn their computers back on, although not all systems had been restored and disruptions are expected to continue.
As of today, no statement has been released about whether the ransom was paid or if files were recovered from backups.
How to Defend Against Ransomware Attacks
The city of Atlanta ransomware attack most likely involved the exploitation of a software vulnerability; however, most ransomware attacks occur as a result of employees opening malicious email attachments or visiting hyperlinks sent in spam emails.
Last year, 64% of all malicious emails involved ransomware. An advanced spam filter such as SpamTitan is therefore essential to prevent attacks. End users must also be trained how to recognize malicious emails and instructed never to open email attachments or click on links from unknown senders.
Software must be kept up to date with patches applied promptly. Vulnerability scans should be conducted, and any issues addressed promptly. All unused ports should be closed, RDP and SMBv1 disabled if not required, privileged access management solutions deployed, and sound backup strategies implemented.
by titanadmin | Mar 20, 2018 | Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News |
The cybersecurity threat level is at an all time high, according to a recently published threat report from McAfee. The AV solution provider has compiled a report from data collected over the final quarter of 2017 which shows the last three months of 2017 saw record numbers of new malware samples detected – 63.4 million samples. A level never before seen.
The soaring value of Bitcoin and other cryptocurrencies in the final quarter of 2017 fueled a massive rise in cryptocurrency hijacking and the use of cryptocurrency miners over other forms of malware that were favored in previous quarters. With Bitcoin valued at $19,000 in December and cryptocurrency mining hardware costing several thousand dollars, it is no surprise that so many threat actors chose to hijack other computers and steal money from cryptocurrency wallets.
Cryptocurrency miners were being used in spam email campaigns, disguised as mobile apps, and there was a massive rise in the hijacking of websites and loading cryptocurrency mining code.
While mining cryptocurrencies has proven to be highly profitable for cybercriminals, they did not abandon the use of other malware variants. The use of ransomware continues to increase, with spam email the primary method of delivery.
McAfee reports that there was 35% ransomware growth in Q4, and 59% growth in 2017. For the fourth consecutive quarter there has been an increase in new ransomware variants, with much of the increase due to the widespread use of Ransom:Win32/Genasom. There is unlikely to be a fall in use of ransomware any time soon.
The use of spam email to deliver malware and ransomware continues to grow, with two botnets – Necurs and Gamut – responsible for delivering 97% of all spam email in Q4, with the former now the most prevalent spamming botnet.
Botnets are also being developed to exploit IoT devices, which typically lack security and often have poor passwords. Infecting the devices allows massive botnets to be easily assembled for use in DDoS and DoS attacks.
Q4 was the fourth consecutive quarter where new malware samples have continued to increase, with total malware samples now just short of 700,000,000. New Mac malware also increased for the third consecutive quarter and there are now approximately 750,000 Mac malware variants, although there was a fall in new mobile malware samples from the 2-year high in Q3.
There was a rise in new Faceliker and macro malware, although the biggest increase was PowerShell malware. Q4 saw a massive jump in new PowerShell downloaders.
While the cybersecurity threat level continues to increase, and all industries are at risk, healthcare was the most targeted industry in 2017 by some distance. Healthcare may have been the third most targeted industry sector in 2016-2017, but the first three quarters of 2017 saw more than twice as many attacks on healthcare organizations than any other industry sector.
McAfee reports that there has been a 210% increase in cybersecurity incidents reported by healthcare organizations in 2017 compared to 2016, although there was some respite in Q4, which saw a 78% quarter over quarter decline in security incidents.
McAfee suggests it is poor security practices that have contributed to the rise in healthcare data breaches and cyberattacks. Many of the reported incidents could have been prevented if cybersecurity best practices had been followed.
by titanadmin | Mar 12, 2018 | Industry News, Internet Security, Network Security |
There have been several major cyberattacks on restaurants in recent months. Organized cybercriminals gangs are using specially crafted malware to silently steal credit card data from POS systems. Not only do the initial intrusions go undetected, the presence of the malware is often not detected for several months, during which time tens of thousands of credit card details are stolen.
Last month saw another large restaurant chain suffer a major breach of payment card data. The cyberattack on Applebee’s affects more than 160 of its RMH Franchise Holdings owned and operated restaurants across 15 states.
Customers who visited one of the RMH restaurants in Alabama, Arizona, Texas, Florida, Illinois, Indiana, Kansas, Kentucky, Ohio, Mississippi, Missouri, Nebraska, Oklohoma, Pennsylvania or Wyoming between November 2017 and January 2018 and paid for their meal on a credit or debit card have potentially had their card details stolen. Customers who paid using the self-pay tabletop devices were not affected, and neither were customers who paid online. The data breach was confined to RMH-operated restaurants. Other restaurants in the Applebee’s network were unaffected.
The data theft occurred as a result of malware on its POS system. The malware had been developed to capture data such as card numbers, expiry dates, CVV codes, and cardholder names. After recording the data, the information was exfiltrated to the attacker’s command and control server.
RMH reports that it has security systems in place to prevent cyberattacks and was able to contain the incident prior to discovery of malware on February 13, 2018. One a breach was discovered, RMH conducted a thorough investigation to identify the full extent of the breach and the individuals potentially impacted. A leading computer forensics firm was contracted to assist with the investigation and help mitigate of the attack. RHM has not disclosed how the malware was installed and nether the type of malware used in the attack.
The Applebee’s cyberattack is the latest in a string of cyberattacks on restaurants and retailers. In 2017 there were similar cyberattacks on restaurants throughout the United States. Arby’s fast food restaurants experienced a POS-malware related breach that affected many of its 1,000+ corporate stores. Chipotle Mexican Grill discovered malware had been installed on its POS system, with most of its stored affected over a 1-month period last spring.
Retailers are also major targets. Earlier this year, the retailer Forever21 discovered malware has been installed on its POS system. It took the retailer 7 months to identify the breach, during which time the credit and debit card details of many thousands of its customers were stolen.
Last year, many of the 750 Kmart stores were infected with POS malware – the second major credit card breach experienced by the chain in the past three years. Buckle Inc., was also attacked, with an undisclosed number of its stores affected. The malware infection remained on its system undetected for more than 5 months.
The breaches highlight the importance of implementing layered defenses to protect the entire attack surface, from spam email defenses to web filters, next generation firewalls, and advanced intrusion detection systems. It is also essential for retailers and restaurateurs to conduct regular vulnerability scans of the entire network to identify and address security flaws, with technical solutions implemented to constantly monitor POS systems for signs of compromise.
by titanadmin | Mar 6, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam Advice, Spam News, Spam Software |
Phishing attacks in healthcare are to be expected. Healthcare providers hold vast quantities of data on patients. Hospitals typically employ hundreds or thousands of members of staff, use many third-party vendors, and historically they have had relatively poor cybersecurity defenses compared to other industry sectors. That makes them an attractive target for phishers.
