Blog
by titanadmin | Feb 8, 2017 | Email Scams, Industry News, Phishing & Email Spam, Spam Software, Website Filtering |
Ransomware attacks on British schools have soared in recent weeks. The problem has become so serious that the British National Fraud and Cyber Crime Reporting Center, also known as Action Fraud, has issued a new ransomware warning to British schools.
Ransomware has grown in popularity with cybercriminals over the past 2 years, with attacks on organizations around the world soaring in 2016. 2017 may only be a few weeks old, but ransomware attacks are continuing at the high levels seen in 2016. Security experts predict that 2017 will see even more cyberattacks on schools and other educational institutions. Ransomware the attack method of choice.
Ransomware is a form of malware that encrypts data on a compromised system. A wide range of file types are locked with powerful encryption and a ransom demand is issued. If payment is made, the attackers claim they will supply the key to unlock the encryption. Without the key – the sole copy is held by the attackers – data will remain locked forever.
Some forms of ransomware have been cracked and free decryptors made available, but they number in the few. The majority of ransomware variants have yet to be cracked. Recovery depends on payment of the ransom or the wiping of the attacked system and restoration of files from backups.
While a standard charge per encrypted device was the norm early last year, ransomware is now more sophisticated. The attackers are able to set their payment demand based on the types of files encrypted, the extent of the infection, and the perceived likelihood of the victim paying up. Ransomware attacks on British schools have seen ransom demands of an average of £8,000 issued.
Ransomware Attacks on British Schools are Targeted, Not Random
Many ransomware attacks are random – Spam emails are sent in the millions in the hope that some of them reach inboxes and are opened by employees. However, ransomware attacks on British schools have seen a different approach used. Recent attacks have been highly targeted.
Rather than send emails out en masse, the spate of recent ransomware attacks on British schools start with a phone call. In order to find their target, the attackers call the school and ask for the email address of the head teacher. The email address is required because sensitive information needs to be sent that should only be read by the head teacher. Information such as mental health assessment forms and teacher guidance forms.
An email is then crafted and sent to the head teacher; addressed to that individual by name. While there are many types of ransomware emails, a number of recent ransomware attacks on British schools involved an email that appears to have been sent by the Department of Education. Other cases have involved the impersonation of the Department of Work and Pensions and telecom providers.
In the text of the email the attacker explains that they have sent some information in an attached file which is important and needs to be read. The attached file, usually in compressed format such as .ZIP or .RAR, contains files that install ransomware if opened.
These ransomware downloaders may be JavaScript files, Word or Excel macros, or a host of other file types. In some cases, links are used instead of attachments. The links are masked so they appear to be official webpages; on the Department for Education website for example. In the case of links, they direct the recipient to a webpage containing an exploit kit or other form of file downloader. Just visiting that link could infect the user’s computer, mapped network drives, and portable storage devices.
How to Prevent Ransomware Attacks
Ransomware attacks on British schools can be highly sophisticated, although risk can be effectively mitigated.
- Ensure all staff with computer access are made aware of the risk of ransomware attacks
- Provide cybersecurity training to all staff, including how to identify ransomware and phishing emails
- Never open attachments or visit links in emails sent from unknown senders
- Implement a spam filter to capture and quarantine malicious spam emails
- Use a web filtering solution to prevent staff members from visiting malicious links and from downloading ‘risky’ files
- Ensure all software is kept up to date and patches are applied promptly
- Keep all anti-virus and anti-malware solutions up to date, setting updates to occur automatically
- Restrict the use of administrator accounts – Only use accounts with high levels of privileges for specific tasks
It is also essential to ensure that backups of all data are made on a daily basis and backup devices are disconnected after backups have been performed. Data should ideally be backed up to the cloud and on a physical backup device. In the event of an attack, data can then be recovered without paying the ransom.
by titanadmin | Feb 7, 2017 | Email Scams, Phishing & Email Spam, Spam Software |
University phishing scams targeting students have increased in recent months. Targeting some of the most well educated individuals may not appear to be the most rewarding strategy for scammers, but students are falling for these university phishing scams in their droves.
University Phishing Scams are Becoming Difficult to Identify
Awareness of phishing tactics has certainly improved thanks to educational programs, email warnings, and media coverage of phishing attacks, but in response, cybercriminals have got better at scamming. Today, phishing emails can be difficult to identify. In fact, in many cases, it is virtually impossible to tell a genuine email from a scam.
While students may be aware of the risks of clicking links in emails from unknown senders, the same cannot be said when the emails are sent from a contact. Emails from university IT departments, professors and colleagues are likely to be opened. Students’ guard is let down when the sender of the email is known.
When a convincing request is included, students often respond and have no idea that they have been scammed into revealing their login credentials or disclosing other sensitive information. All it takes is for one email account of a student to be compromised to start the process. Emails are then sent to that individual’s email address book. A number of those contacts respond. The same happens with their contacts and so on. Given that there are supposedly six degrees of separation between all individuals on the planet, it is easy to see how fast malware infections can spread and how multiple email accounts can be compromised rapidly.
University phishing scams have been increasing for some time, although the past few months have seen even more scams emails sent. Recently, the University of Connecticut sent warnings out to students following a spate of phishing scams. Some of those scams involved the impersonation of the University president. Students at the University of Georgia have also been targeted.
In the case of the latter, one student’s email account was compromised after she responded to a phishing email sent from UGA associate. The email did not arouse any suspicions because the contact was known. In the email the student was told that it was important for her to change her password. Failure to do so would result in her being locked out of her email account. She responded by clicking the link and changing her password. However, what she had done was disclose her old password and her new one to the attacker.
The attacker then used those credentials to set up a mail forwarder on the email account. The student only found out after querying why she was no longer receiving emails with the IT help desk. After investigating, the mail forwarder was discovered.
Other students were similarly targeted and their emails accounts were used to send out huge volumes of spam emails. It was only when spamming complaints were received about the compromised accounts that the problem was identified.
These university phishing scams are conducted for a wide range of nefarious purposes. Spamming and mail forwarders may cause limited harm, but that may not always be the case. Malware infections can result in serious financial harm to students and universities. Ransomware installations can occur after students respond to phishing campaigns, and those attacks can cost tens of thousands of dollars to resolve.
How to Protect Students and Networks from the Scammers
Since these phishing scams are now so hard to identify, training on email and cybersecurity best practices is no longer as effective as it once was. Technological solutions are therefore required to prevent emails from being delivered and to stop end users from being directed to malicious websites.
SpamTitan is an ideal spam filtering solution for universities. SpamTitan blocks 99.97% of spam emails and 100% of known malware. The solution is cost effective to install, easy to administer, and no additional hardware is required or any software updates necessary.
When used in conjunction with WebTitan – TitanHQ’s powerful web filtering solution –all attempts to visit malicious links and known phishing websites can be blocked.
Both solutions are available on a 30-day no obligation free trial. If you want to ensure your students and university networks are properly protected, contact the TitanHQ sales team today to register for the trials and discover the difference that each solution can make.
by titanadmin | Feb 6, 2017 | Email Scams, Phishing & Email Spam, Spam News |
Sophisticated phishing emails and elaborate web-based scams are being used to target students at the University of Connecticut. The extent to which students have been targeted with these scams has prompted UConn Chief Information Officer and Provost for Information Technology to send a warning to all students to be on high alert.
A number of students at the university have received sophisticated phishing emails in recent months that appear to have been sent from University President Susan Herbst. Like many universities and other educational establishments, the email system is protected with a spam filter. The majority of spam and scam emails are filtered out, although some do make it through. If these emails are delivered to students, there is a high probability that they will be opened. After all, the messages do appear to have been sent from the University president.
The emails contain malicious attachments or links to websites that attempt to steal login information and the scam is sophisticated and highly convincing. Many students would be unaware that they have been scammed after disclosing their login credentials.
The same can be said of malware infections, which usually occur silently when a malicious website is visited. Criminals are attempting to install key-loggers that record all sensitive data entered on compromised computers.
These scams are intended to get students to disclose their bank account information, credit card data, or Social Security numbers and personal information. The attackers can then use this information for a wide range of nefarious purposes including identity theft.
Sophisticated Phishing Emails are the New Norm
Email scams of old were quite easy to identify. They often included many grammatical and spelling mistakes and included offers that sounded too good to be true. However, today, sophisticated phishing emails are the new norm and they can be very difficult to identify. Emails are sent from authority figures, are grammatically perfect, and the attackers use wide range of social engineering techniques to get victims to disclose sensitive data or take a particular action.
The scammers are also increasingly sending highly targeted emails. These ‘spear phishing’ emails use personal information unique to the recipient to add credibility. Information is often obtained from social media and professional networking sites.
One of the latest UConn email scams includes information about Blackboard Inc., the Mail Service used by UConn. The attachment has the title “Exclusive Important Announcement from President Susan Herbst.”
Warnings have been issued by email to all students alerting them to this scam and advising them to exercise caution when using email and surfing the Internet. Students have been told not to login on any websites that do not have a valid security certificate.
A Spam Filter and Web Filter in Tandem Offer Greater Protection Against Phishing Attacks
Users should always exercise caution when using email. Attachments from unknown senders should not be opened and links contained in emails from unfamiliar sources should not be visited. However, curiosity often gets the better of students and malicious links are often unwittingly visited.
For this reason, in addition to using an advanced spam filtering solution – such as SpamTitan – universities and other educational establishments should also employ a web filtering solution. The spam filter will block the vast majority of malicious messages. The web filter will ensure that malicious websites and infected webpages cannot be visited. In tandem, a spam filter and web filter will offer far greater protection against phishing attacks and malware/ransomware infections.
by titanadmin | Feb 3, 2017 | Email Scams, Phishing & Email Spam, Spam Advice, Spam News |
A W-2 Form phishing scam that has been extensively used to con businesses out of the tax information of their employees is now being used on educational institutions. School districts need to be on high alert as cybercriminals have them fixed in their cross-hairs.
Over the past few weeks, many school districts have fallen victim to the scammers and have disclosed the W-2 Form data of employees. Teachers, teaching assistants, and other members of school staff have had their Social Security numbers and earnings information sent to fraudsters. The data are used to file fraudulent tax returns in victims’ names.
At face value, the W-2 Form phishing scam is one of the simplest con-tricks used by cybercriminals. It involves sending an email to a member of the HR or payroll team asking for the W-2 Forms of all employees to be sent via email. Why would any employee send this highly sensitive data? Because the email appears to have been sent from individuals within the school district who have a genuine need for the information. This is why the W-2 Form phishing scam is so effective. In many cases, suspicions are not aroused for a number of days after the emails have been sent. By that time, fraudulent tax returns may have been filed in the names of all of the victims.
It is unknown how many school districts have been targeted to date with this W-2 Form phishing scam, although 10 school districts in the United States have announced that their employees have fallen for the scam this year and have emailed W-2 Form data to the attackers. In total, 23 organizations have announced that an employee has fallen for a W-2 Form phishing scam in 2017, and at least 145 organizations fell for similar scams last year.
Due to the number of attacks, the IRS issued a warning in early 2016 to alert all organizations to the threat. The increase in attacks in 2017 has prompted the IRS to issue a warning once again. While corporations are at risk, the IRS has issued a warning specifically mentioning school districts, as well as non-profits and tribal organizations.
The IRS warning explains how cybercriminals have started even earlier this year. While the W-2 Form phishing scam emerged last year, many attacks occurred relatively late in the tax season. Cybercriminals are attempting to get the data sooner this year. The sooner a fake tax return is filed, the greater the chance that a refund will be issued.
A variety of spoofing techniques are employed to make the email appear like it has come from the email account of an executive or other individual high up in the organization. In some cases, criminals have first compromised the email account of a board member, making the scam harder to identify.
This year has also seen a new twist to the scam with victims targeted twice. In addition to the W-2 Form scam, the victims are also subjected to a wire transfer scam. After W-2 Forms have been sent, a wire transfer request is made to the payroll department. Some organizations have been hit with both scams and have disclosed employees’ tax information and then made a wire transfer of several thousand dollars to the same attackers.
Protecting against these scams requires a combination of technology, training and policy/procedural updates. The first step for all organizations – including school districts – is to send an email to all HR and payroll staff warning them about these phishing scams. Staff must be made aware of the scam and told to be vigilant.
Policies and procedures should be updated requiring payroll and HR staff to authenticate any email request for W-2 Form data by telephone prior to sending the information.
An advanced spam filter – such as SpamTitan – can also greatly reduce the risk of W-2 Form scam emails being delivered to end users’ inboxes. Blocking suspicious emails will reduce reliance on training and user awareness of these scams. The spam filter will also be effective at blocking further scams and other malicious emails from being delivered.
by titanadmin | Jan 31, 2017 | Email Scams, Phishing & Email Spam, Spam News |
Osiris ransomware is the latest variant of Locky. As with other versions of the ransomware, there is no free way of unlocking encrypted files if a viable backup of data does not exist.
Cybercriminals use a variety of techniques and attack vectors to spread malicious files such as ransomware and malware. Exploit kits are popular as they can be hidden on websites and used to silently probe visitors’ browsers for vulnerabilities in plugins such as Adobe Flash, Microsoft Silverlight, and Oracle Java. Those vulnerabilities are leveraged to download malware. Malvertising – malicious web adverts – are often used to direct users to these malicious webpages; however, all too often, links to these websites are sent via spam email.
The rise in malware and ransomware attacks over the past few years has prompted many organizations to start providing security awareness training to staff members. Employees are instructed never to click on a link contained in an email unless they are sure that it is genuine.
However, even with security awareness training, a great many employees inadvertently infect their computers with malware or accidentally download ransomware. One of the biggest problems is not malicious links in spam email but malicious attachments. Cybercriminals have increased the use of malicious file attachments in the last year, especially to infect end users with ransomware.
One of the biggest ransomware threats in the past 12 months has been Locky. Locky has been spread via exploit kits in the past, although spam email is now primarily used to infect users.
Office Macros Used to Infect Computers with Osiris Ransomware
The gang behind Locky frequently updates the ransomware, as well as the methods used to fool end users into installing the malicious file-encryptor. The latest Locky variant – Osiris ransomware – encrypts files and adds the .osiris extension to encrypted files.
Locky is commonly spread via malicious macros in Word documents. Typically, the malicious Word documents claim to be invoices, purchase orders, or notifications of missed parcel deliveries.
However, a recent campaign used to distribute the Osiris ransomware variant switches from .DOC files to Excel spreadsheets (.XLS). Recipients of the emails are told the Excel spreadsheet is an invoice. Opening the attached Excel spreadsheet will not automatically result in an Osiris ransomware infection if macros have not been set to run automatically. The user will be presented with a blank spreadsheet and a prompt to enable macros to view the content of the file.
Clicking on ‘Enable Content’ will launch a VBA script that downloads a Dynamic Link Library (DLL) file, which is automatically executed using the Windows file Rundll32.exe. That DLL file is used to download Osiris ransomware. Osiris ransomware encrypts a wide range of file types and deletes Windows Shadow Volume Copies, preventing the user from restoring the computer to the configuration before the ransomware was installed. The only option for recovery from an Osiris ransomware infection is to pay the ransom demand or to wipe the system and restore files from backups.
Protecting Networks From E-Mail-Based Ransomware and Malware Attacks
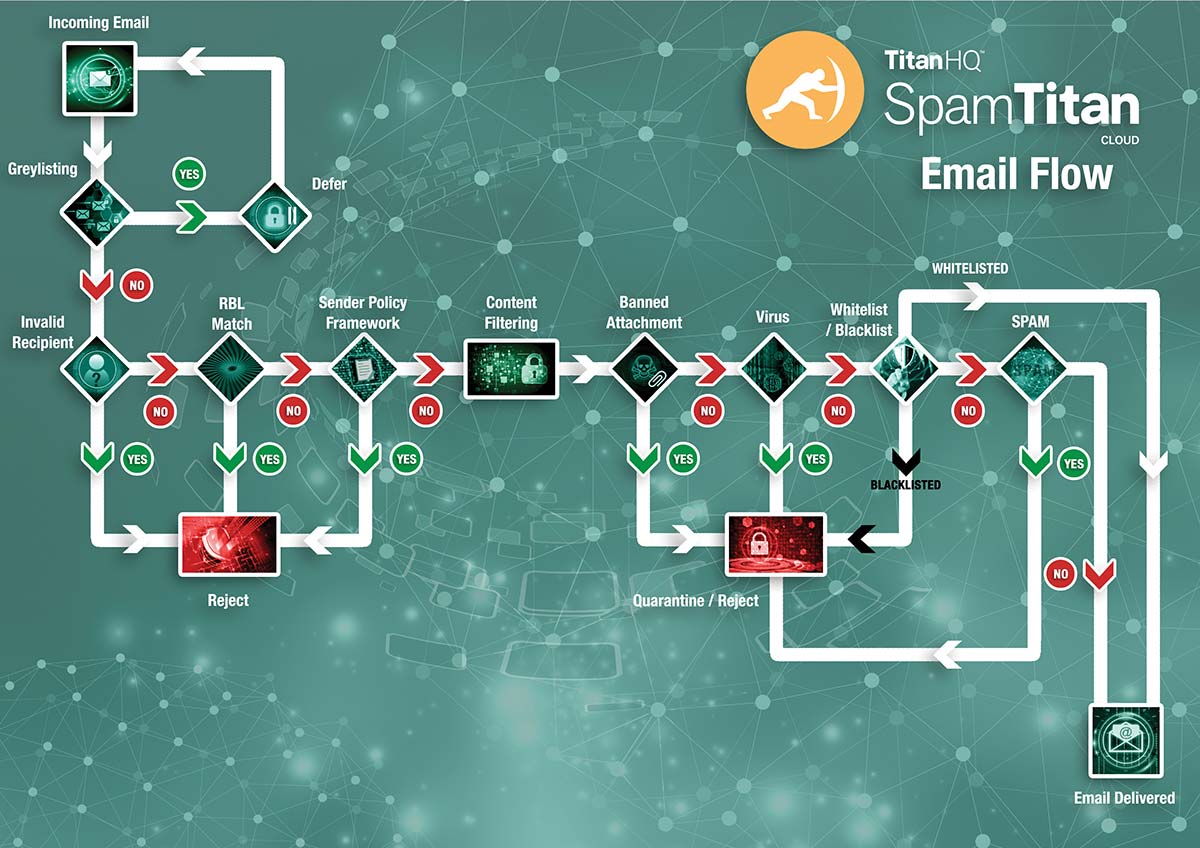
An advanced spam filtering solution such as SpamTitan can be used to block the vast majority of email-borne threats. SpamTitan performs a wide range of front line tests to rapidly identify spam email and prevent it from being delivered, including RBL, SPF, Greylisting and SMTP controls.
SpamTitan uses two enterprise-class anti-virus engines to scan for malicious attachments – Bitdefender and ClamAV – to maximize detection rates.
SpamTitan can also be configured to block specific files attachments commonly used by cybercriminals to infect end users: EXE files and JavaScript files for example. The contents of compressed files are also automatically scanned by SpamTitan.
Host-based tests are performed to examine mail headers, while the contents of messages are subjected to a Bayesian analysis to identify common spam signatures and spam-like content. Messages are also scanned for malicious links.
These extensive tests ensure SpamTitan blocks 99.97% of spam emails, preventing malicious messages from being delivered to end users. SpamTitan has also been independently tested and shown to have an exceptionally low false positive rate of just 0.03%.
If you want to keep your network protected from malicious spam emails and reduce reliance on employees’ spam detection abilities, contact the TitanHQ team today. SpamTitan is available on a 30-day free trial, allowing you to fully test the product and discover the difference SpamTitan makes at your organization before committing to a purchase.
by titanadmin | Jan 25, 2017 | Email Scams, Phishing & Email Spam, Spam News, Spam Software |
Its tax season in the United States, which means the start of scamming season. W2 phishing scams and other tax-related email and telephone scams are rife at this time of year. Businesses need to be particularly careful. There have already been a number of victims of W2 phishing scams and the year has barely started.
