Spam News
Our spam news section provides up to date news on the latest threats that are likely to hit the inboxes of your employees. Cybercriminals are constantly changing tactics with new spam email campaigns, different social engineering techniques and new methods of installing malware and ransomware. By keeping up to date on the latest spam news, organizations can take timely action to mitigate risk.
In that regard, a spam filtering solution is essential. All it takes is for one employee to click on a malicious link or open an infected email attachment for an entire network to be compromised. A spam filter will check all incoming email messages and search for common spam signatures in addition to checking senders’ email accounts against blacklists of known spammers. Email attachments will be checked for virus signatures and hyperlinks compared to blacklists of known malicious domains.
Armed with the latest spam news, information security teams can send email alerts to their employees warning of pertinent threats that they need to be aware of.
This section also includes news on industry-specific attacks, in particular those that are being used to target the healthcare, education, financial services, legal and hospitality sectors.
by G Hunt |
January 31, 2025 |
Phishing & Email Spam, Security Awareness, Spam News
As the massive cyberattack on Change Healthcare demonstrated last year, the failure to implement multifactor authentication on accounts can be costly. In that attack, multifactor authentication was not implemented on a Citrix server, and stolen credentials allowed access that resulted in the theft of the personal and health information of 190 million individuals. The ransomware attack caused a prolonged outage and remediation and recovery cost Change Healthcare an estimated $2.9 billion last year.
The attack should serve as a warning for all companies that multifactor authentication is an essential cybersecurity measure – If passwords are compromised, access to accounts can be prevented. Unfortunately, multifactor authentication protection can be circumvented. Threat actors are increasingly using phishing kits capable of intercepting multifactor authentication codes in an adversary-in-the-middle attack. Phishing kits are packages offered to cybercriminals that cover all aspects of phishing. If purchased, phishing campaigns can be conducted with minimal effort as the phishing kit will generate copies of websites that impersonate well-known brands, the infrastructure for capturing credentials, and templates for phishing emails. After paying a fee, all that is required is to supply the email addresses for the campaign, which can be easily purchased on hacking forums.
Some of the more advanced phishing kits are capable of defeating multifactor authentication by harvesting Microsoft 365 and Gmail session cookies, which are used to circumvent MFA access controls during subsequent authentication. One of the latest phishing kits to be identified is has been dubbed Sneaky 2FA. The kit was first identified as being offered and operated on Telegram in October 2024 by researchers at the French cybersecurity firm Sekoia. The researchers identified almost 100 domains that host phishing pages created by the Sneaky 2FA phishing kit.
As with a standard phishing attack, phishing emails are sent to individuals to trick them into visiting a phishing page. One campaign using the Sneaky 2FA phishing kit uses payment receipt-related emails to trick the recipient into opening a PDF file attachment that has a QR code directing the user to a Sneaky 2FA page on a compromised website, usually a compromised WordPress site. These pages have a blurred background and a login prompt. Microsoft 365 credentials are required to access the blurred content. The phishing pages automatically add the user’s email address to the login prompt, so they are only required to enter their password. To evade detection, multiple measures are employed such as traffic filtering, Cloudfire Turnstile challenges, and CAPTCHA checks.
Many phishing kits use reverse proxies for handling requests; however, the Sneaky 2FA phishing server handles communications with Microsoft 365 API directly. If the checks are passed, JavaScript code is used to handle the authentication steps. When the password is entered, the user is directed to the next page, and the victim’s email address and password are sent to the phishing server via an HTTP Post. The server responds with the 2FA method for the victim’s account and the response is sent to the phishing server. The phishing kit allows session cookies to be harvested that provide account access, regardless of the 2FA method – Microsoft Authenticator, one-time password code, or SMS verification.
Phishing kits such as Sneaky FA make it easy for cybercriminals to conduct phishing attacks and defeat MFA; however, they are not effective at defeating phishing-resistant MFA such as FIDO2, WebAuthn, or biometric authentication. The problem is that these forms of MFA can be expensive and difficult to deploy at scale.
Businesses can greatly improve their defenses with advanced spam filter software with AI- and machine learning detection, email sandboxing, URL rewriting, QR code checks, greylisting, SPF, DKIM, and DMARC checks, and banners identifying emails from external sources. Effective email filtering will ensure that these malicious emails do not land in employee inboxes. TitanHQ offers two email security solutions – SpamTitan email security and the PhishTitan anti-phishing solution for M365. The engine that powers both solutions was recently rated in 1st place for protection in the Q4, 2024 tests by VirusBulletin, achieving a 100% malware and 100% phishing detection rate.
Regular security awareness training should also be provided to all members of the workforce to raise awareness of threats and to teach cybersecurity best practices. With the SafeTitan security awareness training platform it is easy to create and automate training courses and add in new training content when new threat actor tactics are identified. The platform also includes a phishing simulator for reinforcing training and identifying individuals in need of additional training.
For more information on improving your defenses against phishing and malware, give the TitanHQ team a call. Product demonstrations can be arranged on request and all TitanHQ solutions are available on a free trial.
by G Hunt |
October 29, 2023 |
Phishing & Email Spam, Spam News
Has AI surpassed humans at writing phishing emails? A team of researchers at IBM decided to put that to the test and the results are now in. Humans still have the edge, but AI is not far behind and will soon overtake humans.
There has been a lot of press coverage recently about the capabilities of AI and significant concern has been voiced about the threat AI-based systems pose. While there are legitimate concerns that AI systems could turn against humans, one of the most pressing immediate cybersecurity concerns is that cybercriminals could use generative AI tools to devastating effect in their cyberattacks.
Many security researchers have demonstrated that generative AI chatbots such as ChatGPT can write perfect phishing emails, free of spelling mistakes and grammatical errors, and can also create convincing lures to trick humans into opening a malicious email attachment or visiting a malicious website. ChatGPT and other generative AI tools can also be used to write malware code, and there have been demonstrations of AI tools being used to create functional polymorphic malware and ransomware code. One of the key advantages of AI tools such as ChatGPT is the speed at which phishing emails, social engineering lures, and malware code can be generated, which could greatly improve the efficiency and even the quality of a range of malicious campaigns.
Tools such as ChatGPT have guardrails in place to prevent them from being used for malicious purposes such as writing malware or phishing emails. If you ask ChatGPT to write ransomware code or a phishing email, it will refuse to do so as it violates OpenAI’s terms and conditions of use. Those controls can, however, be easily bypassed, plus there are generative AI tools that have been developed specifically for cybercriminal use, such as WormGPT and FraudGPT.
Are Cybercriminals Using AI in Their Campaigns?
Security researchers have shown that it is possible to use generative AI tools for offensive cybersecurity purposes, but are cybercriminals actually using these tools? While there is limited evidence on the extent to which these tools have been used, it is clear that they are being put to use. An August 2023 report by the U.S. cyber defense and threat intelligence firm Mandiant explored this and found threat actors are certainly interested in generative AI but use remains limited. The main area where these AI tools are being used is in information operations, specifically to efficiently scale their activity beyond their inherent means and to produce more realistic content.
Financially motivated threat actors have been using generative AI such as deepfake technology to increase the effectiveness of their social engineering, fraud, and extortion operations, including the use of face swap tools. The main focus currently is on social engineering, such as phishing attacks, for generating convincing lures for phishing emails and greatly reducing the time spent researching potential targets.
Are Generative AI Tools Better than Humans at Phishing?
An IBM X-Force team of social engineering experts recently went head-to-head with a generative AI chatbot to see which was better at creating phishing emails. The researchers would typically take around two days to construct a phishing campaign, with most of the time taken on researching targets to identify potential social engineering lures, such as topics for targeting specific industries, the persons to impersonate, and for creating convincing emails.
They developed 5 simple prompts to get a generative AI chatbot to do this, and the entire campaign was created in just 5 minutes, thus saving a cybercriminal around 2 days of their time. The good news is that the security researchers’ email performed better in terms of a higher click rate and a lower reporting rate, but the margins were very small. Humans still have the edge when it comes to emotional manipulation in social engineering, but AI is not very far behind and is likely to overtake humans at some point.
How to Combat AI-generated Phishing
Generative AI can save cybercriminals a great amount of time and the content generated is almost as good as human-generated content, and certainly good enough to fool many users. The best defense is to provide more extensive and regular security awareness training to employees to improve resilience to phishing attempts and to put cybersecurity solutions in place that incorporate AI and machine learning tools.
TitanHQ’s Email Security solution, SpamTitan, has AI and machine learning capabilities that are used to detect previously unseen phishing threats, such as those generated by AI tools. These capabilities also apply to email attachments, which are sent to an email sandbox for deep analysis of their behavior, allowing SpamTitan to detect and block zero-day malware threats. TitanHQ can also help with security awareness training. SafeTitan is an easy-to-use security awareness training and phishing simulation platform that has been shown to reduce susceptibility to phishing by up to 80%. Combined with multifactor authentication and endpoint detection tools, these solutions can help organizations improve their defenses against cyberattacks that leverage generative AI.
by G Hunt |
January 24, 2023 |
Phishing & Email Spam, Spam News
This month has seen an increase in phishing campaigns targeting professionals purporting to be messages from Human Resources advising them about salary increases, promotions, updates to policies and procedures, and other annual updates. The start of the year typically sees the HR department issue updates to employees, including notifications about changes to employee benefits, proposed pay rises, and annual updates to policies and procedures. It is therefore no surprise that cybercriminals are taking advantage of the increase in HR communications and have adopted lures related to these start-of-year messages. Several campaigns have been detected this month that have targeted employees and used HR-related lures.
The emails have realistic subject lines, appear to have been sent internally, and have lures that are likely to prompt a quick response. Messages about changes to employee benefits, pay rises, and promotions are likely to be opened by employees quickly without thinking, as are other notifications from the HR department such as updates to internal policies. Phishing simulation data shows that these types of emails have some of the highest click rates.
These emails include a combination of attachments and hyperlinks. One campaign claimed to include important information about a new benefits package and required employees to open an attached .shtml file. The email claimed employees needed to review and digitally sign the document to acknowledge receipt. In this case, opening the attached file would load a local copy of a phishing page, which generated a fake Microsoft 365 login prompt in the user’s browser. The user’s email address is populated as the username, and they are required to enter their password. The user is told that their password must be entered as they are accessing sensitive internal information.
These phishing emails may be sent from external email addresses and spoof the HR department, but internal email accounts compromised in previous phishing attacks are often used, adding to the realism of the campaign and making it harder for email security solutions to detect the emails as malicious. It is common for these campaigns to include malicious hyperlinks rather than attachments, where the user is directed to a phishing page that mimics the domain of the organization or a well-known, unrelated company. In one campaign, a healthcare organization was impersonated in an email purporting to provide details of updated medical benefits for employees. One campaign involved notifications about changes to the employee security awareness training program for the new year.
Phishing is one of the most common tactics used by cybercriminals to gain initial access to business networks. The campaigns are easy to conduct, requiring little effort by the attackers, and they are often effective. Simply opening a malicious attachment and enabling the content to view the document is all that is needed to install malware, and if a user can be convinced to disclose their Microsoft credentials, the attacker can gain access to all associated Microsoft applications, including Email, OneDrive, Teams, and SharePoint, giving them the foothold they need for conducting a more extensive attack and access to a considerable amount of sensitive company data.
Cybercriminals mimic the types of emails that employees are likely to receive at different times of the year. Over the next few weeks, it is likely that there will be an increase in phishing campaigns targeting tax professionals, and phishing campaigns targeting individuals that use tax-related lures, such as notifications about tax returns, tax rebates, and unpaid tax as tax season gets into full swing.
Businesses need to take steps to block these attacks. While antivirus software and a spam filter were once effective and could block the vast majority of email-based attacks, phishing is becoming increasingly sophisticated and the speed at which new, previously unseen malware variants can be created and released means these defenses are no longer as effective as they used to be.
To block more phishing attempts, businesses need to adopt a defense in-depth approach. In addition to antivirus/endpoint detection software and an advanced spam filter, they should consider adding a web filter to block access to the web-based component of phishing attacks and block malware downloads from the Internet. Multi-factor authentication should be implemented for accounts, although phishing kits are now being used that can bypass MFA. While any form of MFA is better than nothing, phishing-resistance MFA is ideal and should be implemented, which is based on FIDO standards and provides a much greater level of protection.
While it is the responsibility of organizations to block malicious emails and prevent them from reaching employees, it is inevitable that some will be delivered. It is therefore important to also provide security awareness training to employees to train them how to identify and avoid phishing attempts. Security awareness training combined with phishing simulations, such as those provided by TitanHQ through the SafeTitan platform, are proven to reduce susceptibility to phishing attacks.
by G Hunt |
October 31, 2022 |
Email Scams, Spam Advice, Spam News
Phishing attempts are often very convincing as the emails mimic trusted brands, include their logos and color schemes, and the message format is often copied from genuine company messages. The most commonly spoofed brands are well-known companies that have millions of customers, which increases the chances of the message landing in the inbox of a person who has, at least at some point in the past, used that company’s products or services.
Every quarter, Check Point releases its Brand Phishing Report, which highlights the latest phishing trends and the brands being impersonated most often. LinkedIn, Microsoft, Google, and Netflix are regulars in the top 10 List, with LinkedIn being the most commonly spoofed brand in phishing attacks in the first half of the year; however, the top spot has now gone to the German logistics and package delivery firm, DHL.
DHL accounted for 22% of all worldwide phishing attempts in Q3, 2022. DHL itself issued a warning to customers in July after the company became aware that it was being spoofed in a massive phishing campaign that was being conducted globally. It is probable that DHL will remain in the top spot in Q4 due to the increase in online purchases in the run-up to Christmas.
While there is some variation in the phishing emails impersonating DHL, one of the most common appears to have been sent by DHL Express and alerts the recipient about an undelivered package. The message warns that it will not be possible to attempt redelivery of the package unless delivery information is confirmed. The phishing emails include a link to a website to allow that information to be provided; however, the link directs the user to a website where they are required to log in and provide their name, username, password, and other sensitive information, such as payment details.
While email phishing is the most common form, DHL has been spoofed in SMS messages that achieve the same purpose. Of course, SMS messages are not subject to spam filtering controls and mobile devices are less likely to be protected by web filters, which can detect and block attempts to visit malicious websites. SMS phishing – termed smishing – has been growing in popularity in recent years.
Unsurprisingly, given the number of users, Microsoft achieved second place, accounting for 16% of phishing emails in the quarter. The phishing emails spoofing Microsoft are more varied due to the extensive product range, although OneDrive phishing emails were common. These emails claim to be collaboration requests and target businesses and ask the recipient to click on a button to view a shared document. Like many phishing emails, the messages warn the recipient that urgent action is required, as the document will be deleted in 48 hours. The user is directed to a malicious website where they are asked to enter credentials for their Microsoft account.
It is unclear why LinkedIn has fallen out of favor slightly, although it still achieved 3rd spot and accounted for 11% of phishing attempts in the quarter. The rest of the top ten consists of Google (6%), Netflix (5%), We Transfer (5%), Walmart (5%), WhatsApp (4%), HSBC (4%), and Instagram (3%).
Phishing is one of the main ways that cybercriminals gain access to business networks. The attacks are easy to conduct, low cost, and do not require extensive technical knowledge. Businesses can block the majority of these malicious messages by implementing an advanced spam filter such as SpamTitan Cloud. They should also consider adding an extra layer to their defenses – A web filter such as WebTitan Cloud.
Technical defenses such as these are vital for protecting against phishing attempts, but it is also important for businesses to ensure that they provide regular security awareness training to their employees to make them aware of the threat of phishing and to teach them how to identify phishing emails. In addition to training, phishing simulations should be conducted on the workforce. These have been proven to reduce susceptibility to phishing attempts, as they give employees practice at identifying phishing and any failures are turned into a training opportunity.
With the SafeTitan security awareness training and phishing simulation platform, training is automatically triggered in real-time in response to phishing simulation failures and other security errors, when the training is likely to have the greatest effect.
If you run a business and want to improve your defenses against phishing, give TitanHQ a call. TitanHQ products are available on a free trial to allow you to put them to the test before making a decision about a purchase. MSPs that have yet to add spam filtering, web filtering, and security awareness training to their service stacks should give the TitanHQ channel team a call to find out more about these opportunities to improve their clients’ defenses against phishing and other cyberattacks.
by G Hunt |
March 21, 2022 |
Network Security, Phishing & Email Spam, Spam News
2019 was a particularly bad year for ransomware attacks, and while there was a reduction in the use of ransomware in 2020, attacks increased sharply in 2021, with the education sector and government organizations the most attacked sectors, although no industry sector is immune to attacks.
There is growing concern about the increase in attacks on critical infrastructure organizations, which are an attractive target for ransomware gangs. According to the data from the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the National Security Agency (NSA), 14 of the 16 critical infrastructure sectors in the United States reported ransomware attacks in 2021, including the defense industrial base, emergency services, healthcare, food and agriculture, information technology, and government facilities. Cybersecurity agencies in the United Kingdom and Australia have also said critical infrastructure has been targeted.
Critical Infrastructure Organizations Warned About AvosLocker Ransomware Attacks
This week, a warning has been issued by the Federal Bureau of Investigation (FBI), the U.S. Department of the Treasury, and the U.S. Treasury Financial Crimes Enforcement Network (FinCEN) about ransomware attacks using AvosLocker ransomware.
AvosLocker was first identified as a threat in late June 2021 and despite being a relatively new threat, poses a significant risk. Attacks using the ransomware increased in the latter half of 2021, with spikes in attacks occurring in November and December. Variants of AvosLocker ransomware have now been developed to attack Linux as well as Windows systems.
As is now common, the attackers engage in double extortion and demand payment for the keys to decrypt files and to prevent the release of stolen data. The gang operates a data leak site where a sample of stolen data is uploaded and made accessible to the public. The gang says it then sells the stolen data to cybercriminals if payment is not made. AvosLocker is one of a handful of ransomware operations that also makes contact with victims by phone to encourage them to pay the ransom. The gang is known to issue threats of Distributed Denial of Service (DDoS) to further pressure victims into paying the ransom.
AvosLocker is a ransomware-as-a-service operation where affiliates are recruited to conduct attacks for a percentage of any ransom payments they generate. Consequently, the attack vectors used in attacks depend on the skillsets of the affiliates. Common vulnerabilities are known to be exploited to gain initial access to networks, including vulnerabilities associated with Proxy Shell and unpatched vulnerabilities in on-premises Microsoft Exchange Servers. However, over the past year, spam email campaigns have been a primary attack vector.
Email Filtering Vital for Defending Against Ransomware Attacks
Spam email is a common attack vector used by ransomware gangs. Spam email campaigns are effective and provide low-cost access to victim networks. Phishing and spam campaigns either use malicious attachments or embedded hyperlinks in emails, along with social engineering techniques to convince end users to open the attachments or click the links.
The primary defense against these attacks is email filters. Email filters scan all inbound emails and attachments and prevent malicious messages from being delivered to inboxes. Since cyber actors are constantly changing their lures, social engineering methods, and strategies to bypass email security solutions, it is vital to have an email security solution in place that can respond to changing tactics.
Email security solutions that use artificial intelligence and machine learning to identify and block threats outperform solutions that rely on antivirus engines and blacklists of known malicious IP addresses. SpamTitan incorporates artificial intelligence-based detection mechanisms in addition to blacklists, dual antivirus engines, and email sandboxing, which ensures a high detection rate for malicious emails, including zero day threats. SpamTitan also provides time-of-click protection against malicious hyperlinks in emails to ensure users are well protected against phishing, malware, ransomware, and other email threats.
Don’t Neglect Security Awareness Training for the Workforce
It is also important to provide security awareness training to all members of the workforce from the CEO down. The FBI and the U.S. Treasury Department recommended in the latest alert to “Focus on cyber security awareness and training,” and “Regularly provide users with training on information security principles and techniques as well as overall emerging cybersecurity risks and vulnerabilities (i.e., ransomware and phishing scams).” TitanHQ can help in this regard with SafeTitan – “The only behavior-driven security awareness solution that delivers security training in real-time.”
For more information on improving your defenses against ransomware and other cyber threats, give the TitanHQ team a call to inquire about email filtering, web filtering, and security awareness training for your workforce.
by G Hunt |
February 17, 2022 |
Email Scams, Phishing & Email Spam, Spam News
Business Email Compromise (BEC) is the leading cause of financial losses to cybercrime. The U.S. Federal Bureau of Investigation (FBI) Internet Crime Complaint Center (IC3) received 19,369 complaints about BEC scams in 2020, resulting in adjusted losses of $1.87 billion. While BEC crime ranked number 10 based on victim count, it topped the list in terms of the losses sustained by victims, with three times as much lost to the scams as the second-biggest loss to cybercrime – Confidence/romance fraud.
Business Email Compromise scams usually start with a phishing attack to gain access to email credentials. The attackers seek the credentials of the CEO, CFO, or another executive, and either target those individuals directly with spear phishing emails or compromise the email accounts of lower-level employees and use their email accounts to send phishing emails to the targeted individuals. Once the right credentials have been obtained, the executive’s email account is used to send messages to individuals responsible for wire transfers to trick them into making substantial wire transfers to attacker-controlled bank accounts. While these scams require planning and research, the time spent setting up the scams is well spent, as BEC attacks are often successful.
While BEC scams are usually conducted via email, BEC scammers are increasingly using virtual meeting platforms such as Microsoft Teams and Zoom in their scams. The scammers have taken advantage of the increase in remote working due to the pandemic and the popularity of virtual meeting platforms for communication and collaboration.
Once the scammers have access to the CEO’s email account, they identify their next target and send a request for a virtual meeting. When the target connects to the meeting, the scammer explains that they are having problems with their audio and video, so the meeting proceeds with the scammer on text chat. Oftentimes they will insert a picture of the CEO for added realism. The scammer then provides a reason for the out-of-band request, then asks the employee to make a wire transfer, either in the meeting or after the meeting via email.
The FBI has recently issued a warning to businesses about the increase in the use of virtual meetings for BEC scams, having observed an increase in the use of these platforms for BEC scams between 2019 and 2021. Scammers are also compromising employee email accounts and are inserting themselves into work meetings to gather information about the day-to-day processes at businesses. Since the scammers use genuine email accounts to connect, and audio/visual problems are relatively common, they are able to gather information and steal funds without being detected. The scammers also use compromised CEO email accounts to send emails to employees claiming they are stuck in a virtual meeting and unable to arrange an important wire transfer and ask an employee to initiate the transfer on their behalf.
There are several steps that businesses can take to improve their defenses against BEC attacks. Defending against these attacks should start with an advanced email security solution to block the phishing attacks that allow scammers to gain access to email accounts. SpamTitan has industry-leading detection of phishing URLs in emails and can prevent employees from visiting the web pages where credentials are harvested.
Security awareness training is important as some malicious emails bypass all spam filters. Employees need to be trained on how to identify scam emails. Security awareness training is concerned with creating a ‘human firewall’ to augment technical defenses and should make employees aware of BEC scams and how to identify scam emails from internal email accounts. TitanHQ has recently launched a new security awareness platform called SafeTitan to help businesses with training. SafeTitan is the only behavior-driven security awareness platform that provides real-time training to deal with threats targeting employees.
It is also recommended to implement policies and procedures that require secondary channels or two-factor authentication to verify requests for any changes to account information or atypical requests for bank transfers.
by G Hunt |
December 3, 2021 |
Industry News, Spam News, Spam Software
Phishing is the number one cybersecurity threat faced by businesses and attacks are becoming highly sophisticated. Phishing is used to obtain sensitive information such as login credentials and for distributing malware and ransomware. 91% of all cyberattacks start with phishing emails.
Many businesses now provide security awareness training for the workforce to raise awareness of the threat from phishing and to teach employees the skills that will allow them to identify and avoid phishing emails, but the click rates in phishing emails remain high. According to Security Affairs, 97% of users fail to identify phishing emails. The reason is phishing emails are now being created that are virtually indistinguishable from genuine communications from trusted sources and phishers are experts at social engineering.
The best defense against phishing is a spam filter – A technical solution that scans all inbound (and outbound) emails and performs a wide range of checks and analyses, all of which must be passed in order for an email to be sent to an inbox. Spam filters scan the message headers and message body for signs of spam and phishing, and attachments are scanned using anti-virus engines that identify known malware variants. Hyperlinks in messages are also checked; however, phishers are constantly developing new techniques for hiding malicious URLs from email security solutions.
TitanHQ’s spam and phishing protection solution – SpamTitan – already provides excellent protection from spam and phishing emails; however, a new product – SpamTitan Plus – has now been launched that significantly improves detection rates. SpamTitan Plus provides advanced phishing protection with better coverage, better phishing link detections, faster detection speed, and also has the lowest false positive rate of any product.
“The overwhelming feedback from our users and customer base has been that phishing attacks are becoming more advanced, proficient, and dangerous. Phishing is the number one problem to solve in the email security community,” said TitanHQ CEO Ronan Kavanagh. “With that in mind, we allocated resources and investment to develop a solution with new, cutting-edge, robust, fast phishing threat intelligence driven by a team of security specialists. We’re very happy with the result – SpamTitan Plus”.
SpamTitan Plus includes leading-edge, AI-driven anti-phishing prevention and incorporates the newest “zero-day” threat intelligence, providing better protection than current market-leading email anti-spam service providers at neutralizing malicious links in emails.
All URLs in emails are inspected to determine if they are malicious and are rewritten, and a time-of-click analysis is performed. This is important as the URLs in phishing emails may not be malicious at the time of delivery and may be weaponized with malware after they have passed email security checks. The time-of-click protection involves several dynamic checks, including a page evaluation to identify spoofed websites and login pages and the following of any redirects. If a user clicks on a malicious URL, instead of being directed to the website they will be sent to a local block page that provides further information.
Independent tests of SpamTitan Plus show:
- 100% coverage of phishing threats from the current market-leading anti-phishing feeds
- 5X increase in unique phishing URL threat detection than the current market leaders
- 6X faster and more rapid phishing detection than the current market leaders
10 million new, previously undiscovered phishing URLs are detected every single day and there is only a 5-minute delay from the initial detection of a malicious URL to protect an end user’s mailbox.