Phishing is a method of gaining access to sensitive information which typically involves a malicious actor sending an email to an employee in which they attempt to get that individual to reveal their login credentials. This is achieved using social engineering techniques to make the email recipient believe the email is a genuine. For instance, a security alert could inform the email recipient that an online account has been compromised and a password change is required. They are directed to a spoofed website where they are asked to login. The site is fake but looks genuine.
Credentials are entered and passed to the attacker who uses them to gain access to that individual’s account. Phishing can also involve malware. Emails attempt to convince the recipient to open a malware-infected attachment or download a malicious file from a compromised website.
Compliance with HIPAA Rules Helps to Prevent Phishing Attacks in Healthcare
HIPAA Rules require healthcare providers to implement administrative, technical, and physical safeguards to reduce the risk of cyberattacks and phishing. HIPAA only demands a minimum standard for data security be reached, although complying with HIPAA Rules can help to prevent phishing attacks in healthcare.
HIPAA is not technologically specific on the defenses that should be used to protect patient data. Healthcare providers can choose appropriate defenses based on the results of a risk analysis.
It is possible for healthcare organizations to be compliant with HIPAA Rules but still be vulnerable to phishing attacks. If healthcare providers are to block the majority of phishing attacks and truly secure patients’ data, they must go above and beyond the requirements of HIPAA.
HHS’ Office for Civil Rights Warns of Phishing Attacks in Healthcare
Recent phishing attacks in healthcare have prompted the HHS’ Office for Civil Rights to issue a warning about the risk from phishing.
Attacks are now highly sophisticated and can be hard to detect. The emails are often free from spelling mistakes, have near perfect grammar, include brand images and logos, and appear to have been sent from genuine domains. The reasons given for taking a specific course of action are perfectly plausible as is the need for urgent action.
OCR also highlights the rise in spear phishing attacks in healthcare. These attacks involve more targeted attempts to gain access to sensitive information and can be conducted on specific individuals or groups of individuals in an organization – The payroll or HR department for instance.
These attacks often see a CEO or superiors impersonated to add legitimacy to the attack. These attacks tend to require the opening of attachments or visiting links to download malware. Spear phishing emails are also used to request bank transfers or for sensitive information to be sent via email – W2-Forms of employees for instance. Many healthcare employees have been fooled by these scams.
Recent Phishing Attacks in Healthcare
Listed below are some of the recent examples of phishing attacks in healthcare. This is just a small selection of incidents that have resulted in healthcare records being exposed or stolen. The reality is that many data breaches start with a phishing email. Security awareness training company Cofense suggests that as many as 91% of data breaches have their root in a phishing campaign.
November 2017: 1,670 patients of Forrest General Hospital have their PHI exposed following a phishing attack on business associate HORNE.
October 2017: Henry Ford Health System discovers several email accounts were compromised as a result of employees responding to phishing emails. The PHI of 18,470 patients may have been stolen.
September 2017: Employees of UPMC Susquehanna responded to phishing emails with the attackers able to gain access to the PHI of 1,200 patients.
September 2017: A phishing attack on Wisconsin-based Network Health resulted in the PHI of approximately 51,000 patients being exposed.
August 2017: Chase Brexton Health Care in Maryland experienced a phishing attack that saw several email accounts compromised along with the PHI of 16,000 patients.
July 2017: The Medical College of Wisconsin experienced a phishing attack that allowed attackers to gain access to email accounts and the PHI of 9,500 patients.
July 2017: RiverMend Health employees responded to phishing emails and their accounts were accessed by the attackers. The PHI of 1,200 patients was potentially viewed or stolen.
June 2017: A phishing attack on Elderplan Inc., saw several email accounts compromised along with the PHI of 22,000 individuals.
June 2017: MJHS Home Care experienced a phishing attack that saw email access gained by an unauthorized individual. The compromised email accounts contained the PHI of 6,000 patients.
Staff Training and Anti-Phishing Technology
HIPAA does not specifically mention spam filters, but since phishing is used to target employees via email, spam filtering can be considered essential. By filtering out the majority of spam and malicious messages there is less potential for an employee to click on a malicious link or open a malware infected email attachment.
SpamTitan is a cloud-based anti-spam service that blocks more than 99.9% of spam emails from being delivered to inboxes and has a 0.03% false positive rate. Dual antivirus engines (Bitdefender/ClamAV) ensure malicious email attachments are blocked.
Healthcare employees are the last line of defense, so it is important for them to be able to recognize email threats and anti-phishing training is a requirement of HIPAA. In July 2017, OCR issued advice to healthcare organizations on anti-phishing training in its cybersecurity newsletter.
OCR also recommends using multi-factor authentication to ensure email accounts are not compromised when a password is guessed or stolen. Software and operating systems must be kept up to date and fully patched to prevent vulnerabilities from being exploited, and anti-virus and anti-malware solutions should be deployed to prevent infection. Regular backups can also prevent data loss in the event of a malware or ransomware infection.
by titanadmin | Mar 5, 2018 | Industry News, Spam News, Spam Software |
Titan HQ has announced from March 5, 2018 all new customers signing up to use the SpamTitan cloud-based anti-spam service will benefit from leading antivirus and anti-malware protection from Bitdefender. All existing customers will similarly be protected by Bitdefender, although first they will need to upgrade to SpamTitan v7.00. v7.00 was released on March 5.
The primary AV engine used in previous versions of SpamTitan was provided by Kaspersky Lab, with ClamAV used as a secondary AV engine. SpamTitan v7.00 will also incorporate ClamAV as a secondary AV engine. Kaspersky AV will no longer be supported on SpamTitan suite of products from May 1, 2018.
The change to the new primary AV engine is due to a growing strategic relationship with Bitdefender. Further collaboration with the Romanian cybersecurity firm is planned for the future. Customers already using SpamTitan are encouraged to upgrade to the latest version of the product as soon as possible as several other updates have been incorporated into the latest version, including patches for recently discovered vulnerabilities in ClamAV.
These include the use-after-free vulnerability CVE-2017-12374; buffer overflow vulnerabilities CVE-2017-12375 and CVE-2017-12376; Mew Packet Heap Overflow vulnerability CVE-2017-12377; Buffer Overflow in messageAddArgument vulnerability CVE-2017-12379; and Null Dereference vulnerability CVE-2017-12380. TitanHQ has also included patches for openssl, openssh, php, and wget and updates have been included to resolve potential denial of service attacks.
Customers already on v6.x of the platform who have enabled prefetch of system updates will find the latest patches in the list of available updates on the System updates page. If this option is disabled, they should use the ‘Check for Updates Now’ option in the user interface.
Customers using SpamTitan v4 and v5 have been advised that support for both versions of SpamTitan will cease on May 1, 2018. An upgrade to version 7.00 will therefore be required before the deadline. It is important to note that the update process requires v4/5 to first be upgraded to v6 before installing SpamTitan v7.00. Upgrading to the new version will not change the existing configuration of the product.