2016 Saw a 400% Rise in Tax Season Phishing and Malware Incidents
Tax season in the United States runs from the start of January to April 15. It is the time of year when Americans calculate how much tax they need to pay from the previous financial year. It is also a busy time for cybercriminals. They will not be filing their own tax returns however. Instead they are concentrating on filing tax returns on behalf of their victims.
In order for tax refunds to be fraudulently filed, cybercriminals need information about their victims. Given the number of data breaches that have resulted in the theft of Social Security numbers in the past 12 months, 2017 could well be a record year for tax scams.
However, while past data breaches can provide cybercriminals with the information they need to file fraudulent tax returns, tax season usually sees a massive increase in phishing scams. The sole purpose of these scams is to get victims to reveal their Social Security numbers and the other personal information necessary to file tax returns.
Since the IRS started allowing Americans to e-file their tax returns, scammers had a new option for filing fraudulent tax returns. Phishing emails claiming to have been sent by the IRS request the recipients update their IRS e-file. A link is included in the emails for this purpose. Clicking on the link in the emails will not direct the recipient to the IRS website, but a spoofed version of the site. The information entered online is then used to e-file on behalf of the victims and the scammers pocket the tax refunds.
In 2016, the IRS reported a massive increase in phishing and malware incidents. These scams and malware infections increased by an incredible 400%. The massive rise in scams prompted the IRS to issue a warning to Americans about the scams, with the IRS confirming that it does not initiate contact with taxpayers by email to request personal or financial information.
2017 is likely to be no different. Until April 15, tax-related scams are likely to be rife. All Americans should therefore be wary and must exercise caution.
Tax Season Sees a Massive Rise in W2 Phishing Scams
While consumers are at risk. Businesses in the United States are also extensively targeted at this time of year. The scammers impersonate CEOs, CFOs, and other individuals with authority and make requests for W2 data and other financial information about employees. The requests can be highly convincing and each year many employees fall for these types of scams. The scammers are well aware that some employees would be nervous about questioning a request that has been emailed from their SEO or CFO.
It is difficult to determine how many attempted W2 phishing scams took place last year, but in the first quarter of 2016, at least 41 U.S companies reported that they were the victims of successful W2 phishing scams. Employees were sent email requests to send W2 data by return and they responded. By doing so, employees’ tax information was sent directly to the scammers’ inboxes.
2017 is not yet a month old, yet already W2 phishing scams have been reported. The week, the Tipton County Schools District in western Tennessee reported that it had fallen victim to one of these W2 phishing scams. The attacker had posed as the director of the schools and had requested W2 tax data on all employees. W2 form data were then emailed to the attacker by an employee.
A similar email phishing scam was reported to have been used to attack 8 school districts in Missouri, according to a report by the Missouri Department of Elementary and Secondary Education. In this case, only one of the eight school districts responded to the scam: An employee from the Odessa School District was fooled and send the tax details of the district’s employees to the attackers.
It is not only schools that are being targeted. A hospital in Campbell County, Wyoming was attacked this week. According to a Campbell County Health news release, a hospital executive was impersonated in this attack. A 66-year old hospital worker fell for the scam and emailed W-2 information about employees as requested.
Preventing successful W2 phishing scams requires a combination of technological solutions, employee training, and updates to policies and procedures. All employees with access to sensitive data must be advised of the risk and told to exercise caution. Policies should be introduced that require all email requests for employees’ tax information to be authenticated via telephone or other means. Organizations should also implement a robust spam filtering solution to prevent the scam emails from being delivered to employees’ inboxes.
However, if nothing is done to mitigate risk, 2017 is likely to be another record breaking year for the scammers.
by titanadmin | Jan 24, 2017 | Email Scams, Phishing & Email Spam, Spam News |
You have no doubt heard of Locky and Cryptolocker, but what about Satan ransomware? Unfortunately, you may soon be introduced to this new ransomware variant. No matter where your organization is based, if you do not have a host of cybersecurity defenses to block ransomware attacks, this nasty file-encryptor may be installed on your network.
Satan Ransomware is being offered to any would-be hacker or cybercriminal free of charge via an affiliate model known as ransomware-as-a-service or RaaS. The idea behind RaaS is simple. Developers of ransomware can infect more computers and networks if they get an army of helpers to distribute their malicious software. Anyone willing to commit a little time to distributing the ransomware will receive a cut of any profits.
Ransomware authors commonly charge a nominal fee for individuals to participate in these RaaS schemes, in addition to taking a percentage of any ransomware payments that are generated. In the case of Satan ransomware, the developers offer RaaS totally free of charge. Anyone who wants to distribute the malicious software is free to do so. In exchange for their efforts they get to keep 70% of the ransom payments they generate. The remaining 30% goes to the ransomware authors. The gang behind the RaaS also offers higher percentages as infections increase as a reward for effort. All that is required to get started is to create a username and password. Access to the ransomware kit can then be gained.
What is alarming is how easy it is to participate in this RaaS scheme and custom-craft the malware. The gang behind the campaign has developed an affiliate console that allows the malware to be tweaked. The ransom amount can be easily set, as can the time frame for making payments and how much the ransom will increase if the payment deadline is exceeded.
Help is also offered with the distribution of the malware. Assistance is provided to make droppers that install the malware on victims’ systems. Help is offered to create malicious Word macros and CHM installers that can be used in spam email campaigns. Help is also offered to encrypt the ransomware to avoid detection. Even multi-language support is provided. Any would-be attacker can craft ransom demands in multiple languages via the RaaS affiliate console.
Satan ransomware performs a check to determine if it is running on a virtual machine. If it is, the ransomware will terminate. If not, it will run and will search for over 350 different file types. Those files will be locked with powerful encryption. File extensions are changed to. stn and the file names are scrambled to make it harder for victims to identify individual files. The ransomware will also wipe all free space on the hard drive before the ransom demand is dropped onto the desktop.
There is no decryptor for Satan ransomware. Recovery without paying the ransom will depend on organizations being able to restore files from backups. Since the ransomware also encrypts backup files, those backups will have to be in the cloud or on isolated devices.
RaaS is nothing new, but what is so worrying about Satan ransomware is how easy it has been made for affiliates. Next to no skill is required to run a ransomware campaign and that is likely to see many individuals take part in the RaaS program.
by titanadmin | Jan 23, 2017 | Internet Security, Network Security |
Take a look at the list of the worst passwords of 2016 and you would be forgiven for thinking you are looking at the worst password list for 2015. Or 2014 for that matter. Little appears to have changed year on year, even though the risk to network and data security from the use of weak passwords is considerable.
Every year, SplashData compiles a list of the worst 25 passwords of the year. 2017 is the sixth consecutive year when the company has produced its list. Given the number of largescale data breaches that occurred in 2016, it would be reasonable to assume that organizations would take a proactive step and introduce restrictions on the passwords that can be used to secure corporate networks, computers, and email accounts. Many still don’t. It is still possible for end users to use passwords with no capital letters (or no letters at all), no symbols, and consecutive number strings are still permitted.
Should a hacker attempt a brute force attack – attempting to gain access using an automated system that guesses potential password combinations – a weak password would allow access to be gained incredibly quickly.
If any of the passwords from the list of the worst passwords of 2016 were used, it would be like there was no password required at all. How quickly can a hacker crack one of these passwords? According to Random ize, most of the passcodes on the list of the worst passwords of 2016 could be guessed in under a second. BetterBuys is more pessimistic, claiming most could be guessed in about 0.25 milliseconds.
To compile its list, SplashData scraped data dumps that included passwords. 2016 saw a great deal of data published on darknet sites by cybercriminals that had succeeded in breaching company defenses. For its list, SplashData analyzed more than 5 million credentials, most of which came from data breaches in North America and Europe.
The most commonly used password in 2016 was 123456, as it was in 2015. Password was the second most common password in 2016. There was no change in the top two worst passwords even though cybersecurity awareness has increased. As we saw last year, even John Podesta, chairman of Hillary Clinton’s 2016 presidential campaign, allegedly used a variation of the word password to “secure” his accounts. That poor choice clearly demonstrated that the use of poor passwords offers very little protection against hackers.
The worst password of 2016 was used on an incredible 4% of user accounts, and almost as many individuals used password. SplashData says around 10% of individuals use a password that was on the list of the 25 worst passwords of 2016.
Some individuals have got clever, or so they think. They use a variation of ‘password’. However, password1 and passw0rd are barely any better. The small change would not delay a hacker by any noticeable degree. Hackers are well aware of the use of numbers to replace letters and other techniques to make passwords more secure, such as adding a digit to the end of a word. – Password1 for example.
SplashData’s List of the Worst Passwords of 2016
- 123456
- password
- 12345
- 12345678
- football
- qwerty
- 1234567890
- 1234567
- princess
- 1234
- login
- welcome
- solo
- abc123
- admin
- 121212
- flower
- passw0rd
- dragon
- sunshine
- master
- hottie
- loveme
- zaq1zaq1
- password1
If you were wondering how the list has changed year on year, take a look at last year’s list and you will see a number of similarities.
List of the Worst Passwords of 2015
- 123456
- password
- 12345678
- qwerty
- 12345
- 123456789
- football
- 1234
- 1234567
- baseball
- welcome
- 1234567890
- abc123
- 111111
- 1qaz2wsx
- dragon
- master
- monkey
- letmein
- login
- princess
- qwertyuiop
- solo
- passw0rd
- starwars
In order to make it harder for hackers, complex passwords should be chosen. Passwords should be at least 9 characters, contain numbers, letters (lower and upper case), and symbols. They should not be words, although pass phrases of 15 or more characters would be acceptable. Passwords should also be changed frequently. The use of a password manager is recommended to ensure that these complex passwords can be remembered.
by titanadmin | Jan 20, 2017 | Email Scams, Phishing & Email Spam, Spam News |
A spate of Gmail phishing attacks has hit the headlines this week. While the phishing scam is not new – it was first identified around a year ago – cybercriminals have adopted the campaign once more. The phishing emails are used to obtain Gmail login credentials are highly convincing,. A number of different tactics are used to evade detection, some of which are likely to fool even the most security aware individuals.
The Gmail phishing attacks start with an email sent to a Gmail account. Security aware individuals would be wary about an email sent from an unknown source. However, these attacks involve emails sent from a contact in the target’s address book. The email addresses are not masked to make them look like they have come from a contact. The email is actually sent from a contact’s account that has already been compromised.
Email recipients are far more likely to open emails sent from their contacts. Many people do not perform any further checks if the sender is known to them. They assume that emails are genuine solely from the source.
However, that is not the only technique used to fool targets. The attackers also use information that has been taken from the contact’s sent and received messages and add this to the email. An screenshot of an attachment or image that has already been included in a previous email between the contact and the target is included in the message. Even if the target is slightly suspicious about receiving an email, these additional touches should allay concern.
The aim of the email is to get the target to click on the image screenshot. Doing so will direct them to a Gmail login page where the target is required to sign in again. While this is perhaps odd, the page that the user is directed to looks exactly as it should. The page exactly mirrors what the user would normally expect.
Checking the website address bar should reveal that the site is not genuine; however, in this case it does not. The address bar shows the site is secure – HTTPS – and the web address includes accounts.google.com. The only sign of the scam is the inclusion of ‘data.text/html’ before accounts.google.com in the address bar.
Entering in account credentials will send that information directly to the attackers. The response is lightning quick. Account credentials are immediately used to log into the victim’s account. Before the victim even suspects they have been scammed, the entire contents of their Gmail account could be stolen, including sent and received emails and the address book. Contacts will be subjected to these Gmail phishing attacks in the same fashion.
Google is aware of the scam and is currently developing mitigations to prevent these types of attacks from occurring. In the meantime, however, users of Gmail should be particularly wary. Many users just glance at the address bar and look for the HTTPS and the web address. Failure to very carefully check the address bar and protocol before entering login credentials can – and certainly will in this case – result in the user’s account being compromised. Gmail accounts contain a huge amount of personal information. Information that could be used in future spear phishing attacks, extortion attempts, and other scams on the target and their contacts.
by titanadmin | Jan 17, 2017 | Phishing & Email Spam, Spam News |
A new ransomware variant – Spora ransomware – has been identified by Emisoft which features a new twist. Victims have a wide range of their files encrypted as with other forms of file-encrypting malware, but they are given the option of preventing future ransomware attacks if they pay up.
The attackers would not be able to prevent attacks performed by other gangs – with other ransomware variants – although if the attackers can be believed, victims would only be attacked with Spora once. That is, if they choose the more expensive option of ‘Spora immunity’ rather than just paying to unlock the encryption.
The bad news for the victims is that payment will be required to unlock the infection if a viable backup of data does not exist. At present, there is no decryptor for Spora.
Emisoft reports that the encryption used is particularly strong, and even if a decryptor was developed, it would only be effective against a single user due to the complex method of encryption used – a combination of AES and RSA keys using the Windows CryptoAPI.
In contrast to many ransomware variants that communicate with a command and control server, Spora ransomware does not receive any C&C instructions. This means that files can be encrypted even if the computer has no Internet connection.
The authors have also not set a fixed ransom amount, as this depend on the ‘value’ of the encrypted data. The ransom payment will be set based on who the user is and the files that have been encrypted. Before files are encrypted, a check is performed to see who has been infected. Encrypted files are sorted based on extension type and the information is combined into the .KEY file along with information about the user. The .key file must be supplied in the payment portal. An HTML file is also created on the desktop with details of how payment can be made.
The ransomware is being spread via spam email. Infection occurs when an email recipient opens the infected attachment. The attached file appears to be a genuine PDF invoice, although it includes a double file extension which masks the fact it is actually a .HTA file. Infection occurs via JScript and VBScript contained in the file.
Opening the file launches a Wordpad file which displays an error message saying the file is invalid. In the background, the ransomware will be encrypting data.
Emisoft reports that the ransomware is slick and appears highly professional. Typically, the first versions of ransomware invariably contain multiple flaws that allow decryptors to be developed. In this case, there appear to be none. Spora ransomware also tracks infections via different campaigns. The information will likely be used to determine the effectiveness of different campaigns and could be used to direct future attacks.
The slick design of the HTML ransom note and the payment portal show considerable work has gone into the creation of this new ransomware. Emisoft suggests that Spora ransomware has been developed specifically for the ransomware-as-a-service market.
Prevention remains the best defense. Since Spora ransomware is spread via spam email, blocking malicious messages is the best defense against infection, while recovery will only be possible by paying the ransom demand or restoring data from a backup.
by titanadmin | Jan 16, 2017 | Internet Security, Network Security, Phishing & Email Spam |
A Barts Health malware attack forced the shutdown of hospital IT systems on Friday last week as the UK NHS Trust attempted to limit the damage caused and contain the infection.
Barts Health is the largest NHS Trust in the United Kingdom, operating six hospitals in the capital: Mile End Hospital, Newham University Hospital, St Bartholomew’s Hospital, The London Chest Hospital, The Royal London Hospital, and Whipps Cross University Hospital.
The Barts Health malware attack occurred on Friday 13, 2016. Given the number of ransomware attacks on healthcare organizations in recent months, rumors started to quickly circulate that this was another healthcare ransomware attack.
A statement was released on Friday claiming the Trust had experienced an ‘IT attack,’ and that as a precaution, a number of drives were taken offline to prevent the spread of the infection. The type of malware that had been installed was not known, although the NHS trust did say in its statement that it did not believe ransomware was involved.
Multiple drives were shut down following the discovery of the malware including those used by the pathology department, although patient data were unaffected and the NHS Trust’s Cerner Millennium patient administration system remained operational, as did the systems used by the radiology department.
Today, Barts Health reports that all of its systems are back online and the infection has been removed. Medical services for patients were not affected, although Barts Health said due to the need for requests to be processed manually, it may take a few days for the pathology department to deal with the backlog.
Barts Health also reiterated that at no point were patient medical records compromised. No mention has been made about how the malware was installed and the type of malware involved was not announced. However, the Barts Health malware attack involved a form of malware that had not previously been seen and was a ‘Trojan Malware.’
The Trust said “whilst it had the potential to do significant damage to computer network files, our measures to contain the virus were successful”.
Ransomware Attacks on UK Hospitals
In November last year, the Northern Lincolnshire and Goole NHS Trust was attacked with ransomware which resulted in IT systems at three hospitals being crippled. As a result of that attack, the NHS Trust was forced to cancel 2,800 operations and appointments while the infection was removed and systems restored. The majority of IT systems had to be taken offline, hence the major disruption to medical services.
While Locky and Samas have been used extensively in attacks on U.S. hospitals, the Northern Lincolnshire and Goole NHS Trust ransomware attack involved a ransomware variant known as Globe2 – A relativity new variant that was first identified in August 2016.
Globe ransomware has been spread primarily via spam email and malicious file attachments. Opening the file attachment triggers the downloading of the ransomware. As with other ransomware variants, the attachments appear to be files such as invoices or medical test results.
Malicious links are also used to spread ransomware infections. Clicking a link directs users to malicious websites where ransomware is automatically downloaded. Fortunately for organizations attacked with Globe ransomware, a decryptor has been developed by Emisoft, which is available for free download.
However, relatively few ransomware variants have been cracked. Recovery can also take time resulting in considerable disruption to business processes. Ensuring backups of all critical data are regularly made will ensure that files can be recovered without giving in to attackers’ demands.
Preventing malware and ransomware attacks requires multi-layered defenses. Since many infections occur as a result of infected email attachments and links, organizations should employ an advanced spam filtering solution such as SpamTitan. SpamTitan has been independently tested and shown to block 99.97% of spam email. SpamTitan will also block 100% of known malware.
by titanadmin | Jan 10, 2017 | Network Security, Spam Software, Website Filtering |
A Los Angeles Valley College ransomware attack has resulted in file systems being taken out of action for seven days and considerable costs being incurred to resolve the infection.
Attackers succeeded in taking control of one of the college’s servers on December 30, 2016. When staff returned after the Christmas break they discovered the computer system to be out of action and essential files locked with powerful encryption.
The attackers had succeeded in locking a wide range of file types on network drives and computers. Unfortunately, the college was unable to recover the files from a backup. Administrators therefore faced a tough decision. To try to recover from the attack without paying the ransom and risk file loss or to give in to the attacker’s demands and pay for the keys to unlock the encryption.
Los Angeles Valley College Ransomware Attack Nets Criminal Gang $28,000
Due to the extent of the infection and the number of devices affected, the ransom payment was considerable. The attackers set the price at $28,000 for the decryption keys. The ransom demand was high but the college had little in the way of options.
The ransom note that was loaded onto the college’s X-drive said if the ransom was not paid within 7 days, the unique keys to unlock the encryption would be permanently deleted. That would likely have resulted in all of the locked files being permanently lost.
The college enlisted help from cybersecurity experts to determine the likelihood of files being recovered without paying the ransom. However, college administrators were advised to dig deep and pay the attackers for the key. While there is no guarantee that paying the ransom would result in viable keys being supplied, the college’s cybersecurity experts said there was a high probability of data recovery if the ransom was paid and a very low probability of data being recovered if the ransom demand was ignored. The likely cost of resolving the infection without paying the ransom was also estimated to be higher than attempting to remove the infection. The decision was therefore made to pay the attackers in Bitcoin as requested.
The attackers made good on their promise and supplied the keys to unlock the data. Now IT staff must apply those keys and remove the encryption on the server, network drives, and the many infected computers. Fortunately for the college, a cyber insurance policy will pay out and cover the cost of the ransom and resetting systems. However, there will be other costs that need to be covered, which will must be paid by the district.