SpamTitan is relied upon by 12,000 customers and 3,000 Managed Service Providers for protecting against spam and phishing emails. They can now choose to significantly improve protection with SpamTitan Plus. For more information about SpamTitan Plus, Give the TitanHQ team a call today.
by G Hunt |
November 16, 2021 |
Phishing & Email Spam, Spam News
At the start of 2021, a Europol and Eurojust-led operation involving law enforcement agencies in 8 countries successfully took down the infamous Emotet botnet. The botnet consisted of an estimated 1.6 million devices worldwide that had been infected with the Emotet Trojan.
The Emotet Trojan first appeared in 2014 and was originally a banking trojan, although it evolved into a malware downloader that was rented out to cybercrime gangs under the malware-as-a-service model. The botnet was used to give those threat actors a foothold in victims’ environments and allowed them to install malware such as IcedID, QakBot, and TrickBot. Those malware variants were then used to deliver ransomware such as Conti and Ryuk.
Emotet posed a massive threat to businesses worldwide prior to its takedown. In addition to being a malware distribution tool, the botnet was used to launch Distributed Denial of Service (DDoS) attacks and large-scale spamming campaigns against high-profile targets around the world.
The Emotet botnet was controlled by a network of hundreds of servers worldwide. The takedown, which occurred on January 27, 2021, saw its infrastructure taken over by law enforcement. On April 25, 2021, law enforcement in Germany launched a cleanup operation that added a module that removed the Emotet Trojan from victims’ systems. 2 individuals were arrested who were suspected of involvement in maintaining the botnet, and in the weeks and months that followed no Emotet activity was detected. However, that has now changed.
The Emotet Botnet is Back
Law enforcement took control of the command-and-control infrastructure of Emotet and removed the Emotet Trojan from all infected devices, and while that was sufficient to kill the botnet, it was not enough to prevent its return. Researchers at GData, Advanced Intel, and Cryptolaemus have all discovered instances where the TrickBot Trojan has delivered an Emotet loader.
The Emotet botnet operators have previously worked with the threat actors behind the Trickbot Trojan, using their botnet to grow the TrickBot botnet. That process is now happening in reverse. A new version of the loader and Emotet Trojan have been created and it appears that the Emotet botnet is being reconstructed from scratch.
At this stage, there are relatively few devices infected with Emotet but that is not likely to remain the case for long. Around 246 devices are known to have had the Emotet Trojan installed, and they are being used as its command-and-control infrastructure at present.
Emotet was known for conducting malspam campaigns to grow the botnet, and spamming campaigns have already been detected using several different lures and a variety of attachments. Spam emails spreading Emotet have used Word files and Excel spreadsheets with malicious macros, and to prevent analysis by email security solutions, some emails have used password-protected zip files. Some of the lures detected by security researchers in the first campaigns include notifications about canceled dental insurance, Cyber Monday and Black Friday sales, notifications about canceled meetings, and requests for political party donations.
How to Protect Against Infection with Emotet
Protecting against Emotet involves implementing measures that also protect against TrickBot infections. Since both Emotet and TrickBot are extensively delivered via malspam emails, implementing an advanced email security solution is a good place to start.
One of the most effective tactics used by the Emotet gang was hijacking message threads. This involves sending replies to previous message conversations and adding a malicious hyperlink or infected email attachment. Since the messages were sent from email accounts known to the recipient, links were often clicked, and attachments opened.
Security awareness training often teaches employees to be suspicious of unsolicited messages from unknown individuals. It is important to make employees aware that malicious emails may also come from known individuals and to warn employees that hijacked message threads are used to deliver malware. Security awareness training can be effective, but it is nowhere near as effective as technical solutions that block malicious messages.
Security can be improved by choosing an email security solution with outbound email scanning. This feature will scan outgoing messages to detect compromised email accounts, allowing security teams to take prompt action to isolate infected devices. You should also ensure that your email security solution includes sandboxing in addition to antivirus engines, as the latter can only detect known malware variants. Attachments that pass standard AV scans are sent to an email sandbox where they are subjected to in-depth analysis to identify malicious actions.
These features and many more are included in SpamTitan from TitanHQ. SpamTitan is effective at blocking the full range of email-based threats and is easy to implement and use. If you want to improve your defenses against dangerous email threats such as TrickBot, IcedID, QakBot, and Emotet without breaking the bank, give the TitanHQ team a call for more information about SpamTitan.
SpamTitan is available on a free trial and product demonstrations can be arranged on request.
by G Hunt |
October 27, 2021 |
Email Scams, Phishing & Email Spam, Spam News
A new malware variant dubbed Squirrelwaffle has been identified which is being distributed via spam emails. Squirrelwaffle was first identified in September 2021, with the number of spam emails distributing the malware increasing throughout the month and peaking at the end of September.
The takedown of the Emotet botnet in January 2021 left a gap in the malware-as-a-service market, and several new malware variants have since emerged to fill that gap. Emotet was a banking Trojan that was used to distribute other malware variants to Emotet-infected machines, with Squirrelwaffle having similar capabilities. Squirrelwaffle allows the threat group to gain a foothold in compromised devices and networks, which allows other malware variants to be delivered.
Investigations of the malspam campaign have revealed it is currently being used to distribute Qakbot and Cobalt Strike, although the malware could be used to download any malware variant. The spam emails that deliver Squirrelwaffle include a hyperlink to a malicious website which is used to deliver a .zip file that contains either a .doc or .xls file. The Office files have a malicious script that will deliver the Squirrelwaffle payload.
The Word documents use the DocuSign signing platform to lure users to activate macros, claiming the document was created using a previous version of Microsoft Office Word which requires the user to “enable editing” then click “enable content” to view the contents of the file. Doing so will execute code that will deliver and execute a Visual Basic script, which retrieves the Squirrelwaffle payload from one of 5 hardcoded URLs. Squirrelwaffle is delivered as a DLL which is then executed when downloaded and will silently download Qakbot or Cobalt Strike, which both provide persistent access to compromised devices.
As was the case with the Emotet Trojan, Squirrelwaffle can hijack message threads and send malspam emails from infected devices. Since replies to genuine messages are sent from a legitimate email account, a response to the message is more likely. This tactic proved to be highly effective at distributing the Emotet Trojan. The campaign is mostly conducted in English, although security researchers have identified emails in other languages including French, German, Dutch, and Polish.
The similarities with Emotet could indicate some individuals involved in that operation are attempting a return after the law enforcement takedown, although it could simply be an attempt by unrelated threat actors to fill the gap left by Emotet. Currently, the malware is not being distributed in anywhere near the volume of Emotet but it is still early days. Squirrelwaffle may turn out to be the malware distribution vehicle of choice in the weeks and months to come.
To counter the threat, it is vital for email security measures to be implemented to block the malspam at source and ensure the malicious messages are not delivered to inboxes. Since message threads are hijacked, a spam filtering solution that also scans outbound emails– SpamTitan for example – should be used. Outbound scanning will help to identify compromised devices and prevent attacks on other individuals in the organization and address book contacts. SpamTitan also incorporates sandboxing, which works in conjunction with antivirus engines. Suspicious attachments that bypass the AV engines are sent to the email sandbox for in-depth analysis.
As part of a defense-in-depth strategy, other measures should also be deployed. A web filter is a useful tool for blocking C2 communications, endpoint security solutions will help to protect against Squirrelwaffle downloads, and regular security awareness training for the workforce is recommended to teach cybersecurity best practices and train employees how to identify malicious emails. Employees should be told to never click links or open attachments in unsolicited emails or messages and to be wary of messages from unknown accounts. It is also important to explain that some malware variants can hijack message threads, so malicious emails may come from colleagues and other address book contacts.
by G Hunt |
October 20, 2021 |
Email Scams, Phishing & Email Spam, Spam News
The threat group known as TA505 (aka Hive0065) is known for conducting large-scale phishing campaigns but has not been active since 2020. Now phishing campaigns have been detected that indicate the threat group is conducting attacks once again, with the first mass-phishing campaigns by the group detected in September 2021.
The initial campaigns were small and consisted of a few thousand phishing emails, but as the month progressed larger and larger campaigns were conducted, with phishing campaigns conducted by the group now consisting of tens of thousands of messages. The geographic range has also been increased beyond North American where the gang was initially concentrating its attacks.
Social engineering techniques are used to convince victims to open email attachments or visit links and view shared files, with a variety of lures used by the gang in its phishing attacks. Emails intercepted from the latest campaigns claim to provide insurance claims paperwork, situation reports, media release requests, health claims, and legal requests. Many of the campaigns so far have targeted employees in financial services.
One of the hallmarks of the group is using Excel file attachments in emails that contain malicious macros which deliver a Remote Access Trojan (RAT), the downloading and execution of which gives the group control over victims’ devices. The group is also known to use HTML files that link to malicious websites where the malicious Excel files are downloaded.
While the attacks often start with a file attachment, later in the attack process a Google feedproxy URL is used with a SharePoint and OneDrive lure that appears to be a file share request, which delivers the weaponized Excel file.
The initial infection stage involves the downloading of a Microsoft installer package, which delivers either a KiXtart or REBOL malware loader, which pulls a different MSI package from the C2 server, which then installs and executes the malware. TA505 is known to use the FlawedGrace RAT, which first appeared in 2017, and the latest campaign delivers a new variant of this malware using a malware loader dubbed MirrorBlast. According to an analysis of MirrorBlast by Morphisec labs, the malware will only run in 32-bit versions of Microsoft Office as there are compatibility issues with ActiveX objects.
Macros are disabled by default in Microsoft Excel as a security measure, so social engineering techniques are used in the attacks to convince victims to enable macros. Macros are more commonly used in Excel files than Word files, and end users may not be as suspicious of Excel macros as Word macros.
Email security solutions are capable of detecting files containing malicious Excel macros, especially email security solutions with sandboxing. In an attempt to bypass those measures and ensure the emails are delivered, TA505 uses lightweight, legacy Excel 4.0 XLM macros rather than the newer VBA macros, which has seen many of the messages bypass email security gateways.SpamTitan incorporates a next-gen Bitdefender-powered email sandbox where suspicious attachments are sent for in-depth analysis, which allows Office files with malicious macros to be detected and blocked.
TA505 is a highly creative threat group that regularly changes its attack techniques to achieve its goals, with the gang known to have conducted campaigns to deliver the Dridex banking Trojan, Locky and Jaff ransomware, and the Trick banking Trojan.
The group is known for conducting high-volume phishing campaigns that have targeted a range of different industry sectors and geographical areas.
TA505’s tactics, techniques, and procedures are expected to continue to evolve so it is vital for organizations to ensure email security defenses are implemented to block the emails. Security awareness training should also be provided to the workforce and employees should be made aware of the latest tricks and tactics used by the gang, including raising awareness of the use of Excel files with macros in phishing emails.
by G Hunt |
September 15, 2021 |
Industry News, Spam News, Spam Software
TitanHQ has released a new version of its award-winning email security solution that includes a new security feature – Geo-blocking email filtering, as well as several other security updates and fixes to improve usability.
Geo-blocking is a feature that has been requested by customers and has now been included in the product at no additional cost to users. Geo-blocking, as the name suggests, allows SpamTitan users to block or allow emails originating from certain geographical locations, based on either IP address or country. This feature allows businesses to add an extra layer of protection to block geographic threat vectors and stop malware, ransomware, and phishing emails from reaching inboxes.
The new feature allows businesses and organizations to block emails coming from any country. This extra control is important, as most malware-containing emails come from a handful of overseas countries – Countries that most small- to medium-sized businesses do not normally work with. Blocking emails from those countries eliminates threats, without negatively impacting the business.
Activating the geo-blocking feature could not be any easier. SpamTitan users can click to restrict emails from any country in the SpamTitan Country IP Database and all emails coming from those countries will be blocked. There will naturally be instances where things are not so cut and dry, but that is not a problem. Geo-blocking can be activated for a specific country, and IP addresses, domains, or email addresses of trusted senders within those countries can simply be whitelisted to ensure their messages are delivered.
“Geoblocking has been a much-requested feature and as always we listen to our customers and provide what they need to implement the very best email security they can,” said TitanHQ CEO Ronan Kavanagh. “After experiencing 30% growth in 2021, TitanHQ expects these product enhancements and new features to make 2021 another record-breaking year.”
Several other security enhancements have been made to further improve the already excellent threat detection and blocking mechanisms within SpamTitan. SpamTitan 7.11 includes an upgraded email sandboxing feature to provide even greater protection against malware, ransomware, phishing, spear-phishing, Advanced Persistent Threats, and malicious URLs embedded in emails. These enhancements also provide more detailed information about new threats to help SpamTitan users mitigate risk.
As always with a new release, recently reported bugs have been fixed, and SpamTitan has been further improved with enhanced email rendering in Mail Viewer. Users also now have the ability to remove quarantine report token expiry and improve domain verification, to name but a few of the enhancements.
SpamTitan is delivered either as a 100% cloud-based solution or as an anti-spam gateway, which is run as a virtual appliance on existing hardware. Existing SpamTitan Cloud customers need to do nothing to upgrade to the new version of the solution, released on September 14, 2021. SpamTitan Cloud is automatically updated to the latest version.
Users of SpamTitan Gateway will need to manually upgrade to the latest version via System Setup > System Updates.
by G Hunt |
February 25, 2021 |
Phishing & Email Spam, Spam News
A new phishing scam has been detected targeting UK residents that spoofs the National Health Service (NHS) and offers recipients the opportunity to register to receive a COVID-19 vaccination. The NHS COVID-19 vaccine scam is one of several to be intercepted in recent weeks that offers the chance to get a vaccine, when in reality it will involve disclosing sensitive information.
Since the SARS-CoV-2 virus started spreading beyond the borders of China, scammers have been conducting a wide range of COVID-19 phishing scams. Now that the vaccine rollout is progressing in the UK and globally, using the promise of an early vaccine as a lure was to be expected.
In the latest campaign, the sender’s address has been spoofed to make it appear than the messages have been sent by the NHS, and NHS branding is used in the message body. Recipients are instructed that they have been selected to receive the vaccine based on their family and medical history.
The lure is plausible, as in the UK the most at-risk groups have mostly been vaccinated, and the NHS is now moving into priority group 6, which is all individuals aged 16 to 65 with an underlying medical condition. The NHS has also asked people to be patient and to wait until they are contacted about the vaccine to arrange an appointment, which may be via email.
The NHS COVID-19 vaccine scam emails require the recipient to click a link that directs them to a website where they are instructed to provide some information to confirm their identity. In this case, the aim of the scam is not to obtain credentials, but personal information including name, address, date of birth, and credit card details.
Phishing has become the attack vector of choice for many cybercriminal operations during the pandemic. One study indicates an increase of 667% in phishing as an attack vector, showing the extent to which cybercriminals have changed their attack tactics during the pandemic. One study by Centrify shows the number of phishing attacks had increased by 73% between March 2020 and September 2020.
Research published by the ransomware response firm Coveware shows that the volume of ransomware attacks using phishing as the infection vector increased sharpy in the final quarter of 2020, overtaking all other methods of attacks to become the main method of gaining access to business networks.
Phishing attacks are expected to continue to increase in 2021 due to the ease at which they can be conducted and the effectiveness of the campaigns. Attacks are also becoming more sophisticated and harder for employees to identify.
Spear phishing attacks that target certain companies and individuals are becoming much more prevalent. These campaigns involve prior research, and the messages are tailored to maximize the chance of a response.
With phishing so prevalent, it is vital for businesses to ensure they are sufficiently protected and have an email security solution installed that is capable to blocking these threats.
Dual AV engines and email sandboxing are capable of blocking known and zero-day malware and ransomware threats, while machine learning technology and multiple threat intelligence feeds provides protection against current and emerging phishing threats.
SpamTitan significantly improves protection for Microsoft Office 365 accounts, the credentials to which are highly sought after by phishers and offers businesses excellent protection from all email-based attacks at a very affordable price.
If you want to protect your inboxes and block more malicious emails, contact TitanHQ for more information about SpamTitan. The multi-award-winning antispam solution is also available on a free trial for you to see for yourself how effective it is and how easy it is to use.
by G Hunt |
February 23, 2021 |
Phishing & Email Spam, Spam Advice, Spam News
Tax season has begun and so have the annual scams targeting tax professionals. Each year in the run up to the tax filing deadline, cybercriminals conduct scams in order to obtain electronic filing identification numbers (EFINs).
In the United States, the Internal Revenue Service (IRS) issues EFINS to tax professionals and individuals to allow them to file tax returns electronically. If cybercriminals obtain these EFINs they can file fraudulent tax returns in victims’ names to obtain tax rebates. Obtaining an e-file number of a tax professional will allow tax returns to be filed for many individuals, so these scams can be very lucrative.
These scams usually start with a phishing email using a lure to get the recipient to visit a malicious website where they are asked to provide information or upload documents that contain sensitive information. Alternatively, recipients are told to download files which silently install a malware downloader which ultimately gives the attackers full control of the victim’s computer.
Commonly, the spam emails spoof the IRS and instruct tax professionals to provide information or documents in order to prevent the suspension of their account. At such as busy time of year, suspension of an account is best avoided. Faced with this threat, tax professionals may provide the requested information.
One of the phishing emails recently intercepted spoofed the IRS by using the sender name “IRS Tax E-Filing,” with the subject line “Verifying your EFIN before e-filing.” The emails looked convincing and required “authorized e-file originators” to reverify prior to filing returns through the IRS system. The emails claimed the IRS had started using this new security measure to prevent unauthorized and fraudulent activities. The scammers requested a PDF file/scan of the EFIN acceptance letter and both sides of the individual’s driver’s license. Similar scams have been conducted that require tax preparers’ ID numbers and e-services usernames and passwords to be provided.
This year, in addition to the usual phishing emails spoofing the IRS, campaigns have been detected where the attackers claim to be potential clients looking for tax preparers ahead of the filing deadline. Attachments are provided that would typically be needed by tax preparers, but they are laced with malicious scripts that install keylogging malware that records and exfiltrates keystrokes, with are likely to include usernames and passwords.
Tax preparers that fall victim to these scams can suffer catastrophic damage to their reputations, so it is important to exercise caution when opening any emails and to stop and think carefully about any request to provide sensitive information or download files.
One of the easiest ways to protect against these scams is to implement an advanced spam filtering solution that can identify and block these malicious messages. SpamTitan is a powerful email security solution that identifies and blocks malware and documents containing malicious scripts with dual antivirus engines, sandboxing, and machine learning techniques. In addition to blocking malware threats, SpamTitan is highly effective at blocking phishing emails containing malicious links.
The award-winning spam filter is quick and easy to implement and maintain, requiring no technical knowledge. You can be up and running in minutes and protecting your inbox from phishing and malware attacks, which will allow you to concentrate on your business at this busy time of year and avoid costly cyberattacks.
For more information about SpamTitan, to book a product demonstration or to register for a free trail, give the SpamTitan team a call today.
by G Hunt |
February 22, 2021 |
Phishing & Email Spam, Spam News
Phishers regularly changes their tactics, techniques and procedures and create more convincing scams to trick employees into disclosing sensitive information or installing malware on their computers. One novel tactic that was first observed in the fall of 2020 involved the use of malformed URL prefixes. Over the following months, the number of emails sent with these atypical URL prefixes grew, and according to GreatHorn researchers, the volume of these messages increased by almost 6,000% in the first month of the year.
URLs start with either HTTP:// or HTTPS://, which are the standard URL protocols. While end users may check to see if the URL starts with HTTP or HTTPS to determine whether the connection to the website is encrypted, they may not notice or be overly concerned about what comes after the colon. That is also true of certain security solutions and browsers, which also do not check that part of the URL.
The new tactic sees one of the forward slashes swapped with a backslash, so HTTPS:// becomes HTTP:/ and it is enough of a change to see phishing emails delivered to inboxes. This tactic has been combined with another tactic that reduces the chance of the link being identified as malicious. The URL linked in the emails directs the user to a web page that includes a reCAPTCHA security feature. This feature will be known to most internet users, as it is used by a great deal of websites and search engines to distinguish between real users and robots.
The challenge must be passed for a connection to the website to me made. Having this security feature helps to convince the visitor that they are arriving on a legitimate site, but it also stops security solutions from assessing the content of the site. If the user passes the reCAPTCHA challenge, they are then redirected to a different URL that hosts the phishing form. That webpage very closely resembles the login prompt of Office 365 or Google Workspace, with this campaign mostly targeting Office 365 credentials.
Since this new tactic is now proving popular it is worthwhile incorporating this into your security awareness training sessions to make employees aware of the need to check the URL prefix, and also add a rule in SpamTitan to block these malformed URLs.
by G Hunt |
February 18, 2021 |
Email Scams, Phishing & Email Spam, Spam News
A new Adidas phishing scam has been detected that offers free shoes and money. The messages claim that Adidas is celebrating its 93rd anniversary and is giving 3000 lucky customers a free pair of Adidas sneakers and a free $50 a month subscription.
“Adidas is giving away 3000 Free Pair of Shoes to celebrate its 93rd anniversary. Get your free shoes at <link>”
The very same scam was run in 2019 claiming to celebrate 69th anniversary and on that occasion was giving 2,500 lucky customers a free pair of Adidas sneakers and a free $50 a month subscription. The scammer saw success previously and have clearly decided it's worth trying again.
The Scam Adidas Email
There is also an email version of the scam. The fake Adidas email claims the recipient has won a large sum of money and all they need to do to claim the cash is send their personal details via email.
Scam emails are now a very effective form of cyber attack. Most successful hacking attacks today begin with a phishing email. Scam emails containing ransomware or BEC are a challenge for corporate security.
A successful breach can cost an organization millions but defending against this kind of attack requires powerful anti-spam and malware technology. To defend against this kind of phishing attack you need a cutting edge email security solution to stop scam emails, a security aware workforce to identify a scam email and spot a spoof email, and powerful web protection that blocks user from accessing dangerous websites
WhatsApp phishing scam
The WhatsApp phishing scam is targeting users on mobile devices in specific locations. If the user clicks the link in the message and is determined not to be using a mobile device, they will be directed to a webpage that displays a 404 error. The scam will also only run if the user is in the United States, Pakistan, India, Norway, Sweden, Nigeria, Kenya, Macau, Belgium or the Netherlands.
Provided the user is on a mobile device and located in one of the targeted countries, a series of four questions will be asked. The responses to the questions are irrelevant as all users will be offered a “free” pair of sneakers after answering the four questions.
In order to be able to claim the prize, users must share the offer with their contacts on WhatsApp. Regardless of whether the user does this, they will be directed to another webpage where they are asked further questions and are finally offered a “free” pair of sneakers worth $199.
There is another catch. In order to claim their free sneakers, the user must pay $1. The user is advised that they will also be charged $49.99 a month for the subscription at the end of the month if they do not cancel. The user is told they can cancel at any point.
On the payment screen the user is told that the payment will be processed by organizejobs.net. Proceeding with the payment will see the user charged $1, followed by the subscription cost of $49.99 in 7 days.
The campaign is being run on WhatsApp, although similar scams have been conducted via email and SMS messages. Several variations along the same theme have also been identified spoofing different shoe manufacturers.
The link supplied in the WhatsApp phishing message appears to be genuine, using the official domain for the country in which the user is located. While the domain looks correct, this is an example of a homoglyph attack. Instead of the domain adidas.de, the i is replaced with a vertical line – a homoglyph attack.
These types of scams are commonplace. Homoglyph scams take advantage of the ability to use non-ASCII characters in domain names. Similar scams use a technique called typosquatting – where domains closely matching real brand names are registered: Incorrect spellings for instance, such as “Addidas” instead of Adidas, or with an i replaced with a 1 or an L.
In this case, the attackers appear to be earning a commission for getting users to sign up, although disclosing debit and credit card details could easily see the information used to run up huge bills or drain bank accounts.
There are various warning signs indicating this is an Adidas phishing scam. Close scrutiny of the domain will reveal it is incorrect. The need to share the message to contacts is atypical, being notified of a charge after being told the shoes are free, the failure to ask the user to choose a pair of shoes or even select their size, and an odd domain name is used to process payment. However, even with these tell-tale signs that the offer is not genuine, this adidas phishing scam is likely to fool many people.
Be warned. If you receive any unsolicited WhatsApp message offering you free goods, best to assume it is a phishing scam.
To find out more about some of the key protections you can put in place to improve your resilience against email scams and phishing attacks, contact the SpamTitan team today.
by G Hunt |
January 28, 2021 |
Phishing & Email Spam, Spam Advice, Spam News
DMARC email authentication is an important element of phishing defenses, but what is DMARC email authentication, what does it do, and how does it protect against email impersonation attacks?
There is some confusion about what DMARC email authentication is and what it can do. In this post we explain in clear English what DMARC means and why it should be part of your anti-phishing defenses.
What is DMARC
DMARC is short for Domain-based Message Authentication, Reporting, and Conformance. Its purpose is to make it harder for threat actors to conduct phishing attacks that spoof brands and get those messages delivered to inboxes. DMARC is a critical component of email cybersecurity that reduces an attacker’s ability to get email threat to an end user’s inbox.
With DMARC, organizations can create a record of who is authorized to send emails from their domain. This helps to prevent misuse of a company brand in phishing campaigns.
If DMARC is implemented on email, a business can have all incoming emails checked against DMARC records and any email that fails the check can be subjected to certain actions.
The message can be delivered as normal with a warning and the email will be included in a report of emails that failed the check. The message could automatically be sent to quarantine for manual approval before delivery is made. Alternatively, the message could be rejected or subjected to a custom policy. An organization can select the best policy to adopt based on their level of risk tolerance.
DMARC will not stop all phishing emails from being delivered, but it is an important measure to implement to stop email spoofing and reduce the number of phishing emails that reach inboxes. DMARC is just one of several rules that are used to determine whether emails are genuine and should be delivered or if the messages have been sent from an unauthorized user.
Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and DNS records are also used to determine whether the email server being used is authorized to send emails for the organization.
Find out more about improving your email security defenses. Sign up for a free SpamTitan demo today.