Customers should allow 10-20 minutes for the installation of the new version and should read all product notes before installation.
by titanadmin | Feb 26, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News |
A Colorado Department of Transportation ransomware attack on February 21, 2018 affected at least 21 computers preventing files from being accessed by employees. A prompt response to the ransomware attack limited the harm caused, although to prevent the spread of the ransomware more than 2,000 computers were shut down.
The attack has already caused considerable disruption, which is ongoing as the cleanup operation continues.
The DOT says it received a ransom demand which would need to be paid in order to obtain the keys to unlock encrypted files, but that the DOT has no intention of paying any money to the attackers. Instead the firm has called in an external cybersecurity firm (McAfee) to restore data on the affected workstations and ensure all devices are clean and protected from infection. All encrypted files will be recovered from backups.
Fortunately, the ransomware attack was limited to certain endpoints. Other computer systems that are used with surveillance cameras and traffic alerts were not affected.
The Colorado Department of Transportation ransomware attack is one of several high-profile attacks involving SamSam ransomware to have been reported this year. Hancock Health Hospital in Indiana was one notable victim. The hospital was issued with a ransom demand and paid the attackers for the keys to unlock the encryption, even though backups could have been used to recover files. A Bitcoin payment worth approximately $55,000 is believed to have been paid. The payment was believed to be considerably less than the cost of disruption while files were recovered from backups.
Another Indiana hospital – Adams Memorial Hospital was also attacked with a variant of SamSam ransomware, and Allscripts – an electronic health record provider – also suffered an attack that took down some of its web services.
SamSam ransomware first surfaced in 2015, and while some antivirus and antimalware solutions can detect the malware, the attackers continue to release new variants that are much better at evading detection.
Bleeping Computer reported on January 19 that one of the Bitcoin wallets used by the gang involved in SamSam ransomware campaign had already made approximately $300,000 from ransom payments, although that figure will almost certainly be higher since multiple Bitcoin wallets are believed to be used and the campaign is ongoing.
On February 15, Secureworks reported that the profits from the attacks had increased to at least $350,000, with the firm attributing the attacks to a hacking group called Gold Lowell.
It is unclear how the Colorado Department of Transportation ransomware attack occurred. Some sources report that the attack involved phishing emails, although Gold Lowell’s modus operandi is leveraging vulnerabilities in Remote Desktop Protocol (RDP) services.
With the campaign ongoing, all businesses should be alert to the threat from phishing and RDP attacks. Spam filters, such as TitanHQ’s cloud-based anti-spam service, are essential as is anti-phishing training for employees. If RDP is necessary, strong passwords should be set and controls implemented to reduce the potential for brute force attacks. Rate limiting on login attempts for example. It is also important to make sure that multiple data backups are performed to ensure files can be recovered in the event of an attack.
by titanadmin | Feb 23, 2018 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News |
A new report has been released that shows there has been a massive rise in the global cost of cybercrime, highlighting the seriousness of the threat from hackers and scammers. 2017 global cybercrime costs exceeded $600 billion, according to the McAfee report. That represents a 20% increase since 2014, when the global cybercrime costs were calculated to be around $500 billion. The current global cybercrime costs equate to 0.8% of global GDP.
The report shows that in spite of increases in cybersecurity spending, hackers and scammers are still managing to breach organizations’ defenses and gain access to sensitive data, login credentials, corporate bank accounts, and intellectual property.
Accurately Determining the Global Cost of Cybercrime
Any calculation of global cybercrime costs involves some margin of error, as the figures cannot be totally based on reported losses by businesses. Many companies do not disclose details of data breaches, and even fewer publish information of the financial impact of cyberattacks. When details about financial losses are published, typically only a fraction of the losses are reported. In many cases the losses are not known until many years after the event. It is therefore difficult to obtain a true picture of the losses due to cybercrime because of the shortage of data.
To try to gain an accurate picture of the total cost of cybercrime, McAfee had to turn to the same modelling techniques used by government agencies to determine the costs of criminal activities such as drug trafficking, prostitution, maritime piracy, and organizational crime groups.
McAfee is not the only company to make these predictions. Compared to some reports the figures from McAfee seem quite conservative. The true cost could be considerably higher.
Factors Contributing to the Increase in Losses
McAfee reports that several factors have contributed to the large increase in cybercrime costs over the past few years. The growth in popularity of ransomware has played a part. Ransomware has proved to be a particularly plump cash cow, allowing cybercriminals to rake in millions by extorting companies. The anonymity of cryptocurrencies has helped these cybercriminal gangs obtain payments without detection, while the use of TOR has helped the gangs stay under the radar of law enforcement agencies.
Ransomware-as-a-service has also boosted profits for cybercriminals. The increase in the number of individuals conducting attacks has made it possible to increase the scale of operations and distribute the malicious code more effectively. State-sponsored hacks have also increased, including attacks aimed at sabotaging businesses and critical infrastructure as well as major heists that have seen millions of dollars stolen.
McAfee cites research showing around 300,000 new malware samples are now being identified on a daily basis, while data breaches are exposing a staggering 780,000 records a day.
Personal records can sell for big bucks on darknet forums; however, one of the biggest costs is the theft of intellectual property, which McAfee estimates has resulted in at least 25% of the annual losses to cybercrime. When patented processes are obtained, the benefits of millions in research and development is lost and companies can lose their competitive advantage.
One thing is clear from the report. With global cybercrime costs rising, and the sophistication and frequency of attacks increasing, companies have little alternative than to invest more in cybersecurity and develop more sophisticated defenses.
by titanadmin | Feb 12, 2018 | Industry News, Internet Security |
Last week news broke that government supercomputers in Russia had been turned into cryptocurrency miners, now comes news that many UK government websites have been infected with cryptocurrency mining code.
More than 4,200 Websites Infected with Cryptocurrency Mining Code
The latest attack affects government websites around the globe, with more than 4,200 websites turning visitors’ computers into cryptocurrency miners.
The attack involved a popular website plugin called Browsealoud. Browsealoud is used to convert written website content into audio for the blind and partially sighted. The browser plugin was compromised by hackers who altered the source code of the plugin to include cryptocurrency mining code. By altering the plugin, the malicious code runs every time a site user visits a webpage that offers the audio function using the Browsealoud plugin.
When a visitor arrived at such as webpage, the code ran and turned that user’s computer into a cryptocurrency miner, using the computer’s processing power to mine Monero. Mining is the term given to verifying cryptocurrency transfers. Mining requires a computer to solve a complex problem. Once that problem is solved, the miner is rewarded with a small payment. In this case, the individual(s) who altered the code.
Using one computer to mine cryptocurrency will only generate a small return. However, by hijacking a browser plugin on a website that is visited by many thousands of individuals, the potential returns are considerable. The processing power of millions of computers can be harnessed.