Recovery from the Los Angeles Valley College ransomware attack will not be a quick and simple process, even though the decryption keys have been supplied by the attackers. The district’s Chief Information Officer Jorge Mata said “There are often a lot of steps where there’s no coming back, and if you pick the wrong path, there’s no return.” The recovery process therefore requires care and precision and cannot be rushed. The process could well take a number of weeks. The main priority is to recover the email system. Other systems and devices will then be methodically restored.
Los Angeles Valley College Ransomware Attack One of Many Such Attacks on Educational Institutions
The Los Angeles Valley College ransomware attack has hit the headlines due to the extent of the infection and high ransom demand, but it is one of many such attacks to have occurred over the past 12 months. Educational institutions have been heavily targeted by attackers due to the value of college and school data. Educational establishments cannot risk data loss and are therefore likely to pay the ransom to regain access to files.
In the past few months, other educational institutions in the United States that have been attacked with ransomware include M.I.T, University of California-Berkeley, and Harvard University as well as many K-12 schools throughout the country. Figures from Malwarebytes suggest that 9% of ransomware attacks targeted educational establishments.
How Can Educational Institutions Protect Against Ransomware Attacks?
There are a number of steps that educational institutions can take to reduce the risk of ransomware attacks and ensure that recovery is possible without having to resort to paying a ransom. The most important step to take is to ensure that all data is backed up regularly, including the email system. Backups should be stored on air-gapped devices, not on network drives. A separate backup should be stored in the cloud.
However, backups can fail and files can be corrupted. It is therefore important that protections are implemented to prevent ransomware from being delivered via the two most common attack vectors: Email and the Internet.
Email is commonly used to deliver ransomware or malicious code that downloads the file-encrypting software. Preventing these malicious emails from being delivered to staff and students’ inboxes is therefore essential. An advanced spam filter such as SpamTitan should therefore be installed. SpamTitan blocks 99.97% of spam emails and 100% of known malware.
To protect against web-borne attacks and prevent exploit kit activity and drive-by downloads, schools and colleges should use a web filter such as WebTitan. WebTitan uses a variety of methods to block access to malicious webpages where malware and ransomware is downloaded. WebTitan can also be configured to prevent malicious third-party adverts from being displayed. These adverts – called malvertising – are commonly used to infect end users by redirecting their browsers to websites containing exploit kits.
For further information on SpamTitan and WebTitan, to find out more about how both anti-ransomware solutions can prevent infection, and to register for a free 30-day trial of both products, contact TitanHQ today.
by titanadmin | Jan 8, 2017 | Internet Security, Spam News |
Apple malware infections are relatively rare, although Mac users should not get complacent. New threats do appear from time to time and cybercriminals do target Mac users. This month another malware variant has been discovered – a type of screen locker – that is linked to a tech support scam and its Mac users that are being targeted.
The attack starts when the user clicks on a malicious link in a spam email message, although links on social media sites could also be used to direct end users to the malicious website where the attack occurs. When the malicious website is visited, malicious code on the site causes a denial-of-service attack which freezes the device as its memory is consumed.
The method of locking the computer depends on the version of OS X installed on the device. On older OS X versions, a visit to the malicious website will trigger the creation of multiple emails until the Macs memory is overloaded. The emails have the subject “Warning: Virus Detected”. Since no memory is available, users will not be able to launch any other programs. The email messages are only created as drafts – they are not delivered – although this will be sufficient to freeze the device.
Additionally, a message is loaded into the draft folder containing a phone number to call to have the virus removed. While the message appears to have been sent by Apple, this is part of the scam. This is how the attackers make their money. Removal of the infection will require payment. The attackers appear to be after credit card numbers.
The second variant of the attack affects newer OS X versions. Rather than trigger draft emails, a similar style of attack occurs via iTunes. Multiple iTunes windows are launched, similarly using up the Macs memory. As with the first attack, a message also appears with a telephone number to call to remove the infection.
These tech support scams may not involve any downloaded malware, although responding to this type of scam and providing credit card details will result in multiple payments being taken until the card provider blocks the card or credit limits are reached.
Tech support scams such as this frequently target Windows users via Firefox, IE, Edge or Chrome browsers. Multiple browser windows are launched with a tech support number displayed. A call is required to unlock the infection.
These browser-locking attacks are relatively common. Only last month, Symantec identified a new campaign which locks the screen on Windows computers and displays a browser window detailing imagery from the police force of the country where the user is based – Most of the attacks occurred in the US (FBI) and Europe (Europol).
Users are advised that they have been caught engaging in illegal online activity, usually related to pornography or child abuse. A code must be obtained from the police department to unlock the screen. A phone number is supplied which the user must call to make payment. The attackers rely on victims’ fear and embarrassment to obtain payment.
by titanadmin | Jan 5, 2017 | Email Scams, Phishing & Email Spam, Spam Advice, Spam Software |
Research conducted by the anti-phishing training company PhishMe has shown a worrying increase in phishing attacks in 2016 and has highlighted the importance of taking steps to reduce the risk of spear phishing attacks.
Unfortunately, cybercriminals are becoming much more adept at crafting highly convincing spear phishing campaigns. A wide range of social engineering techniques are used to fool employees into responding to the emails and the campaigns are becoming much harder to identify.
Unfortunately responding to these emails can result in email and network credentials being compromised, malware and ransomware being installed on corporate networks, and sensitive data being emailed to the attackers.
The study of phishing attacks in 2016 showed attacks increased by 55% year on year. PhishMe research shows that out of the successful data breaches in 2016, 90% started with a spear phishing email.
In 2016, business email compromise attacks rose by an incredible 1300%, while ransomware attacks increased 400%. Cybercriminals are attacking companies with a vigor never before seen and unfortunately many of those attacks have been successful.
The figures from the U.S. Department of Health and Human Services’ Office for Civil Rights – which tracks U.S. healthcare data breaches – show that 2016 was the worst ever year on record for healthcare data breaches. At least 323 breaches of more than 500 records occurred in 2016. Undoubtedly many more breaches have yet to be discovered.
Cybercriminals and hackers have employees firmly in their crosshairs. Unfortunately, employees are easy targets. A recent survey conducted by cybersecurity firm Avecto showed that 65% of employees are now wary about clicking on links emailed to them by strangers. Alarmingly, that means 35% are not.
The same survey showed that 68% of respondents have no concerns about clicking on links sent by their friends and colleagues. Given the extent to which email addresses and passwords have been compromised in the last year, this is incredibly worrying. 1 billion Yahoo accounts were breached and 117 million email addresses were compromised as a result of the LinkedIn breach. Gaining access to email accounts is not a problem for cybercriminals. If those accounts are used to send spear-phishing emails, the chance of links being clicked are very high. Unfortunately, all it takes is for one email account to be compromised for access to a network to be gained.
The risk of spear phishing attacks was clearly demonstrated in 2015 when the largest ever healthcare data breach was discovered. 78.8-million health plan members’ records were stolen from Anthem Inc. That breach occurred as a result of an employee of one of the insurer’s subsidiaries responding to a spear phishing email.
Anthem Inc., is the second largest health insurer in the United States and the company spends many tens of millions of highly complex cybersecurity defenses. Those multi-million dollar defenses were undone with a single email.
Organizations must take steps to reduce the risk of speak phishing attacks. Unfortunately, there is no single solution to eradicate risk. A multi-layered defense strategy is required.
An advanced anti-spam solution is essential to prevent the vast majority of spam and phishing emails from being delivered to end users. SpamTitan for example, blocks 99.97% of spam email and 100% of known malware.
Employees must be trained and their training must be tested with phishing exercises. Practice really does make perfect when it comes to identifying email scams. Endpoint defenses should also be employed, along with anti-virus and antimalware software.
The risk of spear phishing attacks will increase again in 2017. Doing nothing to improve cybersecurity defenses and combat the spear phishing risk could prove to be a very costly mistake.
by titanadmin | Jan 3, 2017 | Email Scams, Phishing & Email Spam, Spam News |
Last month, L.a. County reported one of the largest phishing attacks in the United States. A single phishing campaign directed at Los Angeles County employees saw an incredible 108 individuals fall for the scam. Each employee that responded to the campaign inadvertently divulged their email credentials to the attacker. 108 email accounts were compromised as a result of the one phishing campaign.
While it is not known whether the individual behind the campaign successfully retrieved any data from L.A County email accounts, the compromised email accounts were a treasure trove of sensitive information. The email accounts contained the sensitive information of more than 750,000 individuals.
While the announcement of the phishing attack was only made in December, the actual incident occurred on May 13, 2016. In contrast to the phishing and spam email campaigns of old that contained numerous spelling mistakes, grammatical errors, and bordered on the unbelievable, this campaign was expertly crafted. The attacker used realistic text and images, hence the reason why such a large number of employees fell for the scam.
Fortunately for L.A. County, the phishing attack was identified promptly – within 24 hours – therefore limiting the damage caused. A detailed forensic investigation revealed that 756,000 individuals had their sensitive information – including Social Security numbers and protected health information- exposed as a result of the attack.
There was further good news. The lengthy investigation confirmed the identity of the attacker, a Nigerian national – Austin Kelvin Onaghinor. A warrant has been issued for his arrest. Bringing that individual to justice may be another matter. Extraditing foreign nationals to the United States can be a difficult and long winded process. However, L.A District Attorney Jackie Lacey has vowed to “aggressively to bring this criminal hacker and others to Los Angeles County, where they will be prosecuted to the fullest extent of the law.”
Phishing attacks on this scale are unfortunately not that rare. Cybercriminals are becoming much better at crafting convincing emails and gaining access to corporate email accounts. All too often, the phishing attacks are not identified quickly, giving criminals plenty of time to exfiltrate data from compromised accounts. Many phishing campaigns are conducted to obtain network credentials and other information that can be used to gain a foothold in corporate networks. Once access is gained, all manner of nefarious activities take place.
This L.A. County phishing scam clearly demonstrates that employees are the weakest link in the security chain, which is why cybercriminals are committing more time and effort into phishing attacks. It is far easier to compromise an email account or gain access to a network if an employee provides their login credentials than attempting to find a chink in advanced cybersecurity defenses.
Protecting against phishing attacks requires an advanced spam filtering solution. Without such a solution in place, organizations have to rely on employees identifying emails as malicious. Something which is becoming much harder to do as cybercriminals perfect their social engineering techniques.
Blocking phishing emails and preventing them from being delivered to inboxes is the single-most effective solution to counter the phishing threat. Along with staff anti-phishing training and anti-phishing exercises, organizations can mount a defense against such attacks and avoid the not inconsiderable mitigation costs. Providing credit monitoring and identity theft protection services to 756,000 individuals is a sizeable cost for any organization to absorb.
by titanadmin | Dec 30, 2016 | Email Scams, Internet Security, Network Security, Phishing & Email Spam |
2016 was a particularly bad year for data breaches. A large number of huge data breaches from years gone by were also discovered in 2016.
The largest breach of 2016 – by some distance – affected Yahoo. The credentials of more than 1 billion users were obtained by the gang behind the attack. A massive cyberattack on MySpace was discovered, with the attackers reportedly obtaining 427 million passwords. 171 million vk.com account details were stolen, including usernames, email addresses, and plaintext passwords. 2016 also saw the discovery of a massive cyberattack on the professional networking platform LinkedIn. The credentials of more than 117 million users were stolen in the attack. Then there was the 51-million iMesh account hack, and 43 million Last.fm accounts were stolen….to name but a few.
The data stolen in these attacks are now being sold on darknet marketplaces to cybercriminals and are being used to commit a multitude of fraud.
One of the biggest threats for businesses comes from business email compromise (BEC) scams. BEC scams involve an attacker impersonating a company executive or vendor and requesting payment of a missed invoice. The attacker sends an email to a member of the accounts team and requests payment of an invoice by wire transfer, usually for several thousand dollars. All too often, even larger transfers are made. Some companies have lost tens of millions of dollars to BEC fraudsters.
Since the email appears to have been sent from a trusted email account, transfer requests are often not questioned. Cybercriminals also spend a considerable amount of time researching their targets. If access to corporate email accounts is gained, the attackers are able to look at previous emails sent by the targets and copy their writing style.
They learn about how transfer requests are usually emailed, the terms used by each company and executive, how emails are addressed, and the amounts of the transfers that have been made. With this information an attacker can craft convincing emails that are unlikely to arouse suspicion.
The scale of the problem was highlighted earlier this year when the FBI released figures as part of a public awareness campaign in June. The FBI reported that $3.1 billion had been lost as a result of BEC scams. Just four months earlier, the losses were $2.3 billion, clearly showing that the threat was becoming more severe.
This year also saw a huge increase in W-2 scams in the United States. W-2 data is requested from HR departments in a similar manner to the BEC scams. Rather than trying to fool email recipients into making fraudulent transfers, the attackers request W-2 data on employees in order to allow them to file fraudulent tax returns in their names. The IRS issued a warning earlier this following a huge increase in W2 attacks on organizations in the United States.
Companies large and small were targeted, with major attacks conducted on Seagate, Snapchat, Central Concrete Supply Co. Inc, and Mainline Health. Between January and March 2016, 55 major – and successful – W-2 scams were reported to the IRS.
Attackers do not even need email account passwords to conduct these attacks. Email addresses of CEOs and executives can easily be spoofed to make them appear that they have been sent internally. The sheer number of stolen email addresses – and in many cases also passwords – makes the threat of BEC and W-2 attacks even greater. Security experts predict next year will be even tougher for businesses with even more cyberattacks than in 2016.
Improve Your Defenses Against Email-Borne Threats in 2017
Reducing the risk of these attacks requires multi-layered defenses. It is essential that all employees authorized to make corporate bank transfers receive training on email security and are alerted to the risk of BEC scams. Policies should be introduced that require bank transfer requests to be authorized by a supervisor and/or authenticated by phone prior to the transfer being made.
All employees should be instructed to use strong passwords and never to share work passwords anywhere else online. Many employees still use the same password for work as for personal accounts. However, if one online platform is breached, it can give the attackers access to all other platforms where the same password has been used – including corporate email accounts.
Organizations should also implement controls to block phishing and spear phishing attacks. Blocking phishing emails reduces reliance on the effectiveness of anti-phishing training for employees.
SpamTitan is a highly effective tool for blocking malicious spam emails, including phishing and spear phishing emails. SpamTitan uses a range of techniques to identify spam and scam emails including Bayesian analyses, greylisting and blacklists. SpamTitan incorporates robust anti-malware and anti-phishing protection, as well as outbound email scanning to block spam and scams from corporate email accounts. SpamTitan is regularly tested by independent experts and is shown to block 99.97% of spam email with a low false positive rate of just 0.03%.
2016 may have been a particularly bad year for data breaches and the outlook doesn’t look good for 2017, but by taking affirmative action and implementing better defenses against email-borne attacks, you could ensure that your company is not added to the 2017 list of data breach and scam statistics.
by titanadmin | Dec 27, 2016 | Phishing & Email Spam, Spam Software |
How do spam filters block spam email? Spammers are constantly adapting their strategies to bypass spam filters and deliver more malicious messages to corporate users’ inboxes, so how do antispam solutions keep pace and block these annoying and often malicious messages?
Many anti-spam services rely on blacklists to identify spammers’ email addresses and IP addresses. Once a spammer’s IP address has been identified, it is added to a global spam blacklist.
Antispam solutions check incoming messages against these blacklists. As soon as an IP address is blacklisted, any email sent from that IP address is automatically marked as spam and will be deleted or quarantined.
Spammers are aware that the lifespan of an email address for spamming is short. As anti-spam solutions have improved, the time delay between an email address being used for spamming and it being added to a global spam blacklist has reduced considerably. Whereas spammers used to be able to use an email address for weeks before it was identified by anti-spam solutions and blacklisted, now the lag has been reduced to days or even hours.
Spammers therefore have a very small window of opportunity to use email addresses and mail servers for spamming before they are detected and blacklisted.
Snowshoe and Hailstorm Spam Tactics to Get Messages to Inboxes
Spammers have attempted to increase the timespan for using email addresses using a number of methods, the most common being conducting snowshoe campaigns. This tactic involves sending out very low numbers of spam email messages from each IP address. If spam email volume is kept low, there is less chance of the IP address being recognized as used for spamming. To ensure sufficient numbers of messages are sent, spammers use millions of IP addresses. Even using this tactic will not allow the spammers to conduct their activities undetected for very long. Spammers therefore need to constantly add new IP addresses to their spamming networks to enable them to continue conducting their campaigns.
Snowshoe tactics are now widely used and the technique is highly effective, although a new tactic has recently been uncovered that is referred to as hailstorm spamming. Hailstorm spam campaigns similarly involve extremely large numbers of IP addresses, yet they are used very briefly and intensely. Rather than trying to stay under the radar, the spammers use those IP addresses to send huge volumes of messages very quickly.
Researchers at Cisco Talos recently analyzed both tactics and determined that the DNS query volume from a typical snowshoe campaign involved around 35 queries an hour. A hailstorm spam campaign involved around 75,000 queries an hour. The snowshoe campaign would continue at that rate for many hours, whereas the hailstorm spam campaign spiked and then fell to next to nothing. Hailstorm campaigns can therefore be used to deliver huge volumes of emails before the IP addresses are added to blacklists.
How do Spam Filters Block Spam Email?
How do spam filters block spam email when these tactics are used? Snowshoe and hailstorm spam campaigns are effective against antispam solutions that rely on blacklists to identify spammers. Only when an IP address is added to a blacklist will the spam email messages be blocked. Advanced spam solutions offer far greater protection. Blacklist are still used, although a number of other methods of spam detection are employed.
Conducting a Bayesian analysis on all incoming spam email messages greatly reduces the volume of spam email messages that are delivered to end users. A Bayesian analysis involves reading the contents of a message and assessing the words, phrases, headers, message paths, and CSS or HTML contained in the message. While scoring, messages based on content can be effective, Bayesian spam filters also learn as they go. They constantly compare spam emails to legitimate emails and build up the range of spam characteristics that are checked. As spammers change tactics, this is picked up by a Bayesian spam filter and spam messages continue to be filtered.
The use of greylisting is also important in a spam filter. There will be some messages that pass all of the checks and some that monumentally fail. Categorizing these messages as genuine or spam is therefore simple. However, there is a sizeable grey area – messages that could potentially be spam.
If all of these messages are blocked, many genuine emails would not be delivered. If they are all allowed, many spam messages would get through. This would result in poor catch rates or extremely high false positive rates. Greylisting helps in this regard. Suspect messages are returned to the sender’s mail server and a request is made for the message to be resent. Since spammers mail servers are typically constantly busy, these requests are either ignored or they are not dealt with promptly. The time it takes for the message to be resent is therefore a good indicator of whether the message is genuine.
SpamTitan – Keep Your Inboxes Spam Free
SpamTitan uses a range of methods to identify spam emails including blacklists, Bayesian analyses, and greylisting. These checks ensure that more spam emails are identified and blocked, even if IP addresses have yet to be added to spam blacklists. This makes SpamTitan highly effective, even when spammers use snowshoe and hailstorm spamming tactics. By using a range of methods to identify spam emails, spam detection rates are improved and false positives are reduced.
SpamTitan is independently tested every month to determine its effectiveness. SpamTItan is consistently verified as capable of blocking more than 99.97% of spam emails, with a false positive rate below 0.03%.
If you want to find out the difference that SpamTitan makes to the volume of spam messages that are delivered to your employees’ inboxes, why not take advantage of our free, no-obligation 30-day trial. You can implement the solution quickly, evaluate its effectiveness, and you will receive full customer and technical support for the duration of the trial.
by titanadmin | Dec 13, 2016 | Phishing & Email Spam, Spam Advice, Spam Software |
All antispam solutions and spam filters check inbound messages for common spam signatures; however, it is also important to choose a solution that performs outbound email scanning. Outbound email scanning ensures spam emails, or emails containing malware, are not sent from an organization’s email accounts or domains.