Book Free DemoWhat is Sender Policy Framework (SPF)
The Sender Policy Framework (SPF) is an email-authentication technique used to restrict who can send emails from your domain. It allows your mail server determine when a message comes from the domain that it uses. SPF has three major elements: a policy framework, an authentication method and specialized headers to convey the information.
An email message contains two sender addresses:
- The From:header, displaying the name and email address of the sender
- The Envelope From:or Return-Path email address.
Both types of sender addresses can be easily spoofed.
SPF uses a DNS record to verify the Envelope From: only. This means that if a spammer spoofs the Envelope From: address using a domain where SPF is enabled, the mail will be caught by the receiving server. If the spammer spoofs the From: header, SPF will not catch this. The SPF record indicates which email servers are authorized to send mail on behalf of a domain. This would be the organization itself and any third parties, such as marketing companies. The SPF record is a DNS TXT record that includes IP addresses and hostnames that are allowed to send emails from a particular domain. The SPF record is the first thing checked by DMARC rules.
Together with the DMARC related information, this gives the receiver (or receiving systems) information on how trustworthy the origin of an email is. SPF is, just like DMARC, an email authentication technique that uses DNS (Domain Name Service). This gives you, as an email sender, the ability to specify which email servers are permitted to send email on behalf of your domain.
DKIM
DKIM is more advanced and uses a TXT record and asymmetric public-private key encryption. With DMARC enabled, the signature is encrypted with the public key and the key is published on DNS servers. The domain’s private key is then used at the recipient’s email server for verification.
If DKIM is enabled, the public key-encrypted signature is compared with the message that is decrypted using a newly generated key to confirm that the message has not been altered. DKIM also confirms that the sender is from the listed domain and that the sender has not been spoofed.
DMARC offers a much greater level of protection than SPF and is more dependable, so both should be implemented. Both SPF and DMARC are incorporated into SpamTitan to better protect users from email spoofing attacks. Enabling SPF, DKIM and DMARC will help greatly reduce the amount of spoof emails recieved, and that is only good.
To find out more about improving your email security defenses, contact the TitanHQ team today.
by G Hunt |
December 31, 2020 |
Email Scams, Phishing & Email Spam, Spam News
The threat from phishing is ever present and phishing remains the leading cause of data breaches. All it takes is for one employee to fall for a phishing email for threat actors to gain the foothold they need to conduct more extensive attacks on the organization. But how common is phishing? In this post we provide some key 2020 phishing statistics to raise awareness of the threat and highlight the need for businesses to rethink their current phishing defenses.
2020 Phishing Statistics
Phishing is the easiest way for cybercriminals to gain access to sensitive data and distribute malware. Little skill or effort is required to conduct a successful phishing campaign and steal credentials or infect users with malware. The latest figures show that in 2020, 22% of reported data breaches started with a phishing email and some of the largest data breaches in history have started with a phishing attack, including the 78.8 million record data breach at the health insurer Anthem Inc., and the massive Home Depot data breach in 2014 that saw the email addresses of 53 million individuals stolen.
Phishing can be conducted over the phone, via SMS, social media networks, or instant messaging platforms, but email is most commonly used. Around 96% of all phishing attacks occur via email. Successful phishing attacks result in the loss of data, theft of credentials, or the installation of malware and ransomware. The cost of resolving the incidents and resultant data breaches is substantial. The 2020 Cost of a Data Breach Report by the Ponemon Institute/IBM Security revealed the average cost of a data breach is around $150 per compromised record with a total cost of $3.86 million per breach. A single spear phishing attack costs around $1.6 million to resolve.
Employees may believe they are able to spot phishing emails, but data from security awareness training companies show that in many cases, that confidence is misplaced. One study in 2020 revealed that 30% of end users opened phishing emails, 12% of users clicked a malicious link or opened the attachment in the email, and one in 8 users then shared sensitive data on phishing websites. Bear in mind that 78% of users claimed that they know they shouldn’t open email attachments from unknown senders or click links in unsolicited emails.
The 2020 phishing statistics show phishing and spear phishing are still incredibly common and that phishing attacks often succeed. Another study revealed 85% of companies have fallen victim to a phishing attack at least once. Phishing websites are constantly being created and used in these scams. Once a URL is confirmed as malicious and added to a blacklist, it has often already been abandoned by the threat actors. In 2020, around 1.5 million new phishing URLs were identified every month.
2020 has seem a massive increase in ransomware attacks. While manual ransomware attacks often see networks compromised by exploiting vulnerabilities in firewalls, VPNs, RDP, and networking equipment, ransomware is also delivered via email. Since 2016, the number of phishing emails containing ransomware has increased by more than 97%.
How to Detect and Block Phishing Threats
Tackling phishing and preventing successful attacks requires a defense in depth approach. An advanced spam filtering solution is a must to prevent phishing emails from reaching inboxes. Companies that use Office 365 often rely on the protections provided as standard with their licenses, but studies have shown that the basic level of protection provided by Microsoft’s Exchange Online Protection (EOP) is insufficient and average at best and phishing emails are often not detected. A third-party, solution is recommended to layer on top of Office 365 – One that incorporates machine learning to identify never before seen phishing threats. The solution should use email authentication protocols such as DMARC, DKIM, and SPF to identify and block email impersonation attacks and outbound scanning to identify compromised mailboxes.
End user training is also important. In the event of a phishing email arriving in an inbox, employees should be trained to identify it as such and be conditioned into reporting the threat to their IT team to ensure action can be taken to remove all instances of the threat from the email system. Web filters are also important for blocking the web-based component of phishing attacks and preventing employees from visiting phishing URLs. Multi-factor authentication on email accounts is also essential. In the event of credentials being stolen, MFA will help to ensure that the credentials cannot be used to access email accounts.
by G Hunt |
November 30, 2020 |
Email Scams, Spam News
Phishers are constantly changing their tactics to fool employees into clicking on links and disclosing their credentials. During the pandemic, many scammers switched from their tried and tested campaigns using standard business-themed lures such as fake invoices, purchase orders, and shipping notices to COVID-19 themed lures. These lures were topical and took advantage of people craving information about the coronavirus and COVID-19.
Phishers Use Fake Internal Memos About Changes to HR Work from Home Policies
Now a new phishing campaign has emerged that takes advantage of the changed business practices due to COVID-19. Many employees are still working remotely, even though their employers have started reopening their offices. During the pandemic, employees have got used to receiving regular internal company memos and updates.
The new phishing campaign spoofs the company’s HR department and appears to be an automated internal company email, similar to the messages employees are used to receiving. The emails claim to have voicemail attachments, which will also be familiar to many remote workers. The HTML attachments are personalized with the recipient’s name to add credibility to the message.
If the file attachment is opened, the user will be presented with a link they are required to click to receive the company information. In one campaign, this was a SharePoint link, although other cloud services could similarly be used. The link directs the user to SharePoint and provides an update on the company’s remote working policy. After reading the message, the worker is required to click a link that directs them to the actual phishing page where sensitive information is collected.
This campaign is very realistic. The fake remote working policy is well written and plausible and states that if employees wish to continue working from home after the pandemic, they are required to complete an HR form to provide notice in writing. The SharePoint-hosted Excel form where the user is directed is also plausible, but in addition to the request to continue to work from home, the user is required to supply their email credentials.
Phishing Campaign Offers Government Financial Aid to COVID-Affected Workers
A separate phishing campaign has been identified that is also linked to the pandemic, spoofing government agencies and offering pandemic-related financial assistance for individuals prevented from working due to COVID-19 restrictions or have otherwise been adversely affected. This campaign has targeted U.S. citizens, although similar campaigns could be conducted targeting individuals in other countries.
In this campaign, which has the subject message “US government to give citizens emergency financial aid,” the message states that the government begun issuing payments of cash compensation in October 2020. The message states that payment is only provided to USA residents and the maximum payout is $5,800.
A link is supplied in the email that the user is required to click to make a claim, which the email states will be reviewed by a support representative who will send a personal response within 24 hours. The link directs the user to a domain that spoofs the U.S. government. The user is required to enter their name and date of birth, followed by their address, contact information, Social Security number, and driver’s license number on a second form.
Phishing is the Most Common Type of Cybercrime
A recent Clario/Demos survey confirmed that phishing and email attacks are the most common types of cybercrime reported in both the United States and the United Kingdom.
The pandemic has made it easier for phishing attacks to succeed. Phishers are taking advantage of the uncertainty about changes to new ways of working caused by the pandemic, people working home alone without such a high level of support, and vulnerabilities that have been introduced as a result of the change to a fully remote workforce.
Businesses can better protect their employees by using cloud-based email and web filtering solutions. These solutions work in tandem to block the email and web-based component of phishing attacks and malware distribution campaigns. A cloud-based email filtering solution will filter out the majority of malicious messages and will keep inboxes free of threats. A web filter will prevent end users from visiting malicious links, downloading malicious attachments, or visiting malicious websites either through work-related or non-work-related Internet activity when working from the office or remotely.
TitanHQ has developed two easy to use, easy to implement, and highly effective email and web security solutions for protecting office-based and remote workers from the full range of web and email threats, including previously seen phishing emails and zero-minute attacks and new malware threats.
To better protect your business, your employees, and your networks from threats, give the TitanHQ team a call today to find out more. You will also have the opportunity to trial the SpamTitan Email Security and WebTitan Web Security solutions to see for yourself how easy they are to use and the protection they offer. You are also likely to be pleasantly surprised by how little this level of protection will cost.
by G Hunt |
November 26, 2020 |
Phishing & Email Spam, Spam Advice, Spam News
Banking Trojans have long posed a threat to businesses, but one in particular has stood head and shoulders above the rest in 2020: The Emotet Trojan.
Emotet: The Biggest Malware Threat in 2020
The Emotet Trojan first appeared in 2014 and was initially a banking Trojan, which was used to steal sensitive data such as bank account information from browsers when the user logs into their bank account. The Emotet Trojan has since been developed and it has now evolved into a much bigger threat.
Emotet is now far more effective at spreading to other devices, using a worm like element to infect other devices on the network as well as hijacking the user’s email account and using it to send copies of itself to victims’ contacts. Infected devices are added to the Emotet botnet, and have been used in attacks on other organizations. The operators of Emotet have now joined forces with other cybercriminal operations and are using their malware to deliver other Trojans such as TrickBot and QakBot, which in turn are used to deliver ransomware.
Data from HP Inc. revealed Emotet infections increased by 1,200% from Q2 to Q3, showing the extent to which activity has increased recently. Data from Check point show Emotet is the biggest malware threat, accounting for 12% of all infections in October 2020. TrickBot, which is delivered by Emotet, is the second biggest threat, accounting for 4% of infections.
Emotet and TrickBot are Driving the Increase in Ransomware Infections
The Emotet and TrickBot Trojans are driving the increase in ransomware infections globally, especially attacks on healthcare organizations. The healthcare industry in the United States is being targeted by ransomware gangs due to the increased chance of the ransom being paid. In many cases, the recent ransomware attacks have been made possible due to previous Emotet an TrickBot infections.
Unfortunately, due to the efficient way that Emotet spreads, removing the malware can be problematic. It is probable that more than one device has been infected, and when the Trojan is removed from one device, it is often reinfected by other infected devices on the network.
Emotet is primarily spread via phishing emails, most commonly using malicious macros in Word documents and Excel spreadsheets, although JavaScript attachments are also known to be used. The lures used in the phishing emails are highly varied, often using topical lures linked to recent news events, COVID-19, and holiday season lures in the run up to Halloween, Black Friday, and Cyber Monday.
The best way of preventing attacks is stopping the Emotet emails from reaching inboxes and making sure that employees are trained how to recognize phishing emails.
How SpamTitan Can Protect Your Organization
SpamTitan use a wide range of different techniques to identify phishing emails that are used to deliver malware such as Emotet. These measures provide layered protection, so should one check fail to identify the threat, several others are in place to provide protection.
SpamTitan uses dual antivirus engines to identify previously seen malware variants and email sandboxing to identify new (zero day) malware threats. Suspicious email attachments are sent to the sandbox where they are subjected to in depth analysis to identify malicious actions such as command and control center callbacks.
Users can set controls to quarantine or reject messages with certain types of email attachments, and while blocking Word and Excel documents and spreadsheets is not practical for most businesses, setting rules to quarantine these files for manual review if they have macros is certainly wise, as is blocking JavaScript files and other file types commonly used to install malware.
SpamTitan uses Sender Policy Framework (SPF) and DMARC to block spoofing and email impersonation attacks, which are used to convince employees to open attachments and click malicious links. SpamTitan also includes outbound scanning, which detects devices that have potentially been infected and prevents messages from spreading Emotet internally and to business contacts.
There are many cybersecurity solutions that can provide protection against malware, but finding one that is easy to use, effective, and reasonably priced can be a challenge.
SpamTitan ticks all of those boxes. It is the most and best ranked email security solution on Capterra, GetApp and Software Advice, has achieved a rating of 4.9 out of 5 on Google reviews, and is listed in the top three in the email security gateway, MSP email security, and email security for Office 365 categories.
If you want to protect your organization from Emotet and other malware and phishing attacks, give the TitanHQ team a call to find out more about SpamTitan Email Security.
by G Hunt |
October 13, 2020 |
Phishing & Email Spam, Spam News
The TrickBot Trojan, one of the biggest malware threats to appear in recent years, has had its backend infrastructure taken down by a coalition of tech firms.
TrickBot started life in 2016 as a banking Trojan used to target Windows devices but the malware has received many updates over the years and has had many new modules added to give it a much wider range of capabilities. TrickBot targets hundreds of different banks and also steals credentials and Bitcoin wallets. In recent years, the operators have teamed up with several different criminal organizations and have used the Trojan to deliver keyloggers, cryptominers, information stealers and ransomware variants such as Ryuk and Conti. TrickBot can now perform a huge range of malicious actions via many different plugins and in January and February 2020 was targeting more than 600 websites via a webinject module, most of which being financial institutions.
The Trojan achieves persistence on infected devices and adds them to a botnet, which has grown into one of the largest in operation. The operators of the Trojan are also known to use the EternalBlue exploit to move around infected networks and spread the Trojan to other devices on the network. This can make removal of the Trojan difficult, as once it is removed from a device, other infected devices on the network simply reinfect it when it is reconnected.
TrickBot is primarily spread via phishing emails via malicious macros, but other malware-as-a-service operations also deliver TrickBot, such as Emotet. TrickBot typically used lures aimed at business users, such as shipment receipts, receipt reminders, required declarations, delivery notifications, and other logistics themes using Word and Excel attachments and Java Network Launch Protocol (.jnlp) attachments, as well as malicious hyperlinks embedded in emails. In 2020, a large-scale campaign was conducted using coronavirus and COVID-19 themed lures, one of which spoofed humanitarian groups and claimed to offer free COVID-19 tests.
Those emails were sent by a diverse range of compromised email accounts and marketing platforms, with the threat group also using domains with their own mail servers to distribute the malware. There has been growing concern that the botnet could also be used in campaigns to disrupt the upcoming November 3, 2020 U.S. presidential election.
TrickBot is stealthy and uses a variety of mechanisms to evade detection by security solutions, including password protected zip files, delayed downloads of the Trojan when macros are run, heavily obfuscated loaders, encryption of configuration files, and a complex command and control infrastructure. The latter has now been untangled and its backend infrastructure has been taken down.
Several tech firms including Microsoft, ESET, Black Lotus Labs, and NTT have been working together for months to try to disrupt the TrickBot operation. More than 125,000 samples of the TrickBot Trojan were analyzed along with over 40,000 configuration files used by various TrickBot modules. After several months of painstaking work, the command and control servers used by the botnet were identified and its network infrastructure was mapped. Armed with the IP addresses, Microsoft obtained a court order and seized control of the infrastructure of servers used to distribute and communicate with the malware and its various modules. The IP addresses associated with the malware have now been disabled.
When the takedown occurred, more than 1 million devices had been infected with the malware and were part of its botnet. The takedown is great news, as one more malware threat – and a major one at that – has been taken out of action, at least temporarily. Efforts are now underway by ISPs to contact victims to ensure the Trojan is removed from their systems.
by G Hunt |
August 24, 2020 |
Phishing & Email Spam, Spam News
Businesses are constantly targeted by cybercriminals and phishing one of the easiest ways that they can gain a foothold in corporate networks. An email is sent to an employee with a lure to entice them to click an embedded hyperlink and visit a website. When they arrive on the site, they are presented with a login prompt and must enter their credentials. The login prompt is indistinguishable from the real thing, but the domain on which the login prompt appears is controlled by the attacker. Any information entered on the website is captured.
End user training will go a long way to keeping your business protected against phishing attacks. Phishers target people using a variety of “social engineering” tactics to get them to take a specific action, which could be visiting a website and downloading malware, giving up their login credentials, or sending a wire transfer to the criminal’s bank account. By conditioning employees to perform checks and to stop and think before taking any action suggested in an email, you will greatly improve resilience to phishing attacks.
Many employees will say that they can identify a phishing email and will never be fooled, but the number of successful phishing attacks that are occurring every day suggests there are gaps in knowledge and even the most tech-savvy individuals can be fooled.
To illustrate this point, consider the SANS Institute. If you have never heard of the SANS Institute, it is one of the world’s leading computer and information security training and certification organizations, including anti-phishing training.
In August 2020, the SANS Institute announced that one of its employees had fallen for a phishing scam and disclosed their login credentials. The attacker used those credentials to access the account and set up a mail forwarder that sent a copy of every email to the attacker’s email account. 513 emails, some of which contained sensitive information on SANS members, were forwarded to the account before the attack was detected. The emails contained the personally identifiable information of 28,000 SANS members. The SANS Institute decided to use this attack as a training tool and will be providing details of how it succeeded to help others prevent similar attacks.
This incident shows that even the most highly trained individuals can fall for a phishing email. Had training not been provided, instead of one compromised email account there could have been many.
Phishers are constantly changing tactics and developing new scams to fool people and technological anti-phishing solutions. The key to phishing attack prevention is to implement a range of defenses to block attacks. Any one of those measures may fail to detect a phishing email on occasion, but others will be in place to provide protection. This defense-in depth approach is essential given the sophistication of phishing attacks and the volume of messages now being sent.
In addition to regular end user training and phishing simulation emails to harden the human element of your defenses, you need an advanced spam filter. If you use Office 365 you will already have a basic level of protection provided through Microsoft’s basic spam filter, Exchange Online Protection (EOP), but this should be augmented with a third-party solution such as SpamTitan to block more threats. EOP blocks spam, known malware, and many phishing emails, but SpamTitan will greatly improve protection against more sophisticated phishing attacks and zero-day malware.
You should also consider implementing a web filter to block the web-based component of phishing attacks. When an employee attempts to visit a malicious website that is used to steal credentials and other sensitive information, a web filter can prevent that website from being accessed.
With a spam filter, web filter, and end user training, you will be well protected, but you should also implement 2-factor authentication. If credentials are stolen, 2-factor authentication can prevent those credentials from being used by the attacker to gain access to the account.
For more information on spam filtering, web filtering, and phishing protection, give the TitanHQ team a call. Our team of experienced engineers will be happy to help you set up SpamTitan email security and the WebTitan web filter on a free trial so you can see for yourself how effective both are at blocking phishing attacks and other cybersecurity threats.
by G Hunt |
August 14, 2020 |
Email Scams, Phishing & Email Spam, Spam News
Several SBA loan phishing scams identified in recent weeks that impersonate the U.S. Small Business Administration in order to obtain personally identifiable information and login credentials for fraudulent purposes.
Due to the hardships suffered by businesses due to the COVID-19 pandemic, the SBA’s Office of Disaster Assistance is offering loans and grants to small businesses to help them weather the storm.
Hundreds of millions of dollars have been made available by the U.S. government under the Coronavirus Aid, Relief, and Economic Security Act (CARES Act) to help struggling individuals and companies during the pandemic. Cybercriminals have been quick to develop campaigns to fraudulently obtain those funds, raid bank accounts, steal sensitive information, and distribute malware and ransomware.
Several phishing campaigns have been launched since April 2020 targeting businesses that are considering or have already applied for loans under the SBA’s Economic Injury Disaster Loan Program.
Phishing emails have been sent encouraging small businesses to apply for a loan. One such campaign confirms that the business is eligible for a loan and the loan has been pre-approved. The purpose of the scam is to obtain business information that allows the scammers to apply for a loan on behalf of the business and pocket the funds.
Another scam impersonates the SBA and claims an application for a loan is complete and payment will be made once supporting documents have been received. The emails include an attached form that must be completed and uploaded to the SBA website. The email attachment appears to be a .img file but has a hidden double extension and is actually a .exe executable. Double-clicking and running the file will see GuLoader malware installed, which is a downloader that can deliver a range of different malicious payloads.
The same email address used for that campaign was used in a different attack that included a PDF form that requested bank account information and other sensitive data, which needed to be completed and uploaded to a spoofed SBA website.
In the past few days, yet another SBA loan phishing scam has come to light. Phishing emails were sent to Federal Executive Branch, and state, local, tribal, and territorial government agencies. The phishing scam relates to an SBA application for a loan with the subject line “SBA Application – Review and Proceed.” The emails links to a cleverly spoofed SBA web page that indistinguishable from the genuine login page apart from the URL that attempts to steal credentials. The scam prompted the DHS’ Cybersecurity and Infrastructure Security Agency (CISA) to issue an emergency alert warning of the scam.
These SBA loan phishing scams use a variety of lures and have multiple aims, but they can be avoided by following good cybersecurity best practices.
First and foremost, you should have an advanced spam filtering solution in place such as SpamTitan. SpamTitan checks email headers and message content for signs of spam, phishing, and scams and uses DMARC and sender policy framework (SPF) to identify and block email impersonation attacks.
Dual antivirus engines detect 100% of known malware and sandboxing is used to subject attachments to deep analysis to identify malicious code and malware that has not been seen before. Machine learning technology is also used to identify new phishing scams, along with multiple threat intelligence feeds to identify known phishing scams.
Prior to opening any downloaded document or file it should be scanned using antivirus software that has up-to-date virus definitions. Check the properties of files to make sure they are what they claim to be and do not have a double extension.
Care should be taken when opening any email or email attachment, even emails that are expected. Steps should be taken to verify the legitimacy of any request received via email, especially one that requires the provision of personally identifiable information or requests for bank account and other highly sensitive information.
Emails and websites may look legitimate and have SBA logos, but that does not guarantee they are genuine. Always carefully check the sender of the email – Genuine SBA accounts end with sba.gov. The display name can easily be spoofed so click reply and carefully check the email address is correct. Care should be taken when visiting any website linked in an email. Check the full URL of any website to make sure it is a legitimate domain.
CISA also recommends monitoring users’ web browsing habits and restricting access to potentially malicious websites. The easiest way to do this is by using a web filtering solution such as WebTitan. WebTitan allows businesses to monitor Internet activity in real time, send automatic alerts, block downloads of certain file types, and carefully control the types of websites that can be accessed by employees.
For more information on spam filtering and web filtering solutions to protect your business from phishing and other cyberattacks, give the SpamTitan team a call today.
by G Hunt |
July 26, 2020 |
Phishing & Email Spam, Spam News
A new phishing campaign has been detected that uses Google Cloud Services to fool victims into giving up their Office 365 credentials. The new campaign is part of a growing trend of disguising phishing attacks using legitimate cloud services.
The phishing attack starts like any other with an email containing a hyperlink that the recipient is requested to click. If the user clicks the link in the email, they are directed to Google Drive where a PDF file has been uploaded. When the file is opened, users are asked to click a hyperlink in the document, which appears to be an invitation to access a file hosted on SharePoint Online.
The PDF file asks the victim to click the link to sign in with their Office 365 ID. Clicking the link will direct the user to a landing page hosted using Google’s storage.googleapis.com. When the user arrives on the landing page, they are presented with an Office 365 login prompt that looks exactly like the real thing. After entering their credentials, they will be directed to a legitimate PDF whitepaper that has been obtained from a well-respected global consulting firm.
The campaign has been designed to make it appear that the victim is simply being directed to a PDF file that has been shared via Sharepoint, and the actual PDF file is displayed after the victim has divulged their credentials. It is therefore likely that the victim will not realize that their Office 365 credentials have been phished. The only sign that this is a scam is the source code on the phishing page, which even tech-savvy individuals would be unlikely to check.
This campaign was identified by researchers at Check Point, but it is just one of many similar campaigns to have been identified over the past few months. Since these domains are legitimate and have valid SSL certificates, they are difficult to detect as malicious. This campaign abused Google Cloud Services, but several other campaigns have been detected using the likes of IBM Cloud, Microsoft Azure and others to add legitimacy to the campaigns.
This campaign highlights the importance of providing security awareness training to the workforce and warning employees about the risks of clicking links in unsolicited emails, even those that link to genuine domains. An advanced email security solution should also be implemented to block malicious emails and ensure the majority of malicious messages are not delivered to inboxes. That is an area where TitanHQ can help.
by G Hunt |
July 24, 2020 |
Phishing & Email Spam, Spam News
Emotet was the most prolific malware botnet of 2018 and 2019, but the botnet fell silent on February 7, 2020, but it has now sprung back to life and is being used to distribute Trojan malware. The botnet returned with a malicious spam campaign on July 17 of at least 30,000 emails, mostly targeting organizations in the United States and the United Kingdom. The scale of the campaign has now grown to around 250,000 emails a day with the campaign now global.
The Emotet botnet is a network of computers infected with Emotet malware and there are estimated to be around half a million infected Windows computers under the control of the botnet operators. Those infected devices are contacted through the attackers’ command and control (C2) servers and are sent instructions to send out spam emails spreading Emotet malware.
Once the malware is downloaded, the infected computer is added to the botnet and is used to send spam emails. Emotet infections can also spread laterally within an organization. When investigations are launched following the detection of Emotet, it is common for other computers to be discovered to be infected with the malware.
What makes Emotet particularly dangerous is the operators of the botnet pair up with other threat groups and deliver other malware variants. Emotet has been used to distribute a range of malware variants since its creation in 2014, but recently the malware payload of choice was the TrickBot Trojan. TrickBot is a banking trojan cum information stealer that also serves as a malware downloader. In addition to stealing sensitive data, the operators of TrickBot pair up with other malware developers, notably the developers of Ryuk ransomware. Once TrickBot has stolen information, the baton is passed over to Ryuk, which will also steal data before encrypting files on the network. The new Emotet campaign started by distributing the TrickBot Trojan, although the payload has since switched to the QakBot banking Trojan. QakBot also delivers ransomware as a secondary payload, with Prolock often used in the past.