Browsealoud was developed by the British company Texthelp. According to its website, its plugin has been installed on 4,275 domains. In the United Kingdom, many government websites use the plugin, including the Financial Ombudsman Service, the Information Commissioner’s Office, the Student Loans Company, many National Health Service (NHS) websites, and local government websites including the .gov.uk sites used by Camden, Croydon, Manchester, and Newham to name but a few. Many federal and state government websites in the US have turned their visitors’ devices into cryptocurrency miners, and it is the same story in Australia, Ireland, Sweden, and beyond.
The Browsealoud plugin is understood to have been infected with cryptocurrency mining code at some point between 0300 and 1145 UTC on February 11, 2018. The code was only active for a few hours before the change was identified and Texthelp disabled the plugin.
The mining only took place while a visitor was on a webpage that used the Browsealoud plugin. As soon as the tab or browser was closed, the mining stopped. Visiting the website that had been infected with cryptocurrency mining code via the plugin would not result in a malware infection. The only noticeable effect for any visitors to the websites would have been a slowing down of their computers or the fan starting as their computer started going into overdrive.
This incident has however made it quite clear to government agencies that their websites are not secure and using third party plugins on their sites to improve services for website users introduces risk.
How to Secure Your Website Against JavaScript-Based Supply-Chain Attacks
These supply-chain attacks exploit a trusted relationship between the website owner and a third-party software/plugin supplier and the benefits for cybercriminals are clear. All it takes is for one plugin to be hacked to have malicious code run on many thousands of websites, thus targeting millions of website visitors. In this case, the damage caused was minimal, but the attack could have been much worse. The goal on this occasion was to mine cryptocurrency. The attackers could easily have inserted much more malicious code and attempted to steal login credentials.
In this case, the plugin required websites to use JavaScript in their content for the plugin to work. Wordfence has recently published details of a simple script that can be included on websites that use JavaScript from third parties that will prevent code from running if it has been modified from its original form.
Protecting sites requires the use of a security feature called Subresource Integrity (SRI). Websites that include JavaScript from an external source using the <SCRIPT> tag can include an integrity attribute to prevent modified JavaScript from running. An SRI hash for a website can be generated on here.
One problem with using this approach is any modification to the code will prevent the JavaScript from running, which means the JavaScript will also be blocked when legitimate updates are made by the plugin developer.
That means a new hash is required if the vendor does not include a version number in their updated code. However, it will ensure that attacks such as this, or worse attacks with much more malicious code, will be blocked.
by titanadmin | Feb 8, 2018 | Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam Software, Website Filtering |
Following a slew of cyber extortion attacks on schools, the FBI and the Department of Education’s Office of the Inspector General have issued a warning. Schools need to be alert to the threat of cyber extortion and must take steps to mitigate risk by addressing vulnerabilities, developing appropriate policies and procedures, and using technologies to secure their networks.
K12 schools and other educational institutions are an attractive target for cybercriminals. They hold large quantities of valuable data – The types of data that can be used to commit identity theft and tax fraud. Further, in education, security defenses are typically of a much lower standard than in other industries. Poor defenses and large volumes of valuable data mean cyberattacks are inevitable.
The warning comes after several cyber extortion attacks on schools by a group of international hackers known collectively as TheDarkOverlord. The hacking group has conducted numerous attacks on the healthcare industry the public school system since April 2016.
The modus operandi of the hacking group is to search for vulnerabilities that can be easily exploited to gain access to internal networks. Once network access is gained, sensitive data is identified and exfiltrated. A ransom demand is then issued along with the threat to publish the data if payment is not made. The hacking group does not make empty threats. Several organizations that have failed to pay have seen their data dumped online. Recent attacks have also included threats of violence against staff and students.
Access to networks is typically gained by exploiting vulnerabilities such as weak passwords, poor network security, unpatched software, and misconfigured databases and cloud storage services.
The FBI reports that the hacking group has conducted at least 69 cyber extortion attacks on schools, healthcare organizations, and businesses and has stolen more that 100 million records containing personally identifiable information. More than 200,000 of those records have been released online after ransom demands were ignored. More than 7,000 students have had their PII exposed by the hackers.
The escalation of the threats to include violence have caused panic and some schools have been temporarily closed as a result. Sensitive data has been released which has placed staff and students at risk of financial losses due to fraud. The FBI recommends not paying any ransom demand as it just encourages further criminal activity. What schools must do is take steps to mitigate risk and make it harder for their institution to be attacked. By doing so, cybercriminals are likely to continue their search for organizations that are easier to attack.
Ransomware and DDoS Attacks are Rife
TDO is not the only criminal group conducting cyber extortion attacks on schools, and these direct attacks are not the only way access to school networks is gained.
The past two years have seen a massive rise in the use of ransomware on schools. Ransomware attacks are often indiscriminate, taking advantage of vulnerabilities in human firewalls: A lack of security awareness of staff and students. These attacks commonly involve email, with malicious attachments and links used to deliver the ransomware payload.
Ransomware is malicious code that is used to search for stored files and encrypt them to prevent access. With files encrypted, organizations must either restore files from backups or pay the ransom demand to obtain the key to unlock the encryption. Since the code can also encrypt backup files, many organizations have had no alternative other than paying the ransom, since data loss is not an option.
Other cyber extortion attacks on schools do not involve data theft. DoS and DDoS attacks bombard servers with thousands or millions of requests preventing access and often damaging hardware. Cybercriminal gangs use mafia-style tactics to extort money, threatening to conduct DoS/DDoS attacks unless payment is made. Alternatively, they may conduct the attacks and demand payment to stop the attack.
The rise in cyber extortion attacks on schools means action must be taken to secure networks. A successful attack often results in educational institutions suffering major losses. The ransom payment is only a small part of the total cost. Removing ransomware, rebuilding systems, and protecting individuals whose sensitive data has been exposed can cost hundreds of thousands of dollars.
How to Protect Against Cyber Extortion Attacks on Schools
Schools and other educational institutions can develop policies and procedures and use technologies to deter cybercriminals and improve network and email security. By adhering to IT best practices and adopted a layered approach to security, it is possible to mount a robust defense and prevent cyber extortion attacks on schools.
Educational institutions should:
Implement strong passwords: Weak passwords can easily be cracked using brute force methods. Set strong passwords (Upper/lower case letters, numbers, and special characters or long 15+ digit passphrases) and use rate limiting to block access attempts after a set number of failures. Never reuse passwords for multiple accounts.
Patch promptly: Vulnerabilities in software and operating systems can easily be exploited to gain access to networks. Develop good patch management policies and ensure all software and operating systems are updated promptly.
Implement an advanced spam filter: Phishing and spam emails are commonly used to deliver ransomware and obtain login credentials. Do not rely on the spam filters of email service providers. Implement separate, advanced anti spam software or a cloud-based filtering service to block email-based threats and prevent them from reaching inboxes.
Provide security awareness training: Cybersecurity should be taught. Staff and students should be made aware of email and web-based threats and told how to identify malicious emails and potential web-based threats.