Your employees would be unlikely to knowingly use their corporate email accounts to send spam emails, but malware infections can allow cybercriminals to gain access to email accounts and use them to send high volumes of spam email messages. Cybercriminals could also compromise email accounts and use an organization’s domain to send malware and ransomware to clients and customers.
Should this happen, it can have a seriously detrimental effect on an organization’s reputation and may result in corporate email accounts or an entire domain being blacklisted.
Blacklists are maintained by a number of organizations – spamhaus.org for example. Internet Service Providers (ISPs), web servers, and antispam solutions check these blacklists before allowing emails to be delivered to end users. If a particular IP address, email account, or domain is listed in one of the blacklist databases, emails sent from the domain, IP address or email account will not be delivered.
Blacklists are updated in real-time and contain many millions of blocked domains and email addresses that have been reported as having been used for unwanted activity such as the sending of spam emails. If emails are sent from a blacklisted account, domain, or IP address those emails will either be directed to a quarantine folder, deleted, or will simply be rejected.
If a business has its domain added to a spam blacklist important emails to clients and customers will not get through. This can prove costly, as real estate firm Keller Williams has recently discovered.
Blacklisted Domains and Email Accounts Can Prove Costly for Businesses
Over the past few days, email messages sent from the kw.com domain used by Keller Williams have been rejected by AOL. Yahoo has been blocking emails from the kw.com account for some time. The problem appears to be the addition of the kw.com domain to spam blacklists.
If a Keller Williams real estate agent needs to send an email to a customer who has an AOL or Yahoo account, it will not be delivered. Agents have therefore been forced to get customers to open Google email accounts in order to send online paperwork or documents requiring e-signatures.
The issue also affects online paperwork sent via the transaction management software program Ziplogix, with one Keller Williams agent also claiming Dotloop is also affected. Some agents at Keller Williams have reportedly had to send important paperwork for listings and sales via personal email accounts to ensure emails are delivered.
The AOL website explains that when domains have been flagged as being abusive, the server will be temporarily blocked until the spamming stops. Until a domain is removed from its blacklist, AOL account holders will be prevented from receiving emails from the blocked domain. Removing the domain from the blacklist can take up to a week.
Removing a domain from the 80+ commonly used spam blacklists can be a time-consuming task; furthermore, if spam emails are sent from the account again, the domain will simply be added to the blacklists once more.
Outbound Email Scanning Prevents the Blacklisting of an Organization’s Domain
Unlike many third-party antispam solutions, SpamTitan checks incoming email messages for spam signatures as well as performing outbound email scanning. If an email account has been compromised and is being used to send spam emails, if malware is sending spam, those messages will be blocked and will not be sent. Outbound email scanning is an important protection that will prevent an organization’s domain or email accounts from being used to send spam or malware.
Organizations can therefore avoid the embarrassment and reputation damage that results from being suspected as engaging in spamming or malware delivery. They can also rest assured that in addition to blocking 99.97% of inbound email spam, their domains and email accounts will not be added to spam blacklists.
by titanadmin | Dec 2, 2016 | Phishing & Email Spam, Spam News, Website Filtering |
‘Tis the season to be jolly, although ‘tis also the season to be infected with malware. The holiday season is an annual highlight for cybercriminals. Holiday season malware infections are to be expected as cybercriminals increase their efforts and try to infect as many users with malware as possible.
Malware is an ever-present threat, but the increase in online activity in the run up to the holiday season means easy pickings for cybercriminals. Consumers are starting to prepare for the holidays earlier, but not as early as the scammers. As consumers head online in their droves, scammers and other cybercriminals are lying in wait.
The advent of Black Friday and Cyber Monday – days where shoppers are offered amazing deals to prompt early Christmas purchases– see a frenzy of online activity. There are discounts aplenty and great deals to be had.
However, not all of those discounts are genuine. Many are scams that are used to phish for sensitive information or spread malware infections. As is the case every year, the holiday season sees a spike in malware infections, with the biggest spike over Thanksgiving weekend. This year has been no exception. Holiday season malware infections have increased significantly year on year.
Holiday Season Malware Infections Rise 118% Above Normal Levels
This year, over the first official shopping weekend of the holiday season, malware infections increased by 106% according to data compiled by the Enigma Software Group. On Cyber Monday, when even more great deals on online purchases are made available, malware infections were 118% higher than normal.
Those figures are only for Windows users. Add in smartphones and Apple devices and the figures would be higher still. The problem is also getting worse. Last year there was a spike of 84% over normal levels during the Thanksgiving weekend.
There have been a number of suggestions put forward as to why the figures are so high this year. One of the main reasons is simply due to the number of shoppers heading online. Each year sees more individuals choosing to go online shopping over Thanksgiving weekend. More online shoppers mean more opportunities to infect users with malware.
However, there are also more actors involved in online scams, malware-as-a-service and ransomware-as-a-service has also grown in popularity, and many cybercriminals have started up affiliate schemes to get more help spreading their malicious software. Individuals who succeed in infecting computers with ransomware are given a cut of the profits and there is no shortage of people willing to try the affiliate schemes to boost their own earnings.
Cybercriminals are also getting better at developing convincing scams and malicious email messages. The grammatical and spelling mistakes that were common in phishing emails in years gone by are largely gone. Now, almost perfect emails are sent and scammers are using a wide range of social engineering techniques to lure end users into clicking on malicious links or opening infected email attachments. Spoofed retail sites are also now commonplace – and extremely convincing.
The growth of social media has also helped boost cybercriminal activity. Malicious posts are being shared online offering discounts, special offers, and unmissable deals. However, all end users get is a malware download.
Avoiding a Bad Start to Holiday Season
To avoid becoming a victim of a scam or having to deal with a malware or ransomware infection, shoppers must be vigilant and exercise more caution. Offers that sound too good to be true usually are. Unsolicited emails should always be treated as suspicious and extra care should be taken when clicking on any link or visiting a retail site.
Businesses should also take extra precautions. A malware or ransomware infection can prove extremely costly to resolve. While warnings should be sent to end users about the risks of holiday season malware infections, technological solutions should also be in place to prevent malicious file downloads.
Antispam solutions are highly effective at blocking malicious messages such as phishing emails and emails containing malware. SpamTitan blocks 99.97% of spam messages, contains a powerful anti-phishing module, and blocks 100% of known malware.
Malicious links on social media sites and on third-party ad networks (malvertisting) are a very real risk. However, a web filter can be used to control access to social media sites, block malicious third-party adverts, and prevent end users from visiting websites known to contain malware.
If you want to keep your network free from malware this holiday season, if you have not already used these two solutions, now is the time. They will also help to keep your network malware free around the year. And with security experts predicting a massive increase in ransomware and malware attacks in 2017, there is no better time to start improving your defenses.

by titanadmin | Nov 30, 2016 | Phishing & Email Spam, Spam Advice, Website Filtering |
The Federal Trade Commission (FTC) in the United States has responded to the current ransomware epidemic by issuing ransomware advice for businesses and consumers. The FTC ransomware advice for businesses comes following a spate of high profile ransomware attacks on U.S businesses. The threat has prompted many U.S. government agencies to release ransomware advice for businesses in the past few months.
Ransomware is a form of malware that encrypts files on a victim’s computer and prevents them from being accessed. After a computer is infected, the attackers issue a ransom demand. In order to obtain the key to unlock the encryption the victim is required to pay a ransom. The ransom amount can be set by the attackers, although it is often around $500 per infected computer.
Ransomware has proved incredibly popular with cybercriminals as it offers a quick source of revenue. Since payment is made in an anonymous cryptocurrency such as Bitcoin, money can be collected without fear of being caught.
The scale of the problem has been shown by numerous reports by security firms. This month, SentinelOne released the results of a global survey that showed 48% of organizations had experienced at least one ransomware attack in the past 12 months. The companies that had been attacked had been forced to deal with an average of 6 ransomware incidents in the past year.
A report released by Beazley’s Breach Response Unit suggests ransomware attacks between January and September were four times higher than in 2015, while a report from Kaspersky Lab suggests there has been an eightfold increase in attacks in the past year.
Ransomware is installed via a number of different attack vectors. Ransomware gangs use exploit kits on websites that probe for vulnerabilities in browsers. Those vulnerabilities are leveraged to download ransomware. Malvertising is also used. This is the use of third party ad networks to spread malware. Adverts are created containing malicious code which directs users to websites that silently download ransomware. Ransomware downloaders were also allegedly sent out via Facebook Messenger this week.
However, the biggest attack vector is email. Spam emails are sent containing attachments that have been infected with malicious macros, JavaScript files, and other ransomware downloaders. Links to malicious websites are also distributed via email. The attackers use a range of social engineering techniques to convince email recipients to click on malicious links or open infected attachments. Doing so results in ransomware being installed.
While not all ransomware attacks result in files being encrypted, attacks carry a significant cost. SentinelOne suggests that in the United States, organizations spend an average of 38 man-hours restoring files from backups after a ransomware attack. Additional investment in security is also required after an attack.
Since ransomware can spread laterally across a network, a single infection can result in many computers being infected. Ransom demands of the order of tens of thousands of dollars are not uncommon. The recent ransomware attack on the San Francisco ‘Muni’ rail system saw a ransom demand of $73,000 issued.
Ransomware Advice for Businesses
Unfortunately, antivirus software can be ineffective at preventing ransomware attacks. Businesses looking to defend against ransomware must therefore use a range of techniques. These include:
- Ensuring all software is kept up to date and patches applied promptly
- Setting antivirus and antimalware programs to update definitions automatically
- Use endpoint security controls to prevent ransomware installations
- Implement a robust spam filter to prevent malicious emails from being delivered to end users
- Use a web filtering solution to prevent employees from visiting malicious websites and to monitor users’ online activities to identify high risk activities
- Use intrusion prevention software
- Train the workforce on security best practices and test knowledge to ensure training has been effective
- Ensure all members of staff are aware who to contact and what to do if they believe they have inadvertently installed malicious software
To avoid paying a ransom, it is essential to ensure that regular backups of data are performed. Multiple backups should be made to minimize the risk of data loss. Those backups should be stored on an air-gapped device to avoid backup files also being encrypted. A ransomware response plan should also be developed to reduce disruption to the business in the event of an attack.
by titanadmin | Nov 25, 2016 | Email Scams, Phishing & Email Spam |
The email marketing service MailChimp employs security controls to ensure that its customers do not use the service to send spam; yet, this week malicious spam emails were sent from multiple accounts after a MailChimp account hack.
Customer accounts that were breached included Business News Australia, Brisbane’s The Sit Down Comedy Club, and gardening and home services provider Jim’ Group.
MailChimp accounts are valuable to spammers as subscribers to company newsletters are more likely to trust the emails than they would an email from an unknown sender. The hijacked accounts were used to send spam emails demanding an invoice be paid. Spammers often target businesses with malicious emails that spread malware. If malware such as a keylogger can be installed, the attackers can gain access to corporate email accounts or gain network access. Corporate bank account details can be stolen and fraudulent transfers made.
A fake invoice is a common ploy used to fool email recipients into opening an infected email attachment or clicking on a malicious link. A sense of urgency is often included to scare the recipient into opening the attachment. A threat of legal action if the outstanding invoice is not paid promptly is a common tactic.
In this case, a number of different variants were sent. Some emails contained an image with an embedded hyperlink which recipients could click to view the invoice. The spammers also included the logo of accounting software Quickbooks for extra authenticity.
Other emails included an attached zip file which contained a malicious JavaScript file. If run, the JavaScript downloaded malware onto the email recipient’s computer.
Initially, it appeared that MailChimp had experienced a security breach that resulted in spammers gaining access to accounts; although the company issued a statement saying that an investigation of the incident did not point to an internal breach.
MailChimp told Motherboard “MailChimp’s normal compliance processes identified and disabled a small number of individual accounts sending fake invoices. We have investigated the situation and have found no evidence that MailChimp has been breached. The affected accounts have been disabled, and fraudulent activity has stopped.”
How the MailChimp account hack was pulled off remains a mystery. The spammers may have managed to guess the passwords that were used to secure accounts or they could have obtained those passwords by other means. The practice of reusing passwords on multiple platforms could be to blame. If a breach of one platform occurs, cybercriminals can gain access to all other online services that use the same password.
In a recent post, computer security blogger Graham Cluley suggested some passwords were obtained by the password stealing Trojan Vawtrak. Cluley was contacted by an anonymous source who claimed to be in possession of two thousand MailChimp login credentials which were recorded by Vawtrak.
Details of the MailChimp account hack are unlikely to be released, although the incident shows how important it is for businesses to use two-factor authentication to secure their online accounts. The incident also shows how important it is to exercise caution and to treat any email attachment of hyperlink as potentially malicious, even if the sender of the email is known.
by titanadmin | Nov 25, 2016 | Email Scams, Phishing & Email Spam |
The biggest hacking threat to businesses comes not from unpatched software, but phishing. An incredibly simple, yet highly effective way that cybercriminals gain access to networks. Phishing can be used to bypass even the most sophisticated of cybersecurity defenses. Why go to the trouble of trying to find a weakness in highly sophisticated cybersecurity defenses when a simple email can get an employee to give the attacker their login credentials?
As Jeh Johnson, Secretary for the U.S. Department of Homeland Security, recently explained to attendees at the Financial Crimes and Cybersecurity Symposium in New York, phishing is one of the department’s biggest fears.
“The most devastating attacks by the most sophisticated attackers almost always begin with the simple act of spear-phishing,” says Johnson. It is no surprise that phishing is the biggest hacking threat to businesses. Phishing is alarmingly effective.
Even multi-million dollar cybersecurity defenses can be bypassed with a simple phishing email. The social engineering techniques used by cybercriminals often get the desired response.
Most of the largest hacks in the United States were possible not due to a security weakness, but because an employee responded to a phishing email. The cyberattacks on Ebay, Target, the Office of Personnel Management, JP Morgan, Anthem, and Sony Pictures all started with a simple phishing email.
Cybercriminals have also started using phishing emails to distribute ransomware. Malicious links are sent to company employees along with a request to click for free items, to take part in prize draws, or even to secure their computers to prevent cyberattacks.
Phishing has been around for as long as email and cybercriminals will not stop using phishing to gain access to networks, install malware, lock files with ransomware, and steal data. Phishing is likely to remain the biggest hacking threat to businesses. Organizations – and their employees – just need to get better at identifying and blocking phishing attempts.
One of the best defenses against phishing is to ensure that all staff members from the CEO down receive security awareness and anti-phishing training.
Training alone is insufficient. Staff can be told how to identify phishing attempts, but their ability to spot a phishing email must be put to the test. Anti-phishing skills need to be regularly tested. Dummy phishing emails should be sent to check to see who responds. Johnson says his department often sends fake phishing emails – free Redskins tickets for example – to test anti-phishing prowess. Anyone who responds is provided with further training.
Training is important in case a phishing email reaches an employee’s inbox, although it is far better to ensure phishing emails are not delivered. The best technological defense against phishing is the use of an anti-spam service. If phishing emails are not delivered to inboxes, staff members will not be able to respond and their anti-phishing skills will not be put to the test.
SpamTitan is a highly effective spam filtering solution for businesses that blocks 99.97% of spam email. Each month SpamTitan is independently tested for effectiveness. SpamTitan has now won 36 consecutive VB Bulletin antispam awards.
SpamTitan is a highly scalable anti-spam solution that’s suitable for businesses of all sizes. SpamTitan can be installed as a software solution, as a virtual appliance, or as a 100% cloud-based solution, the latter being ideal for managed service providers (MSPs).
Each solution is quick and easy to install, requires a low management overhead, and incorporates a host of features to block malware and prevent the delivery of phishing emails.
We are so confident that you will be impressed with SpamTitan that we offer the full product on a 100% free, 30-day trial. For further information contact TitanHQ today and take the first step toward banishing spam.
by titanadmin | Nov 18, 2016 | Email Scams, Network Security, Phishing & Email Spam, Spam News |
Malicious email spam volume has increased again. According to the latest figures from Kaspersky Lab, malicious email spam volume in Q3, 2016 reached a two-year high.
In Q3 alone, Kaspersky Lab’s antivirus products identified 73,066,751 malicious email attachments which represents a 37% increase from the previous quarter. Malicious spam email volume has not been at the level seen in Q3 since the start of 2014. Kaspersky Lab’s figures show that six out of ten emails (59.19%) are spam; a rise of around 2% from Q2, 2016. September was the worst month of the year to date, with 61.25% of emails classified as unsolicited spam.
Spam includes a wide range of unsolicited emails including advertising and marketing by genuine companies, although cybercriminals extensively use email to distribute malware such as banking Trojans, keyloggers, and ransomware. The use of the latter has increased considerably throughout the year. In Q3, the majority of malicious emails contained either ransomware or downloaders that are used to install ransomware on personal computers and business networks.
Ransomware is a form of malware that locks files on a computer with powerful encryption, preventing the victim from gaining access to their data. Many ransomware variants are capable of spreading laterally and can encrypt files on other networked computers. All it takes is for one individual in a company to open an infected email attachment or click on a malicious link in an email for ransomware to be downloaded.
Spammers often use major news stories to trick people into opening the messages. The release of the iPhone 7 in Q3 saw spammers take advantage. Spam campaigns attempted to convince people that they had won an iPhone 7. Others offered the latest iPhone at rock bottom prices or offered an iPhone 7 for free in exchange for agreeing to test the device. Regardless of the scam, the purpose of the emails is the same. To infect computers with malware.
There was an increase in malicious email spam volume from India in Q3. India is now the largest source of spam, accounting for 14.02% of spam email volume. Vietnam was second with 11.01%, with the United States in third place, accounting for 8.88% of spam emails sent in the quarter.
Phishing emails also increased considerably in Q3, 2016. Kaspersky Lab identified 37,515,531 phishing emails in the quarter; a 15% increase compared to the Q2.
Business email compromise (BEC) attacks and CEO fraud are on the rise. These scams involve impersonating a CEO or executive and convincing workers in the accounts department to make fraudulent bank transfers or email sensitive data such as employee tax information. Some employees have been fooled into revealing login credentials for corporate bank accounts. Cybercriminals use a range of social engineering techniques to fool end users into opening emails and revealing sensitive information to attackers.
Security awareness training is important to ensure all individuals – from the CEO down – are aware of email-borne threats; although all it takes is for one individual to be fooled by a malicious email for a network to be infected or a fraudulent bank transfer to be made.
The rise in malicious email spam volume in Q3, 2016 shows just how important it is to install an effective spam filter such as SpamTitan.
SpamTitan has been independently tested by VB Bulletin and shown to block 99.97% of spam emails. SpamTitan has also been verified as having a low false positive rate of just 0.03%. Dual antivirus engines (Bitdefender and ClamAV) make SpamTitan highly effective at identifying malicious emails and preventing them from being delivered to end users.
If your end users are still receiving spam emails you should consider switching antispam providers. To find out the difference that SpamTitan can make, contact the Sales Team today and register for a free, no obligation 30-day trial.
by titanadmin | Oct 31, 2016 | Email Scams, Phishing & Email Spam, Spam News |
Thanksgiving weekend sees Americans head on line in the tens of millions to start online Christmas shopping in earnest and this year the holiday season scams have already started.
Black Friday and Cyber Monday are the busiest online shopping days, but some retailers are kickstarting their promotions early this year and have already started offering Black Friday deals. Amazon.com for example launches its first Black Friday offers tomorrow, well ahead of the big day on 25th November.
It is no surprise that retailers are trying to get ahead. 41% of shoppers start their holiday shopping in October according to a recent National Retail Federation survey. 41% of shoppers wait until November. 82% of shoppers like to make an early start, and this year so are the scammers.
A popular tactic used by cybercriminals is typosquatting – the registration of fake domains that closely match the brand names of well-known websites. Phishers use this tactic to obtain login credentials and credit card numbers. In recent weeks, there has been an increase in typosquatting activity targeting banks and retailers.