Emotet emails use a variety of lures to get recipients to click links to malicious websites or open infected email attachments. Emotet targets businesses, so the lures used are business-related, such as fake shipping notices, invoices, purchase orders, receipts, and job applications. The emails are often personalized, and threat actors are known to hijack email threads and send responses with malicious documents added.
An Emotet infection is serious and should be treated with the same urgency as a ransomware attack. Prompt action may allow Emotet to be removed before a secondary payload is delivered.
Fortunately, Emotet malware is delivered via email which gives businesses an opportunity to prevent infections. By deploying an advanced spam filter such as SpamTitan that has sandboxing to subject email attachments to deep analysis, these malicious emails can be identified and quarantined. Coupled with other email security measures such as end user training, businesses can mount a robust defense and block infections.
The return of Emotet was inevitable, and while the resumption of activity is bad news, there is some good news. A vigilante hacker has started sabotaging Emotet operations by targeting a weak link in their infrastructure. Emotet malware is downloaded from the internet from a range of hacked WordPress sites. The vigilante has found that the temporary stores of Emotet can be easily hacked as they tend to all use the same password. After guessing that password, the Emotet payload has been replaced with a variety of animated GIFs and has disrupted operations, reducing infections to around a quarter of their normal levels. That said, the Emotet gang is attempting to regain control of its web shells and infections with Emotet are still growing.
by G Hunt |
May 21, 2020 |
Network Security, Spam News, Spam Software
A recent survey by Capterra on British SMEs has revealed 30% have fallen victim to a phishing attack during the COVID-19 lockdown. Just under half of the phishing emails received (45%) were related to coronavirus or COVID-19.
COVID-19 phishing emails increased significantly during the first quarter of 2020 as the coronavirus spread around the world. Since the virus was unknown to science, scientists have been working tirelessly to learn about the virus, the disease it causes, how the virus is spread, and what can be done to prevent infection. The public has been craving information as soon as it is available, which creates the perfect environment for phishing attacks. People want information and threat actors are more than happy to offer to provide it.
The Capterra survey highlights the extent to which these campaigns are succeeding. Employees are receiving phishing emails and being fooled by the social engineering tactics the scammers have adopted. The high success rate has seen many threat actors temporarily abandon their tried and tested phishing campaigns that they were running before the SARS-CoV-2 outbreak, and have repurposed their campaigns to take advantage of the public’s thirst for knowledge about the virus. In the first quarter of 2020, KnowBe4 reported a 600% increase in COVID-19 and coronavirus themed phishing emails.
The high percentage of businesses that have experienced phishing attacks during the COVID-19 lockdown indicates many SMEs need to augment their anti-phishing defenses. There is also a need for further training to be provided to employees, as the emails are being opened and links are being clicked.
On the training front, formal training sessions may be harder to administer with so many employees working remotely. Consider conducting short training sessions via teleconferencing platforms and sending regular email alerts warning about the latest techniques, tactics and procedures being used in targeted attacks on remote workers. Phishing simulation exercises can be hugely beneficial and will help to condition workers to check emails thoroughly and report any threats received. These simulations also help identify which employees need further training to help them recognize potential phishing attacks.
Of course, the best way to ensure that employees do not open phishing emails and malicious attachments is to ensure they are not delivered to employees’ inboxes. That requires an advanced spam filtering solution.
Many SMEs and SMBs have now moved to an Office 365 hosted email solution, in which case email filtering will be taking place using Microsoft’s Exchange Online Protection – The default spam filtering service that protects all office 365 users. If you are reliant on this solution for filtering out phishing emails and other types of malicious messages, you should consider adding a third-party solution on top of EOP.
Exchange Online Protection provides a reasonable level of security and can block phishing emails and known malware threats, but it lacks the features of more advanced spam filtering solutions and cloud-based email security gateways, such as machine learning and predictive technology to identify attacks that have not been seen before.
As an additional protection against phishing attacks, a web filtering solution should be considered. In the event of a phishing email arriving in an inbox, a web filter serves as an additional layer of protection to prevent attempts by employees to visit websites linked in the emails. When an attempt is made to visit a known phishing website or web content that violates your acceptable internet usage policies, access will be blocked and the user will be directed to a local web page telling them why access has been denied.
Multi-factor authentication should also be implemented for email to ensure that in the event that credentials are compromised, a second factor must be provided before access to the email account is granted.
For more information on spam filtering and web filtering, and further information on TitanHQ’s advanced cloud-based email security solution – SpamTitan – and DNS-based web filtering solution – WebTitan – give the TitanHQ team a call today.
by G Hunt |
April 15, 2020 |
Email Scams, Phishing & Email Spam, Spam News
Data obtained by the UK think tank Parliament Street has revealed the extent to which universities are being targeted by cybercriminals and the sheer number of spam and malicious emails that are sent to the inboxes of university staff and students.
Data on malicious and spam email volume was obtained by Parliament Street through a Freedom of Information request. The analysis of data from UK universities showed they are having to block millions of spam emails, hundreds of thousands of phishing emails, and tens of thousands of malware-laced emails every year.
Warwick University’s figures show that more than 7.6 million spam emails were sent to the email accounts of staff and students in the final quarter of 2019 alone, which included 404,000 phishing emails and more than 10,000 emails containing malware.
It was a similar story at Bristol University, which received more than 7 million spam emails over the same period, 76,300 of which contained malware. Data from the London School of Hygiene and Tropical Medicine revealed more than 6.3 million spam emails were received in 2019, which included almost 99,000 phishing emails and more than 73,500 malware attacks. 12,773,735 spam and malicious emails were received in total for 2018 and 2019.
Data from Lancaster University revealed more than 57 million emails were rejected for reasons such as spam, malware, or phishing, with 1 million emails marked as suspected spam. The figures from Imperial College London were also high, with almost 40 million emails blocked in 2019.
Like attacks on companies, cyberattacks on universities are often conducted for financial gain. These attacks attempt to deliver malware and obtain credentials to gain access to university networks to steal data to sell on the black market. Universities store huge amounts of sensitive student data, which is extremely valuable to hackers as it can be used for identity theft and other types of fraud. Attacks are also conducted to deliver ransomware to extort money from universities.
Universities typically have high bandwidth to support tens of thousands of students and staff. Attacks are conducted to hijack devices and add them to botnets to conduct a range of cyberattacks on other targets. Email accounts are being hijacked and used to conduct spear phishing attacks on other targets.
Nation state-sponsored advanced persistent threat (APT) groups are targeting universities to gain access to intellectual property and research data. Universities conduct cutting-edge research and that information is extremely valuable to companies that can use the research data to develop products to gain a significant competitive advantage.
Universities are seen as relatively soft targets compared to organizations of a similar size. Cybersecurity defenses tend to be far less advanced, and the sprawling networks and number of devices used by staff and students make defending networks difficult.
With the number of cyberattacks on universities growing, leaders of higher education institutions need to take steps to improve cybersecurity and prevent the attacks from succeeding.
The majority of threats are delivered via email, so advanced email security defenses are essential, and that is an area where TitanHQ can help.
Independent tests show SpamTitan blocks in excess of 99.97% of spam email, helping to keep inboxes free of junk email. SpamTitan incorporates dual anti-virus engines to block known threats, machine learning to identify new types of phishing attacks, and sandboxing to detect and block zero-day malware and ransomware threats. When email attachments pass initial tests, suspicious attachments are sent to the sandbox for in-depth analysis to identify command and control center callbacks and other malicious actions. SpamTitan also incorporates SPF and DMARC controls to block email impersonation attacks, data loss prevention controls for outbound messages, and controls to detect potential email account compromises.
If you want to improve your cybersecurity defenses, start by upgrading your email security defenses with SpamTitan. You may be surprised to discover the little investment is required to significantly improve your email security defenses. For more information, call the TitanHQ team today.
by G Hunt |
March 11, 2020 |
Phishing & Email Spam, Spam News
Microsoft has announced it has taken control of the U.S. infrastructure of the Necurs botnet and has taken steps to prevent the botnet operators from registering new domains and the rebuilding the Necurs infrastructure.
The Scale of the Necurs Botnet
The Necurs botnet first appeared in 2012 and has grown into one of the largest spam and malware distribution networks. The botnet consists of around 9 million devices that have been infected with Necurs malware. Each device within the botnet is under the control of the cybercrime group behind the botnet.
The Necurs botnet is used to commit a wide range of cybercrimes by the operators of the botnet as well as other cybercriminal groups who rent out parts of the botnet as a service. The Necurs botnet was used for malware and ransomware distribution, cryptocurrency mining, and attacks on other computers to steal credentials and confidential data. The Necurs botnet also has a distributed Denial of Service (DDoS) module capable of performing massive DDoS attacks, although this function is yet to be used.
The main use of the botnet is spamming. The botnet has been used to send vast quantities of spam email, including emails pushing fake pharmaceutical products, pump and dump stock scams, and Russian dating scams. To give an example of the scale of the spamming, over a 58-day period of observation, Microsoft found that a single Necurs malware-infected computer had sent out 3.8 million spam emails to 40.6 million email accounts. That is just one infected device out of 9 million! In 2017, the botnet was being used to spread Dridex and Locky ransomware at a rate of around 5 million emails an hour and between 2016 and 2019 the botnet was responsible for 90% of email-based malware attacks.
The Takedown of Necurs Infrastructure
Microsoft has tracked the criminal activity of the Necurs botnet operators for 8 years. The gang is believed to be Evil Corp, the Russian cybercriminal group behind the Dridex banking Trojan. Evil Corp has been named the most harmful cybercrime group in the world.
The takedown of the Necurs botnet involved a coordinated effort by Microsoft and partners in 35 countries. Microsoft obtained an order from the U.S. District Court for the Eastern District of New York on March 5, 2020 to seize the U.S. domains used by the botnet operators. These domains were used to issue commands to the 9 million infected computers.
Simply seizing the domains would not be sufficient to take down the botnet, as the botnet’s command and controls servers could be rapidly rebuilt. Domains used by the threat actors are often taken down, so new domains are constantly registered weeks or months in advance.
The key to long-term disruption of the botnet was cracking the algorithm used by the threat actors to generate new domains. Microsoft analyzed the algorithm and calculated more than 6 million domains that would be used by the threat actors over the next 25 months. Steps have been taken to prevent those domains from being registered and becoming part of the Necurs infrastructure.
The 9 million devices around the world are still infected with Necurs malware. Microsoft and its partners have identified the infected devices and are working with ISPs and CERT teams around the world to rid those devices of the malware.
by G Hunt |
February 17, 2020 |
Phishing & Email Spam, Spam News
Just a few days after new figures from the FBI confirmed business email compromise scams were the biggest cause of losses to cybercrime, news broke of a massive cyberattack on a Puerto Rico government agency. Cybercriminals had gained access to the email account of an employee, understood to work in the Puerto Rico Employee Retirement System.
The compromised email account was used to send requests to other government agencies requesting changes be made to standard bank accounts for remittance payments. Since the email account used was trusted, the changes to bank accounts were made. Scheduled payments were then made as normal and millions of dollars of remittance payments were wired to attacker-controlled bank accounts.
The Puerto Rico Industrial Development Company, a state-owned corporation that drives economic development of the country, was one of the worst hit. Emails were received requesting changes to bank accounts and two payments were made. The first payment of $63,000 was made in December and another payment of $2.6 million in January. Other departments were also targeted, including the Tourism Company. The latter made a payment of $1.5 million. In total, the scammers attempted to steal around $4.73 million.
The business email compromise scam was uncovered when those payments were not received by the correct recipients. Prompt action was then taken to block the transfers and some of the payments were frozen, but the government has not been able to recover around $2.6 million of the stolen funds.
A full investigation has been launched to determine how the attackers gained access to the email account to pull off the scam. While the method used has not been confirmed, BEC attacks usually start with a spear phishing email.
A phishing email is sent to a person of interest requesting urgent action be taken to address a problem. A link is supplied in the email that directs the user to a website that requests their email account credentials. The account can then be accessed by the attacker. Attackers often set up mail forwarders to receive a copy of every email sent to and from the account. This enables them to learn about the company and typical payments and construct highly convincing scam emails.
Once access to a corporate email account is gained, the BEC scam is much harder to identify and block. The best defense is to ensure that the initial phishing emails are not delivered, and that is an area where TitanHQ can help.
by G Hunt |
January 31, 2020 |
Email Scams, Phishing & Email Spam, Spam News
A novel coronavirus phishing campaign has been detected that uses scare tactics to trick users into infecting their computer with malware.
The World Health Organization has now declared the 2019 novel coronavirus outbreak a global emergency. The number of cases has increased 10-fold in the past week with almost 9,100 cases confirmed in China and 130 elsewhere around the world.
A worldwide health crisis such as this has naturally seen huge coverage in the press, so it is no surprise that cybercriminals are capitalizing on the concern and are using it as a lure in a malspam campaign to scare people into opening an email attachment and enabling the content.
A novel coronavirus phishing campaign has been detected that uses a fake report about the coronavirus to get email recipients to open a document that details steps that should be taken to prevent infection. Ironically, taking the actions detailed in the email will actually guarantee infection with a virus of a different type: Emotet.
The coronavirus phishing campaign was identified by IBM X-Force researchers. The campaign is targeted on users in in different Japanese prefectures and warning of an increase in the number of local confirmed coronavirus cases. The emails include a Word document attachment containing the notification along with preventative measures that need to be taken.
If the attachment is opened, users are told they must enable content to read the document. Enabling the content will start the infection process that will see the Emotet Trojan downloaded. Emotet is also a downloader of other malware variants. Other banking Trojans and ransomware may also be downloaded. Emotet can also send copies of itself to the victim’s contacts. Those messages may also be coronavirus related.
To add credibility, the Emotet gang makes the emails appear to have been sent by a disability welfare service provider in Japan. Some of the captured messages include the correct address in the footer.
More than 2,000 new infections have been confirmed in the past 24 hours in China and all of its provinces have now been impacted. Cases have now been reported in 18 other countries with Thailand and Japan the worst hit outside of China with 14 cases confirmed in each country. As the coronavirus spreads further and more cases are reported, it is likely that the Emotet gang will expand this campaign and start targeting different countries using emails in different languages. Kaspersky lab has also said that it has identified malspam campaigns with coronavirus themes that use a variety of email attachments to install malware.
Businesses can protect against Emotet, one of the most dangerous malware variants currently in use, by implementing a spam filtering solution such as SpamTitan that incorporates a sandbox where malicious documents can be analyzed in safety to check for malicious actions.
For further information on protecting your email system, contact TitanHQ today.
by G Hunt |
January 30, 2020 |
Industry News, Phishing & Email Spam, Spam News
It has been well documented how much time businesses waste dealing with spam and there is no denying the threat that malicious spam emails (malspam) pose, but it is not just a problem for big business. Spam in academia is also a major problem.
A recent study published in the journal, Scientometrics, explores the cost of spam in academia. The study was primarily focused on spam emails sent by new, non-peer-reviewed journals that are attempting to gain a share of the market. These journals are adopting the same spam tactics often used by scammers to sell cheap watches and cut-price medications and for phishing and spreading malware.
Three researchers – Jaime A. Teixeira da Silva, Aceil Al-Khatib, and Panagiotis Tsigaria – attempted to quantify the amount of time that is being wasted dealing with those messages and the losses that result.
To assess the extent of the problem, the researchers used figures from several studies on spamming to obtain an average number of targeted spam emails that academics receive each day. They opted for a conservative figure of 4-5 messages, per academic, per day. Most of those messages take just a few seconds to open and read but that time mounts up. They assumed an average time of 5 seconds per message – less than half a minute per day. That equates to $100 per researcher, per year at an average hourly rate of $50. Using the United Nations estimate of the number of researchers in academia globally, the total global cost of spam in academia was estimated to be $1.1 billion a year.
That figure is based on the lost time alone and does not factor in non-targeted spam emails – bulk unsolicited emails not specifically targeting researchers. Add in the time dealing with those messages and the global cost reaches $2.6 billion a year. To put the cost into perspective, $2.6 million is much more than the time researchers devote to peer review, which has been estimated at a cost of $1.9 billion a year. The figures do not include the considerable losses due to phishing, malware, and ransomware attacks. Factor in those costs and the losses would be several orders of magnitude higher.
Co-author of the study, Panagiotis Tsigaris, a professor of economics at Thompson Rivers University in Canada, explained that there is no silver bullet when it comes to dealing with spam and suggested several ways that the cost of spam in academia could be reduced.
Tsigaris suggests that penalties should be increased for publishing in predatory journals, and that academics should be educated about spam email and that improvements should be made to email filtering technology.
Here at TitanHQ, we are well aware of the problem of spam, both in terms of the productivity losses that spam causes, and harm caused by malicious spam emails.
To help prevent losses and downtime due to spam and email-based threats, TitanHQ has developed a powerful, easy-to-use, and cost-effective cloud-based spam filtering solution called SpamTitan. SpamTitan has been independently tested and shown to block in excess of 99.9% of spam email, 100% of known malware and ransomware threats, and thanks to a host of detection measures and sandboxing, SpamTitan is also effective at blocking zero-day (new) malware and ransomware threats.
To find out more about SpamTitan and how you can block more spam and ensure malicious emails do not reach your researchers’ inboxes, give the TitanHQ team a call today.
by G Hunt |
December 3, 2015 |
Spam News
A recent study conducted by CyberArk has revealed that enterprises now face a high level of risk of privileged account hacking. In fact, the majority of enterprises are at risk of being hacked. Many companies are underestimating the risk, although IT professionals have long been aware of the danger of privileged account hacking.
The study suggests 88% of enterprise networks are susceptible to attack. A complete compromise of the corporate network is possible via 40% of Windows machines. The researchers predict that all it would usually take is for one privileged account to be hacked to allow the attackers to gain access to most accounts and systems. The researchers also determined that any enterprise that has Windows hosts is susceptible to attack via privileged account hacking.
To produce the report “Analyzing Real-World Exposure to Windows Credential Theft Attacks” CyberArk surveyed 51 organizations of varying sizes to determine the level of risk faced from privileged account hacking and the extent to which networks could be compromised should hackers manage to gain access to super-user and/or service accounts.
The results of the survey paint an incredibly worrying picture. The hacking of privileged accounts is not just a problem that must be dealt with by large corporations. Small to medium-sized businesses are also being targeted. Hackers are gaining access to their systems and are using them to launch attacks on their supply chain partners.
The privileged account hacking risk is often underestimated
Many organizations are not even aware how substantial the privileged account hacking risk is. An organization employing 500 individuals may have 1500 or more privileged accounts according to the researchers. The risk of attack is greatest with servers and lower with workstations. This is because servers can be used to gain access to a much wider range of systems and data than workstations. If any one server is compromised, attackers can use that machine for privileged account hacking and can gain access to many other Windows hosts on the network.
Attackers have months to analyze the network infrastructure and exfiltrate data
Mandiant recently estimated the median number of days for enterprises to discover their networks have been compromised is 229 days. The latest report from CyberArk also suggests a similar timescale for detection – placing the time frame at between 6 to 8 months. Once attackers have gained access to a network, they are exceptionally good at hiding and covering their tracks, and have months to browse the network.
How are hackers gaining access to privileged account login credentials?
In many cases, user credentials are stolen via phishing campaigns. Oftentimes, the attacks are highly sophisticated and highly targeted. Individual users are selected and a campaign is developed to fool them into visiting a malicious website and downloading malware or opening an infected email attachment.
Information about the target is obtained via social media networks such as Facebook, Twitter, or LinkedIn. Their contacts are identified, and a phishing email is either sent from a hacked colleagues account or is masked to make it appear that it has been sent from a trusted individual.
All too often a sophisticated attack is not necessary. If malware can be installed on just one single computer, shared-privilege accounts can be used to gain access to a wide range of systems.
What can enterprises do to protect their networks from privileged account hacking?
Protecting against the hacking of privileged accounts is difficult. It is not possible to eliminate privileged accounts as they essential to the functioning of the business. Since these accounts cannot be eliminated, efforts must be made to make accounts more secure. Unfortunately, the management of privileged accounts is complicated and is difficult to automate.
A survey recently conducted by Dimensional Research/Dell highlights the extent of the current problem. 560 IT professionals were asked about privileged access management and 41% revealed that they did not use any software at all or rely on Excel or other spreadsheet software packages to manage their accounts.
Fewer than half of respondents did not log or monitor privileged account access. 23% did not have a defined account management process. 28% did not have a defined process for changing default passwords on new equipment and software. Passwords were also found not to be changed frequently. Only a quarter of organizations changed admin passwords every month.
Make it harder for networks to be compromised by privileged account hacks
In order to improve security and prevent the hacking of privileged accounts, IT professionals should:
- Develop a defined process for managing privileged accounts
- Conduct a full audit of the network to locate all privileged accounts
- Ensure all passwords are unique, complex, and very difficult to guess
- Monitor and audit account passwords
- Use different passwords for different systems
- Change default passwords on all new devices and software
- Change passwords at least once a month
- Implement an automated solution to manage privileged accounts
- Ensure that a full risk assessment is conducted and any security holes are plugged rapidly (Hours rather than weeks or months)
- Conduct an audit of all suppliers and business partners to ensure they have sufficient security in place
- Implement solutions to protect users from phishing and spear phishing attacks, such as anti-spam software with anti-phishing controls
- Implement a web filter to reduce the probability of a user downloading malware to the network from malicious websites.
Fail to secure your login credentials, and privileged account hacking will not be only be a risk; it will be a reality.
by G Hunt |
November 27, 2015 |
Spam News
Cryptowall 3 ransomware is the latest incarnation of the Trojan that first appeared in the latter half of 2014. This variant was discovered earlier this year and it has been used to extort millions out of individuals and businesses.
The threat from ransomware is growing
Ransomware infections have been reported much more frequently in recent months. A fortune has already been spent undoing the damage caused. Unfortunately, since the malware is evolving, it can be difficult to block.
Cryptowall 3 ransomware is very similar to previous incarnations and operates in a very similar fashion. The problem is that the algorithm it uses to obfuscate the dropper, which is applied three times, differs from Cryptowall 2. This makes it harder to identify.
Cryptowall 3 ransomware employs multiple dropper files and contains a number of different exploits. Once initiated, code is injected into a new explorer.exe process which installs the malware while disabling system protections. Malicious code is then hidden in a new SVChost.exe process.
The malware collects a considerable amount of data from the host computer, obtains an external IP address, establishes a connection, and registers the machine with the hacker’s command and control center. A POST request is made and the main Cryptowall 3 thread is initiated.
Cryptowall 3 ransomware subsequently encrypts certain file types on mounted network drives and local drives using public-key cryptography. The key to unlock the encryption is only stored on the hacker’s server. The victim is then advised to pay a ransom to have the infection removed and files unlocked. Failure to respond will see files locked forever or permanently deleted.
Cryptowall 3 ransomware is spread via email spam
Cryptowall 3 ransomware is primarily, but not exclusively, spread via spam email. The email contains a zip file attachment which houses an executable file. If the executable file is run, it installs the malware on the host computer. Videos, text files, and images files are then encrypted with its RSA2048 algorithm. Users often have files created on the desktop instructing them how to unencrypt their computer. Once infected, users are given approximately 7 days to pay the ransom, which is commonly $500 in the form of Bitcoins (2.17).
There is no guarantee that payment will result in the encryption being removed, although oftentimes it is. Payment certainly does not mean all traces of the malware will be removed from the infected machine. Users are often allowed to decrypt certain files to prove that the criminals behind the campaign can actually make good on their promise.
Victims are usually given little alternative but to give into the hacker’s demands, unless they want to lose all the files that have been encrypted.
Millions have been obtained from Cryptowall 3 ransomware infections
Cryptowall 3 ransomware has spread rapidly and the malware has already claimed tens of thousands of victims. The malware was only discovered in January 2015, yet already the criminals behind the infections have managed to obtain an estimated $325 million in ransoms according to Cyber Threat Alliance (CTA) figures. The ransoms have been tracked via Bitcoin payments, although the system used to assess criminals’ profits is somewhat unreliable. The figure of $325 million has been confirmed, but the total profits from Cryptowall 3 ransomware infections could well be double that total.
Cryptowall 3 ransomware infections usually start with a phishing campaign. The phishing campaigns usually contain an attachment with an innocent looking name, such as “invoice” or “fax”.
Drive-by attacks have been known to install the malware. These take advantage of security vulnerabilities in browser plugins. Exploit kits such as Angler are also used.
Fortunately, it is possible to train employees to be more cautious and not to open file attachments sent from unknown individuals. However, the emails may appear to have been sent by a friend, relative, or colleague inside their company.
Training should be provided to employees and company-wide warnings issued. However, the best defense is to prevent the ransomware from being delivered to inboxes. If SpamTitan Anti-Spam solutions are implemented, Cryptowall 3 ransomware email spam will be blocked and quarantined. End users will then be prevented from accidentally installing the malware.
by G Hunt |
November 18, 2015 |
Spam News
Cybercriminals are using SSL certificates installed on fake domains to fool users into thinking that the websites are genuine. The websites often use names that closely resemble a well-known brand. We have previously reported that criminals have been using domains containing typos to obtain website traffic and fool the unwary; however, it is also common for domains to be purchased using a well-known company name with additional words added to the end.
Because the websites contain the brand name, many visitors will be fooled into thinking that the websites are genuine. This is even more likely if a website has a valid SSL certificate and displays a padlock next to the URL. This is seen as a sign by many consumers that the website is real. A SSL certificate can no longer be trusted. It is only one indication that a website is genuine. Many new websites are offered a free SSL certificate.
Electronic Frontier Foundation phishing scam brought to an end
One website that has been fooling visitors into thinking the site was official is believed to have been set up by the cybercriminals behind the Pawn Storm phishing campaign: A group of hackers known as APT28. The group, which has links to the Russian government, used the brand name of the Electronic Frontier Foundation as part of a phishing campaign.