Implement a web filter: A web filter is necessary for CIPA compliance to protect students from harm caused by viewing obscene images online. A web filter is also an important cybersecurity defense that can block malware and ransomware and stop staff and students from visiting phishing websites. Web filters protect staff and students at school, but also protect devices that are taken home.
Secure remote desktop/access services: Conduct audits to determine which devices have remote access enabled. If remote access is not necessary, ensure it is disabled. If the services cannot be disabled, ensure they are secured. Use Secure Sockets Layer (SSL) Transport Layer Security for server authentication, ensure sessions are encrypted, and use strong passwords. Whitelist access is strongly recommended to ensure only authorized devices can connect.
Use two-factor authentication: Use two-factor authentication on all accounts to prevent access if a password is used on an unfamiliar device.
Limit administrator accounts: Administrator accounts should be limited. When administrator access is not required, log out from those accounts and use an account with fewer privileges.
Segment your network: Segmenting the network can limit the damage caused when malware and ransomware is installed, preventing it from spreading across the entire network.
Scan for open ports and disable: Conduct a scan to identify all open ports and ensure those open, unused ports are disabled.
Monitor audit logs: Audit logs for all remote connection protocols, check logs to ensure all accounts were intentionally created, and audit access logs to check for unauthorized activity.
Backup all data: Good backup polices are essential for recovery from ransomware attacks: Adopt a 3-2-1 approach. Make three copies of backups, store them on at least two different media, and keep one copy off site. Backups should be on air-gapped devices (not connected to the Internet or network).
by titanadmin | Jan 5, 2018 | Industry News, Internet Security, Network Security |
It has been pretty difficult to avoid the news of Meltdown and Spectre – Two vulnerabilities recently discovered that could potentially be exploited to gain access to sensitive information on PCs, Macs, servers, and smartphones. Meltdown and Spectre affect virtually all devices that contain CPUs, which amounts to billions of devices worldwide.
What are Meltdown and Spectre?
Meltdown and Spectre are two separate vulnerabilities affecting CPUs – central processing units. The chips that power a wide range of electronic devices. The flaws make devices vulnerable to side-channel attacks, in which it is possible to extract information from instructions that have been run on CPUs, using the CPU cache as a side channel.
There are three types of attacks, two for Spectre and one for Meltdown. Spectre Variant 1 – tracked as CVE-2017-5753- is a bounds check bypass, while Spectre variant 2 – tracked as CVE-2017-5715 – is a branch target injection. Variant 3, termed Meltdown – tracked as CVE-2017-5754 – is a rogue data cache load, memory access permission check that is performed after kernel memory read.
The less technical explanation is the attacks leverage the prediction capabilities of the CPU. The CPU will predict processes, load them to an easily accessible, fast sector of the memory to save time and ensure fast performance. Spectre allows data to be read from the memory, but also for information to be loaded into the memory and read that would otherwise not be possible.
Meltdown also reads information from the memory, stealing information from memory used by the kernel that would not normally be possible.
What Devices are Affected by Meltdown and Spectre?
US-CERT has warned that the following vendors have been affected by Meltdown and Spectre: AMD, Apple, Arm, Google, Intel, Linux Kernel, Microsoft, and Mozilla. Apple has said that virtually all of its Macs, iPhones, and iPads are affected. PCs and laptops with Intel, Arm, and AMD chips are affected by Spectre, as are Android smartphones. while Meltdown affects desktops, laptops, and servers with Intel chips. Since servers are affected, that has major implications for cloud service providers.
How Serious are Meltdown and Spectre?
How serious are Meltdown and Spectre? Serious enough for the Intel chief executive officer, Brian Krzanich, to sell $25 million of his shares in the company prior to the announcement of the flaws, although he maintains there was no impropriety and the sale of the shares was unrelated to the announcement of the flaws a little over a month later.
For users of virtually all devices that contain CPUs, the flaws are certainly serious. They could potentially be exploited by malicious actors to gain access to highly sensitive data stored in the memory, which can include passwords and credit card data.
What makes these flaws especially serious is the number of devices that are affected – billions of devices. Since one of the flaws affects the hardware itself, which cannot be easily corrected without a redesign of the chips, resolving the problem will take a considerable amount of time. Some security experts have predicted it could take decades before the flaws are totally eradicated.
Fortunately, companies have been scrambling to develop patches that can at least reduce the risk of the flaws being exploited. For example, Chrome and Firefox have already released updates that will prevent attacks from occurring via browsers. Since the attacks can be performed using JavaScript, securing web browsers is essential.
At present, it would appear that the flaws have not been exploited in the wild, although now the news has broken, there will certainly be no shortage of individuals attempting to exploit the flaws. Whether they are able to do so remains to be seen.
What Can You do to Prevent Meltdown and Spectre Attacks?
As is the case when any vulnerability is identified, protecting against Meltdown and Spectre requires patches to be applied. All software should be updated to the latest versions, including operating systems, software packages, and browsers. Keeping your systems 100% up to date is the best protection against these and other attacks.
Some third-party antivirus software will prevent Windows patches from being installed, so before Windows can be updated, antivirus must be updated. Ensure that your AV program is kept up to date, and if you have automatic updates configured for Windows, as soon as your system is ready for the update it will be installed.
Chrome and Firefox have already been updated, Microsoft will be rolling out a patch for Windows 10 on Thursday, and over the next few days, updates will be released for Windows 7 and 8. Apple has already updated MacOS version 10.13.2, with earlier versions due to receive an update soon.
Google has already issued updates for Android phones, although only Google devices have so far been updated, with other manufactures due to roll out the updates shortly. Google has already updates its Cloud Platform, and Amazon Web Services has also reportedly been updated. Linux updates will also be issued shortly.
Fixes for Meltdown are easier to implement, while Spectre will be harder as true mitigations would require major changes to the way the chips work. It is unlikely, certainly in the short term, for Intel to attempt that. Instead, mitigations will focus on how programs interact with the CPUs. As US-CERT has warned, “[The] Underlying vulnerability is caused by CPU architecture design choices. Fully removing the vulnerability requires replacing vulnerable CPU hardware,” although that advice is no longer detailed in its updated vulnerability warning.
Applying patches will help to keep computers protected, but that may come at a cost. For example, the fix for the Meltdown vulnerability changes the way the computer works, which means the processor will have to work harder as it has to repeatedly access information from the memory – tasks that would otherwise not normally need to be performed.
That will undoubtedly have an impact on the performance of the machine. How much of a dip in performance can be expected? Some experts predict the changes could slow computers down by as much as 30%, which would certainly be noticed at times when processor activity is particularly high.
by titanadmin | Jan 4, 2018 | Industry News, Internet Security, Network Security |
A recently discovered Forever 21 POS malware attack has seen customers’ credit card data compromised. While malware attacks on retail POS systems are now commonplace, in the case of the Forever 21 POS malware attack, the security breach stands out due to the length of time malware was present on its systems. Attackers first gained access to its POS system seven months before the infection was discovered.