A fake domain is registered that closely matches that of the targeted website. For instance, the Amaz0n.com domain could be purchased, with the ‘o’ replaced with a zero. Alternatively, two letters could be transposed to catch out careless typists. A website is then created on that domain that closely matches the targeted website. Branding is copied and the layout of the genuine site is replicated.
There is another way that scammers can take advantage of careless typists. Each country has its own unique top level domain. Websites in the United States have .com. Whereas, websites registered in the Middle Eastern country of Oman have the .om domain. Scammers have been buying up the .om domains and using them to catch out careless typists. In the rush to get a holiday season bargain, many users may not notice they have typed zappos.om instead of zappos.com.
Visitors to these scam websites enter their login credentials as normal, yet all they are doing is giving them to the attackers. The scammers don’t even need to spoof an entire website. When the login fails, the site can simply redirect the user to the genuine site. Users then login as normal and complete their purchases. However, the scammers will have their login credentials and will be able to do the same.
However, many websites now have additional security features to prevent the use of stolen login credentials. If a login attempt is made from an unrecognized IP address, this may trigger additional security features. The user may have to answer a security question for example.
Some scammers have got around this problem. When a user attempts to login on a scam site, a login session is automatically opened on the genuine website. The information entered on the scam site is then used by the attackers on the genuine site. When the unusual IP address triggers an additional security element, this is then mirrored on the scam site with the same question forwarded to the user. The question is answered, and an error message is generated saying the login was unsuccessful. The user is then redirected to the genuine site and repeats the process and gains access. Chances are they will be unaware their account details have been compromised. Hours later, the scammers will login to the genuine site using the same credentials.
Businesses must also exercise caution at this time of year and should take steps to reduce the risk of employees falling for holiday season scams. Employees keen to get the latest bargains will undoubtedly complete some of their purchases at work.
Email scams increase at this time of year and business email accounts can be flooded with scam emails. Offers of discounts and special deals are likely to flood inboxes again this year. Email holiday season scams may not be about stealing login credentials. Given the increase in malware and ransomware infections in 2016, this holiday season is likely to see many holiday season scams infect businesses this year. A careless employee looking for an online bargain could all too easily click a link that results in a malware download or ransomware infection.
As holiday season fast approaches, the scammers will be out in force. It is therefore important for both businesses and consumers to take extra care. If you want to find out how you can protect your business from malware and ransomware, contact the TitanHQ team today and find out more about our security solutions.
by titanadmin | Oct 28, 2016 | Phishing & Email Spam, Spam News, Spam Software |
Spam email volume has reduced over the past couple of years following the takedown of key botnets – and individuals – behind some of the biggest spamming campaigns. It was starting to look like the super-spamming days of the early 2010s were a thing of the past. However, spam email volume has been increasing in recent months.
Necurs botnet activity has increased and last month the Tofsee botnet came back to life after years of dormancy. Both of these botnets had previously been used to send annoying but relatively harmless spam emails offering cheap pharmaceuticals and offers of beautiful Russian brides. However, the increase in activity is also coupled with the move to malicious email attachments containing malware and ransomware.
These and other botnets such as Helihos are also growing in size at alarming rates and spam email volume is soaring. Some reports suggest spam email volume has increased from around 200,000 spam emails per second to 450,000 emails per second over the past couple of months.
But what are these malicious email attachments, and how big is the risk?
97% of Malicious Spam Email Attachments Contain Locky Ransomware
Locky ransomware first appeared in February 2016. It has since become one of the biggest email threats. The ransomware is being sent in massive spam campaigns and increasingly sophisticated social engineering techniques are used to infect end users.
To put these email campaigns into some perspective, historically, the volume of spam email used to deliver malware, ransomware, and other email nasties stood at around 2% of the total spam email volume. By around April this year, two months after Locky first appeared on the scene, malicious spam emails containing the ransomware accounted for around 18% of total spam email volume.
The Quarterly Threat Report issued by ProofPoint earlier this month suggests the volume of spam email containing malicious attachments or links reached record levels in quarter 3, 2016. The vast majority of those emails contained Locky. According to the report, 97% of captured spam emails with malicious attachments were used to deliver Locky. That’s a 28% increase from Q2, and a 64% increase since Q1.
Since its release, Locky ransomware has been infecting users via Word documents containing malicious macros, JavaScript files, executable HTML files (HTA), and more recently Windows Script Files (WSF) hiding the Nemucod downloader. Now, another change has been detected. Earlier this month, researchers at the Microsoft Malware Protection Center discovered the actors behind Locky ransomware had made another change to the way they infect computers and made the switch to shortcut files (LNK) containing PowerShell commands.
This discovery coincided with a drop in detection and a relatively quiet period for the past two weeks. However, Locky is back with a vengeance. On Monday this week, three new campaigns were detected, one of which was massive and involved 14 million messages in around half a day. 6 million of those messages were sent in a single hour!
The risk from Locky is considerable. Locky is capable of deleting Windows Shadow Files and encrypting a wide range of data, including data on portable storage devices and network drives. Resolving an attack can prove extremely costly. It is therefore essential to improve defenses to prevent attacks.
Ransomware and Malware Protection
Larger botnets and the move to malicious messages means organizations need to be prepared and take steps to ensure that these messages are effectively blocked.
Protecting your organization from email attacks is critical. It is therefore essential to employ a robust enterprise spam filtering solution. SpamTitan blocks 99.7% of spam email, preventing malicious email attachments and links from being delivered to your end users. This reduces reliance on training programs to educate end users on email threats.
Preventing ransomware infections requires a multi-layered approach. There is no silver bullet that will offer total protection against ransomware infections, but there are security products that can greatly reduce risk.
Protecting against exploit kits and malvertising requires a web filtering solution. By blocking websites known to contain malware or exploit kits, and carefully controlling the website content that can be accessed by employees, organizations can effectively protect against web-borne infections. WebTitan offers that protection and can be used to block malicious websites and reduce the risk from infections via malvertising.
Along with intrusion detection systems, firewalls, antivirus and anti-malware solutions, it is possible to defend against ransomware and malware attacks and keep your data secured.
by titanadmin | Sep 23, 2016 | Email Scams, Internet Security |
In July, news started to break about a massive Yahoo Inc data breach. It has taken some time, but the Yahoo Inc data breach has now been confirmed. And it was huge.
The Yahoo Inc data breach beats the massive cyberattack on Heartland Payment Systems in 2009 (130 million records), the LinkedIn cyberattack discovered this summer (117 million records), and the 2011 Sony data breach (100 million records). In fact, the Yahoo Inc data breach is the largest ever reported. More records were stolen in the cyberattack than those three breaches combined. More than 500 million accounts were compromised, according to Yahoo.
Yahoo Inc Data Breach Worse than Initially Thought
The Yahoo Inc data breach came to light when a hacker added a listing to the Darknet marketplace, theRealDeal. The credentials of 280 million account holders were offered for sale by a hacker called ‘Peace’. To anyone who follows Internet security news, the name of the hacker selling the data should be familiar. Peace recently listed the data from the LinkedIn hack for sale.
The 280 million Yahoo records were listed for a paltry $1,800. That payment would buy a cybercriminal names, usernames, easily crackable passwords, backup email addresses, and dates of birth. While the data were listed for sale 2 months ago, Yahoo has only just announced the breach.
After being alerted to the listing, Yahoo initiated an internal investigation. The investigation allegedly did not uncover any evidence to suggest that the claims made by “Peace” were genuine. However, the internal investigation did reveal that someone else had hacked Yahoo’s systems. Yahoo claims the hack was performed by a state-sponsored hacker.
Yahoo issued a statement saying “The investigation has found no evidence that the state-sponsored actor is currently in Yahoo’s network.” While that is undoubtedly good news, the bad news is that access is no longer required because user’s data have already been stolen.
The stolen data include names, email addresses, dates of birth, telephone numbers, security questions and answers, and hashed passwords. According to Yahoo, users’ bank account information and payment card details do not appear to have been stolen. Those credentials were stored in a separate system.
What is most concerning about the Yahoo Inc data breach is not the fact that its systems were compromised, but how it has taken so long for Yahoo to discover the cyberattack. The breach did not occur over the summer. The hack took place in 2014.
The results of the Yahoo Inc data breach investigation will have come as a nasty shock to Verizon. The company agreed to buy Yahoo’s core web business, including Yahoo email, in the summer for $4.8bn. It is possible that Verizon may now be having second thoughts about that deal. Whether the hack will have an impact on the purchase remains to be seen, but for Yahoo the timing could not be much worse.
Yahoo Account Holders Advised to Change Passwords and Security Q&As
Yahoo account holders are unlikely to be concerned about any potential sale of their email accounts to Verizon. They will however be concerned about the sale of their credentials to cybercriminal gangs. Even if the data that were listed for sale by Peace are not genuine, someone somewhere does have their data. Most likely, their data are in the hands of multiple criminals. Those data can – and will – be used in a variety of malicious ways.
Yahoo has now placed a notice on its website alerting users to the breach of their data. Yahoo has also sent out emails to affected users urging them to login to their accounts and change their passwords and security questions. The old security questions and answers have now been invalidated and Yahoo has told users to check their accounts for any suspicious activity, albeit out of “an abundance of caution”.
Fortunately for account holders, the majority of passwords were encrypted with bcrypt – a relatively secure form of encryption. However, that does not mean that the passwords cannot be cracked nor that email account holders are not at risk as a result of the Yahoo Inc data breach.
Yahoo Users at Risk of Phishing Attacks
Cybercriminals may not be able to crack the passwords and gain access to user accounts, but they have all the data they need to conduct phishing campaigns.
Yahoo has already emailed users alerting them to the breach, but the emails contained links that can be used to change passwords and security questions. Any cybercriminal in possession of the stolen data is likely to copy the official emails sent by Yahoo. However, instead of links to Yahoo’s website, the emails will contain links to phishing sites.
Those sites are likely to look exactly the same as the official Yahoo site. However, any user entering a new password or security question, would simply be disclosing that information to the attacker. Emails are also likely to be sent that direct users to websites containing exploit kits. Clicking the links will result in malware and ransomware downloads.
If the criminals behind the attack – or those in possession of the data – do manage to crack the passwords, it is not only Yahoo email accounts that could be compromised. Any individual who has used the same password on other websites faces a high risk of other accounts being compromised. Bank accounts, social media accounts, other email accounts, E-bay and Amazon.com accounts could all be at risk.
The data could also be used for social engineering scams, via email or telephone. Criminals will be looking to obtain the extra data they need to commit identity theft and other types of fraud.
How to Minimize Risk and Protect Yourself
- Never click on any links contained in emails. Even if an email looks official and contains a link to help.yahoo.com or login.yahoo.com, do not click on the links. Instead, login to your account in the usual way by entering the web address directly into your browser and change your password and security questions.
- Use a strong password containing letters (capitals, and lower case), numbers, and special characters.
- If you have used the same password for multiple websites, change those passwords immediately. Each website requires a different password. Use a password manager – either a free or paid service – to remember all your passwords.
- Use Yahoo Account Key, which will eliminate the need for a password altogether
- Never respond to any email request for personal information
- Never open any attachments sent via email unless you are certain of their genuineness
by titanadmin | Sep 13, 2016 | Network Security, Phishing & Email Spam |
In response to the massive rise in ransomware attacks on healthcare organizations, the Department of Health and Human Services’ Office for Civil Rights has developed new HIPAA guidance on ransomware for covered entities.
The guidance covers best practices that can be adopted to prevent cybercriminals from installing ransomware, along with helpful advice on how to prepare for ransomware attacks and how to respond when critical files are encrypted by malicious software. Importantly, the new HHS guidance on ransomware also confirms how these security breaches are classified under the Health Insurance Portability and Accountability Act. Many healthcare security professionals feel that HIPAA guidance on ransomware has been long overdue due to the uncertainty about maintaining HIPAA compliance following a ransomware attack. .
HIPAA Guidance on Ransomware Clarifies Attacks ARE Reportable Data Breaches
In the new HIPAA guidance on ransomware, OCR has clarified the reporting requirements for ransomware attacks under HIPAA. Over the past few months, as ransomware attacks on healthcare organizations have soared, there has been much confusion over whether these attacks are classed as security incidents under HIPAA Rules.
It has been argued that since ransomware blindly encrypts files and does not usually involve the attackers actually gaining access to data, the incidents should not be reportable to the HHS. Also, it has been argued that there is no need to issue breach notification letters to patients whose data are temporarily encrypted.
The OCR has now confirmed that ransomware attacks are reportable and require a full breach response, including the mailing of breach notification letters to affected patients and health plan members.
A ransomware attack is considered to be a data breach unless the covered entity can demonstrate that there was only a “low probability that PHI has been compromised.” The OCR considers a breach to have occurred if “unauthorized individuals have taken possession or control of the information.”
How HIPAA Covered Entities Must Respond to Ransomware Attacks
Any HIPAA covered entity that experiences a ransomware attack must orchestrate a full breach response and proceed as they would for a malware attack or if a hacker gained access to PHI.
An accurate and thorough risk assessment must be conducted to determine whether there is any risk to the confidentiality, integrity, or availability of electronic protected health information (ePHI). HIPAA requires the infection to be contained and data must be restored to allow normal operations to continue. Security measures must be implemented to mitigate risks and prevent future attacks.
The Office for Civil Rights must be notified of the breach within 60 days of the discovery of the attack if the breach impacts 500 or more patients, or at the end of the year in the case of a smaller breach of patient records. Breach notification letters must also be mailed to patients within 60 days, in accordance with the HIPAA Breach Notification Rule. A breach notice must also be submitted to the media if the breach impacts 500 or more individuals.
Preparing for a Ransomware Attack
The new HIPAA guidance on ransomware explains that organizations must be prepared to deal with ransomware attacks.
Healthcare organizations should implement cybersecurity protection measures to prevent ransomware attacks, such as installing a robust spam filtering solution such as SpamTitan. Spam filters can prevent the majority of malicious emails from being delivered to end users. Staff members should also be trained on the risk of ransomware and advised how to identify phishing emails and malicious websites.
A risk analysis should be conducted to identify potential cybersecurity vulnerabilities that could be exploited by hackers to install ransomware. Any vulnerabilities that could increase the risk of a ransomware attack being successful should be addressed in a timely fashion.
An emergency operation plan must also be developed that can be immediately put in place upon discovery of a ransomware attack. The new HIPAA guidance on ransomware also states that emergency response plans should be regularly tested to ensure that they are effective.
Ransomware Attacks on Healthcare Organizations Soar
This year has seen an extraordinary number of ransomware attacks on healthcare organizations. In February, ransomware was installed on computers at Hollywood Presbyterian Medical Center in California and a ransom demand of $17,000 was issued. Hollywood Presbyterian Medical Center felt the best course of action to minimize damage was to pay the ransom and obtain the decryption keys to unlock data. On receipt of the funds, the attackers made good on their promise and supplied the keys to unlock the encryption.
However, some organizations have discovered that simply paying a ransom demand does not spell the end of the problem. There have been cases – notably Kansas Heart Hospital – where a ransom has been paid, only for a second ransom demand to be issued. Other companies have paid and not been supplied with working keys. Paying a ransom is no guarantee that data can be decrypted.
The FBI advises against paying ransom demands. Not only is there no guarantee that the attackers will supply working keys, but payment of ransoms only encourages the attackers to continue with their ransomware campaigns. Only by preparing for ransomware attacks can organizations ensure that in the event of ransomware being installed, they will be able to recover their files quickly without giving in to attackers’ demands.
The Ransomware Threat Should Not Be Ignored
The threat to healthcare organizations is severe. Research conducted by anti-phishing company PhishMe showed that in Q1, 2016, 93% of phishing emails contained ransomware. Figures from Symantec Security Response show that on average, 4,000 ransomware attacks have occurred every day since January 1, 2016. A report from security firm Solutionary, shows that in 2016, 88% of ransomware detections were by healthcare organizations.
So far this year, in addition to the attack on Hollywood Presbyterian Medical Center, ransomware attacks have been reported by MedStar Health and DeKalb Health, while Prime Healthcare reported that three of its hospitals – Desert Valley Hospital, Chino Valley Medical Center and Alvarado Hospital Medical Center – were attacked with ransomware. Methodist Hospital in Kentucky, Massachusetts General Hospital, and Yuba Sutter Medical Clinic in California have also reported ransomware attacks this year, to name but a few.
It may not be possible to prevent ransomware attacks, but if healthcare organizations invest in better security protections, the majority of attacks can be prevented. Provided that adequate preparations are made for ransomware attacks, in the event that the malicious software is installed, damage can be limited.
The HIPAA guidance on ransomware can be downloaded from the HHS website.
by titanadmin | Sep 8, 2016 | Spam Advice |
Knowing how to avoid email server blacklisting is vitally important for any organization that relies on email as a channel of communication. The consequences of your email server being blacklisted can be costly, inconvenient, and potentially damaging to your organization´s credibility.
To best understand what email server blacklisting might mean to your organization, it is ideal to have a little knowledge about how email server filters work. Consequently we have divided this post into three sections explaining a little about email server filters, what may cause your email server to be blacklisted, and how to avoid email server blacklisting.
A Little about Email Server Filters
Email server filters do not actually filter your incoming emails at server level. They protect your organization from spam emails and other email-borne threats from the cloud or as a virtual appliance installed between your firewall and your email server. The distinction between the two types of filter is that virtual appliances can be more appropriate for some larger organizations.
Regardless of how they are deployed, email filters effectively work in the same way – using fast front-end tests to detect and reject the majority of spam emails before a deeper analysis is conducted of the email that remains. One of these front-end tests is a comparison of each email against a list of known sources of spam. This list is known as the Realtime Block List or RBL.
If your organization´s IP address appears on this list, all of your emails will be rejected by most email filters until the IP address is removed from the list – something that can take anything from 24 hours to six months to resolve completely. During this time you will have to ask your customers and other contacts to add your email address to a safe list or “whitelist”.
Why Was My Email Server Blacklisted?
There are several reasons why an email address (or IP address) can be blacklisted, and it is important to find out the exact reason(s) before trying to get your organization´s IP address removed from the Realtime Block List. If you fail to identify the cause, and fail to take steps to avoid email server blacklisting in the future, it can be much tougher to get un-blacklisted second time around.
Blacklisting typically occurs for one of several reasons:
- Your system has been infected with a spambot that has created multiple email accounts within your organization´s domain and is using those accounts to send out spam email.
- Someone in your organization may have revealed their login credentials and a spammer is using that information to send spam emails from the end-user´s email account.
- Emails sent innocently from one or more end-user accounts have had a high proportion of spam-related keywords, or have had infected files attached to them.
The last scenario is entirely possible if an end-user has prepared a presentation or spreadsheet on an infected home computer and bought the infected file into the workplace on a flash drive. Most email filters have antivirus software for identifying malware in attachments. If the infected attachment is sent to multiple recipients – and identified by multiple email filters – your organization´s IP address will quickly be blacklisted.
How to Avoid Email Server Blacklisting
Ideally, organizations should be able to avoid email server blacklisting by having robust antivirus protection and educating their end-users about online security. There should also be an email usage policy in place that would avoid email server blacklisting due to inappropriate content or unsafe attachments – even when these events occur inadvertently.
Unfortunately end-users are the weakest link in the security chain, and it only takes one end-user to click on a malicious URL or reveal their login credentials for an organization´s IP address to be blacklisted. In fact, if blacklisting is the worse consequence of a security breach, your organization has got off lightly and should consider itself lucky that the consequences were not far more serious.
Consequently, the best way how to avoid email server blacklisting is with an email filter that has malicious URL blocking to prevent end-users visiting malware-infested websites, with phishing protection to reject emails directing an end-user to fake website, and outbound scanning to identify potential spam and infections contained in – or attached to – outgoing emails.