The Electronic Frontier Foundation phishing campaign used a .org website with the domain name, ElectronicFrontierFoundation. The official site used by the company is also a .org, but just uses the company’s initials: EFF.
The Electronic Frontier Foundation phishing site was not used to obtain bank account or credit card details, instead it was used to spread malware. The fake site was discovered to contain malware that exploited a zero-day vulnerability in Java software.
Electronic Frontier Foundation was alerted to the existence of the website and issued a complaint to the UN’s World Intellectual Property Organization (WIPO) – an organization that helps protect the intellectual property rights of corporations. After assessing the compliant, WIPO ruled that Electronic Frontier Foundation was entitled to take control of the domain, which has been ordered to be transferred to the non-profit digital rights group. Once that happens, the site will no longer pose a threat and ownership will be transferred from an individual based in Bali, Indonesia.
Organizations believing their copyright has been infringed can attempt to claim a registered domain by following the Uniform Domain-Name Dispute-Resolution Policy (UDRP) set up by ICANN. However, it can take a long time for the process to be completed. All the time that a fake domain is active it can result in a loss of income for the company concerned. Many customers or potential customers could have malware installed or be defrauded until the matter has been addressed and ownership of the website transferred.
In a case such as this, the domain name and SSL certificate made the website appear 100% legitimate, which no doubt resulted in many people having their computers infected with the malware.
by G Hunt |
November 10, 2015 |
Spam News
Bermuda residents and holiday home owners have been put on high alert after a new BELCO email scam has been uncovered. A warning has now been issued by the company after some customers were targeted by scammers and were sent malware-infected emails from the company’s email domain.
BELCO, the Bermuda Electric Light Company Limited, supplies electricity to homes in Bermuda and is the only supplier in the British Overseas Territory. All individuals who own or rent a property on the islands are at risk of receiving a spam email that could potentially infect their computer, mobile phone, tablet or laptop with malware.
The type of malware sent in the spam emails is a form of ransomware. This type of malware is particularly nasty as it will allow the perpetrators of the campaign to lock files on an infected computer and potentially also on a business network to which the device connects. The malware delivered in the BELCO email scam can also cause corruption of computer files. The criminals behind the campaigns have designed the malware to give victims little choice but to pay the ransom.
Critical files are encrypted via the ransomware to prevent the user from gaining access. The only way of regaining access to the files is by restoring them from a backup or by paying a ransom to the criminals behind the campaign. Once a ransom has been paid, the criminals behind the BELCO malware attack will supply a security key that can be used to unlock the data. There is no guarantee that the security key will be provided once the ransom has been paid and it is conceivable that the criminals could continue to extort customers who give into their demands.
On a personal computer, files such as personal documents or family photographs could potentially be encrypted and lost. For business users the risk is even higher. Without access to critical files, all business could effectively grind to a halt. Even when a backup can be used to restore the ransomware-encrypted files, significant losses could be suffered. Performing a full restoration of data takes time and unless a backup was made just minutes before files were encrypted, some data will invariably be lost. Customers will also experience disruption to services while remediation takes place and systems are restored.
BELCO email scam uses legitimate company domain
The BELCO email scam uses a common technique to fool targets into installing malware on their devices. Criminals have been using email to deliver malware for many years, but they are now getting very good at creating highly convincing campaigns. It is becoming much harder to identify a spam email containing malware.
What makes this campaign particularly convincing is the emails appear to have been sent from the BELCO.bm domain. Even an individual who has adopted email security best practices, such as checking the sender’s address before opening an attachment, may be fooled into installing the malware contained in the email.
The email informs the recipient of an unpaid electricity bill and includes a warning that electricity will be cut off if the bill is not paid promptly. In order to find out how much money needs to be paid customers are required to open the attachment. Doing so will result in the malware being installed.
The email was sent from the address billerz @belco.bm. The domain is correct, although there is no official billerz address used by the electricity company. A warning sent to customers advises that any legitimate bill sent by the company will come from ebilladmin @belco.bm.
Simply receiving the email will not infect a computer but it is imperative that the attachment is not opened under any circumstances. Any customer receiving the email should delete it immediately from their inbox or spam folder. They should then ensure it is also deleted from their deleted email folder.
Identifying spam and scam emails
The BELCO email scam is convincing. It could easily pass for a genuine email if the recipient of the email is not particularly security conscious. There are tell-tale signs that it is a fake.
- The email address differs from the one usually used by the company to send electronic electricity bills
- There is a threat contained in the email – Immediate action is required to avoid unpleasant consequences
- Insufficient information is included in the email body, requiring the user to open an attachment
- The email address contains an odd spelling not typically used by a reputable company – billerz
Individuals, and especially companies, should consider implementing additional controls to prevent emails such as this from being delivered. Using a spam filtering solution will prevent the vast majority of spam and scam emails from being delivered. As more phishing and spam emails are being sent, and the perpetrators are becoming more skilled at creating convincing campaigns, this is one of the best defenses to prevent accidental malware infection. The cost of an Anti-Spam solution will be considerably less than the cost of a ransom to unlock vital data.
by G Hunt |
October 23, 2015 |
Spam News
Softlayer Rated Biggest Spam Hosting ISP by Spamhaus
According to a new report by the not-for-profit anti-spam organization, Spamhaus, the biggest spam hosting ISP is Softlayer, the IBM-owned cloud computing provider. A reported 42% of the ISP’s outbound emails have been discovered to be spam.
The report, issued on Wednesday, shows the ISP to be the current biggest offender, found to be supporting spammers and hosting numerous malware operations. The extent of the company’s emails found to be spam is astonishing, making it the undisputed champion of spam. Spamhaus has recorded over 685 separate spam issues on Softlayer, almost three times as many as the ISP in second place, Unicom-sc, which has had 232 reported spam issues.
Typically, the biggest web hosting companies and internet service providers do not feature so highly in the spam list, as they tend to employ numerous measures to prevent their servers being used by spammers and internet criminals. While Softlayer has not featured so highly in the past, recently it has been rising up the rankings, even though it does make efforts to fight spammers and implements controls to prevent them from using its servers.
In recent years the company has increased efforts to keep spammers at bay, and has taken firm, decisive action when reports of spamming have been received. But this has not proved to be sufficient.
It would appear that the ISP is now being targeted by Brazilian cybercriminals who are using its services to send out high volumes of spam emails and host numerous malware-infected websites. Softlayer is understood to have relaxed its criteria and vetting processes recently in an effort to attract more business; which does appear to have been successful, albeit for the wrong kind of business.
Spamhaus also pointed out that it has received requests to have Softlayer removed from its listing, but will only do so when it is clear that all of the issues have in fact been resolved. Spamhaus pointed out that cyber-criminals from Brazil were so active that “many listed ranges were being reassigned to the same spam gang immediately after re-entering the pool of available addresses.” The report went on to say, “these specific issues would not be removed until Softlayer was able to get control of the overall problem with these spammers.”
Softlayer has responded to the new number 1 ranking, saying affirmative action is being taken to tackle the issue. Communications Director, Andre Fuochi, recently told Krebsonsecurity, “We are aggressively working with authorities; groups like The Spamhaus Project, and IBM Security analysts to shut down this recent, isolated spike.”
Unfortunately, while action is being taken, it is not fast enough to stop the spammers. As soon as accounts and websites are shut down, more are created. Users are able to provision and de-provision sites and applications cheaply and quickly, which is why the ISP is struggling to stop spam emails from being sent and malware sites from being created.
Cloudmark recently confirmed Spamhaus’s rating, saying the Softlayer network was the largest single source of spam in the world during the third quarter of this year. The spammers and scammers will always find a home somewhere, but to find it at a company owned by IBM must come as a major embarrassment. IBM is, after all, a major player in the software security market.
by G Hunt |
October 21, 2015 |
Spam News
A bank phishing scheme operated by a Moldovan man has resulted in $3.55 million being transferred from the bank accounts of a Pennsylvania mining company – the Penneco Oil Company Inc. – according to federal prosecutors.
The perpetrator of the campaign, Andrey Ghinkul, 30, has been charged following his recent arrest in Cyprus. He is awaiting extradition to the United States, with a hearing scheduled for next week.
The phishing campaign was sent out to numerous companies, with a number of recipients reportedly opening the email, only to have their computers infected with Bugat malware. Bugat Malware is a little known form of malware, operating in a similar fashion to the well-known Trojan Zeus.
Bugat malware functions as a SOCKS proxy server, allowing hackers to directly download and execute programs on an infected host’s computer, or upload files to remote servers. In order to escape detection, the malware communicates encrypted data with its command, and by doing so fails to trigger many traffic inspection software warnings.
The malware has been used to log information entered during online banking sessions, with Firefox and Internet Explorer browsers so far exploited. With the information obtained, hackers are able to make fraudulent wire transfers and ACH transactions. So far, small to mid-sized businesses have been most commonly targeted.
While many organizations are now looking out for Zeus infections, this new form of malware can escape detection more easily. The attacks also show how cybercriminals are diversifying their attacks in order to gain access to financial account information and avoid detection.
The phishing campaign was used to send emails to a number of recipients in U.S companies, with the emails appearing to have been sent from medical providers, indicating the recipients had received a positive diagnosis for cancer.
Bugat Malware Bank Phishing Scheme Nest Hackers Over $10 Million
According to the FBI, Bugat malware has resulted in around $10 million in funds being transferred from U.S company accounts to hackers in Russia and Belarus.
The transfers from Penneco Oil’s accounts were made possible by the malware, which recorded bank passwords as they were entered on the infected computer. That information was then used to make the transfers. The first transfer of $2.2 million was made in August 2012, with the funds being received by a bank based in Krasnodar, Russia. A second transfer was made the following month, this time the recipient account was in Minsk, Belarus.
While the transfers did go through, action was swiftly taken by the bank – Indiana, PA-based First Commonwealth – and the funds were rapidly restored. Senior Vice President of Penneco, D. Marc. Jacobs, said the bank “worked to completely restore our funds almost immediately.” In this case, Penneco had all funds restored and the bank had to cover the cost.
Should Ghinkul be extradited, the case will be heard in Pittsburgh where another attempted victim was targeted. Sharon City School District nearly lost $999,000 to a Russian account. Fortunately, that transaction was successfully blocked.
by G Hunt |
October 19, 2015 |
Spam News
A new iTunes email scam has been uncovered which attempts to trick users into revealing their credit card numbers, according to a recent report issued by Malwarebytes.
The latest iTunes email scam targets users of iTunes and offers them a refund for a purchase that has been made using their iTunes account, indicating they have been affected by an email scam already. In order to receive the refund, the users must provide their Apple ID, password, and credit card details so the refund can be processed.
Emails have been sent to iTunes account holders telling them that their account has been fraudulently used to purchase an app valued at £34.99 ($53), with the emails containing a fake receipt for the purchase. The app is question is provided by CoPilot Premium HD, a supposed navigation service. The receipt contains a link that the recipient of the email must click in order for their refund to be issued, if the purchase is not genuine.
There is of course no such app, and the high price is perhaps a warning that something is amiss. Unfortunately for users looking to protect themselves from fraud, the very actions they take to protect themselves will actually ensure they do become victims.
Not the Only iTunes Email Scam Recently Uncovered
This is not the only email phishing scam to have been sent to Apple users in recent weeks. Another email spam campaign attempts to get users to click a link to update their credit/debit card, which users have been informed in the email is about to expire. Users have been requested to click a link and enter their new card details, including the CSC code on the reverse of their card, as well as the new expiry date.
As with many email scams of this nature, the email is sent with a threat of account suspension if they do not comply. In this case, users have little time to respond. The email link is said to expire in one hour’s time if it is not clicked, reducing the time for users to verify if the email is in fact genuine.
They are provided with a link to store.apple.com which is seemingly genuine; however, hovering over the link will reveal that the link directs them to a different location.
There are other common tell-tale signs that the email is a fake, even though the correspondence does contain seemingly genuine Apple imagery and appears to have been sent from Apple’s customer service department. One of the most telling signs is the volume of spelling mistakes contained in the email. Any email sent by Apple is likely to have at least been run through a spell check before being used as a template for millions of Apple device owners. A sure sign that the email is not genuine.
The email contains spelling and grammatical errors such as informing the recipient that the link will “expire one hours after the email was sent.” iPhone “ore” iPads is another, and feature is spelled “feauter.”
The advice to all Apple users is to take time to carefully read any email sent from Apple, and to attempt to verify any request to provide ID numbers or financial information.
by G Hunt |
October 16, 2015 |
Spam News
It has now been over a year since the U.S Postal Service was affected by a phishing campaign that resulted in the exposure of the personal information of 800,000 current and former workers, yet the postal service is still not effectively dealing with the phishing threat. Employees have been tested, and they are not identifying phishing emails.
Postal Service Employees are at Risk of Falling for Phishing Emails
The network data breach of 2014 occurred as a result of employees falling for spear phishing campaigns, which allowed criminals to gain access to postal service networks containing sensitive data. The data thieves were able to gain access to the network and exfiltrate data without meeting much in the way of resistance. It would appear that if a similar campaign was conducted again now, even more data may be exposed.
The Office of the Inspector General (OIG) recently took the decision to put postal service workers to the test, to determine whether lessons have been learned since last year. In total, 3,125 fake phishing emails were sent to employees of the U.S Postal Service to determine whether they were actually able to identify a potential phishing campaign.
There was some good news. 75% of workers were able to resist the temptation to click on the phishing links in the emails. The bad news was 25% did click. Unfortunately, all it takes is for one person to respond to a phishing email for criminals to gain access to data. 780 responses to fake phishing emails shows risk is not being effectively managed.
However, perhaps worse still, was the lack of compliance with policies that had been put in place in the wake of last year’s successful attack. For instance, the postal service’s Computer Incident Response Team should be alerted if a suspicious email is received by workers, yet only 7% of employees did so during the test.
The reason is perhaps quite easy to explain. Only 4% of staff had completed the Postal Service cybersecurity training course, so presumably were unaware of the policy of reporting suspicious emails, if they were in fact able to identify them as suspicious.
OIG Report Shows Postal Service is Not Dealing with the Phishing Threat
The OIG report on the cybersecurity test stated that awareness training does have a positive impact, and can substantially reduce the risk of employees responding to a phishing campaign. Research shows training can reduce security-related risks by as much as 70%.
Policies must of course be turned into procedures, and the staff must receive training. The OIG said, “When management does not require all employees with network access to take annual information security awareness training, users are less likely to appropriately respond to threats.”
One of the main problems for organizations trying to tackle the threat of phishing is the fact that criminal organizations and hackers are developing ever more complex and convincing campaigns to fool users into opening malware-infected attachments and visiting links to malware-infected websites. However, if training is not provided to the staff, even uncomplicated phishing campaigns could well succeed.
At present, only new members of staff and CIO office members are required to undergo annual cybersecurity training: That is not the most effective way of dealing with the phishing threat. However, in response to the OIG report, the Postal Service will be implementing new training policies by April 2016.
by G Hunt |
October 14, 2015 |
Spam News
The Federal Trade Commission has issued a warning over a new gaming email phishing scam that targets video game players and takes advantage of their love of the games to get them to divulge their account information.
Gamers invest considerable time and money into buying add-ons and developing gaming characters; however, the fear of loss of their gaming account is seeing many fall for the latest scam.
Cyber Criminals Opt for Gaming Phishing Email Scam
Hardcore gamers are not difficult to find, having registered on forums and gaming websites, providing their email addresses and other information about their gaming habits. Once criminals obtain email addresses of gamers, they are sent fake emails from gaming companies suggesting they have been discovered to have sold gaming items or characters for real money, and by doing so have violated the rules of the game.
Consequently, the users are threatened with account suspensions, or in some cases, legal action. A number of emails have been received by gamers with threats that they will be sued for amounts up to $2,700 for repeated violations of gaming rules and regulations. The intention is not to get the users to part with that money, but to get them to reveal details of their bank accounts or credit cards used to make purchases.
Users are often fooled into responding out of fear of losing their accounts or being suspended or banned from their favorite games. The email campaigns can also be highly convincing, using templates that appear legitimate, often including company logos and names the users may be familiar with.
The scammers have been targeting users of some of the most popular online games, such as World of Warcraft and Diablo III, both produced by Blizzard Entertainment, although the scam is not restricted to players of these games. The volume of emails sent to gamers, and complaints received, has resulted in Blizzard emailing users to tip them off to what it called “rampant scams.”
The FTC has also got involved, issuing a warning of its own. According to the FTC warning, targets are advised that they should check the status of their accounts and challenge the suspension if they have done no wrong. They are supplied a link for this purpose and are required to fill in a ‘verification’ form.
They are then asked to enter information in order to confirm their accounts and identities, and must reveal account and financial information. The perpetrators of the scam then empty their accounts.
This is not the only technique used by online fraudsters to get users to reveal their credentials. Gamers are being sent spam emails asking them to login in order to receive free gifts and exclusive game add-ons, with users requested to click a link in the email to login in order to claim their prize.
It is not always essential that account details are entered in the online forms to which the users are directed to. The links contained in the emails can direct the users to malware-infected websites. Malicious software is automatically downloaded to the users’ computers, allowing the perpetrators to gain access to the device and trawl files looking for personal information such as bank account details, login names and passwords.
Gamers have been warned to always try to verify any such emails, and not to click on links, open attachments or use the contact details provided. All requests that are out of the ordinary should be independently verified with the company concerned, using the gaming website’s contact information.
by G Hunt |
October 12, 2015 |
Spam News
There has been some good news reported recently that indicates email spam levels are now at the lowest point seen in the past 12 years. According to a report issued by Security company Symantec, spam emails fell to 49.7% of all emails sent in June this year. Spam email levels fell further still in July, dropping to 46.4% of total email volume. Symantec also reported that the volume of phishing campaigns also saw a fall in June.
A number of reasons have been cited for the fall in spam levels, including bringing a number of spammers to justice and closing down their criminal networks, in addition to shutting down a number of rampant botnet networks, many of which were located in the United Kingdom.
The botnets were identified by UK police forces which orchestrated a number of takedowns. UK and European internet service providers had been collaborating with the police and passed on information on suspected botnets, helping to reduce the effectiveness of the networks, ultimately leading to many being shut down.
While this is good news, this does not mean there has been a reduction in risk. Phishing schemes may have seen a small drop in June, but the number of malware variants now being discovered has increased dramatically. The variation in malware is causing a problem, as the malicious software is becoming harder to identify. The extent of the increase in variants is considerable. In just two months the number of malware types had almost doubled from 29.2 million in April to 57.6 million pieces of malware caught by Symantec in July. This is the second highest figure reported in the past 12 months, with only November 2014 seeing more malware attacks caught (63.6 million).
The attack landscape is constantly changing, with cybercriminals now diversifying their attack vectors. Ransomware for instance, is becoming more popular. Just under half a million attacks (477,000) were thwarted by Symantec in June, with the volume of ransomware having risen for two months in a row.
While cyber criminals based in the UK and United States may be diversifying attack vectors, hackers in other countries still favor email spam, with eastern Europe and China still seeing huge volumes of spam emails being sent. It is certainly not a time to let one’s guard down or become complacent about email spam.
Businesses Still Receiving High Volumes of Spam Emails
Overall, levels of spam may have fallen, but small to mid-sized companies are still seeing high levels of spam emails received, with the percentage of spam emails remaining above 50%. Spam email traffic to small to medium companies (those with one to 250 employees) stood at 52% in June.
Malicious emails are also still being used extensively to target organizations of all sizes. In June, malicious emails were being most commonly used against companies employing 1501-2500 individuals, with one in 164 emails recorded as being malicious in nature.
In July the figures had improved, with organizations employing 251-500 individuals the most common recipients of malicious emails, registering one email in 260 as being malicious in nature, closely followed by small organizations employing under 250 individuals, with one in 275 emails rated as malicious.
Spam emails were still being sent at high levels to particular industries, with mining and manufacturing industries receiving high levels of spam in June. Over 56% of emails received in the mining sector were spam, with the manufacturing, construction, retail and non-traditional service industries all registering spam email volumes of 53% or more in June.
The figures for July actually showed an increase in spam for some industry sectors. Mining had increased to 55.7%, with only very slight falls in spam levels in other industry sectors. Manufacturing, retail and construction all registered spam percentages above 53%.
Each of the other 6 industry sectors (Professional services, agriculture/forestry/fishing, wholesale, non-classifiable establishments, finance/insurance/real estate, and non-traditional services) all registered spam email percentages of between 51.9% and 52.5%, indicating email spam remains a major problem for most U.S. businesses.
by G Hunt |
October 9, 2015 |
Spam News
The Ponemon Institute has released a new report detailing the cost of phishing attacks on U.S businesses, suggesting the average annual cost for U.S companies has now risen to $4 million. Ponemon calculated phishing attacks take an average of 23.7 days to resolve, and are having a huge impact on U.S organizations, with smaller companies often suffering the most.
Cost of Phishing Attacks & Cyber Crime Assessed
The report indicates that the biggest costs suffered as a result of cyber crime come from phishing campaigns and social engineering, which accounted for 16% of total cyber crime costs. Phishing and social engineering were found to have affected 59% of organizations, while botnets affected 66% and web-attacks were suffered by 76% of organizations.
The Ponemon study, conducted in conjunction with HP Enterprise, involved a representative sample of 58 private and public sector U.S organizations being surveyed on cyber crime and the costs of dealing with criminal attacks. The results of the study show that in the U.S, the mean annualized cost of cyber crime has risen to $12.7 million per year, with the highest total average cost of dealing with cyber crime being $15.42 million – more than double that of Germany in second place.
The study showed that organizations are having to pay between $1.6 million and $61 million per year to resolve cyber attacks. The cost of the dealing with those attacks was found to be higher for larger organizations, although the per capita costs were highest for smaller organizations.
The new 2014 Cyber Crime Report shows the cost of dealing with attacks has risen 19% in just 12 months, with the global average cost of cyber crime estimated to have exceeded $7.7 million. Some companies are having to cover costs of up to $65 million to resolve criminal attacks, which were shown to have increased in both frequency and severity during the past 12 months. Email attacks remain one of the biggest causes for concern, being one of the main methods used by criminals seeking access to computer networks.
Phishing Emails Are Proving to be Highly Effective
Earlier this year, communications company Verizon produced a report indicating phishing campaigns can be highly effective methods of attack, and suggested that all too often staff training efforts are not particularly effective. Many organizations are now providing staff with information on how to identify phishing emails, yet this information does not appear to be retained. The study found that 23% of individual who received a phishing email opened it, and an alarming 11% of recipients clicked on the link contained in the email or opened the attachment.
The provision of training manuals on phishing to employees can be effective, but retention of information tends to be poor. The Ponemon study did suggest that one of the best methods of training staff how to identify phishing emails is to provide examples, indicating the sending of simulated phishing emails was particularly effective at reinforcing training, providing up to a 37% return on investment.
With phishing emails representing such a substantial proportion of cyber security costs, and training proving not always particularly effective at substantially reducing the risk of attacks being successful, greater efforts should be put into intercepting phishing emails and preventing them from being delivered to recipients’ inboxes. For that, a robust and effective email spam filter is required.
by G Hunt |
October 8, 2015 |
Spam News
Although many reports suggest that email spam is reducing, email spam and botnet infection is still a major issue for most U.S organizations and individuals – with criminal practices netting cybercriminal gangs billions of dollars every year.
Determining the infection levels and the volume of spam being sent was one of the missions of the Messaging, Malware and Mobile Anti-Abuse Working Group (M3AAWG). M3AAWG, is a global organization tasked with promoting cybersecurity best practices and fighting organized internet crime. M3AAWG was formed a decade ago by a number of leading internet service providers, with the goal of improving collaboration and sharing knowledge to make it harder for criminals to spam account users. By reducing the impact of email spam on individuals and organizations, ISPs would be able to better protect users, IPS’s email platforms and their reputations.
Quantifying Email Spam and Botnet Infection a Complex Task
It was discovered that quantifying email spam and botnet infection levels was a complex task; one that was only possible with collaboration between internet service providers. As a result of this collaboration, the organization has produced reports on the global state of email spam and botnet infection. Its latest analysis suggests that approximately 1% of computer users are part of a botnet network.
The data gathered by M3AAWG involved assessing 43 million email subscribers in the United States and Europe.,The data analysis showed that IPS’s typically block between 94% and 99% of spam emails. The company’s report suggests that on the whole, IPS’s do a good job of blocking email spam.
The figures look impressive but, considering the huge scale of email spam, billions of spam emails are still getting through to users, with financial organizations and other companies now being regularly targeted with spam and malware.
Email spammers are well funded, and criminal organizations are using email spam as a means of obtaining tens of billions of dollars each year from internet fraud. Spam emails are sent to phish for sensitive information, such as bank account information, credit card details and other highly sensitive data including Social Security numbers. Accounts can be emptied, credit cards maxed out and data used to commit identity theft; racking up tens of thousands of dollars of debts in the victims’ names.
In years gone by, email spammers concentrated on sending emails randomly to accounts with offers of cheap Rolexes, Viagra, potential wives and the opportunity to claim an inheritance from a long lost relative. Today, spammers have realized there are far greater rewards to be had, and emails are now sent containing links to malware-infected websites which can be used to compromise users’ PCs, laptops and Smartphones, gaining access to highly sensitive data or locking devices and demanding ransoms.
Some emails may still be sent manually, but the majority are sent using botnets. Networks of infected machines that can be used to send huge volumes of spam emails, spread malware or organize increasingly complex attacks on individuals and organizations. The botnets are available for hire, with criminals able to rent botnet time and use them for any number of reasons.
Many of the attacks are now coming from countries where there is little regulation and a very low risk of the perpetrators being caught. Countries in Africa, as well as Indonesia and the Ukraine house huge volumes of cybercriminals. They have even set up call centers to deal with the huge volume of enquiries from criminals seeking botnet time to orchestrate phishing and spamming campaigns. Tackling the problem at the source is difficult, with corruption rife in the countries where the perpetrators reside.