The Forever 21 POS malware infections were first identified in October, when a third-party linked credit card fraud to customers who had previously visited Forever 21 stores. The potential malware infections were investigated and a third-party cybersecurity firm was called in to assist.
Forever 21 first made the announcement about a data breach in November, although the investigation has been ongoing and now new details about the attack have been released.
The investigation has revealed the attack was extensive and affected many POS devices used in its U.S. stores. The Forever 21 POS malware attack started on April 3, 2017, with further devices compromised over the following 7 months until action was taken to secure its systems on November 18, 2017. Forever 21 reports that some POS devices in its stores were only compromised for a few days, others for a few weeks, while some were compromised for the entire timeframe.
In response to the increased threat of cyberattacks on retailers, Forever 21 started using encryption technology on its payment processing systems in 2015; however, the investigation revealed the encryption technology was not always active.
While the encryption technology was active, the attackers would have been prevented from obtaining the credit card details of its customers, although the information could be stolen at times when the encryption technology was turned off.
Further, some devices that were compromised by the malware maintained logs of completed credit card transactions. When the encryption technology was not active, details of completed transactions were stored in the logs and could therefore be read by the attackers. Since those logs contained details of transactions prior to the malware infections, it is possible that customers who visited affected Forever 21 stores prior to April 3, 2017 may also have had their credit card details stolen.
Each store uses multiple POS devices to take payments from consumers, and in most cases only one device per store was compromised. The attackers concentrated their efforts on stores where POS devices did not have encryption enabled. Further, the attackers main aim appeared to be to find and infect devices that maintained logs of transactions.
On most POS devices, the attackers searched for track data read from payment cards, and in most cases, while the number, expiry date and CVV code was obtained, the name of the card holder was not.
The investigation into the Forever 21 POS malware attack is ongoing, and at present it is unclear exactly how many of the company’s 700+ stores have been affected, how many devices were infected, and how many customers have had their credit and debit card details stolen. However, it is fair to assume that an attack of this duration will have affected many thousands of customers.
The type of malware used in the attack is not known, and no reports have been released that indicate how the attackers gained access to its systems. It is not yet known if stores outside the US have been affected.
by titanadmin | Dec 27, 2017 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam Advice |
Digimine malware is a new threat that was first identified from a campaign in South Korea; however, the attacks have now gone global.
Ransomware is still a popular tool that allows cybercriminals to earn a quick payout, but raised awareness of the threat means more companies are taking precautions. Ransomware defenses are being improved and frequent backups are made to ensure files can be recovered without paying the ransom. Not only is it now much harder to infect systems with ransomware, rapid detection means large-scale attacks on companies are prevented. It’s harder to get a big payday and the ability to restore files from backups mean fewer organizations are paying up.
The surge in popularity of cryptocurrency, and its meteoric rise in value, have presented cybercriminals with another lucrative opportunity. Rather than spread ransomware, they are developing and distributing cryptocurrency miners. By infecting a computer with a cryptocurrency miner, attackers do not need to rely on a victim paying a ransom.
Rather than locking devices and encrypting files, malware is installed that starts mining (creating) the cryptocurrency Monero, an alternative to Bitcoin. Mining cryptocurrency is the verification of cryptocurrency transactions for digital exchanges, which involves using computers to solve complex numeric problems. For verifying transactions, cryptocurrency miners are rewarded with coins, but cryptocurrency mining requires a great deal of processing power. To make it profitable, it must be performed on an industrial scale.
The processing power of hundreds of thousands of devices would make the operation highly profitable for cybercriminals, a fact that has certainly not been lost on the creators of Digimine malware.
Infection with Digimine malware will see the victim’s device slowed, as its processing power is being taken up mining Monero. However, that is not all. The campaign spreading this malware variant works via Facebook Messenger, and infection can see the victim’s contacts targeted, and could potentially result in the victim’s Facebook account being hijacked.
The Digimine malware campaign is being spread through the Desktop version of Facebook Messenger, via Google Chrome rather than the mobile app. Once a victim is infected, if their Facebook account is set to login automatically, the malware will send links to the victim’s contact list. Clicking those links will result in a download of the malware, the generation of more messages to contacts and more infections, building up an army of hijacked devices for mining Monero.
Infections were first identified in South Korea; however, they have now spread throughout east and south-east Asia, and beyond to Vietnam, Thailand, Philippines, Azerbaijan, Ukraine, and Venezuela, according to Trend Micro.
A similar campaign has also been detected by FortiGuard Labs. That campaign is being conducted by the actors behind the ransomware VenusLocker, who have similarly switched to Monero mining malware. That campaign also started in South Korea and is spreading rapidly. Rather than use Facebook Messenger, the VenusLocker gang is using phishing emails.
Phishing emails for this campaign contain infected email attachments that download the miner. One of the emails claims the victim’s credentials have been accidentally exposed in a data breach, with the attachment containing details of the attack and instructions to follow to mitigate risk.
These attacks appear to mark a new trend and as ransomware defenses continue to improve, it is likely that even more gangs will change tactics and switch to cryptocurrency mining.
by titanadmin | Dec 20, 2017 | Email Scams, Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News |
A Q3 malware threat report from McAfee charts the continued rise in malware threats throughout the year. Malware variants have now reached an all time high, with the volume of threats having risen each quarter in 2017.
In 2016, there were high levels of malware in Q1, rising slightly in Q2 before tailing off in Q3 and A4. That trend has not been seen this year. The malware threat report shows Q1 figures were higher than the previous two quarters, with a massive rise in Q3 and a continued increase in Q3. Malware threats rose 10% quarter over quarter, rising to a quarterly total of 57.6 million new samples of malware: The highest quarterly total detected by McAfee. That averages out at a new malware sample detected every quarter of a second!
The ransomware epidemic has also got worse in Q3, with new ransomware variants increasing by 36% last quarter, fueled by a sharp increase in Android screen lockers. In total, new mobile malware variants increased by 60% in Q3.
In its Q3 Malware Threat Report, McAfee noted that attackers were continuing to rely on spam email to distribute malware, with the Gamut botnet the most prevalent spamming botnet in Q3, closely followed by the Necurs botnet. The latter was used to spread ransomware variants such as Locky. Mac malware rose by 7% in Q3, and macro malware increased by 8%.
Technologies such as PowerShell are still commonly used to install malware, along with Office macros. New PowerShell malware variants doubled in Q3, 2017, and while new JavaScript malware declined by 26% quarter over quarter, the level of new JavaScript malware is still substantially higher than the level seen in 2016.
Vulnerabilities in software and operating systems were also extensively exploited, even though patches to address those vulnerabilities were released promptly.
McAfee notes that employees and organizations are making it far too easy for attackers. Employees are responding to phishing emails, are visiting malicious links and are opening attachments and enabling the content. Employers are no better. Patches are released, yet they are not being applied promptly, opening the door to attackers. In many cases, patches have still not been applied several months after they have been released.