Avoid Email Server Blacklisting with SpamTitan
Not all email filtering solutions have mechanisms to avoid email server blacklisting. However, SpamTitan has taken these factors into account in the design of SpamTitan Cloud and SpamTitan Gateway. Both of our solutions for email filtering use “URIBL” and “SURBL” protocols to compare links contained within inbound emails and their attachments against a global blacklist of known malicious and phishing sites.
The same protocols – along with several other mechanisms – are used in the scanning of outbound mail to ensure it is clear of viruses and could not be interpreted as having spammy content. Outbound scanning would also identify spam emails originating from a spambot or a compromised email account in order to prevent it from being sent and avoid email server blacklisting.
Naturally, you do not want your end-users to be under the impression that their emails have been sent when they are caught by the outbound filter. So SpamTitan Cloud and SpamTitan Gateway have comprehensive reporting features that advise of any problems in order that the problems can be rectified quickly and effectively – certainly more quickly than trying to get your organization´s IP address removed from a Realtime Block List.
by titanadmin | Aug 31, 2016 | Phishing & Email Spam, Spam News |
The use of Word macros and malicious JavaScript to deliver malware is nothing new; however, Microsoft has recently discovered that malicious actors are using malicious OLE embedded scripts to deliver a different payload. The discovery had prompted the software giant to issue a warning to Windows users to alert them to the risk.
Attackers are using the MS Office object linking and embedding (OLE) function to insert malicious scripts into spam emails. Social engineering techniques are also used to encourage users to double click on the malicious OLE embedded scripts.
The spam email messages used for these campaigns are simplistic, but effective. They appear to contain an invoice or receipt in the form of an attached Word document. However, the document contains a malicious JS script called Trojan:JS/Certor.A. Running the script will result in the users’ proxy settings being changed which will allow the attackers to steal authentication credentials and other sensitive data.
Opening the attached Word document will not automatically result in a user’s computer being compromised. The attached documents contain malicious OLE embedded scripts which are masked by text or icons. Typically, these embedded objects contain text asking the user to double click to view the invoice or receipt.
If the user double clicks as requested, they will receive a security warning on screen asking for confirmation that they want to open the file. The file will be identified as a Jscript Script file, but it will have an innocuous name. The user may not realize that the file is malicious. Although the names of the file are different for each campaign, they typically include terms such as PayPal, invoice, or receipt.
Allowing the file to be opened will see a range of malicious functions executed. Registry keys related to browser proxy settings will be modified, and a number of components will be dropped and executed. The malware even carries its own certificate.
The malware can be used to redirect users to malicious websites containing exploit kits, phishing campaigns, or ads. However, the malware will also enable the attackers to monitor HTTPS content and traffic and steal sensitive data such as login credentials entered on secure websites. The end user will be unaware that their computer has been compromised and that their actions online are being monitored.
To avoid infection, users have been told not to open attached files that are sent from unknown senders. Microsoft also says that this advice is all too often ignored by end users. For large businesses with many employees, preventing all users from running malicious OLE embedded scripts is a problem. There is always one employee that ignores security best practices. Unfortunately, all it takes for a network to be compromised is for one employee to run a malicious script.
The best step to take to ensure this doesn’t happen is to use a powerful spam filtering solution such as SpamTitan. SpamTitan stops 99.97% of spam emails from being delivered to end users’ inboxes.
Additionally, to prevent malicious OLE embedded scripts from being run, Microsoft offers the following advice:
“For added defense-in-depth, you can reduce the risk from this threat by following [Microsoft] guidance to adjust the registry settings to help prevent OLE Embedded Objects executing altogether or running without your explicit permission.”
by titanadmin | Aug 25, 2016 | Email Scams, Phishing & Email Spam |
Users of Apple devices have been warned about a new fake invoice email scam that attempts to get them to provide attackers with their bank details.
Another Email Scam Targets Apple Device Users
Criminals are sending spam emails in the millions in the hope that they will be received by owners of Apple devices. The spam emails contain a bogus invoice which indicates the user’s iTunes account has been used to download a number of videos, games, singles, and albums.
The fake invoice includes Apple logos and details of the amounts charged for each purchase. The email is intended to scare iTunes account holders into thinking their account has been compromised and used to make fraudulent purchases.
At the bottom of the invoice is a link for users to click if they did not authorize the purchases. The email recipient is told that they have 14 days to query purchases and receive refunds. However, clicking the “manage my refunds” link will not take the user to the Apple App Store website, but to a spoof site where they are asked to enter in their bank account information. The attackers claim that a refund will be given; however, divulging bank account details will enable the attackers to make fraudulent charges to the users’ accounts.
Both Apple and the FBI are investigating the latest fake invoice email scam. While Apple has not released a statement about this fake invoice email scam, after previous email spam campaigns Apple has told customers that they would not be asked to reveal sensitive information such as bank account details, passwords, and credit card numbers in emails.
When bank account information is required, such as to set up an iTunes account, the web address will be a subdomain of apple.com: store.apple.com for example. Apple advises customer never to reveal their sensitive information on any non-Apple website.
Fake Invoice Email Scam Targets Netflix Users
Criminals often spoof popular websites and attempt to phish for sensitive information such as credit card numbers and bank account details. Netflix it another popular target for scammers due to the number of subscribers to the service. A similar fake invoice email scam is also being used to fool Netflix account holders into disclosing their bank account information.
The spam emails contain an invoice for a subscription to Netflix claiming the user’s account will be charged to renew their subscription. The funds will be automatically taken from users’ accounts unless action is taken to change their auto-renew settings.
As with the Apple scam, a link is provided on the invoice which allows the email recipient to manage their subscription settings. The email appears to have been sent from Netflix, but clicking the link in the email will similarly take the user to a scam site. They are then taken through a series of steps to manage their subscription, which involves confirming their bank account details.
How to Avoid Becoming a Victim of Email Scams
These fake invoice email scam are designed to catch out the unwary and scare people into revealing sensitive information. However, by adopting some email security best practices it is easy to avoid scams such as these.
If you are sent an invoice in an email that claims to be from a web service, never click on the links in the email, no matter how realistic the email appears to be. Instead visit the official website and check account details or account charges directly on that website.
Cybercriminals often include links to spoofed websites in an attempt to obtain sensitive information, although the links can also direct the email recipient to a website hosting an exploit kit. Exploit kits probe for vulnerabilities in browsers and plugins that can be exploited to automatically download malware.
It is safest to assume that all attachments sent via email could be malicious. Never open an email attachment contained in an email unless you are 100% sure that it is genuine. Cybercriminals use email attachments to transmit malware and ransomware. Opening an attachment can potentially result in a malware infection.
Small business owners should use software solutions to prevent the downloading of malware. While anti-virus and anti-malware software can prevent malware from being installed, cybercriminals are developing highly sophisticated malware which is not detected by anti-virus software. By installing a spam filtering solution such as SpamTitan, small businesses can prevent these malicious emails from being delivered to end users’ inboxes. This reduces reliance of employees’ ability to identify phishing and scam emails.
Version française de cet article.
by titanadmin | Jul 30, 2016 | Email Scams, Phishing & Email Spam, Spam News |
A highly sophisticated PayPal email scam has been uncovered that is being used to deliver banking malware. Rather than promise the email recipient a sum of money or the opportunity to claim an inheritance from a long lost relative, this PayPal email scam claims a payment has been made to the victims account and that the money needs to be refunded.
The scam emails say that $100 has been fraudulently sent to the victims account and a refund is requested. The emails contain PayPal logos and appear to have been sent directly from PayPal. The emails appear to have been sent from the members@paypal.com email account. The message contains the subject line “You’ve got a money request”.
It is not clear how the attacker has managed to spoof the PayPal email account, or how the email manages to bypass the spam filter of Gmail.
If the victim responds to the email and makes the payment they will have lost $100; however, that is not all. The victim will also have malware loaded onto their computer. The malware will be loaded automatically regardless of whether the payment is made.
A link is contained in the email which the user must click to find out more about the transaction. The link contains a shortened URL and directs to a document detailing the transaction. The document has a goo.gl address and the link appears to be a jpeg image of the transaction details.
However, clicking the link will result in a javascript (.js) file being downloaded onto the victim’s computer. The script will download a flash executable file, which will install the malware if it is run.
Chthonic Banking Malware Delivered via PayPal Email Scam
The malware that is installed is a variant of the infamous Zeus banking malware – Chthonic. This malware has been programmed to inject its own code and images into banking websites. When the victim visits their online banking website the malware captures login names, passwords, PIN numbers, and answers to security questions. Many banking malware variants target a small number of financial institutions; however, Chthonic is capable of recording information entered into more than 150 different banking websites. Victims are primarily in the UK, US, Russia, Japan, and Italy.
Chthonic isn’t the only malware delivered. Researchers at Proofpoint have determined that an additional previously unknown malware variant called AZORult is also installed onto victims’ computers. Little is known about this new malware variant.
by titanadmin | Jul 28, 2016 | Email Scams, Internet Security, Phishing & Email Spam |
As the sports spectacular fast approaches it is time to be on high alert for Rio Olympics email scams. The Olympics have not yet started, but the scammers have certainly been active. Many new Rio Olympics email scams have been spotted in recent weeks and the number will certainly increase as the opening ceremony draws closer.
Any large sporting event that attracts massive global media interest is a good opportunity for scammers. With sports fans hungry for news of the latest events, information about competitors, or the latest betting odds, it is all too easy for the guard to be let down. A scramble for last minute tickets sees scammers rake in hundreds of thousands of dollars.
Many scammers feel that the Olympics is shooting fish in a barrel season. Which sadly it is.
Kaspersky Lab has reported that the first Rio Olympics email scams were uncovered as early as 2015; however, as the opening ceremony draws closer activity has increased by several orders of magnitude. In the UK, Action Fraud – the National fraud reporting body – has already received reports of 47 cases of fraud relating to the Rio Olympics, which has resulted in attackers gaining more than £300,000 ($392,800) in funds.
Watch out for these Rio Olympics Email Scams
The Rio Olympics email scams are as diverse as the events being competed over the 17-day competition. It is therefore a time to be particularly cautious.
Criminals are after bank details for fraudulent transfers, credit card details to make purchases, personal data for identity theft, and login credentials for all manner of nefarious activities. It is a time for everyone to be on their guard. Be prepared for a barrage of Rio Olympics email scams over the next few weeks and keep your wits about you online.
Fake Tickets Scams
The price of a ticket to the opening ceremony will cost anywhere between $60 to $1,400, although touts are offering tickets at vastly inflated prices. Ticket prices to see the most popular events can cost several thousand dollars. If a scammer can get a victim to part with their hard earned cash it could potentially be a big payday. If you are still planning on attending and you haven’t yet purchased a ticket, only buy from official sellers.
Scammers have already registered a host of official-looking domain names to fool the unwary into purchasing tickets and parting with their credit card numbers. The websites use official logos that have been lifted from the Internet and appear genuine. Fake or cheap SSL certificates are also purchased making the connections appear secure, yet checks may not have been performed on the company. A SSL (website starting with https) does not guarantee it is genuine. Before parting with your money, at least perform a WHOIS search on the domain owner. Fake domains have usually been purchased in the past few weeks or months. Also perform some online checks to make sure the website is genuine.
Be aware that just because a website ranks highly in the search engines it doesn’t mean it is legitimate. Many scammers use search engine poisoning to increase the rank and position of their websites. They may even appear above those of official ticket vendors.
Many Rio Olympics email scams direct sports fans to unofficial ticket sellers and scam websites. You will at best pay over the odds for a ticket, but most likely you will just be giving your money to a scammer and no tickets will ever arrive in the post.
Congratulations! You Have Won!
If you receive an email informing you that you have won (insert amazing prize here), chances are it is a scam. If it sounds too good to be true, it most probably is. While many Rio Olympics email scams attempt to get individuals to disclose bank details and credit card information, a great deal attempt to obtain money by other means.
Many Rio Olympics email scams direct users to official looking scam websites. Be very careful about disclosing any information on any website during the Olympics.
Emails are sent with fake attachments which, if opened, will infect the email recipients’ computer with malware or ransomware. Malware can log keystrokes and obtain login credentials. Ransomware will encrypt files and a ransom must be paid in order to obtain decryption keys. Links contained in websites often direct users to malicious websites where drive-by malware downloads take place.
Olympics and Zika News
If you are a sports fan and you want to follow the latest news, search for sports sites online and bookmark the pages. Do not click links contained in emails that are delivered to your inbox or spam folder. Many people click on any links contained in emails that seem interesting. Doing so could prove very costly. Scammers are sending out fake news emails or links to legitimate stories. Those links do not direct the recipient to news websites, but to sites loaded with exploit kits which download malware and ransomware onto users’ computers.
Fake Prize Draws
Social media is awash with offers to enter prize draws to win tickets to the Olympics. Be exceptionally careful about disclosing any personal information on social media sites. Scammers often use fake prize draws to obtain sensitive personal data. Those data can be used for future email scams, or to gain access to online accounts. Phishing campaigns are rife during the Olympics.
Fake lottery scams are also commonplace. Emails are sent out in the millions telling recipients they have won a prize draw or lottery. To claim the winnings, it is necessary to pay an admin fee and disclose credit card details or provide bank details for the transfer along with other sensitive information. The golden rule is: If you have not entered the draw, you cannot have won it. If you are asked to make a payment in order to receive winnings it is likely a scam.
If in any doubt as to the legitimacy of an email, delete it. Chances are you have not won a competition you have not entered and you are not lucky enough to have won an all-expenses paid trip to Rio to see the Olympics. It is likely to be one of the many Rio Olympics email scams currently circulating cyberspace.
Protecting Employees and Networks from Attack
Businesses need to take care to protect their networks and prevent their employees from inadvertently downloading malware or giving attackers a foothold in their network. There are plenty of malicious actors that will be using the frenzy surrounding the Rio Olympics to conduct their nefarious activities.
One of the best defenses against Rio Olympics email scams – and other malicious email spam in general – is to use a robust email spam filter such as SpamTitan. SpamTitan blocks 99.97% of email spam, preventing malicious emails from being delivered to end users.
To find out how SpamTitan can help you improve your security posture and prevent malware, ransomware, and phishing emails from being delivered to your employees, give the TitanHQ sales team a call today.
by titanadmin | Jul 27, 2016 | Internet Security, Network Security, Phishing & Email Spam, Spam News |
According to the latest threat report from Proofpoint the top email security threat is now Locky ransomware. Locky, which is primarily distributed via spam email, has become the biggest threat to businesses in the past quarter. Locky is delivered via JavaScript email attachments which download the malicious file encrypter onto the computers of unsuspecting users.
Locky Ransomware Replaces Dridex as the Top Email Security Threat
Locky was first identified in February 2016 and is believed to have been released by the criminal gang behind the Dridex banking malware. In fact, Locky is distributed using the infamous Necurs botnet, one of the largest botnets currently in operation. Necurs was also used to deliver Dridex malware, which was the top email security threat in Q1. Figures from Proofpoint suggest Locky has been used in 69% of email attacks involving malicious documents in Quarter 2, 2016.
Not only is Locky now the top email security threat, malicious message volume also increased significantly in quarter 2. Proofpoint charted the rise in malicious email volume and the Quarterly Threat Summary shows volume has increased by 230% since Q1, 2016.
Bear in mind that the huge rise in malicious emails occurred even though the Necurs botnet went silent in early June and Locky emails essentially stopped being delivered. However, the botnet did not remain inactive for long. By the end of June it was back with a vengeance, with huge volumes of Locky emails delivered as part of a massive new campaign.
Malicious emails are now being sent at rates that have never before been seen, with JavaScript email attachments the delivery method of choice. Stopping these messages from being delivered now requires automated anti-spam solutions. According to Proofpoint, “Organizations must have a scalable, automated defense against email-based advanced threats that can adapt to new techniques and approaches.”
Exploit Kits Are Mostly Delivering CryptXXX Crypto-Ransomware
While Locky may be the top email security threat, exploit kits still pose a major risk to businesses and personal computer users. The Angler exploit kit may have died a death in early June, but Neutrino has now taken over as the EK of choice. Neutrino is targeting numerous vulnerabilities and CryptXXX crypto-ransomware is the main threat. The ransomware variant only appeared in Q2, but it has fast become a major problem and the most common EK threat.
CryptXXX may now be the most prevalent EK ransomware variant in use; however, there has been an explosion in the number of ransomware variants in 2016. Since the final quarter of 2015, the number of ransomware variants has increased by a factor of between 5 and 6 according to Proofpoint. The majority of ransomware is delivered via exploit kits, although many users are directed to malicious websites via links delivered by spam email.
Fortunately, EK activity has fallen considerably since April. Angler EK activity started to decline in late April and by the start of June EK activity had dropped by around 96%. Since the end of June, EK activity has started to increase with Neutrino the main EK now in use. Fortunately, EK activity has not returned to pre April levels. So far at least.
by titanadmin | Jul 22, 2016 | Internet Security, Phishing & Email Spam, Spam News |
CryptXXX has fast become one of the most prevalent strains of ransomware, although until recently infection was only possible via malicious websites. Now researchers at Proofpoint have spotted CryptXXX ransomware emails. The group behind the attacks have added a new attack vector. CryptXXX ransomware emails contain a Word document containing a malicious macro. If the macro is allowed to run it will load a VB script into the memory which will use Powershell to make contact with the attackers’ command and control server. Once a connection has been made, CryptXXX will be downloaded onto the victim’s computer. Authors have realized the benefits to be gained from adopting an affiliate model to help infect machines and now a number of new players have entered the ransomware market.
If a “ransomware kit” is provided, individuals with little hacking skill can conduct their own ransomware campaigns. The ransomware authors can charge a nominal fee for supplying the kit, and can also take a cut on the back end. When an affiliate infects a computer and a ransom is paid, the authors receive a cut of the payment. This model works well and there is no shortage of individuals willing to try their hand at running ransomware campaigns. The CryptXXX ransomware emails are being sent by an affiliate (ID U000022) according to Proofpoint.
Identifying CryptXXX Ransomware Emails
The CryptXXX ransomware emails are being sent with a subject line of “Security Breach – Security Report #Randomnumber.” The emails contain only basic information about a supposed security breach that has occurred. The security report is supplied as an attached Word document. The body of the email contains the date, time of the attack, the provider, location, IP address, and port. The email recipient is instructed to open the file attachment to view details of the attack and find out about the actions that should be taken.
The file attachment is given a name such as “info12.doc” according to Proofpoint. If the attached Word file is opened, a Microsoft Office logo is displayed. The user is informed that the document has been created in a newer version of Microsoft Office. The content of the document will only be displayed if macros are enabled. Enabling the macros will result in the VB script being loaded. Then ransomware will then be downloaded and users’ files encrypted.
There is no fix if files are encrypted. The victim must pay the ransom or lose their files. Once an infection has occurred, files can only be recovered from backups if the victim does not pay the ransom.
CryptXXX Ransomware Still Being Delivered by Neutrino
Since the demise of the Angler exploit kit, CryptXXX was moved over to Neutrino. There was a dramatic fall in infections as activity temporarily stopped; however, Invincea recently reported a surge in activity via compromised business websites. The SoakSoak botnet is being used to scan the Internet for vulnerable websites. The websites being targeted run the WordPress Revslider slideshow plugin. Scripts are appended to the slideshow that redirect visitors to a malicious site containing Neutrino.
CryptXXX will only be downloaded if the endpoint lacks certain security tools that would detect an installation. If Wireshark, ESET, VMware, Fiddler, or a Flash debugging utility is present, the ransomware will not be downloaded.
by titanadmin | Jul 12, 2016 | Email Scams, Phishing & Email Spam |
The Tennessee Board of Professional Responsibility has issued an alert warning of a new phishing scam after a number of attorneys received a fake notification of action phishing email.