However, it is possible to reduce spam level, and the risk of employees falling for a scam or downloading malware by installing a robust email antispam filter, reducing the potential for spam emails and phishing campaigns getting through to individual accounts. According to Verizon, 23% of users open phishing emails and 11% open attachments and click on links. Stopping the emails from reaching users is therefore one of the best methods of defense against attacks.
by G Hunt |
October 6, 2015 |
Spam News
Lawyers representing plaintiffs affected by spammy marketing practices by business networking website LinkedIn have reached a $13 settlement in a California court, with the LinkedIn email spam lawsuit likely to result in users of the website receiving a payout of around $10 per person.
Lawyers argued that the marketing practices used to attract new users breached California’s common law right of publicity and constituted unfair competition, with millions of users having had their privacy violated. The class-action lawsuit was filed in September 2013 and lasted two years before LinkedIn agreed to settle the case without admission of liability. LinkedIn claimed no wrongdoing and that its business practices broke no laws.
Alleged Spammy Marketing Practices used by LinkedIn to Attract New Users
Users of LinkedIn are permitted to import contacts from email accounts such as Gmail. Users electing to “Add Connections”, will generate an email that is sent to their contacts list inviting those individuals to connect and sign up for an account with the website.
Site users were asked before emails were sent to their imported email contacts, but they were not advised about a further two emails that were triggered if their contacts did not respond to the original email request within a fixed period of time. The follow-up emails were reminders that the invitation was still waiting for approval.
The lawyers claimed that LinkedIn had been “breaking into its users’ third-party email accounts, downloading email addresses that appear in the account, and then sending out multiple reminder emails.” The case centered on the fact that users were not advised that this would be the case. It was claimed that the website was using the names and likeness of users to drum up more business without consent, thus breaching the privacy rights of site members.
Last year, LinkedIn petitioned U.S. District Judge Lucy Koh requesting the case be dismissed, as users had in fact given their consent for contacts to be sent emails; however, Koh ruled that while consent had been provided for one email to be sent, users had not given LinkedIn consent to send any further emails if individuals did not respond to the initial request to join the website.
Other claims made against LinkedIn were rejected, such as the breach of federal wiretap law and claims of hacking users accounts. As a result, the case was required to be resubmitted.
LinkedIn Users Invited to Submit Claims for Compensation
The LinkedIn email spam lawsuit has now been settled, although users of the site are unlikely to receive much in the way of compensation. Any user who used the Add Connections feature of the website between September 17, 2011 and October 31, 2014 have now been invited to submit claims, and have until December 14, 2015 in order to do so.
Due to the volume of individuals affected, it is probable that the payout for each affected user will be around $10. LinkedIn has agreed to add further funds – $750,000 – if the volume of claims it receives results in individuals qualifying for a payout of less than $10 a head. Linked in will also be required to cover legal fees in addition to paying the $13 million settlement.
From the end of the year, all users of the “Add Connections” feature will be informed that by doing so, they are giving their consent for their imported email contacts will be sent one email, and up to two follow-up emails if no response is received from the initial request. There will also be a new option added which will allow invitations and reminder emails to be stopped.
by G Hunt |
October 1, 2015 |
Spam News
The threat from phishing emails is causing Health IT professionals major headaches, and is one of the main data security concerns according to a recent HIMSS cybersecurity survey. The recent HIMSS survey was conducted on 300 healthcare IT security professionals and suggests that the increase in phishing emails is one of the main reasons why the healthcare industry is having to invest so heavily in data security. 69% of survey respondents believed that to be the case.
Phishing campaigns are now being devised that are difficult to identity, with cybercriminals investing considerable time and effort into creating highly convincing emails in an attempt to get healthcare employees to divulge their login credentials.
Threat from Phishing Keeps CISOs Awake at Night
Criminals may still be sending random email spam in an attempt to obtain credit card details and banking information, but healthcare providers are now being increasingly targeted for the high volume of Social Security numbers and other personal patient information held; data that can be easily used to commit identity theft and obtain far more than is possible with credit card numbers. According to HIMSS Senior Director of Research Jennifer Horowitz, phishing is now “the number one thing that keeps CISOs up at night.”
The survey showed that data security has become one of the main business priorities for healthcare organizations, with 87% of respondents claiming data security has increased in priority over the course of the last year. Out of the respondents that said data security is a main priority now, two-thirds believe phishing to be the main cause for concern, and the same volume of respondents claimed their organizations had already suffered a phishing or other online scamming attack.
Phishing is a technique used by cybercriminals to obtain personal information, and is used as part of a wider attack on a corporate network. If users can be convinced to visit a link to a website or open an attachment, malware is downloaded to their device. A third of survey respondents indicated they have already become the victim of such an attack this year.
One problem faced by the healthcare industry in particular is the tactics used by criminals frequently change. Phishing was a technique most commonly associated with mass spam emails sent by individuals in the hope that some email users would fall for the scams. It would appear that now individuals, or specific groups of individuals, are being targeted. Many criminals now opt for quality over quantity, and are devising campaigns to target individuals with access to the data they seek. These “spear phishing” campaigns can prove to be highly effective.
Tackling the Threat from Phishing Emails
Efforts are being made by healthcare organizations to reduce the risk of individuals falling for campaigns. Spam filtering can be effective at limiting the volume of emails that make it through to the inboxes of healthcare workers, and training is now being provided to staff to help individuals recognize the signs of a phishing email. However, it would appear that while training is sometimes provided, this is not subsequently tested in many cases. Phishing email exercises designed to test users’ ability to identify phishing campaigns are still not being used by the majority of healthcare organizations. Only a quarter claimed they are using exercises to test staff readiness to deal with the threat, and that is a recipe for disaster.
by G Hunt |
September 9, 2015 |
Spam News
A new Netflix phishing scam has been uncovered which works by telling users their Netflix accounts have been closed, requiring action to regain access to the service. Doing so will give your confidential login details to the scam operators.
Netflix has 62.27 million users, making it a highly attractive target for email scammers and spammers, and consequently Netflix phishing scams are common.
Latest Netflix Phishing Scam Convinces users to Reveal their Account Details
Recipients of the fake Netflix emails are required to click a link in order to reactivate their accounts. Unknown to the victims of this Netflix phishing scam, clicking on the link will direct them to a fake Netflix page, and by reactivating their accounts they will be giving the scammers their account names, passwords, and potentially other sensitive information.
Unfortunately for Netflix users, revealing passwords for one account may also mean other online accounts are compromised. Many users share their passwords across different websites, often using the same or similar passwords for Netflix, Facebook, and a host of other sites, including online banking portals.
TitanHQ recommends Netflix users ignore the email and delete it, and certainly do not to click on the link in the email. Phishing scams such as this usually direct users to a website that has been infected with malware, and clicking the link will result in that malware being downloaded, even if no information is entered on the page.
The best course of action is to login to your Netflix account as you would normally do, by typing in the URL or using your bookmark, and check your account status directly with Netflix. In all likelihood, it will still be active.
Further Information on the New Netflix Phishing Scam
Below is a screenshot of the latest Netflix phishing scam. The email appears genuine enough, although close inspection will reveal a few grammatical errors, such as missing apostrophes and misplaced exclamation marks. However, the email could be enough to fool the unwary, and especially individuals who tend to skim read emails and click first and think later.
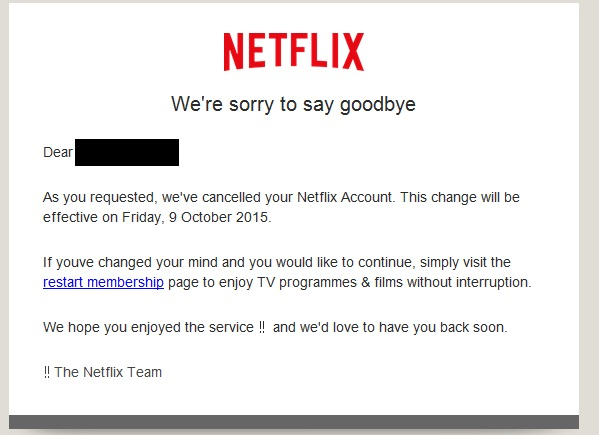
This phishing campaign is similar to others that have been recently sent to users of other online services. Phishing emails are devised to give the recipient a legitimate reason for handing over sensitive information, usually via webpage.
These include, but are not limited to:
- Upgrading security settings
- Performing essential system maintenance
- Verifying account details to prevent fraud
- Claiming a refund for a bill that has been paid
- Giving money back for an incorrect charge
- Offering you a free gift or service
Email scams often deliver malicious programs – malware – that has been created to steal confidential data such as account login names and passwords. Phishing campaigns are launched on social media, although email is the most common way that these scams are delivered.
Generally speaking, phishing campaigns can be categorized in three types:
Off-the-Shelf Jacking Toolkits
Criminals can purchase malware online which can be used to scam users into revealing passwords, which can subsequently be used to empty bank accounts, rack up debts, or hold people to ransom (the latter is becoming increasingly common and is referred to as ransomware). Once access is gained to an account or computer, Ransomware is used to encrypt data. The users are then required to pay a ransom to the perpetrator of the scheme in order to get their data unlocked.
These campaigns are usually opportunistic in nature, and involve millions of spam emails being sent. It is a numbers game, and some users will click on the phishing links and compromise their computers and networks.
Zero-day Vulnerability Exploits
The net is also cast similarly widely with these email phishing campaigns; however, the malware delivered is more complex, and the hackers behind these schemes are considerably more skilled. Zero-day vulnerabilities are new security flaws that have been discovered in software that have yet to be discovered by the software vendor. Consequently, patches do not exist to deal with the threat. Malware is created to exploit these vulnerabilities, which is usually delivered via an infected email attachment, although it can be downloaded when users visit a phishing website.
Spear Phishing Campaigns
These are targeted attacks that are conducted on individuals, or in some cases, organizations. The perpetrators of these schemes are skilled, and invest considerable time and effort into creating convincing campaigns. Oftentimes extensive information is gathered on the targets prior to the phishing emails being sent.
These schemes similarly use zero day vulnerabilities, and these advanced persistent threats (APT) have been used in a number of high profile attacks, such as the recent Carbanak malware attacks which have made the headlines recently.
How to Avoid Becoming a Phishing Victim
The best defense against attack is to be vigilant. Security awareness training for employees is essential. Staff members must be alerted to the risk, the consequences of clicking on a phishing link, and told how to identify scams. They should be instructed to check links before clicking (by hovering the mouse arrow over the link to check the real address).
It is also essential to keep all software patched and up to date. This applies to operating systems, applications, web browsers and other software. Software should be configured to update automatically wherever possible. Organizations should also develop concise patch management policies. Continuous security audits should be conducted and multi-layered network security controls developed.
There are a number of ways that spam and phishing emails can be prevented from being delivered to users, such as using a spam filter. Web filtering is particularly useful in prevent users from visiting known malware and phishing sites.
by G Hunt |
August 26, 2015 |
Spam News
In 1998, ICANN issued the first domain names and IP addresses. There were not many top level domains (TLDs) to choose from. Each country had its own domain suffix, but the choice was limited to .com, .org, .net, .edu, .mil and .gov. Over the years, a few more options have been introduced such as .me, .mobi, .tv and .biz, but the suffix that has caused the most controversy is .xxx – a TLD intended for websites containing images of a sexual nature.
The .xxx TLD was seen as a method of introducing a red light district to the Internet, cleaning it up aside from a dirty corner that could be policed and easily blocked. Some purveyors of pornography allegedly welcomed the move, while others were opposed to it.
There were protests, but the new TLD was released in December 2011, and ICM Registry – a Fort Lauderdale for-profit business – was assigned responsibility for allocating the TLDs. Incidentally, the contract for this was quite lucrative. ICM Registry expected to make in the region of $200 million per year out of the deal.
Sometimes a good idea on paper doesn’t always work out so well in practice. For instance, some companies had spent a long time building up a brand name. They operated their domain on the .com domain, had bought up the .net, .mobi, .org versions and all other TLDs to protect their brand. They did not like the idea of having to do that again with the XXX version, and neither would they be willing to move their main site over to the .xxx TLD.
Few were in favor of the new XXX TLD
Pornographers were not the only objectors to the introduction of the .xxx TLD. The Bush Administration was opposed to the release. In fact ICANN was asked to withdraw support for the proposal. Criticism of the proposal mounted and ICANN came under a considerable amount of pressure. The American Department of Commerce, that has power over ICANN, received over 6,000 complaints about the introduction of the .xxx TLD. Even politicians who had originally backed the idea in the year 2000 changed their mind a decade later. Naturally, conservative groups also applied pressure to block the proposal. It was not enough. The TLD was released – with a delay of a month – and a swathe of new porn websites were subsequently launched.
Unsurprisingly, there has not been a reduction in the number of .com porn websites on the Internet. The new domain has seen even more created. Go figure!
ICANN was subsequently sued on the grounds that it had created a monopoly and that the introduction of the TLD forced businesses to spend even more money registering domain names to protect their brands from being piggybacked. After a couple of years, the lawsuit was dropped.
Controls put in place to protect trademarks
ICM regulators created the new TLD in order to clean up the Internet apparently. The .xxx TLD was seen as a way to make it easier for people wanting to view pornography to find it (it wasn’t exactly difficult, it must be said – type “porn” into a search engine for example) and as a way of promoting a responsible attitude toward it. It would, in theory at least, eventually lead to a dedicated area where pornographic websites could be housed.
However, trademark and patent protection advocate Inventa pointed out that opposition to the new .xxx TLD was virtually universal. No one wanted it apart from ICANN (and ICM Registry).
As for the fears that domain-sitters and entrepreneurs would take advantage, there were controls to prevent this. Eligibility criteria needed to be met. A company owning the trademarked .com version of a website could purchase the corresponding .xxx TLD to use as an adult domain or to prevent others from using it. Amazon.xxx, for example, could only be bought by Amazon.com. The ICM Registry reserved it for them. If there was no trademark, the domain name could be bought by anyone.
Was it worth all the effort?
ICM Registry would be inclined to agree, but as for making the Internet a safer place for children, cleaning up some porn, and having a dedicated online red light district, that clearly hasn’t worked. The biggest names in Internet porn still use their dotcom websites and have not made the switch to XXX domains. People interested in viewing pornography do not need an .xxx TLD to be able to find it, and don’t care what the name of the website is let alone the TLD, provided it gives them what they are looking for.
It is no easier to block pornographic websites than it was before the release. Simply blocking access to XXX suffixed websites will make no discernable difference to the amount of porn that is viewable online.
Until laws are passed to force porn websites to use the XXX domain – which would be incredibly difficult to implement – the move has not been particularly effective.
The only way to block effectively access block pornography from being displayed is to use a web filter such as SpamTitan Technologies. By using real-time classification, URL filtering, blocklists, keyword filters and other tools, SpamTitan Technologies web filtering solutions prevent the websites from being viewable. Something very important for schools, universities, colleges, charities, and corporations.
Any organization believing written policies on allowable uses of the Internet are sufficient to stop inappropriate use, should bear in mind that surveys have revealed that 20% of men and 13% of women have admitted to downloading pornographic content while at work. A recent pool of 500 Human Resources professionals indicated two thirds had discovered pornographic content on work computers, and the majority of porn is viewed during office hours (between 9am and 5pm).
If you want to stop employees accessing pornography in the workplace, the only effective way of doing so is with a robust web filtering solution.
by G Hunt |
August 18, 2015 |
Spam News
Former employees of Kaspersky Labs have tipped off the media to an alleged practice of faking malware. It is claimed the company used fake malware to get rival anti-virus companies to flag the programs as malicious, potentially tarnishing their reputations with numerous fake positives.
For obvious reasons, the tip-offs have come from anonymous individuals who claim to have worked for Kaspersky Labs, yet their identities naturally cannot be verified. They could in fact be employees of rival anti-virus companies. It is therefore difficult to determine whether there is any truth in the allegations. Kaspersky Labs denied the allegations, in fact Eugene Kaspersky has been quite vocal on social media and has spoken out on Twitter, vehemently denying the accusations.
In an effort to find out more, we contacted Kaspersky Labs to find out further details. We received a reply as follows:
Kaspersky Denies Fake Malware Claims
“Contrary to allegations made in a Reuters news story, Kaspersky Lab has never conducted any secret campaign to trick competitors into generating false positives to damage their market standing. Such actions are unethical, dishonest and illegal.” Kaspersky went on to say, “Accusations by anonymous, disgruntled ex-employees that Kaspersky Lab, or its CEO, was involved in these incidents are meritless and simply false. As a member of the security community, we share our threat intelligence data and IOCs on advanced threat actors with other vendors, and we also receive and analyze threat data provided by others. Although the security market is very competitive, trusted threat data exchange is a critical part of the overall security of the entire IT ecosystem, and we fight hard to help ensure that this exchange is not compromised or corrupted.”
Interestingly though, there does appear to be a grain of truth in the accusations, with the anti-virus software giant confirming that harmless malware was in fact created and uploaded. However, this was part of a test of its own software systems, not an attempt to discredit rivals. The statement issued explained the experiment:
“In 2010, we conducted a one-time experiment uploading only 20 samples of non-malicious files to the VirusTotal multi-scanner, which would not cause false positives as these files were absolutely clean, useless and harmless. After the experiment, we made it public and provided all the samples used to the media so they could test it for themselves. We conducted the experiment to draw the security community’s attention to the problem of insufficiency of multi-scanner based detection when files are blocked only because other vendors detected them as being malicious, without actual examination of the file activity (behavior).” The story was reported at the time in the media.
Kaspersky also explained that “After that experiment, we had a discussion with the antivirus industry regarding this issue and understood we were in agreement on all major points.” Further information on cascading false positives can be found here.
“In 2012, Kaspersky Labs was among the affected companies impacted by an unknown source uploading bad files to VirusTotal, which led to a number of incidents with false-positive detections. To resolve this issue, in October 2013, during the VB Conference in Berlin, there was a private meeting between leading antivirus vendors to exchange the information about the incidents, work out the motives behind this attack and develop an action plan. It is still unclear who was behind this campaign.”
False positives are common in the internet security industry. What is not known, and probably never will be, is who creates the bad samples that lead to false positives. As Ronan Kavanagh, CEO at TitanHQ, points out,“Kaspersky is an excellent product, we have never had an issue with it, quite the opposite in fact. Of course we have seen false positives, we were targeted by bad samples as were many other security vendors but we would have no visibility on who carried out these attacks. The critical thing is that as an industry we work together in fighting back”.
Have you discovered false positives when you have run your software security programs?
by G Hunt |
July 29, 2015 |
Spam News
The threat to corporate data security is higher than ever, with hackers and other cyber criminals devising ever more complex ways of gaining access to company secrets, employee data, and protected health information. IT security teams now need to monitor and track new threats like never before. Phishing emails must be blocked, employees must be prevented from visiting malicious websites, audits must be conducted to check for malware and viruses, and systems protected against keyloggers and Trojans.
The volume of new malware now being discovered is enough to keep IT security professionals awake at night, with many fearing the security of their systems. IT budgets are strained enough as it is, and the rapidly changing threat landscape is placing those budgets under even greater strain.
What Information are Cyber Criminals Trying to Obtain?
Individual hackers may attempt to break through security defenses for any number of reasons, in fact their aims are not always financially motivated. A grudge may be held against an ex-employer. Business practices may be deemed to be questionable. A company’s carbon footprint may even make it a worthy target for attack. Often the aim is to sabotage, with unscrupulous business competitors willing to employ hackers to enable them to gain a competitive advantage.
However, in the majority of cases, cyber criminals attack companies for the data they hold, which can be sold on to the highest bidder on Darknet websites or used to obtain goods, services, or cold hard cash. Data carries a high value on the black market as it can be used for a myriad of different types of fraud.
Healthcare data can be used to fraudulently obtain medical services. Insurance data used to make bogus insurance claims. Social Security numbers can be used for identity theft or to file false tax returns, and credit card details used to rack up thousands of debts in victims’ names. Corporate secrets such as product development information can be obtained and sold to competitors. The theft of that information can be used by competitors to devastating effect.
Some cyber criminals are not interested in stealing data, just in preventing companies from accessing it. If ransomware can be installed, criminals are able to encrypt an entire system and hold the company to ransom. They will only release the security keys to unencrypt data if a ransom is paid.
How Are Criminals Obtaining the Data?
Spam emails and phishing campaigns (via email, social media networks and over the telephone) are common, although one of the biggest threats to data security comes from malware. If malware can be installed on computers or servers, it can record and exfiltrate data to the hacker’s control centers. All communications can be intercepted and all keystrokes recorded. This enables hackers to obtain login names and passwords: Those used to access internal systems or online bank accounts. It is not just corporate data that is at risk. Any information stored on clients and customers can also potentially be obtained by the attackers.
Common Hacking Techniques Used to Gain Access to Data
Some of the techniques used by hackers to gain access to data include:
Cross Site Request Forgery (CSRF)
Even apparently safe websites can allow hackers to install malware or access sensitive data. This type of attack involves legitimate websites sending requests to other sites. Twitter has suffered cyber attacks involving this method, resulting in logins and passwords of site users being obtained.
Web 2.0 Application Exploits
These attacks are difficult to prevent as they are often not identified by standard anti-virus defense mechanisms. They can exploit vulnerabilities in Adobe Flash, XML, JavaScript, JSON and Xpath to deliver malware and malicious code.
Cross-Component Attacks
Take two innocent looking sections of malware code that have been installed on a website. Individually they do no harm, and can easily evade detection. However, when two appear on the same webpage they interact and infect visitors’ devices with malware.
SQL Injection
One of the most popular techniques for hacking involves the insertion of meta-characters or SQL commands into input fields on a website. The commands are able to execute back-end SQL code.
Cross-Site Scripting
Hackers can embed code in URLs which can be used to execute Javascript code on visitors’ devices when the links are clicked.
All Companies are at Risk, and the Majority Have Already Been Impacted by Malware
If you think only small to medium sized organizations are at risk from malware (due to IT security budgetary constraints) think again. Even the world’s largest corporations are at risk from malware. Earlier this year, Apple was targeted by hackers and suffered a serious malware attack. Full details of the extent of the attack were not disclosed, but a number of Apple Mac computers were compromised by the attackers.
How could the hackers install malware on the computers of such a security conscious company with exceptionally deep pockets? Via a perfectly legitimate website! Users had visited a software development website, with the hackers gaining access via an unpatched Java bug.
The biggest social media sites are not immune to attack either. Twitter suffered a malware attack that exposed the confidential accounts of approximately 250,000 users. This is believed to have happened as a result of the same unpatched Java vulnerability.
No Company is Immune to Cyber Attacks
Around this time last year, a medical equipment manufacturer called Neurocare was targeted by cyber criminals. In that attack, all employees of the organization were affected. In that case, it was not the company’s systems that were attacked directly. The malware came via the company’s payroll processor.
These are all very large companies. But last year hackers used malware to pull of an even bigger and bolder campaign, launching an attack on the International Monetary Fund (IMF). As you could well imagine, the IMF has rather robust security controls in place, yet even they proved no match for the hackers. The attackers just went for the weakest link: IMF employees.
That attack involved spear phishing. Individuals working for the IMF were targeted with a highly convincing campaign which allowed malware to be installed on their computers. That attack was highly sophisticated in nature, and is believed to have been orchestrated by a team of hackers who had received backing from foreign governments. Highly confidential data was exfiltrated in the attack.
Phishing Campaigns Have Proved to be Highly Effective
This year, Kaspersky Labs reported a sizable increase in phishing attacks involving Apple IDs. Two years ago, the average number of attacks per day was just 1,000. Only 12 months later that figure had jumped to 200,000 per day.
Even security firms are not immune to phishing scams. RSA, a prominent American computer and network security company, suffered a phishing attack that was caught by the company’s spam filter. The emails were quarantined, yet were opened from within, unleashing a Trojan that harvested data from employee accounts. RSA’s SecurID tagsix was compromised in that attack.
RSA should not be singled out of course. Even bigger companies have suffered at the hands of phishers. An estimated 20% of Fortune 500 companies have become victims of these campaigns. Even the world’s largest corporations have been hit in recent months. IBM has been affected, and bigger companies still. Microsoft and Google are also victims of phishers.
Beware of Blended Threats Delivered Through Spam Email
The web may now carry the highest risk of malware distribution, but email is still commonly used to deliver malicious software. It remains one of the commonest attack vectors used by phishers. Email spam can be used to attack any device capable of receiving and opening email. This means tablets and Smartphones are vulnerable to attack, not just laptop computers and desktops.
One of the biggest threats comes from blended attacks. These are spam emails that contain links to malicious websites, or even legitimate websites that have been infected with malware. These threats are more difficult to deal with. They require a different form of defense that uses a combination of standard email anti-spam controls along with web security defenses.
Spam may not be the favored choice of hackers these days, but it still represents a serious threat to businesses. Dealing with the emails can waste an extraordinary amount of time and money. Spam can take up huge amounts of bandwidth that affects all employees in a company. Dealing with spam adds significant amounts to operational budgets.
The messages by themselves may not be dangerous, but links to malicious websites can represent a serious problem, especially if staff members have not been warned how to identify malicious links. Infected attachments also place computer systems at risk. Both methods can be used to deliver malware, which has potential to cause a serious amount of damage.
A number of defenses can be used to reduce the risk of malware attacks. Anti-virus software is a must, as is a separate anti-malware shield and scanner. Anti-spam controls are vital, as they can prevent the delivery of phishing emails to employees. Web filtering solutions are also highly beneficial. If a spam email gets through to an endpoint user, the software can prevent a malicious website from being visited.
Unfortunately, there is no single control that can be used to prevent all attacks. The solution is to use multi-layered security defenses and to keep them updated.
by G Hunt |
July 15, 2015 |
Spam News
LinkedIn is a social networking website aimed at professionals, which helps them develop contacts, network, get new business, and find new employment opportunities. One of the main purposes of the site is to build up new contacts, making the site perfect for criminals looking to phish for information. The information that can be gathered can be used against individuals – or organizations – to conduct highly convincing spear phishing campaigns.
What is a Spear Phishing?
You may be aware of phishing, a technique used by criminals to get computer users to reveal their login names, passwords, credit card details and other highly sensitive information. Phishing is like using a trawl net behind a boat. The aim is to catch as much as possible. Sooner or later something will swim into the net. With phishing, spam emails are sent out in the millions in the hope that someone will respond. It is a numbers game, and the unwary will be caught.