One of the most commonly exploited vulnerabilities in Q3, 2017 was CVE-2017-0199 which affected WordPad and Microsoft Office. An exploit for the vulnerability was made available through GitHub, making remote code execution attacks easy; provided employees could be convinced to open specially crafted files. Many employees fell for the scam emails.
The McAfee Q3 Malware Threat Report highlighted several continuing malware trends, including the increase in the use of fileless malware. PowerShell malware increased by 119% in Q3 alone.
Q3 saw a new Locky variant released – Lukitus. Lukitus was spread via spam email, with more than 23 million messages delivered in the first 24 hours since its release. That, combined with other new ransomware threats, have contributed to a 44% increase in ransomware samples in the past 12 months.
Q3 also saw the release of a new variant of the Trickbot Trojan, which incorporated the EternalBlue exploit that was also used in the WannaCry and NotPetya attacks.
While no industry is immune to attack, it is the healthcare and public sectors that are taking the brunt of the attacks, accounting for 40% of all reported security incidents in Q3. In the United States, healthcare was the most commonly attacked industry.
The extensive use of spam and phishing emails to spread malware highlights the importance of using an advanced spam filtering solution such as SpamTitan, especially considering how employees are still struggling to identify malicious emails. Blocking these threats and preventing malicious messages from being delivered will help organizations prevent costly data breaches.
The high level of infections that occurred as a result of exploited vulnerabilities also shows how important it is to apply patches promptly. McAfee notes that many of the exploited vulnerabilities in Q3 were patched as early as January. If patches are not applied promptly, they will be exploited by cybercriminals to install malware.
by titanadmin | Dec 19, 2017 | Industry News, Network Security, Spam Advice, Spam Software |
In this article we explore the cost of HIPAA noncompliance for healthcare organizations, including the financial penalties and data breach costs, and one of the most important technologies to deploy to prevent healthcare data breaches.
The Health Insurance Portability and Accountability Act (HIPAA)
In the United States, healthcare organizations that transmit health information electronically are required to comply with the Health Insurance Portability and Accountability Act (HIPAA). HIPAA was introduced in 1996 with the primary aim of improving healthcare coverage for employees between jobs, although it has since been expanded to include many privacy and security provisions following the introduction of the HIPAA Privacy and Security Rules.
These rules require HIPAA-covered entities – health plans, healthcare providers, healthcare clearinghouses and business associates – to implement a range of safeguards to ensure the confidentiality, integrity, and availability of protected health information (PHI). Those safeguards include protections for stored PHI and PHI in transit.
HIPAA is not technology specific, if that were the case, the legislation would need to be frequently updated to include new protections and the removal of outdated technologies that are discovered not to be as secure as was initially thought. Instead, HIPAA leaves the actual technologies to the discretion of each covered entity.
In order to determine what technologies are required to keep PHI secure, covered entities must first conduct a risk analysis: A comprehensive, organization-wide analysis of all risks to the confidentiality, integrity, and availability of PHI. All risks identified must be managed and reduced to an appropriate and acceptable level.
The risk analysis is one of the most common areas where healthcare organizations fall afoul of HIPAA Rules. Healthcare organizations have been discovered not to have included all systems, hardware and software in the risk analysis, or fail to conduct the analysis on the entire organization. Vulnerabilities are missed and gaps remain in security controls. Those gaps allow hackers to take advantage and gain access to computers, servers, and databases.
When vulnerabilities are exploited, and a data breach occurs, HIPAA-covered entities must report the security breach to the Department of Health and Human Services’ Office for Civil Rights (OCR): The main enforcer of HIPAA Rules. OCR investigates data breaches to determine whether they could realistically have been prevented and if HIPAA Rules have been violated.
What is the Cost of HIPAA Noncompliance?
When healthcare organizations are discovered not to have complied with HIPAA Rules, financial penalties are often issued. Fines of up to $1.5 million per violation category (per year that the violation has been allowed to persist) can be issued by OCR. The cost of HIPAA noncompliance can therefore be severe. Multi-million-dollar fines can, and are, issued.
The cost of HIPAA noncompliance is far more than any financial penalty issued by OCR, or state attorneys general, who are also permitted to issue fines for noncompliance. HIPAA requires covered entities to notify individuals impacted by a data breach. The breach notification costs can be considerable if the breach has impacted hundreds of thousands of patients. Each patient will need to be notified by mail. If Social Security numbers or other highly sensitive information is exposed, identity theft protection services should be offered to all breach victims.
Forensic investigations must be conducted to determine how access to data was gained, and to establish whether all malware and backdoors have been removed. Security must then be enhanced to prevent similar breaches from occurring in the future.
A data breach often sees multiple lawsuits filed by the victims, who seek damages for the exposure of their information. Data breaches have a major negative impact on brand image and increase patient churn rate. Patients often switch providers after their sensitive information is stolen.
On average, a data breach of less than 50,000 records costs $4.5 million to resolve according to the Ponemon Institute and has an average organizational cost of $7.35 million.
The 78.8 million-record breach experienced by Anthem Inc. in 2015 is expected to have cost the insurer upwards of $200 million. That figure does not include lost brand value and reputation damage, and neither a HIPAA fine from OCR.
A summary of the cost of HIPAA noncompliance, including recent fines issued by attorneys general and OCR has been detailed in the infographic below.
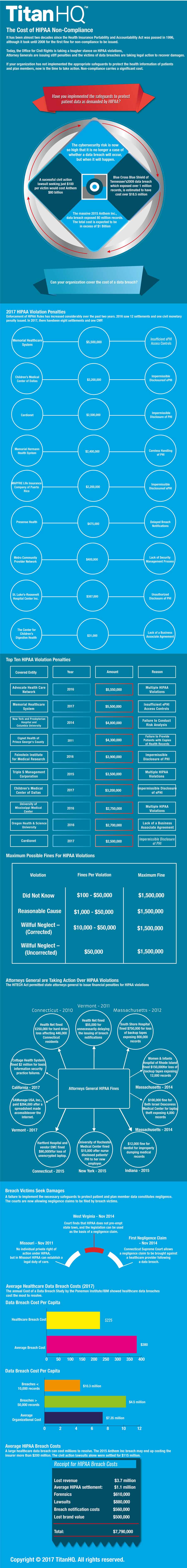
The Importance of Protecting Email Accounts
There are many ways that unauthorized individuals can gain access to protected health information – via remote desktop applications, by exploiting vulnerabilities that have not been patched, accessing databases that have been left exposed on the Internet, or when devices containing unencrypted PHI are stolen. However, the biggest single threat to healthcare data comes from phishing.
Research from PhishMe indicates more than 90% of data breaches start with a phishing email, and a recent HIMSS Analytics survey confirmed that phishing is the biggest threat, with email ranked as the most likely source of a healthcare data breach.