The notification of action phishing email appears to have been sent from attorney regulatory agencies and requests the recipient clicks on a link or opens an infected email attachment to view the details of a new legal complaint. If the attachment is opened or the link is clicked, crypto-ransomware will be installed on the email recipient’s device. Files will be locked and a ransom demand will appear demanding payment in exchange for a decryption key.
Alerts Issued After Spate of Phishing Emails Received by U.S Attorneys
The Center for Internet Security also issued a cyber-alert recently after becoming aware of new email scams that were targeting U.S lawyers. Lawyers in Alabama, California, Florida, Georgia, Nevada, and Tennessee have all been targeted.
Last month, more than 50 lawyers reported receiving fake emails about new discipline investigations. The emails appeared to come from state disciplinary bodies and bar associations. The emails were designed to cause concern and prompt the recipient to click on links to find out more information.
In contrast to many phishing emails, this campaign appears to be targeted. The emails contain personal information about the recipient which may fool some attorneys into thinking the messages are authentic. The emails are particularly well written, which makes it harder to identify them as phishing scams.
While personal information is included, that information is likely to have been taken from attorneys’ websites or social media websites such as LinkedIn.
Some of the emails indicate a complaint has been filed against the recipient, some claim that the individual’s bar membership has lapsed. The links contained in the emails direct users to a spoofed website where a drive-by malware download occurs.
How to Identify a Notification of Action Phishing Email
Since the latest emails have been personalized and are well written, identifying them as fake is a little harder than with standard phishing emails.
To prevent a drive-by download of malware it is important to ensure that browsers and plugins are kept up to date. Email links from unknown recipients should not be clicked, and even if the email appears to be genuine care should be exercised.
If a notification of action phishing email appears to have come from a regulatory body, the recipient should visit the appropriate website by entering in the URL directly into their browser. Hovering the mouse arrow over the link will show the real address that that the recipient will be directed to if the link is clicked. Oftentimes this will display an alternate URL.
Anti-spam email solutions such as SpamTitan offer an additional level of protection. SpamTitan blocks 99.97% of spam emails from being delivered.
by titanadmin | Jul 11, 2016 | Email Scams, Phishing & Email Spam, Spam News |
A new, sophisticated Game of Thrones phishing scam has been uncovered which is targeting individuals who illegally download pirated copies of the HBO series. Game of Thrones is the most pirated TV show in history, with many individuals choosing to illegally download the latest episodes to get their GOT fix. This has not escaped the attention of scammers.
Game of Thrones Phishing Scam Emails Sent via ISPs
The scammers have used an innovative trick to make their scam more realistic. The emails claim to have been sent by IP-Echelon, the company that is used by HBO and other entertainment companies to enforce copyright claims. IP-Echelon has already sent many copyright infringement emails to illegal downloaders of movies and TV shows on behalf of a number of companies.
The Latest Game of Thrones phishing scam uses emails that appear to have been generated by IP-Echelon. The emails are extremely well written and contain the same language that is used by the organization when sending out legitimate notices to ISPs.
The ISPs, believing the copyright infringement notices to be genuine, then forward the emails to customers. Since the notice is sent by the ISP, the Game of Thrones phishing scam appears to be genuine.
The customer is told that they must settle the case promptly – within 72 hours – in order to avoid legal action. To settle the case, the customer must visit a link to review the settlement offer and make payment. Failure to do so will see that settlement offer withdrawn. The email says that the settlement about will increase as a result.
The scam has been run in the United States, although there have been a number of reports of individuals in Canada, Europe, and Australia also having been targeted with the same email scam.
A Convincing Phishing Scam That Has Fooled Many ISPs
It is unclear at this point whether the scammers are specifically targeting individuals who have accessed torrent sites and have downloaded torrent files, or whether the emails are being sent out randomly. Some individuals have taken to Internet forums to claim that they have not performed any illegal downloads, while others have been using torrent sites to illegally download TV shows and movies.
HBO has previously taken action over illegal downloaders and has used IP-Echelon to send out notices very similar to those being used by the scammers. Since the Game of Thrones phishing scam appears to be so realistic, many illegal downloaders may be fooled into making the payment. However, that payment will go directly to the scammers.
As is the case with all email requests such as this, the recipient should take steps to verify the authenticity of the email prior to taking any action. Contacting the company that sent the message – using the contact telephone number on the company’s official website – is the best way to confirm authenticity. Email recipients should never use any contact information that is sent in the email body.
Some ISPs have taken steps to confirm the authenticity of the emails and have discovered they are a scam, but not all. Many have been forwarded on by ISPs who believed the scam emails to be legitimate.
by titanadmin | Jul 7, 2016 | Email Scams, Phishing & Email Spam |
A new phishing scam has been discovered that is being used to steal the login credentials and phone numbers of employees. The new scam uses blurred images of invoices to lure victims into revealing sensitive information. In order to view the document or spreadsheet in higher resolution, the victim must supply their email address and password. It is not clear whether this blurred image phishing scam is being used for targeted attacks on businesses or whether the emails are being sent out randomly.
The Blurred Image Phishing Scam
A number of different versions of the same scam have been discovered by the Internet Storm Center, each of which uses a different document.
The initial email appears to have been sent from a legitimate company – a well-known company likely to be very familiar to most business users. HSBC for example. The emails contain corporate logos and are well written. They contain a link that must be clicked to view a purchase order or invoice.
Clicking the link will take the email recipient to a webpage where they are presented with what appears to be a legitimate document. The attackers use a screenshot of an excel spreadsheet (or word document) which appears blurred. The screenshot was taken on a low resolution yet is displayed in high resolution to ensure it cannot be read, although it is clear what the document is.
In order to view the file, the victim is required to enter their email and password in a popup box to confirm their identity. The popup asks for the victim’s email account credentials. The attackers use a JavaScript file to validate the email address.
The login credentials are harvested and sent to the attacker along with the victim’s location and IP address. Users are subsequently directed to a fake Google authentication portal where they are asked to supply their phone number. If the victim enters their details and clicks to view the document, a PDF file will open.
This blurred image phishing scam may not be particularly sophisticated – it uses simple JavaScript, HTML and PHP – but it is still likely to be effective. The blurred images and corporate images may be enough to fool many users into believing the emails are legitimate.
by titanadmin | Jul 5, 2016 | Email Scams, Phishing & Email Spam, Spam News |
The EU referendum that recently took place in the United Kingdom has sparked a spate of Brexit phishing attacks. Brexit – a contraction of British exit from the European Union – has caused considerable economic turmoil in the UK and a great deal of uncertainty about the future. It is not only the UK that has been affected. The decision of 52% of British voters to opt to leave the EU has had an impact on markets around the world.
Whenever a big news story breaks, criminals seek to take advantage. Cybercriminals have been quick to take advantage of the UK EU referendum result and have launched a wave of Brexit phishing attacks which trick people into downloading malware onto their computers.
The Brexit phishing attacks are being conducted using spam email messages. Attackers are sending out emails in the millions with subject lines relating to the Brexit result. The emails play on fears about the uncertainty of the financial markets, the economic turmoil that has been caused, and the political upheaval that has followed.
The emails contain malicious attachments which, if opened, install malware onto the victims’ computers. Many email messages contain links to malicious websites where drive-by malware downloads take place. Some of the emails offer victims help to keep their bank accounts and savings protected from currency fluctuations. In order to protect accounts, the victims are required to divulge highly sensitive information such as bank account details via scam websites.
The malware being sent is capable of logging keystrokes made on computers. These malicious software programs then relay sensitive information such as online banking login information to the attackers, allowing them to make fraudulent transfers.
All computer users should be extremely wary about unexpected email messages. Opening file attachments sent from unknown senders is risky and may result in malware being loaded onto computers. Ransomware can also be installed. The malicious software locks files until a ransom payment is made to the attackers.
Any email that contains a link to a news story should be deleted. The story will be covered by the usual news websites if it is genuine. Those sites should be accessed directly through the browser or via the search engines.
Organizations can protect their networks and users from Brexit phishing attacks and other malicious spam email campaigns by installing a spam filtering solution such as SpamTitan. SpamTitan captures more than 99% of spam email, preventing phishing emails from being delivered. This reduces reliance on employees being able to identify a phishing scam or malicious email.
by titanadmin | Jul 4, 2016 | Email Scams, Phishing & Email Spam, Spam News |
Facebook phishing attacks are fairly common. The website has 1.65 billion active monthly users, a considerable number of which access the social media platform on a daily basis. With such a huge number of users, it is understandable that criminals often target users of the platform.
However, the latest phishing scam to target Facebook users is notable for the speed and scale of the attacks. Kaspersky Lab reports that the latest Facebook phishing attacks have been claiming a new victim every 20 seconds.
The Facebook phishing attacks took place over a period of two days, during which time more than 10,000 Facebook users had their computers infected with malware.
The phishing scam involves site users being sent a message from their ‘friends’. The messages say the user has been mentioned in a comment on a Facebook post. However, when they respond to the message they download a Trojan onto their computers and inadvertently install a malicious Chrome browser extension. In the second phase of the attack, the Trojan and the browser extension are enabled.
When the victim next logs into Facebook the login details are captured and sent to the attacker. This gave the attackers full control of the victims’ Facebook accounts. This allows them to make changes to the privacy settings, steal data, and send their own messages to all of the victims’ contacts on Facebook. The attacks were also used to register fraudulent likes and shares.
The attackers took steps to prevent the infections from being detected. The malware was capable of blocking access to certain websites which could potentially result in the victims discovering the malware infection. The websites of a number of cybersecurity sites were blocked, for instance.
The phishing attack mostly affected Facebook users on Windows computers, although Kaspersky Lab noted that Windows mobile phones were also compromised in the attacks. Individuals who accessed Facebook via Android and Apple phones were immune.
The attacks concentrated on users in South America, with Brazil the worst hit, registering 37% of the Facebook phishing attacks. Columbia, Ecuador, Mexico, Peru, and Venezuela were also heavily targeted. Attacks in Europe were mostly conducted on users in Poland, Greece, and Portugal, with Germany and Israel also hit hard.
The malware used in the latest Facebook phishing attacks is not new. It was first identified about a year ago. Kaspersky Lab reports that the attackers are most likely of Turkish origin, or at least Turkish-speaking.
What sets this phishing scam apart from the many others is the speed at which users were infected. However, the response to the attacks was also rapid. Users who discovered infections spread the news on Facebook, while the media response helped to raise awareness of the scam. Google has also taken action and has now blocked the malicious Chrome extension.
by titanadmin | Jun 29, 2016 | Email Scams, Phishing & Email Spam, Spam News |
Cybercriminals are conducting CEO fraud scams with increasing frequency and many organizations have already fallen victim to these attacks. Many companies have lost tens of thousands of dollars as a result of these criminal attacks. In some cases, companies have lost hundreds of thousands or millions of dollars.
What are CEO Fraud Scams?
CEO fraud scams involve an attacker impersonating the CEO of an organization and sending an email to the CFO requesting a bank transfer to be made. The account details of the attacker are supplied, together with a legitimate reason for making the transfer. Oftentimes, these scams involve more than one email. The first requests the transfer, followed by a second email with details of the amount and the bank details for the transaction. By the time the fraudulent transfer is discovered, the funds have been withdrawn from the account and cannot be recovered.
The FBI has issued warnings in the past about these CEO fraud scams. A spate of attacks occurred in Arizona recently. The average transfer request was between $19,000 and $75,000. An April 2016 FBI warning indicated $2.3 billion in losses had been reported between October 2013 and February 2016, with CEO fraud scams increasing by 270% since January 2015.
By training all employees on the common identifiers of phishing emails and also to be more security aware, organizations can reduce the risk of attacks being successful. However, while training is often provided to employees, it is not always given to executives and the CEO. According to a recent survey conducted by Alien Vault, only 44% of IT security professionals said every person – including the CEO – received training on how to identify a phishing email.
Protecting Against CEO Fraud Scams
It is possible to take steps to prevent CEO fraud scams. Email security solutions – SpamTitan for example – can be configured to prevent emails from spoofed domains from being delivered; however, if the email comes from the account of a CEO, there is little that can be done to prevent that email from being delivered. It is therefore essential that training is provided to all members of staff – including executives – on phishing email identification techniques.
Alien Vault polled 300 IT security professionals at Info Security Europe 2016 to determine how prepared organisations were for phishing attacks and what steps had been taken to reduce risk. The results of the survey show that the majority of organisations now provide training to reduce risk, although almost one in five are not taking proactive steps to reduce the risk of phishing and CEO fraud scams.
Almost 45% of companies said they train every single person in the organization on phishing email identification techniques, while 35.4% said that most employees are trained how to identify malicious emails. 19.7% said they do not take proactive steps and deal with phishing problems as and when they occur.
37% of Executives Have Fallen for a Phishing Scam
Out of the 300 respondents, 37% reported that at least one executive had fallen for a phishing scam in the past, while 23.9% of respondents were unaware if they had. However, even though many had experienced phishing attacks, IT security professionals were not confident that such attacks would not happen again in the future.
More than half of respondents believed that company executives could fall for a scam, while nearly 30% said that if the scam was convincing, their executives may be fooled. Only 18.5% said that their executives had been thoroughly briefed and were well aware of the dangers and would not fall for such a scam.
CEO fraud scams can be extremely lucrative for attackers, and oftentimes a considerable amount of time is spent researching companies and crafting clever emails. A variety of social engineering techniques are used and the emails can be very convincing.
Training is important, but it is also vital that efforts are made to ensure the training has been effective. The best way to ensure that all individuals have understood the training is to conduct phishing exercises – Sending dummy phishing emails in an attempt to get a response. This allows IT departments to direct further training programs and ensure that weak links are addressed.
by titanadmin | Jun 28, 2016 | Phishing & Email Spam, Spam News |
A new Microsoft Office 365 zero day vulnerability is being exploited by hackers to deliver Cerber ransomware. The latest attack is being conducted on a large scale and it has been estimated that millions of business users have already been impacted by the latest Cerber ransomware campaign.
It can be difficult to keep up to date with all of the ransomware variants currently being used by cybercriminals. The malicious file-encrypting software is constantly being tweaked and reinvented by cybercriminals. Cerber ransomware especially. The criminals behind Cerber frequently change its attack mode.
Cerber was first seen in February this year and has already been delivered using a variety of methods, most recently via the Dridex botnet. Spam emails containing malicious Word macros has been favored in the past. If allowed to run, the macros would download Cerber onto victims’ devices. Cerber would then proceed to encrypt documents, images, and a host of other file types.
Victims would be presented with a warning message on screen alerting them to the infection, and an audio file would be played to chilling effect. Cerber was unique in this respect, essentially speaking to its victims. Cerber has also been delivered using malvertising – advertisements placed in third party ad networks that direct web visitors to malicious webpages hosting exploit kits. Those exploit kits probe for browser and plugin vulnerabilities which are exploited to deliver the ransomware. That campaign mainly infected users that had failed to keep their Flash plugins up to date.
It is the rapid changes being made by the attackers that has made it so difficult to detect Cerber and prevent infections. Earlier this month, Invincea discovered that Cerber was able to manufacture new payload variants “on the fly”, allowing the attackers to bypass traditional signature-based anti-virus products. Unique hashes and payloads were being generated every 15 seconds! In tests, 40 unique hashes were discovered.
Cerber Ransomware is Now Infecting Users via Microsoft Office 365 Zero Day Vulnerability
The latest attack has bypassed many users’ anti-virus products according to security firm Avanan. It is unclear at this stage exactly how many organizations have been affected, although Avanan reports that 57% of its clients that use Office 365 have been hit.
Users who have not implemented additional email security controls have been infected via their cloud email accounts. The latest attack is bypassing the controls put in place by Microsoft and the spam emails are being delivered to end user accounts. Unfortunately, should Cerber ransomware be installed, the victims will have to recover the encrypted files from backups or pay the ransom.
The criminals behind the latest campaign may currently be exploiting the Microsoft Office 365 zero day vulnerability, but we can be sure that Cerber will continue to evolve.
To protect against Cerber ransomware attacks, business users must ensure that all patches and software updates are applied promptly.
Since ransomware is capable of infecting or deleting back up files, it is essential that backup devices are air gapped. When backups have been performed, the drives need to be disconnected.
Implementing an anti-spam solution – and not relying on Microsoft or Gmail anti-spam filters – can also help to keep businesses protected by reducing the risk of ransomware and other phishing emails from being delivered to end users.
by titanadmin | Jun 24, 2016 | Internet Security, Network Security, Spam News, Website Filtering |
After a period of quiet, the Necurs botnet is back in action. A number of security companies have reported a massive surge in botnet activity which started on June 21, 2016.
The Necurs botnet has previously been used to send out huge volumes of Dridex malware and Locky; a sophisticated ransomware variant that was first discovered in February 2016. It is too early to tell whether this is just a temporary spike in activity or whether the botnet will be sending emails at the levels seen before the recent lull.
Necurs botnet activity dropped off on May 31. The volume of malicious emails being sent using the botnet fell to as few as 3 million emails per day. However, the number of emails being sent surged on June 21, shooting up to around 80 million emails. 24 hours later the volume of malicious emails had doubled to 160 million. The surge in activity comes is linked to a massive spam email campaign that is delivering emails containing malicious attachments which install Locky ransomware.
It is unclear why there was a period of quiet. Security experts having been pondering this since the dramtic fall in activity on May 31.
The Necurs botnet is massive and is believed to contain approximately 1.7 million computers, spread over 7 separate botnets. It is clear that the botnet had not been taken down, although activity across all seven of the botnets stopped. In April and May of this year, spam email volume was regularly exceeding 150 million emails a day. Now the Necurs botnet appears to be back up to speed.
Around the same time as the pause in activity, Russia’s FSB security service conducted raids resulting in the arrests of approximately 50 hackers. The gang was using the Lurk Trojan to defraud banks and other targets in Russia. It is unclear whether some of those arrests resulted in a disruption to the botnet, or whether the pause was for some other reason. Numerous theories have been suggested for the three-week pause, including the sale or the botnet and issues the operators may have had with the C&C infrastructure. If the botnet has changed hands, a single organization would likely be in control as activity across all seven botnets resumed at the same time.
The resurrection of the Necurs botnet is bad news. According to Proofpoint, the resurrection of the botnet has been accompanied by a new Locky variant which has new capabilities. The latest form of Locky is better at evading detection and determining whether it is running in a sandbox. The new capabilities were detected by Proofpoint shortly before the Necurs botnet went dark.
by titanadmin | Jun 24, 2016 | Email Scams, Phishing & Email Spam |
A new Eir phishing scam has been uncovered which has prompted the Irish communications company to issue a warning to customers. Hundreds of customers received emails offering them a refund yesterday. To claim the refund, the email recipients have been instructed to login to their My Eir account. A fake link is supplied in the email which must be clicked to claim the refund.
Eir Phishing Scam Captures Credit Card Details of Customers
That link directs the email recipient to a fake webpage. The malicious website has been designed to look identical to the Eir website. Users are required to confirm their credit card details in order to obtain the refund. Those credentials are logged by the website and are sent to the criminals running the Eir phishing scam.
Eir has warned customers to be on the lookout for the fraudulent email messages and to delete them if they are received. Any individual who has fallen for the Eir phishing scam and has provided credit card details via the malicious website faces a high risk of credit/debit card fraud.
Phishing email campaigns such as this are commonplace. Attackers use a variety of social engineering techniques to get users to reveal sensitive information such as credit and debit card numbers, which are used by the attackers to make online purchases and rack up huge debts in the victims’ names.
The malicious emails can be extremely convincing. Criminals use legitimate imagery in the phishing emails to fool email recipients into believing the emails are genuine. The malicious spam messages usually contain a link that directs to victims to malicious websites where personal information must be disclosed in order to receive a refund, free gift, or to view important documents. The websites can look identical to the legitimate sites.