Spear phishing on the other hand is not random. Individual victims are targeted. Spear phishing campaigns are often very convincing, and emails are sent containing information that is likely to fool a specific individual – or small group of individuals- into revealing passwords, login credentials, security codes or other information. These campaigns are also highly effective at getting users to click links to malicious websites, or open malware-infected email attachments.
How does Spear Phishing Work?
In order to convince users to install malware or reveal their sensitive information, those individuals must be convinced to take a specific action. To increase the chances of that happening, the criminals behind the campaigns need some nuggets of information. These could be gained from social media websites. People reveal a wealth of information about themselves on Twitter and Facebook, and some leave their accounts open for anyone to see.
LinkedIn is similarly being used by hackers to gain information about users, with the data harvested being utilized in future phishing and spamming campaigns. Data is collected on users, and used to devise phishing emails containing malicious software or links to malware-infected websites, or fake websites which convince users to enter in their sensitive details.
LinkedIn Used by Scammers to Gather Sensitive Data
One of the latest scams identified involves the creation of fake LinkedIn contacts. Accounts are created by scammers, and then used to make connections with people in similar industries. Unfortunately, connecting with these individuals will allow them to obtain a wealth of information on you, such as your employment and education history, phone numbers and whatever information you add to your profile. In many cases, you will be supplying your entire CV to a hacker by accepting them as a contact. Fake LinkedIn contacts are now a major problem as they pose a big security risk.
This means that every contact must be vetted and assessed before you agree to a connection, and who has the time to do that?
How to Spot Fake LinkedIn Contacts
Fortunately, there are some common tells, and a little research (even a couple of minutes) can reveal fake LinkedIn contacts.
No photograph has been added
LinkedIn is all about making professional contacts. Photographs are therefore essential. People like to see who they are connecting with. If no photograph has been added, treat the account with extreme suspicion. Would the CEO of a mining company really be that concerned about someone finding out what he or she looks like?
Stock Photographs Used
Stock photographs can be purchased from image libraries for cents. Complete a quick Google image check against the user’s name and photo. If they are interested in business networking, their photo is likely to appear on other websites. If it appears under a different name, you will know the account is a fake.
Stolen Photographs Used
A photo search can reveal quite a lot of information about the genuineness of a contact. If your prospective contact is a librarian, it is perhaps unlikely they will also be a Ukrainian heavyweight boxing champion (Not necessarily of course!)
Numerous fake accounts have been created with the individuals claiming to be directors of companies. By day, they are the CEO of two or three different companies, by night they supplement their income by producing internet porn (Images have been taken from adult sites and used for LinkedIn). Unlikely perhaps, that CEOs would feel the need to do this.
Some fake LinkedIn accounts are very convincing
Not all fake LinkedIn accounts are suspicious. Many have extensive contacts, and a realistic profile. However often times that information has been lifted from other websites. Sometimes a photo will not have been used elsewhere online, but frequently the text has. One way of checking is to cut and paste small section of their profile and pasting it in Google. It may reveal that the data has been copied from a legitimate LinkedIn account or other social media site.
What is the Risk of Connecting with Fake LinkedIn Contacts?
There are a number of reasons why criminals go to the trouble of creating fake LinkedIn contacts. Spammers can use LinkedIn to obtain email addresses. Criminals can gain information to launch phishing campaigns and information can be gathered to commit identity theft. If a scammer can convince you they are genuine, they may create a fake job for you and get you to reveal some very sensitive information.
Of course the only way to be sure that you are not accepting fake LinkedIn contacts is to only connect with people you know, but that kind of defeats the whole purpose of the website. The answer is therefore to conduct a rudimentary check to make sure the person you are about to share information with is in fact genuine.
by G Hunt |
April 12, 2015 |
Spam News
Ireland may not produce many highly innovative cybersecurity companies, but Galway-based SpamTitan technologies is bucking that trend. The company has recently been rising up the ranks and has now taken its place among the best cybersecurity companies in the world, according to the latest Cybersecurity Ventures report.
Only four Irish companies have made it into the Q2 2015 edition of the Cybersecurity Ventures Cybersecurity 500 list: Netfort, PixAlert, VigiTrust and SpamTitan Technologies, with SpamTitan now having ascended to position 123.
This is a major achievement, with the company having previously been placed at 393 for the previous quarterly report. The massive jump in position has been attributed to the hard work put in by all members of staff, who are committed to providing the best possible service in the fight against cybercrime. The company can now be considered one of the best, and also one of the hottest new prospects in the world of cybersecurity.
Each quarter, Cybersecurity Ventures publishes its new top 500 list, which features companies from all around the world. Experts in the field of cybersecurity assess companies for the efforts made, as well as determining each company’s potential. CISOs, VCs and a host of security professionals provide their input for the reports.
Many similar reports tend to focus on the size of the company, turnover and profits achieved. This list is different as it is more concerned with potential and innovation. Founder and CEO of Cybersecurity Ventures, Steve Morgan, said, “We do not think a list of the largest cybersecurity companies is useful to our target audience of cyber and IT security decision makers, evaluators, and recommenders”. He went on to say, “They already know who the biggest vendors are. Instead, we give a nod to the hottest and most innovative companies.” It is, after all, these companies that really need the recognition.
The list contains all of the hottest new prospects and top performers, with the ranking based on each company’s merits and prospects. Ronan Kavanagh, CEO of SpamTitan Technologies is proud of the rise in position, and the value of the list. After hearing of the new position in the top 125 cybersecurity companies, he said, “We recognize the importance of being included on such a significant industry list as the Cybersecurity 500.” He went on to say, “At SpamTitan, our staff are assisting our customers on a daily basis in dealing with the constant threat of cyber attack, and this is now as important for the smaller businesses as it is for the fortune 500 company. We are delighted to be working with Cybersecurity 500 in highlighting the need for vigilance and raising awareness for all businesses.”
For further information, and to find out the full list of top 500 companies, visit www.Cybersecurity500.com
by G Hunt |
March 9, 2015 |
Spam News
Facebook hacking is rife and, if it happens to you, you are not alone. Unfortunately, there is no one to blame other than yourself. Facebook hacking is caused, in the vast majority of cases, by poor security practices and a lack of security awareness.
Facebook accounts get hacked because:
- Passwords are stolen in phishing attacks
- Two-factor account authentication is not used
- Passwords are shared across multiple sites
- Keyloggers have been installed on a computer used to access Facebook
If a hacker manages to obtain one password, chances are that same password is used on other sites. Criminals sell passwords online, and there are plenty of would be purchasers. Hackers even buy them on exchanges. Sharing passwords across sites is therefore very bad news, especially on sites that have poor security practices.
Fortunately, on Facebook at least, if you are hacked you can report it easily and should be able to recover your account.
A blocked Facebook account does not necessarily mean you have been hacked!
Facebook does frequently block user accounts. It does this as a security precaution, which is good for all users and offers some peace of mind. How often are accounts blocked? About 600,000 times a day, according to TechCrunch!
That is an awful lot of compromised accounts, yet do bear in mind that Facebook has over a billion users. So 600,000 represents just 0.06% of the total. Which is 6/10,000 if you prefer fractions to percentages.
When Facebook blocks an account is because the account has potentially been compromised. According to Facebook, this occurs when “we are not absolutely confident that the account’s true owner is accessing the account and we either pre-emptively or retroactively block access.”
This means that there is suspicious activity, Facebook often errs on the side of caution and blocks access. That could indicate an account has been hacked, or that action is being taken to prevent the account from being hacked. The good news is that when this happens, only the real owner can get the account unblocked. In theory at least.
When the figures of the number of blocked accounts emerged, the story was widely misreported in the media. Facebook was accused of a “shocking lack of security,” but the compromised account definition had not been read by many Facebook users, and even some reporters. Also bear in mind, that those 600,000 blocked accounts will include many false positives.
Determining exactly how many Facebook accounts have been hacked is rather difficult, unless you work for Facebook and have access to that data. It is possible however to come up with a fairly reasonable estimate, based on research conducted by security and market research firms. Their data can be used to get a reasonable estimate.
Take Statista’s figures for example. It conducted surveys on individuals who had been hacked, and 66% said they had had their Facebook accounts compromised. Then combine that with study data from Pew Research. The company determined that the volume of “internet users have had an email or social networking account compromised or taken over by someone else without permission” was 22%.
Using a simple calculation an estimate can be obtained: There are 1 billion Facebook users. 22% of individuals claim to have had an account hacked, and Statista says 66% of those were Facebook accounts. That works out at 145 million users, which should be a fairly reasonable estimate.
Fortunately, Facebook security is robust. A mobile phone is required as part of the account recovery process, so you would need to have lost that as well in order for your challenge question to be used to login. SSL certificates prevent network snooping, and the brute force approach will be prevented by Facebook’s security controls. But phishing scams are likely to leave your account open.
Fortunately, there are ways that you can protect yourself, and your Facebook account.
It can be difficult to avoid phishing scams, and all too easy to fall for one. One of the best defenses is to use Antispam software. SpamTitan’s software will prevent phishing campaigns from being delivered to your inbox. Parental controls at home, and web filtering controls at the office are excellent ways of blocking malicious links.
Unfortunately, not all access points have the above controls, so you will have to rely on common sense and become more security aware. For example:
- Never click on a link that appears to take you to an unfamiliar site.
- Never open email attachments sent from unfamiliar senders.
- Use different passwords – don’t share them between websites
- Use complex passwords, containing characters, capitals, and numbers
- Don’t share everything about your life on social media
- Change passwords regularly, certainly every 6 months
- Don’t reuse passwords
- Keep your anti-spam software, virusguard, and anti-malware programs updated, and scan regularly
- Set your account recovery options and security questions as if they were passwords
And remember, just because you have friends and family on Facebook, don’t let it create a false sense of security. You can never be sure how security conscious they are! Complacency is likely to leave you vulnerable to hackers.
If your Facebook account has been hacked, let us know. We want to hear your stories!
by G Hunt |
February 15, 2015 |
Spam News
Phishing emails may not account for a high percentage of total email traffic, but they are becoming more prevalent. In fact, since 2014 the growth of these malware spreading emails has tripled, according to a new report issued by Kaspersky Labs.
Kaspersky determined that the percentage of phishing emails in total email traffic is now 0.0071%. Compare that to spam emails which accounted for 66.34% of all email traffic in the first quarter of 2014, and the figure seems very small. However, the damage that can be caused by the emails is considerable. For some companies, the damage can be catastrophic. When phishing emails lead to financial losses, funds can rarely be recovered.
Phishing emails are becoming increasingly common, but spam appears to have declined a little. A fall of 6.42% was registered since the last quarter of 2013.
Social Media Overtakes Email as Main Method of Phishing Campaign Delivery
Phishing campaigns are frequently delivered to potential victims via email. A link to a malicious website is sent – often randomly – to individuals in the hope that they are fooled into clicking. That link will take the person to a website where they are required to enter confidential data such as login names and passwords. Oftentimes, visiting the website will result in malware being downloaded to the visitor’s computer.
Spam emails are still favored by cyber criminals in some countries such as China and South Korea; however, social media has now overtaken email as the main method of delivery of phishing campaigns according to Kaspersky.
This may not come as a surprise. Rather than hackers sending the campaigns to new victims, victims of phishing campaigns share the links voluntarily (and unwittingly) via Twitter and Facebook pages. Infecting new computers could not be any easier.
Infected email attachments are still a popular method of malware and virus delivery. If these attachments are opened, the user will install malware and viruses on their device.
Top Ten Malicious Programs Spread by Email
Even with the rise in popularity of social media for malware delivery, spam emails are still responsible for spreading a huge volume of malware. In Quarter 2 of 2014 alone, Kaspersky Labs were able to block an incredible 528,799,591 malware attacks. The volume of different types of malware is also astonishing. During the same period, Kaspersky Labs detected and blocked 114,984,065 unique potentially unwanted objects.
Many of the viruses and malicious programs are camouflaged to look innocent. Take the most popular malicious program used by cyber criminals as an example. Trojan-Spy.HTML.Fraud.gen appears to be a standard HTML page containing a form for online banking. When data is entered, the information is transmitted to hackers who are then able to use the information to gain access to users’ bank accounts.
Cybercriminals Earning over $100 Billion a Year
Cybercriminal attacks are increasing in frequency and severity, and this is unlikely to change given the huge sums of cash that can be obtained. According to recent estimates by the FBI, the proceeds of cyber crime are in the region of $100 billion per year. The bad news is that criminals are devising ever more sophisticated ways of attacking organizations, and many of those organizations are ill-prepared to deal with the risks. Oftentimes even basic security measures against cyber attacks are found to be lacking. This is due to extremely limited IT security budgets, which hamper efforts to deal with all the threats.
Many organizations do not have clear and concise IT security policies in place, and do not place an individual in overall charge of cybersecurity. Sometimes there is not even a dedicated IT security professional employed and many organizations are still not providing all members of staff with security awareness training.
A failure to employ the appropriate staff, allocate sufficient budgets to IT security and train the staff can prove very costly indeed. Lost and stolen data, system downtime and drained bank accounts result in far heavier losses than the cost of implementing security measures to prevent attacks. Even the cost of new IT security staff will pay dividends in the long run.
Staff Security Awareness Training is Critical
Spam emails and phishing campaigns generally have one of two main aims: To trick users into revealing sensitive information or to fool people into downloading and installing malicious software and code. The latter allows hackers to take control of computers and infiltrate networks.
Spam and phishing emails can be very convincing, yet there are a number of tell-tale signs that emails are not all they appear to be. By providing training to staff members on these tell-tale signs, the risk of employees falling for a scam can be drastically reduced.
Email Security Solutions Must be Employed to Protect Sensitive Data from Attack
Can you be sure that staff members will be vigilant and security aware? Unfortunately, even with training, employees will make mistakes. They are human after all. It is therefore important to install security solutions that will limit the volume of spam emails that are delivered to employees’ inboxes.
One of the best solutions is a spam filter such as SpamTitan Anti-Spam. This data security solution has now been employed by IT security professionals in over 120 countries around the world. They benefit from being able to block over 99.7% of spam emails.
Since SpamTitan uses two separate anti-virus engines (Bitdefender and Clam AV) the catch rate is particularly high. Furthermore, SpamTitan includes an anti-phishing module as standard that filters out emails containing links to known malicious websites. This further reduces the risk of an employee accidentally clicking on a link and downloading malicious software. Consequently, SpamTitan is one of the best investments to protect against cyber attacks.
by G Hunt |
August 20, 2014 |
Spam News
Cyber criminals are using phishing to lure web visitors into revealing their sensitive data. Internet surfers are presented with a baited hook, which draws them into revealing login names, passwords, security keys and other valuable data.
The technique can be employed by individuals with little to no hacking skill, luring users to a malware-ridden website in exchange for payment. There are plenty of would-be criminals looking to make a quick buck, and since the campaigns can be so effective, online thieves and criminals are increasingly using this technique to make money.
Many online criminals use phishing in random campaigns sent via email. There is little skill involved. It is simply a numbers game. If enough emails are sent, sooner or later someone will respond and fall for the bait. However, we are now seeing much more sophisticated campaigns launched.
It used to be easy to spot a phishing email. They were littered with grammatical errors and spelling mistakes. Images were used that were clearly fake, and the emails would only fool the most unsuspecting computer user. They claimed victims, nonetheless, but only a few.
Some of the phishing emails now being sent are extremely convincing and very difficult to identify. Even well trained, security-conscious IT professionals have fallen for some of the scams. The reason? They work by exploiting traits in human behavior and use techniques that are particularly effective at drawing the required response.
Human Traits Successfully Being Manipulated by Hackers
Cyber criminals are exploiting human behavior to get users to click on links to malicious websites or open attachments. They rely on common traits that are all but guaranteed to get the desired response. The male of the species, for instance, is easily tricked into opening an apparent JPEG file if he is promised a glimpse of bare female flesh. An offer of sex from an unknown admirer can also work particularly well.
Not everyone is motivated by sex. For others the promise of financial gain does the trick. Criminals exploit greed to get users to click on a link. A money making scheme, or a hot stock tip, can entice many people to click on a link. Curiosity is also exploited. Major news events, conspiracy theories, celebrity news, and information on natural disasters have all been used by email spammers and scammers to get people to visit a malware site or open an email attachment.
Even the sense of duty has been exploited. Emails are sent from the accounts of work colleagues, bosses, civil authorities or law enforcement officers. These are effective at fooling users into complying with requests.
By exploiting human traits and evoking emotions, recipients of these scam and spam emails swallow the hook, and often the line and sinker too.
Spear Phishing: Effort Put in is Rewarded with More Victims
The sending of millions of mistake-ridden emails results in very few individuals falling for the scams. When email spam filtering software is employed, the filters will prevent these emails from even being delivered.
However, a little research goes a long way. Phishers who invest time into researching victims can see the time they spend on the campaign really pay off. A search on social media will reveal a considerable amount of information on an individual. Employers can be found on LinkedIn, Facebook can be used to find out friends’ names, and Twitter exploited to find out a user’s interests. With this information, highly effective campaigns can be developed.
These phishing campaigns are referred to as spear phishing. As the name suggests, the hacker goes after one fish. These campaigns can be incredibly effective as they exploit trust. If an email is sent that appears to be from a friend or colleague, it is far more likely to be opened. But how is this possible?
SMTP Weaknesses Are Exploited by Phishers
Unfortunately, the SMTP protocol contains a security weakness. Hackers can exploit this weakness to mask the true sender of an email and the return address. To the casual viewer it appears that the email has been sent from a known individual, and even replying to the mail appears to direct it to the correct mail recipient.
Fortunately, a spam or phishing email is not dangerous. It requires an action to be taken by the recipient. Deleting such an email will delete the risk. Only opening the attachment, downloading it, or visiting a link contained in the email will result in the delivery of malware, a virus or the installation of malicious code.
Unfortunately, while most employees know never to double click on a file with a .exe extension, file extensions can be all to easily masked. They can be made to appear as a PDF file or JPEG, or other supposedly innocent file type. Without training, users are likely to open these attachments, and unwittingly activate the executable file.
The way to prevent users from clicking on links and opening attachments is to provide them with security awareness training. Teach staff members how to identify phishing campaigns, and they can check the genuineness of emails before they take action. Developing a culture of security awareness is therefore essential in the fight against cyber crime.
Blocking the emails with a spam filter is even better. That way, the email will never be downloaded and delivered. Unfortunately, from time to time emails do slip through the net. When that happens, employees must know how to react.
Training is therefore important even if a robust and reliable spam filter is used. After all, it is best to be shown how to deal with a phishing email that never arrives than to fall for the first one that gets past a spam filter.
by G Hunt |
August 6, 2014 |
Spam News
The news is full of reports of data breaches that have been suffered by companies and even governments. Numerous media reports detail how hackers have managed to obtain tens of thousands of confidential records, or in some cases, tens of millions or more. However, it is rare that a hacker is caught and brought to justice for the crimes committed.
Recently, a hacking group in Russia was reported to have stolen a staggering 1 billion passwords. If that was not shocking enough, the authorities know the individuals are located in central Russia. They are also in their early 20s. If they have been identified, why have they not been arrested?
Bringing hackers to justice is complicated
In this case, there are problems because it is the United States that wishes to take action. The crimes were committed against Americans but some countries are unwilling to turn over their own citizens to other countries. In this case, should the criminals be tried in Russia or in the United States? Where should justice occur, where the crimes were committed or in the country most affected by the crimes? Should hackers be extradited?
If there is no treaty in place between two countries, hackers will be tried and sentenced (or not) in their own countries. The United States has tried to get five Chinese hackers extradited and brought to the United States to face trial. They worked for the Chinese military. China is unlikely to take any action, and certainly will not release them to the United States. The individuals are believed to be behind attacks on Alcoa, U.S. Steel and Westinghouse, as well as on other U.S. firms. The criminals were indicted, but that is as far as the U.S. got. They are very likely working on new hacks against U.S. companies.
In some cases, hackers do not need to be extradited. The FBI has previously tricked hackers into coming over to the United States voluntarily. By doing so the tricky issue of extradition has been avoided. The FBI set up a job interview for two hackers using a fake Seattle company. The pair, Alexey Ivanov and Vasily Gorshkov, arrived for the interview and were promptly arrested. The latter received a sentence of 3 years, the former got 48 months.
Spam email kingpin sent 30% of all junk emails!
If you are a cybercriminal or spammer and you have launched attacks on Americans, it is a wise move never to visit the country. However, some just can’t resist. When visiting a car show in Las Vegas in 2010, Russian super-spammer, Oleg Nikolaenko, was arrested and charged for his crimes. He had used a botnet to send the spam emails. That botnet included a staggering half a million computers. Even more staggering was the volume of emails he sent. An estimated 10 billion per day. He is awaiting trial.
Hackers are very good at hiding their real identities and consequently can be difficult to locate. It can be even harder to bring them to justice.
It should come as no surprise to hear that many successful hackers are based in countries that offer protection against extradition to the United States. Unless there are international laws signed, and more cooperation between countries to tackle the global problem of cybercrime, they are unlikely to be tried and sentenced for their offenses.
by G Hunt |
May 29, 2014 |
Spam News
eBay customers have started to receive emails advising them to change their passwords. Their user names and passwords have been obtained by hackers, and a new password must be set for security reasons.
Unfortunately for many eBay account holders, the requests to change passwords have not been sent by eBay, but by phishers. The emails contain a link to a website which looks like eBay, but it isn’t. It is a fake website devised to get users to reveal their current passwords. This sneaky phishing campaign is likely to catch out many eBay account holders.
Data breach was suffered, but not identified for 2 months
In late February/early March, three employees of eBay had their login credentials compromised in a cyberattack. The cybercriminals used the login credentials to access a database containing the names of 233 million site users. Phone numbers, addresses, email addresses, dates of birth, and customer names were stolen, along with encrypted passwords.
In early May, eBay became aware of the breach, two months after it occurred. The company then waited a couple of weeks to make the announcement. The delay was because eBay didn’t realize that account information had actually been stolen. It took the best part of a month to realize data were actually stolen in the attack. Fortunately, PayPal information was not compromised and neither was any financial information.
A breach that does not involve bank account details or credit card information being exposed can still be serious and, in this instance, eBay account holders are at risk.
Passwords may have been encrypted but hackers I’ll be able to guess some as they have a lot of personal data. Dates of birth for example. They are often used as passwords. Since email addresses were obtained, the victims that have not had their passwords guessed are now being spammed with phishing campaigns.
Most customers will be aware of the exposure of their data and as a result, they may believe the phishing emails to be genuine. If they do, they will inadvertently reveal their passwords when they attempt to change them.
Investigations launched into the eBay data breach
Investigations into the eBay data breach have now been launched by state attorneys general in three States – Connecticut, Illinois and Florida. In Europe investigations are also being conducted. The attorney general of New York has spoken out about his expectations. He believes credit protection services should be offered to breach victims without charge. At the present moment in time, eBay has no plans to offer any risk remediation services to customers.
eBay has been criticized for the slow identification of the breach, as well as the slow response when it was discovered. Initially there were no victims, then there were 145 million. eBay finally settled on 233 million accounts.
It may not be a problem for spammers to send 233 million emails, but for eBay that has taken some time. The company tweeted news of the breach, but email notifications took a considerable amount of time to be sent. This may have resulted in more individuals responding to the phishing requests.
eBay breach victims must exercise caution
A data breach of this magnitude, affecting a company as large as eBay, is worrying. How good were the security measures it had in place? Why was the phishing campaign not identified before three people responded? Why were the phishing emails not blocked and prevented from being delivered? Only time will tell.
Since information has been compromised, and hackers are now attempting to guess passwords based on the personal data they have acquired, it is a wise security precaution for account holders to login to the site directly and change their passwords. They should not respond to an email, as it may be a phishing campaign.
by G Hunt |
May 26, 2014 |
Spam News
Unfortunately, all it takes to lose swathes of customers and destroy the reputation an ISP is for a single email spammer to get a block of your IP addresses blacklisted by a number of ESPs and RBLs. It is a nightmare scenario, yet it is one that could all too easily play out.
Customers using any of the blacklisted domains would have their outbound emails blocked and, if they cannot send emails, they will leave in their droves for another provider. Perhaps even worse than losing those valuable customers will be the comments they invariably post all over the Internet. Negative feedback can seriously damage a company’s reputation and it can take a long time for a damaged reputation to be restored.
There are steps that can be taken to at least temporarily fix the situation. The IP addresses affected could be swapped, and netblock could be used as a temporary fix. Unfortunately, recovering blacklisted IP addresses is a very slow process. During this time, other IP address blocks could be lost.
Managing risk is difficult. It is possible to set limits on the number of emails that can be sent by a particular domain. Alerts can be configured to identify a domain that is being used to send spam, and it may be caught in time to prevent blacklisting. IP netblocks can be changed should it not be possible to prevent a domain being blacklisted by ESPs and RBLs.
The process of undoing the damage caused by spammers is a nightmare as well. New domains must be warmed up, and efforts made to ensure they are operated within acceptable ESP limits. Otherwise they will just get blacklisted again and the process must restart.
Fortunately, there is a solution that can be adopted by MSPs and ISPs that can prevent blacklisting. Install the latest version of SpamTitan!
SpamTitan v6.3 includes outbound email filtering
SpamTitan will prevent spam emails from being delivered to inboxes; however, version 6.3 also includes a sophisticated and powerful outbound email filter that can be used to prevent spam emails from being sent from accounts. If a domain is hijacked and used to send spam emails, or is used by an individual within your organization, the emails will be blocked and the ESP will not be alerted.
SpamTitan v6.3 uses the same identifiers to clean and filter outbound email as it does for incoming spam. System administrators can set rate limits by email address, IP address range, or domain.
If an organization needs to send a high volume of emails, to avoid inadvertently causing problems with an ESP, a pool of IP addresses can be used to send email and these can be rotated. This allows risk to be effectively managed. Damage to the reputation of IP addresses and the business itself can be easily prevented.