Protecting email accounts is therefore an essential part of HIPAA compliance. OCR has already fined healthcare organizations for data breaches that have resulted from phishing emails.
Healthcare organizations should implement a solution that blocks malicious emails and scans for malware and ransomware. In addition to technology, employees must also be trained how to identify malicious emails and taught to be more security aware.
How TitanHQ Can Help with HIPAA Compliance
TitanHQ developed SpamTitan to keep inboxes secure and prevent email spam, phishing messages, and malware from being delivered to inboxes. SpamTitan blocks more than 99.9% of spam email, and dual anti-virus engines ensure emails with malicious attachments are identified and quarantined. With SpamTitan, your organization’s email accounts will be protected – an essential part of HIPAA compliance.
WebTitan compliments SpamTitan and offers an additional layer of protection. WebTitan is a web filtering solution that allows you to carefully control the websites that your employees visit. WebTitan will prevent employees from visiting malicious websites via emailed hyperlinks, general web browsing, malvertising or redirects, protecting your organization from web-based attacks, drive by downloads of ransomware and malware, and exploit kit attacks.
For more information on TitanHQ’s cybersecurity solutions for healthcare, contact the TitanHQ team today.
by titanadmin | Nov 17, 2017 | Industry News, Internet Security, Network Security, Phishing & Email Spam, Spam News |
The Ponemon Institute has published the findings of a new report on endpoint security risk, which shows that ransomware attacks have occurred at most companies, the risk of fileless malware attacks has increased significantly, and successful cyberattacks are resulting in average losses of more than $5 million.
For the Barkly-sponsored endpoint security risk study, the Ponemon Institute surveyed 665 IT security professionals that were responsible for the management of their organization’s security risk.
7 out of ten respondents claimed endpoint security risk was significantly higher this year than in 2016, and one of the biggest threats was now fileless malware. Companies are still using traditional anti-virus and anti-malware solutions, although they are not effective at preventing fileless malware attacks.
Fileless malware is not detected by most anti-virus solutions since no files are written to the hard drive. Instead, fileless malware remains in the memory, oftentimes leveraging legitimate system tools to gain persistence and spread to other devices on the network.
These fileless malware attacks are occurring far more frequently, with respondents estimating a 20% rise in attacks in 2017. 29% of all cyberattacks in 2017 involved fileless malware, and the threat is expected to continue to increase, and will account for more than a third of all attacks in 2018.
The switch from file-based malware to fileless malware is understandable. The attacks are often successful. 54% of companies surveyed said they had experienced at least one cyberattack that resulted in data being compromised, and 77% of those attacks involved exploits or fileless malware. 42% of respondents said they had experienced a fileless malware attack that resulted in systems or data being compromised in 2017.
Fileless malware attacks are increasing, but so are ransomware attacks. Over half of companies that took part in the endpoint security risk study said they had experienced at least one ransomware attack in 2017, while four out of ten firms experienced multiple ransomware attacks. Even though most companies backup their files, 65% of respondents said they had paid a ransom to recover their data, with the average amount being $3,675. The primary method of ransomware delivery is email.
While the ransom payments may be relatively low, that represents only a small proportion of the costs of such attacks. For the endpoint security risk study, firms were asked to estimate the total cost of cyberattacks – On average, each successful attack on endpoints cost an average of $5,010,600 to resolve – $301 per employee.
Protect Against Malware Attacks by Blocking the Primary Delivery Vector
Email is the primary method for distributing malware. Implementing a spam filtering solution, preferably a gateway solution, can keep an organization protected from malicious emails and will prevent malicious messages from being delivered to end users, and is important for helping organizations manage endpoint security risk.
Many companies opt for an email gateway filtering appliance – an appliance located between the firewall and email server. These solutions are powerful, but they come at a cost since the appliance must be purchased. These appliance-based solutions also lack scalability.
If you want the power of an appliance, but want to keep costs to a minimum, consider a solution such as SpamTitan. SpamTitan offers the same power as a dedicated appliance, without the need to purchase any additional hardware. SpamTitan can be deployed as a virtual appliance on existing hardware, offering the same level of protection as an email gateway filtering appliance at a fraction of the cost.
Don’t Forget to Train Your Employees to be More Security Conscious
A recent InfoBlox survey on healthcare organizations in the United States and United Kingdom revealed that companies in this sector are realizing the benefits of training employees to be more security aware, although only 35% of firms currently provide training to employees.
No matter what email filtering solution you use, there will be times when spammers succeed, and messages are delivered. It is therefore important that staff are trained how to identify and respond to suspicious emails. If end users are not aware of the threats, and do not know how to recognize potential phishing emails, there is a higher chance of them engaging in risky behavior and compromising their device and the network.
by titanadmin | Nov 17, 2017 | Industry News, Network Security, Phishing & Email Spam, Spam Advice, Spam News |
A serious MS Office remote code execution vulnerability has been patched by Microsoft – One that would allow malware to be installed remotely with no user interaction required. The flaw has been present in MS Office for the past 17 years.
The flaw, which was discovered by researchers at Embedi, is being tracked as CVE-2017-11882. The vulnerability is in the Microsoft Equation Editor, a part of MS Office that is used for inserting and editing equations – OLE objects – in documents: Specifically, the vulnerability is in the executable file EQNEDT32.exe.
The memory corruption vulnerability allows remote code execution on a targeted computer, and would allow an attacker to take full control of the system, if used with Windows Kernel privilege exploits. The flaw can be exploited on all Windows operating systems, including unpatched systems with the Windows 10 Creators Update.
Microsoft addressed the vulnerability in its November round of security updates. Any unpatched system is vulnerable to attack, so it is strongly advisable to apply the patch promptly. While the vulnerability could potentially have been exploited at any point in the past 17 years, attacks exploiting this MS Office remote code execution vulnerability are much more likely now that a patch has been released.
The flaw does not require the use of macros, only for the victim to open a specially crafted malicious Office document. Malicious documents designed to exploit the vulnerability would likely arrive via spam email, highlighting the importance of implementing a spam filtering solution such as SpamTitan to block the threat.
End users who are fooled into opening a malicious document can prevent infection by closing the document without enabling macros. In this case, malware would be installed simply by opening the document.
Microsoft has rated the vulnerability as important, rather than critical, although researchers at Embedi say this flaw is “extremely dangerous.” Embedi has developed a proof of concept attack that allowed them to successfully exploit the vulnerability. The researchers said, “By inserting several OLEs that exploited the described vulnerability, it was possible to execute an arbitrary sequence of commands (e.g. to download an arbitrary file from the Internet and execute it),”
EQNEDT32.exe is run outside of the Microsoft Office environment, so it is therefore not subject to Office and many Windows 10 protections. In addition to applying the patch, security researchers at Embedi recommend disabling EQNEDT32.EXE in the registry, as even with the patch applied, the executable still has a number of other vulnerabilities. Disabling the executable will not impact users since this is a feature of Office that is never needed by most users.