Any MSP providing multiple client domains can implement SpamTitan v6.3 and ensure that emails are sent safely, while the risk of blacklisting is kept to a bare minimum. The Anti-Spam solution will also ensure that incoming emails are cleaned and spam is quarantined, while the Anti-phishing module will protect against malicious attachments.
by G Hunt |
February 18, 2014 |
Spam News
The expert researchers at Kaspersky Labs have been hard at work this winter uncovering new malware threats, viruses and malicious code that threatens computers, mobile phones, servers, and corporate networks. However, what has recently been discovered is very worrying indeed. A new and highly malware named the Careto virus.
This is not a run-of-the-mill virus. It is nasty, very sophisticated, and consequently, probably the work of government-backed hackers. The Careto virus came from a previously known location, one that has produced a similar virus not so long ago. Kaspersky discovered the new virus and took rapid action to neutralize the threat.
Kaspersky Labs has already produced a detailed description of their discovery after conducting a detailed forensic analysis. That said, some techniques used to explore the nature of the virus were not particularly sophisticated and could be performed by any IT professional.
Kaspersky used “strings” – a Linux program that can be used to explore executable files – to extract text from the file. What they found was a series of instructions in Spanish, together with the name assigned to the new virus: Careto.
The name “Careto” is colloquial Spanish for “ugly face”, the corresponding name in English being “ugly mug”. It doesn’t translate as disaster, but it might as well do. This virus wreaks havoc.
Hidden inside this virus is a rootkit and a bootkit. The malware is particularly nasty and versatile, containing a Linux version, Mac OS X, and it is presumed it would also work on Android phones and the iOS system. It is very sophisticated in nature, and because of its complexity it has been suggested it is not the work of a bored, skilled teenager coding away in a bedroom. The complexity suggests that a considerable amount of time and effort has been put in to developing the virus. The Careto virus is capable of working on multiple systems at once, which Kaspersky suggests makes it the work of a team of hackers, not one individual.
Kaspersky investigated the Careto virus and started monitoring command-and-control (C&C) servers that were known to be used by hackers. This enabled the researchers to determine that the virus is proving to be effective. It has already infected over 380 computers, with those infections discovered in 31 countries around the world. The Careto virus appears to have been used to target specific organizations, and has been discovered in government organizations around the world, in particular, foreign embassies. Oil companies, gas companies, private equity firms, and research institutions have also been targeted.
The virus is primarily being spread by spear phishing campaigns. The targets have been sent links to fake versions of popular newspapers, including The Washington Post, as well as the Spanish Newspapers, El Pais, El Espectador, Publico and El Mundo.
The link contained in the phishing email has been masked, with users fooled into thinking they are actually visiting the genuine periodicals. The virus has also been discovered to have been used to infect computers via a security vulnerability in Adobe Flash (The 2012 version). Flash is used on a number of (typically older) websites to display advertising and video files.
Users may be wary of double clicking on emailed executable (.exe) files, but what about harmless picture files such as JPEGs. The executable file was found to reside in apparent JPEG files. The names, chef.jpg, waiter.jpg and dinner.jpg having been used to make them appear innocent.
What Does the Careto Virus do?
The types of individuals targeted thus far gives a clue as to what the Careto virus does. Its aim is to collect highly sensitive information, which it does by intercepting all communications channels used on the victims’ computers.
It “listens” in on Skype calls, chat sessions, and records and exfiltrates data from the infected device. Passwords are stolen, and encryption keys, bank account numbers, email addresses, phone numbers, and all manner of sensitive information obtained by hackers. This data is sent to the hackers’ command and control servers, one of which was discovered to reside on one of the IBM-owned Softlayer cloud service provider’s servers.
Unfortunately for the infected, detecting the virus is difficult. This is because it has stealth rootkit capabilities, cyber-espionage modules and other functionalities to help it avoid detection. After discovering and analyzing the virus, Kaspersky was able to track infected computers.
Fortunately, AV definitions have now been updated to spot the Careto virus, which incidentally, is blocked by SpamTitan Anti-spam software. SpanTitan is able to prevent this nasty virus from being delivered to your inbox.
by G Hunt |
September 23, 2013 |
Spam News
Security technologies are some of the most advanced technologies, but security itself must be combined with good business and user practices to work effectively. No matter how advanced and well implemented the technology is, it is only as good as the methods used in using and managing it.
-
Acceptable use policy – what network activities are allowed and which ones are not
To protect employees, customers and suppliers all members of staff should be given a copy of the company’ s policy for acceptable use of IT resources including Internet and email. Often this forms part of the contract of employment. Having an acceptable usage policy in place helps protect the organization from exposure to malware and web threats as well as helping in disputes with employees.
-
E-mail and communications activities
To help minimize problems from e-mails and attachments, informing user behavior is key. Robust email and web security, coupled with appropriate user training and security procedures, are absolutely essential to the protection of corporate data, financial and other electronic assets. Without adequate solutions and controls, cybercriminals can exploit gaps in security defenses and cause serious damage to an organization.
For example:
- On Christmas Eve and again on December 26th, 2012, cybercriminals used malware installed on a local PC at Ascent Builders to transfer $900,000 from the company’s Bank of the West account. The theft was followed shortly after by a major distributed denial-of-service (DDoS) attack on the bank, presumably to conceal the theft of funds.
- In December 2012, cybercriminals added 11 bogus employees to the payroll of Niles Nursing, Inc. by using the company controller’s login credentials. Using ACH payments from Niles’ bank account, the criminals initially transferred $58,000 in funds to these individuals, who were to wire the funds to contacts in Russia and Ukraine. In total, approximately $170,000 was stolen from the firm.
- A study conducted for the UK Cabinet Office found that the loss of intellectual property – much of it the result of malware and other forms of cybercrime – costs British organizations upwards of £9.2 billion annually.
To help protect networks against threats such as viruses, worms, and Trojan horses, companies need to implement anti-virus protection on all company devices – specifying what anti-virus software is installed and what interval they are scheduled to run at. In addition, the anti-virus software and the virus pattern files must be kept up-to-date. Virus-infected computers must be removed from the network until they are verified as virus-free. System Admins are usually responsible for creating procedures that ensure anti-virus software is run at regular intervals and computers are verified as virus-free. Any activities with the intention to create and/or distribute malicious programs into the company (e.g. viruses, worms, Trojan horses, e-mail bombs, etc.) should be clearly stated as prohibited, in accordance with an Acceptable Use Policy. Any employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
To help safeguard the network from unauthorized users, current corporate policies surrounding network security often neglect the most critical and weak security component: the human element. An organization’s overall security is only as strong as its weakest link – the user. Environments with disparate sources of identity information have different approaches for organizing user entries, security practices and access control. Internal identity issues can be complicated and need clarifying in a policy format.
-
Password policy, to help employees select strong passwords and protect them
A complex security system won’t matter if a hacker or phisher gets a hold of an employee’s password. If you take a laissez-faire approach to creating and protecting passwords these type of security breaches are more likely to happen. Smart password practices require next to no budget. They don’t need to take up much time either when formalized in a company policy. Password policy is often overlooked, but it’s a very important part of keeping secure in an online world.
-
Encryption policy, to provide guidance on using encryption technology to protect network data
A common scenario occurs when a company with a security policy in place directs the use of encrypted USB storage and distributes these devices to its users. After time it becomes apparent the company is still at risk from a data breach because users continue to use unencrypted USB keys. This company had a security policy in place and they issued encrypted devices yet still there’s a data breach that they must deal with. An encryption policy will not work unless users understand their role in protecting company data. It’s important to have an encryption policy but it’s just as important to have an encryption policy that can be enforced and is easy for the end user to adhere to. The hard part in this process is that it often requires a behavior change, the secret to success is showing employees how they benefit from tighter network security. Cybercrime and phishing attacks most commonly originate with an employee clicking a link to a website hosting malware, opening a file attached to an email that contains malware, or simply just giving up corporate information when asked via a phishing email or website. Such information can then be used as the basis for a sophisticated phishing attack or may be sufficient to get the scammer what they need. There is no silver bullet, but these threats can be mitigated against by training the workforce to identify, prevent, and report such attacks in a timely manner.
by G Hunt |
March 10, 2013 |
Spam News
Cyber criminals often take advantage of major news stories to launch new spam and phishing campaigns. Email subject lines containing news headlines are more likely to be opened by email users. A percentage of individuals who open the emails will click on the links contained in those emails or open the attachments.
One of the latest email scams uses the death of Hugo Chavez to get users to open spam and phishing emails. Unfortunately, curious individuals are likely to end up compromising their computer, and even the network to which it connects.
The latest spam campaign takes advantage of users’ curiosity with a good old conspiracy theory. In this case, the theory is that the FBI or CIA were behind the death of Venezuelan president, Hugo Chavez.
Researchers at Kaspersky Labs intercepted one of these spam emails and investigated. The email directed users to a website containing malicious software. Visiting the link would result in the user’s device being infected using the BlackHole 2.0 exploit pack. This would happen without the users’ knowledge. In this case, the malware was widely known. According to Kaspersky Labs, when the link was clicked “The payload dropped was not disclosed; however, 8/46 antivirus programs were able to detect the exploit code.”
The Aim of Many Spam Emails is to Infect Devices with Malware
Kaspersky Labs AV engine is used by SpamTitan to detect emails containing malware or malicious links. The anti-virus giant keeps its virus definitions database up to date and checks for the signatures of the latest malware and viruses to be discovered. The company has already identified a number of Hugo Chavez email scams doing the rounds, all of which have the purpose of delivering malware to unsuspecting email users.
The emails take advantage of people’s curiosity and direct users either to fake websites or genuine websites that have been hijacked and loaded with malware. Oftentimes the emails contain attachments containing malicious code. Opening those attachments will similarly result in users’ systems being compromised.
The latest emails are nothing new. Spammers and hackers often take advantage of major news events to get their malicious emails opened. Major sporting events, celebrity news, weddings, deaths, elections and natural disasters usually spawn a wave of new spam emails. Cyber criminals are devising ever more complex campaigns to fool users into installing malware or revealing their sensitive information.
Unfortunately, the problem is likely to get worse. As long as it proves profitable to send these spam email campaigns and phish for information, there will be criminals who are more than happy to commit time to developing the campaigns.
Fortunately, it is possible to lower the risk of becoming a victim of the spammers by following some simple rules and being vigilant.
Guidelines to Avoid Becoming a Victim of a Phishing Attack
- If you don’t know the sender of the email, don’t open it. Mark it as junk or delete it
- Never open an attachment sent by someone you do not know
- Never click on a link in an email unless you are sure it is genuine
- Never unsubscribe from an email newsletter or service that you have not subscribed to – Doing so will just confirm to hackers that your email address is valid. This will likely see you targeted by even more spammers
- If you receive a special offer that you are interested in, visit the website of the vendor directly to check the validity of the offer. DO NOT use the link contained in the email
- Ensure your anti-virus and anti-malware definitions are up to date
- Develop a culture of security awareness in your organization – The majority of security breaches come as a result of employees falling for a phishing campaign or responding to spam emails
- Install a robust spam filter to prevent spam from ever reaching inboxes
- Use web filtering to prevent users from visiting known malware and phishing websites
by G Hunt |
November 25, 2012 |
Spam News
Cyber Monday is one of the busiest online shopping days of the year, in fact the four days from Black Friday to Cyber Monday see huge volumes of people head online rather than travel to the shops.
This period is the busiest time of year for online shopping, with millions of shoppers going online to buy presents for Christmas. Over $1.5 billion is expected to be spent online on this single day, according to figures from ComScore. That represents a 20% increase in spending year on year. Ever since 2005 – the first Cyber Monday – online criminals have taken advantage of the unsuspecting. This frenetic period of shopping sees many internet surfers and bargain hunters let their guard down.
There are bargains galore, huge discounts to be had and a small fortune can be saved. However, it is a time when users and businesses need to be particularly vigilant. Financial ruin awaits the unwary. Spammers, scammers, phishers and other cyber criminals are very active during this four-day period and are waiting to take advantage of Internet users that do not take precautions.
Retailers do tend to concentrate efforts on Cyber Monday, but that is not to say that the remaining days in the run up to Christmas will not be busy. Cyber Monday is just the start of a long spell of intensive online shopping. Cyber criminals are aware of this. Individuals failing to take care could well become victims of fraud and identity theft. A high percentage of victims are created during the period from Black Friday to Christmas Eve.
A cybercrime report issued earlier this year suggests that 431 million adult victims have become victims of cyber crime in the past 12 months. The global losses from online criminal activity have now reached an incredible $114 billion a year.
Shopping Frenzy Sees Basic Email Security Measures Forgotten
Cyber Monday is not a holiday. It is just a particularly busy day for online shoppers. Since people are at work, the time available for online browsing is therefore limited. Time pressures combined with amazing bargains is only a good mix for online scammers. They take advantage of lapses in security precautions that inevitably occur when shoppers are concentrating on special offers and discounts.
Scammers use this time of year to send huge volumes of spam emails containing links to exclusive deals and special offers. Email attachments are commonly sent containing vouchers providing even greater savings. This is not just a problem for shopping addicts. Employers face an elevated threat of having their networks compromised during this busy period. According to recent research, 80% of all online shopping occurs during working hours, with employees sneaking online while at the office.
Employers must therefore ensure that their employees are not taking unacceptable risks that could compromise their computers and networks. Should malware be downloaded, or phishing links clicked, the consequences could prove to be catastrophic.
Should Access to Shopping Sites Be Banned at Work?
Human resource consulting firm, Robert Half Technology, recently conducted a survey that showed CIOs do not typically block access to internet shopping sites from the workplace. 77% of CIOs allowed fairly free access to the internet from work, with only 23% of CIOs banning online shopping. However, that said, internet access is closely monitored and action taken against employees found to be excessively surfing and shopping from work computers.
By permitting casual internet surfing and online shopping at work, CIOs are allowing employees to potentially engage in risky behavior. Many choose to reduce the risk of users visiting phishing sites by restricting access to the internet to secure websites only. This is often achieved by implementing a web filtering solution, which prevents employees from visiting specific websites or certain types of websites.
This is arguably one of the best methods of protecting business networks, without placing too many restrictions on the staff. Internet access can be allowed, which leads to happier staff, yet networks can be protected from phishing websites, viruses and malware.
The use of anti-spam filters will similarly prevent spam emails from being delivered to inboxes, further reducing the risk of employees clicking on links and opening attachments that could compromise a network. If these email security measures are employed and security awareness training is provided, the Black Friday to Cyber Monday period can be enjoyed safely. Many data security headaches will also be prevented.
by G Hunt |
August 30, 2012 |
Spam News
The news that Google will pull the plug on Postini spam filtering software may not come as a shock to the 26 million businesses and consumers who use the product to keep their inboxes clear of email spam. There have been rumors circulating for a while now about the Postini Anti-Spam pull out. However, now it is time to actually start looking for an alternative email spam filtering provider, as the rumor has been confirmed as being true.
Google is attempting to move all Postini customers over to Google Apps, which the search engine giant hopes will be a smooth process. Not all Postini customers will welcome the move. For them, they will need to put effort into assessing the alternative spam filtering to Postini and will need to choose another vendor.
Google Apps may offer email security solutions but there are drawbacks, the main one relating to privacy. Google does like to know everything about its customers and many organizations are unhappy about giving Google so much information about them and their business.
A new Anti-Spam solution is critical
Since email spam filtering is a critical business system, there cannot be a gap between the termination of the Postini service and the implementation of a new spam filter. Due to the volume of spam emails now being sent, inboxes are likely to be swamped with spam the second the Postini service expires. Spammers are likely to seize the opportunity and send out even more emails hoping to capitalize on the gap in service that many companies may experience.
Changing provider is a pain. Small enterprises are typically short staffed and switching any service provider means a lot more work needs to be done. When staff are already stretched and overworked, the time needed to assess new service providers and install and test a new Anti-Spam system must be found from somewhere.
It doesn’t take a long time to change an MX record, but changes allow errors to creep in. If a period is entered in the wrong place it could result in the email system grinding to a halt. Email crashes can take a long time to resolve.
Postini’s exit from the email filtering market may not be a shock, but Webroot customers are likely to have one. They too will have to find a new Anti-Spam service provider. It would appear that by the end of 2013, Webroot will also be pulling the plug on its anti-spam products.
SpamTitan is the natural choice for soon to be ex-customers of Webroot and Postini
SpamTitan email filtering solutions are an ideal alternative for Webroot and Postini customers. SpamTitan is an up and coming company that is growing at an impressive rate. The company has now topped the honors list in recent industry awards – SpamTitan has just been voted the Number 1 Anti-Spam solution in July’s Virus Bulletin Test – and in addition to an impressive catch rate and low false positive rate, its anti-spam solutions represent excellent value for money.
SpamTitan advantages
Businesses located in over 100 countries around the world have adopted SpamTitan as their preferred Anti-Spam solution. The company’s products are highly effective at blocking spam email, with SpamTitan filters preventing 99.97% of spam emails from being delivered thanks to the powerful dual AV engines at the heart of the software. Tests have shown a false positive rate of virtually 0%, and additional protection is also provided by an anti-phishing module.
Summary of benefits of SpamTitan Anti-Spam solutions
- Catch rate of over 99.97% – Fewer spam emails will be delivered
- Virtually 0% false positive rate – Genuine emails will not be caught in its filter
- Dual AV engines employed– Bitdefender and Clam Anti-Virus stop more spam
- Anti-phishing capability – Anti-phishing protection to prevent malware infections
- Multiple deployment choices – Choose from ISO, SpamTitan on Demand, and VMware
- Competitive prices offer cost savings over competitors
- Seamless migration from existing Anti-Spam service providers
- Excellent customer service
For further information on migration, pricing, and implementation timescales, just give the SpamTitan team a call.
by G Hunt |
June 20, 2012 |
Spam News
Ransomware is all the rage these days. Employees are fooled into downloading malware onto work computers, and hackers lock company data with powerful encryption software. Once encrypted, the data can only be accessed by using a security key. Unfortunately, they are all held by the hackers and will not be released unless a ransom is paid. Agree to pay the ransom and the data will be unencrypted. There is no guarantee that this will happen of course, but companies are often given no choice.
Ransoms are also demanded following the theft of corporate data. The criminals responsible are not looking to use the data personally. They just want a quick and easy payout. AmeriCash Advance, a well-known U.S. Pay Day loan provider, was recently attacked and had customer data stolen by a hacking group called Rex Mundi.
The group asked for a ransom to be paid, but AmeriCash refused to give in to the demand for $15,000. The company had been warned that if it didn’t pay up the stolen data would be posted online. Loan applicants and the company’s customers would then have their financial information sent out via Twitter and social media networks. This would place those individuals at a high risk of suffering fraud, having their identities stolen, or being targeted by phishers and scammers. That would likely result in customers taking their business elsewhere.
The refusal to pay means that is likely to now happen. Previous applicants for loans and AmeriCash customers must therefore be on their guard.
How much risk do victims face?
The level of risk depends on the data that have been stolen. If credit card numbers, full bank account information, Social Security numbers and account logins have been compromised, the risk of identity theft and fraud being suffered will be very high.
Any individual affected would need to put a credit freeze on their accounts, register for credit monitoring services and be extremely careful responding to emails and divulging any information. In the case of the latest attack, individuals had the last four digits of their Social Security numbers exposed, the amount of money they requested or had had loaned, and their names and email addresses. In this case only a small quantity of data was stolen and, although customers are still at risk, it could have been a whole lot worse.
Any person in possession of the data is unlikely to be able to steal the identities of the victims without obtaining further information. The first 5 digits of the Social Security number for example along with a date of birth. Criminals who have purchased data will likely attempt to obtain the further details they need. For that they will use phishing scams. These aim to fool users into revealing sensitive information and the campaigns can be very convincing.
What can be done to reduce risk following a successful cyberattack?
According to a report on CNet, AmeriCash did what all companies should to. The company made sure that its systems were secured to prevent further attacks. The relevant authorities were contacted and law enforcement agencies were notified.
Customers also needed to be advised that their data have been compromised and warned of the risk of phishing campaigns. That process was also performed.
Offering affected individuals free credit monitoring and identity theft resolution services can help reduce fallout. Some state laws demand that this is offered if Personally Identifiable Information (PII) or Protected Health Information (PHI) is exposed.
It is also wise to increase security measures to prevent future attacks. Web filtering solutions and anti-spam protection can reduce the risk of suffering data breaches. It can also prevent employees from falling for phishing campaigns that give hacking groups the information needed to gain access to corporate networks.
by G Hunt |
February 23, 2012 |
Spam News
Following the news that Boulder-based Internet security company, Webroot, is set to leave the email security market, many IT security professionals have started looking for an alternative solution to deal with their organizations’ spam problems. A great many IT security professionals will be sorry to lose Webroot email security products, having relied on their protection for a number of years. Webroot email security solutions were popular and effective.
Two months previously, Webroot was reported to be looking to leave the email security market, and is to retire support for its products as 2013 comes to a close. A lack of support means a change will be necessary for any company currently running Webroot email security solutions if they are to keep their email systems protected. Fortunately, SpamTitan is well positioned to take up the reins.
The company offers industry leading cloud-based anti-spam service tailored to the needs of individual businesses. Not only do the company’s products boast a high success rate – blocking over 99% of spam emails – they also have a very low false positive rate.
SpamTitan also boasts one of the most competitive pricing models of any anti-email spam service. With IT security budgets stretched to breaking point already, this will come as very welcome news to CIOs, CISOs and IT security professionals.
SpamTitan Enterprise Anti-Spam Solutions
To date, SpamTitan has been deployed in over 100 different countries around the world, with IT security professionals choosing the company’s products for their exceptionally high spam catch rates. The products have consistently scored highly in independent anti-spam tests, and boast a catch rate in excess of 99.97%. The high catch rate is achieved, in part, by using dual AV engines. This ensures that if one engine fails to catch a spam message or phishing email, there is an excellent chance that the second engine will. The two industry-leading AV engines used by SpamTitan are those developed by Bitdefender and Clam Anti-Virus.
Additionally, the products have a false positive rate of virtually 0%, with next to no genuine emails mistakenly caught up in the spam filters. Businesses can therefore use the products with confidence, knowing that important, genuine emails will be delivered to the correct recipients. As a result, IT professionals will not be bombarded with requests by employees to look for expected emails that have not been received.
SpamTitan is much loved by users because of the ease at which the company’s solution can be implemented. System administrators love the products for the easy-to-use interface and level of customization possible. This allows tweaks to be made to suit each organization’s needs and requirements. Multiple deployment options are also offered, such as ISO, Vmware, in addition to the ever popular SpamTitan On Demand.
The products also boast excellent protection from phishing emails thanks to a powerful and robust anti-phishing email module. Phishing emails are a growing threat to network security, and with higher volumes of malicious emails now being sent, this is a very important feature to help ensure network security.
Need to Switch from Webroot to Another Anti-Spam Service Provider?
Any organization looking to make the switch from the soon-to-be unsupported Webroot to a new anti-spam solution provider should contact SpamTitan to discuss the options available. Advice can be offered on migration from Webroot and other anti-spam providers to ensure a seamless transition.
New SpamTitan customers also benefit from a totally free 30-day trial period, with prices starting from as little as $395 per month.
Further information on anti-spam, anti-phishing, and web-filtering solutions can be obtained by emailing the Customer Service team on info@spamtitan.com
by G Hunt |
August 7, 2011 |
Spam News
Firefox is a popular web browser created by a global non-for-profit organization. It boasts excellent controls against viruses and has proved popular for its security features, anti-tracking functionality, and its speed. However, as with all web browsers, it requires frequent updates to remain 100% virus-free.
Updates must be installed promptly to keep the browser secure. Users are alerted to these new updates as and when they are released, and installing them is a quick and simple process.
These updates are announced via the browser. Users of Firefox are not emailed reminders to update their browser to the latest version. That said, a number of emails have recently been received by users of Firefox alerting them to the urgent need to download the latest version of the browser. These emails are part of a fake Firefox update scam.
Fake Firefox Update Scam Discovered
If you receive an email telling you to update your Firefox version “for security reasons” you will not be alone. Many other users have received similar emails. These are not genuine. They are part of a new email spam campaign that attempts to fool recipients that their browser is out of date and an update is essential.
To make it as easy as possible to install the necessary security protections, a handy link is included in the email. This will take the user to the Firefox website where they can download the latest version of the web browser. However, be warned. The link is fake, and by clicking the link and attempting to improve security, all you will be doing is downloading a Trojan to your device. That Trojan will be used to steal your passwords.
This is a common tactic used by email spammers. Emails are sent which contain important information on security updates to fool the unwary into downloading malicious software. The emails play on data security fears and warn of repercussions for not taking the requested action. Many email recipients are fooled into clicking links or opening infected attachments as a result.
SpamTitan regularly issues warnings about the latest spam campaigns, fake emails and new malware as they are discovered. Internet users are instructed to take precautions to protect themselves against these attacks.
Fortunately, there are some very easy steps that can be taken to reduce the risk of attack via email. Receiving a spam or phishing email will not compromise your system (generally speaking) unless an action is taken, such as opening an email attachment or clicking on a link supplied in the email. Consequently, protecting yourself from attack can be quite straightforward.
SpamTitan Financial Preservation Tips
Don’t give hackers the data they need to empty your bank accounts and max out your credit cards. Follow the simple instructions below and you can protect your hard earned cash.
- Do not open any suspicious attachments sent to you by email and do not download them to your computer. You must be sure of the genuineness of an attachment before you open it
- Do not click on links to websites that you do not know
- Check all links before clicking as they may have been faked. Hover your mouse arrow over the link and you will find out where that link will direct you. If you are unsure, never click
- Check the ‘From’ field. The name may be familiar, but the email address from which the email has been sent may not be. Do not take any chances. The ‘From’ field can easily be faked
- If you have not requested a new password, never click on a link that asks you to reset it
- Never divulge sensitive information in an email, even if requested to do so. IT departments and legitimate web service providers will never ask for your login details and passwords to be sent by email
- Always keep your anti-virus and anti-malware definitions up to date. They are released on a daily basis and sometimes every few hours. Set your software to download these automatically
- Install a spam filter to prevent spam and phishing emails from being delivered to your inbox