Spam Email Poses a Considerable Risk to Businesses
Email scams often direct victims to malicious websites containing exploit kits which probe for weaknesses in browsers and plugins and leverage those vulnerabilities to download malware.
The malware poses a considerable risk for businesses. Malware is used to gain a foothold in a computer network, which can be used to launch cyberattacks to steal valuable data or to gain access to corporate email and bank accounts.
To protect against such attacks, employees should be instructed never to use links sent in emails and to login to websites directly via their browsers. Employees should be provided with training to help them identify phishing emails and email and web spam.
Businesses should also use an anti-spam service such as SpamTitan to capture spam and phishing emails. Preventing the messages from being delivered to end users is the best form of defense against such attacks, and reduces reliance of employees to identify phishing scams.
by titanadmin | Jun 17, 2016 | Email Scams, Phishing & Email Spam, Spam Advice, Spam News |
The FBI issued a new public service announcement which includes new business email compromise scam data. The new data indicates U.S. businesses have lost almost $960 million to business email compromise scams in the past three years, and the total losses from these scams is now almost $3.1 billion.
What is a Business Email Compromise Scam?
A business email compromise scam is a sophisticated attack on a company by scammers that attempt to trick individuals into wiring funds from corporate accounts to the bank accounts of the attackers. Businesses most commonly targeted are those that frequently make foreign transfers to international companies. The attackers must first gain access the email account of the CEO or another high level executive. Then an email is sent from that account to an individual in the accounts department requesting a bank transfer be made. Occasionally the scammer asks for checks to be sent, depending on which method the targeted organization most commonly uses to make payments.
A business email compromise scam does not necessarily require access to a corporate email account to be gained. Attackers can purchase an almost identical domain to that used by the targeted company. They then set up an email account in the name of the CEO using the same format as that used by the company. This can be enough to fool accounts department workers into making the transfer. Business email compromise scams use a variety of social engineering techniques to convince the targeted accounts department employee to make the transfer.
Business Email Compromise Scams are a Growing Problem
The FBI has previously warned businesses of the growing risk of business email compromise scams. In April this year, the FBI Phoenix Office issued a warning about a dramatic rise in BEC attacks. The data showed that between October 2013 and February 2016 there had been at least 17,642 victims of BEC attacks in the United States, and the losses had reached $2.3 billion.
New data from the FBI suggest that the problem is far worse. The FBI has now incorporated business email compromise scam data from the Internet Crime Complaint Center (IC3). 22,143 reports have now been received from business email compromise scam victims, which correspond to losses of $3,086,250,090.
Between October 2013 and May 2016, there have been 15,668 domestic and international victims, and losses of $1,053,849,635 have been reported. In the U.S. alone, there have been 14,032 victims. Since January 2015, there has been a 1,300% increase in losses as a result of BEC attacks. The majority of the funds have been wired to Asian bank accounts in China and Hong Kong.
The FBI warns of five scenarios that are used by criminals to commit fraud using BEC scams:
- Requests for W-2s or PII from the HR department – The data are used to file fraudulent tax returns in the names of employees
- Requests from foreign suppliers to wire money to new accounts – Attackers discover the name of a regular foreign supplier and send an email request for payment, including new bank details (their own).
- Request from the CEO for a new transfer – The CEO’s (or other executive) email account is compromised and a request for a new bank transfer is sent to an individual in the accounts department who is responsible for making bank transfers
- A personal email account of an employee of a business is compromised – That account is used to send payment requests to multiple vendors who have been identified from the employee’s contact list
- Impersonation of an attorney – Emails are sent from attackers claiming to be attorneys, or representatives of law firms, requesting urgent transfers of funds to pay for time-sensitive matters
To protect against BEC attacks, businesses are advised to use 2-factor authentication on all business bank transfers, in particular those that require payments to be sent overseas. Organizations should treat all bank transfer requests with suspicion if a request is sent via email and pressure is placed on an individual to act quickly and make the transfer.
The FBI recommends that businesses never use free web-based email accounts for business purposes. Organizations should also be careful about the information posted to social media accounts, in particular company information, job descriptions and duties, out of office details, and hierarchical information about the company.
by titanadmin | Jun 16, 2016 | Email Scams, Phishing & Email Spam, Spam News |
The self-proclaimed Spam King, Sandford Wallace, has been sentenced to 30 months in jail for a Facebook spam campaign conducted between November 2008 and February 2009.
Wallace hacked approximately 550,000 Facebook accounts and used those accounts to post spam messages to users’ walls which directed their Facebook followers to webpages which harvested login credentials and other personal information.
For each account that was compromised, Wallace gathered details of the users’ friends and posted spam messages to their walls. Wallace used an automated script to sign into the hacked accounts and post spam messages. In total, more than 27 million spam messages were sent via those accounts. Wallace was allegedly paid for sending traffic to websites via the spam messages. Wallace’s activities earned him the nickname “Spamford” Wallace.
It has been widely reported that Wallace was a career spammer, having first made a business out of spamming in the 1990’s with a company called Cyber Promotions. The company was reportedly sending around 30 million spam emails a day.
Wallace had been found guilty of Internet offenses in civil cases in the past, resulting in a fine of $4 million in 2006 for use of malicious popup adverts and a fine of $230 million for phishing attacks via MySpace in 2008. This is the first time the spam king has received a criminal conviction for his online activities.
Wallace was indicted in 2011 for the improper accessing of Facebook accounts and for sending unsolicited adverts on three occasions, spread over a period of 4 days. He was banned from accessing Facebook, yet violated the court order resulting in a charge of criminal contempt of court. Wallace was released on a bond, and while he was due to be sentenced in December, the case had to be delayed after two of Wallace’s lawyers quit.
The Spam King’s campaigns have resulted in him being ordered to pay more than $1 billion in damages, although Wallace was unable to pay the civil fines.
Wallace was convicted of one count of fraud and related activity in connection with electronic mail and one count of criminal contempt. The Office of the United States Attorney for the Northern District of California recently announced the sentence, which was passed down by Judge Edward J. Davila.
In addition to the jail term, the spam king has been ordered to pay fines of over $310,000. Wallace could have received a maximum jail term of three years. Wallace will also be required to undergo 5 years of supervised release once the sentence has been served. That sentence begins on Sept, 7, 2016.
by titanadmin | Jun 7, 2016 | Internet Security, Phishing & Email Spam, Spam News |
Researchers at a number of Internet security firms have discovered a surge in JavaScript spam emails in recent months. The emails are being used to download Locky ransomware onto users’ devices and the problem is getting more severe.
The volume of JavaScript spam emails is increasing, as is the frequency of spam email campaigns. The attacks first started in early February, spiking in March/early April. There was something of a lull around the middle of April, yet by the end of the month the campaigns started again at an increased level. Volumes of JavaScript spam emails continued to rise throughout May.
JavaScript Spam Emails Being Favored by Spammers
The latest wave of JavaScript spam emails is being sent from IP addresses in India and Vietnam, and while the United States and Canada have not escaped, the emails are predominantly being used to target users in Europe. The emails contain a ZIP file containing malicious JavaScript files. If the user opens and unzips the file and opens a file, the JavaScript is executed and silently runs via the Windows Script Host Service (WSH) and downloads an intermediate malware known as JS/Danger.ScriptAttachment. This malware will then download Locky ransomware, although the attackers could easily update the campaign to deliver different malicious payloads. One security firm has reported that the wave of JavaScript spam emails is the biggest spam email campaign seen in recent years.
There are no known fixes for Locky ransomware infections. If Locky is installed on a computer, the users’ only defense is to restore encrypted files from a backup or face losing them permanently. This campaign masks the JavaScript with a XOR encryption algorithm to reduce the likelihood of detection.
Spike in Spam Emails Containing Malicious Office Macros
Combo Threat Research Labs also detected a surge in spam emails on May 17, with the campaign lasting 12 hours. During this spam email blitz, more than 30 million messages were sent. While the aim of the attackers was to download Locky ransomware onto users’ devices, the gang behind this campaign used fake Amazon shipping notices rather than JavaScript spam emails.
The documents containing the shipping notices contained a malicious macro. In order to open the attached file, users were required to enable macros on their devices. Doing so would trigger a ransomware download. Email recipients who have their office settings configured to automatically allow macros to run are at particularly at risk, as simply opening the email attachment would result in Locky being downloaded onto their devices.
Proofpoint also recorded this spike in malicious spam emails, although the company put the total number of emails in the campaign at over 100 million, making this one of the largest spam email campaigns seen in recent years, and certainly one of the biggest campaigns of 2016.
The Amazon spam email campaign is being distributed using spam botnets on virtual machines and consumer devices. This campaign was notable because the attackers were able to manipulate the email headers. This made the messages appear legitimate to email recipients. Any email recipients who regularly use Amazon.com for purchases could easily be fooled into opening the file attachment.
The emails used the subject line: “Your Amazon.com order has dispatched” along with a code number, closely mimicking the emails sent up Amazon. The body of the email did not contain any text. If users want to find out which order the email refers to, they would need to open the file attachment. The emails also appear to have been sent from the Amazon.com domain, making it much harder for email recipients to determine that the messages are malicious spam.
Surge in Spam Email Highlights the Importance of Using Spam Filtering Solutions
Spam email may have been in decline in recent years, but the latest waves of attacks clearly demonstrate that criminal gangs have far from given up on the medium for delivering ransomware. Spam emails containing links to malicious websites have remained at a fairly constant level over the past few months, yet JavaScript spam emails and malicious macros have surged. These spam email spikes show just how important it is to use a robust spam filtering solution such as SpamTitan.
SpamTitan captures 99.97% of spam email and prevents malicious spam emails from being delivered to inboxes. Since malicious actors are getting much better at masking their messages and making them appear legitimate, it is essential to limit the volume that are delivered to end users rather than rely on individuals to be able to identify emails as spam.
by titanadmin | Jun 6, 2016 | Internet Security, Website Filtering |
A recent report issued by the Anti-Phishing Working Group highlights worrying phishing activity trends. According to the Phishing Activity Trends Report, the number of new phishing websites is growing at an alarming rate.
A recent report published by PhishMe showed that email phishing activity has now reached unprecedented levels. Phishing email volume increased by 789% quarter over quarter. The APWG report shows that cybercriminals are also increasingly conducting web-borne attacks. Phishing websites increased by 250% from the last quarter of 2015 through the first quarter of 2016.
APWG expected to see an increase in the number of phishing websites created in the run up to the holiday season. Every year, criminals take advantage of the increased number of online purchases being made around Christmas. Many new phishing websites are created in November and December and online fraud always increases in December.
However, typically, there is a drop in spamming an online fraud in January. This year that fall did not occur. In fact, the number of new phishing websites continued to rise in January. There was a slight fall in February, before a major increase in March. According to the Phishing Activity Trends Report, in December 2015, 65,885 unique phishing websites were detected. In January 2016, the total had risen to 86,557. By March the total had reached a staggering 123,555 unique phishing websites.
Cybercriminals are most commonly targeting the retail sector and are spoofing websites in an attempt to defraud consumers. 42.71% of phishing websites target the retail sector, with the financial sector in second place with 18.67% of sites. Payment services accounted for 14.74% of sites, ISPs 12.01%, and multimedia sites 3.3%.
The phishing activity trends report indicates an increase in the targeting of cloud-based or SAAS companies, which it is claimed is driving the attacks on the retail sector.
More than 55% of phishing websites contain the name of the target brand somewhere in the URL. Attackers are concentrating the attacks on the most popular brands. By March 2016, APWG reported that 418 different brands were being targeted using phishing websites.
Phishing email campaigns are known to be sent extensively from outside the United States, although when it comes to phishing websites they are usually hosted in the United States. 75.62% of phishing websites are hosted in the US.
The United States also hosts the most phishing-based Trojans and downloaders – 62.36%. China is also being extensively targeted. China hosted 5% of phishing-based Trojans and downloaders in January. By March, the figure had risen to 13.71%.
More than 20 million new malware samples were detected at the start of 2016 – That’s an average of 227,000 new malware samples every day. The majority of new malware are Trojans, which account for 66.81% of new samples. Viruses were second (15.98%) and worms third (11.01%).
The massive rise in phishing websites highlights how important it is for caution to be exercised when purchasing online. Businesses should also take additional precautions. Web filters can be used to block phishing websites from being visited by employees. A web filtering solution – WebTitan for example – can also be used to prevent drive-by downloads of malware and ransomware.
by titanadmin | Jun 4, 2016 | Phishing & Email Spam, Spam News |
The latest phishing email statistics released by the anti-phishing training company PhishMe show the extent to which the use of phishing has increased in recent months.
PhishMe compiles quarterly phishing email statistics and tracks the volume of phishing emails being sent. During the first three months of 2016, the volume of phishing emails increased by a staggering 789%. More than 6.3 million more phishing emails were sent in Q1, 2016 than in Q4, 2015.
According to the quarterly report, the biggest problem currently faced by personal and corporate computer users is ransomware. Ransomware emails now account for more than 93% of all phishing emails. Ransomware offers a quick payout for cybercriminals and the campaigns can be quickly developed and run. In fact, ransomware emails are being sent by criminals with little or no programming skill. They can simply purchase ransomware kits on darknet marketplaces and obtain a cut of the ransom payments that are made.
Targeted ransomware attacks are now being conducted on businesses of all sizes. Criminals are well aware that many organizations do not regularly perform backups of critical data. Even when backups are performed, many organizations do not unplug their backup devices. The latest ransomware variants are capable of deleting Windows shadow copies and encrypting backup files on connected storage devices. This gives organizations no alternative but to pay the ransom demand to recover files. The biggest threat is now Locky. Locky is delivered via spam email using JSDropper or malicious Word macros.
PhishMe’s phishing email statistics also show two other main trends. Cybercriminals are tending to concentrate on soft-targeted campaigns. Spear phishing emails target just one or two individuals, but the latest trend sees malicious emails messages sent to a group of individuals in an organization – the billing department for instance. The emails are targeting specific roles in an organization rather than specific individuals.
The phishing email statistics also show a rise in the use of JSDropper applications. JSDropper applications are now present in around a third of all phishing emails. Malicious Word macros are still extensively used to infect computers with malware and ransomware, but JavaScript applications are now the most common type of malicious files sent in phishing emails according to the report.
The increase in malicious spam email shows how important it is for organizations to employ a robust spam filtering solution – SpamTitan for example – and to also ensure that employees are informed of the high risk of phishing attacks occurring. Employees should also be instructed how to identify phishing emails and told how they should respond if they believe they have been sent a malicious email message.
by titanadmin | Jun 2, 2016 | Email Scams, Phishing & Email Spam, Spam Advice, Spam News, Spam Software |
A new report by anti-phishing training company PhishMe shows a marked rise in the volume of ransomware emails in March. The report shows that spam emails are now predominantly being used to deliver ransomware to unsuspecting victims. The spike in ransomware emails highlights how important it is to conduct anti-phishing training and to use anti-spam solutions to prevent the malicious file-encrypting software from being delivered to employee’s inboxes.
Spike in Ransomware Emails as Criminals Seek Easy Cash
Ransomware has been around for about a decade, yet it has not been favored by cybercriminals until recently. Throughout 2015, under 10% of phishing emails were being used to transmit ransomware. However, in December there was a major spike in ransomware emails, which accounted for 56% of all phishing emails in December. The upward trend has continued in 2016 and by March, 93% of phishing emails contained ransomware – or were used to infect users by directing them to malicious websites where drive-by downloads of the malicious software occurred.
Spam email volume has been in general decline, in no small part to the shutting down of major botnets in recent years. However, that does not mean that the threat of cyberattacks via email can be ignored. In fact, PhishMe’s figures show there has been a surge in the number of phishing emails being sent. In the first quarter of 2016, the number of detected phishing emails soared to 6.3 million, which represents a 789% increase from the volume captured in the last quarter of 2015.
Ransomware is increasingly being used by cybercriminals for a number of reasons. Ransomware is now easy to obtain and send out. Many ransomware authors offer ransomware-as-a-service to any criminal looking to make a quick buck. Not only can the ransomware be hired for next to nothing, instructions are supplied on how to use it and criminals are allowed to set their own ransoms and timescales for payment. All they need to do is pay a percentage of the ransoms they obtain to the authors.
What makes the use of ransomware even more attractive is the speed at which criminals can get paid. Time limits for paying ransoms are usually very short. Demands for payment within 48 hours are not uncommon. While phishing emails have commonly been used to obtain credit card details from victims, which then need to be sold on, criminals can run a ransomware campaign and rake in Bitcoin payments in just a few days.
The ransoms being demanded are also relatively low. This means that many individuals can afford to pay the ransom to obtain the decryption keys to unlock their files, and businesses are also likely to pay. The cost of recovering data and restoring systems, together with the lost revenue from the time that computer systems are down, is often less than the ransom being demanded.
Ransomware Is Becoming Much More Sophisticated
The latest forms of ransomware now being used – Locky, CryptXXX, TeslaCrypt, and Samas (Samsam) – are capable of spreading laterally. Not only can the ransomware infect files on a single computer, other networked computers can also be infected, as can network drives, servers, portable storage devices, and backup drives. Some forms are also capable of deleting Windows shadow copies and preventing the restoration of files from backups.
All that the criminals need is for one business computer to be infected in order to encrypt files throughout the network. That means only one end user needs to be fooled into opening an infected attachment or visiting a malicious webpage.
Ransomware emails often contain personal information to increase the likelihood of an individual clicking a malicious link or opening an infected attachment. Word files are now commonly being used to infect users. Embedded macros contain code that downloads the malicious payload.
The malicious software is sent out in spear phishing campaigns targeting one or two users in a company, such as accounts and billing department executives. Personal information is often used in the emails – names, addresses, and job titles for example – to increase the likelihood of attachments being opened and links being clicked.
As criminals get better at crafting phishing emails and the ransomware becomes more sophisticated, it is more important than ever to use anti-spam solutions such as SpamTitan to trap ransomware emails and prevent them from being delivered. SpamTitan traps 99.9% of spam emails, helping organizations protect their networks from ransomware attacks.
by titanadmin | May 26, 2016 | Email Scams, Phishing & Email Spam, Spam News |
With 1.65 billion active Facebook accounts, the social media network is a big target for scammers, so it is no surprise that there is a new Facebook phishing scam currently doing the rounds. If the spammers behind the latest attacks can get even a tiny percentage of users to fall for the scam they could be in for a very big payday.
Latest Facebook Phishing Scam Warns of Violation of Terms of Service
The latest Facebook phishing scam threatens account holders by telling them that their accounts will be closed due to a violation of Facebook’s terms of service. The email claims that the account owner has been reported for irregularities of content and that action must be taken to correct the issue of the account will be permanently closed.
The message contains an ow.ly shortlink that users must click to verify that they are the actual owner of the account. The link contains the works “Verify” and “Facebook,” which may fool some message recipients into thinking the message is genuine.
The link included in the email is fake of course. It directs the victim to a phishing website where they are asked to supply their login credentials. If account holders are fooled into clicking the link they are likely to proceed and enter in their account login and password, which will not grant access to Facebook to remove the offending violations. It will simply give those credentials to the attackers. Victims are also asked to supply their date of birth and a security question.
Since many people often use the same passwords for multiple social media accounts, email accounts, and online banking, the potential losses could be considerable. Worse still, many individuals use the same passwords for their private accounts as they do for their work accounts. The fallout from this single scam could therefore be considerable.
With the login and password, the attackers could abuse the account and use it to send phishing messages to all of the account holder’s friends. However, the latest scam does not stop there. After supplying these details, the second phase of the scam starts. The victim is directed to a new page where they are asked for their credit card details to confirm their identity. If supplied, the details would be used to make purchases in the victim’s name
This latest Facebook phishing scam is fairly easy to spot as it contains many tell-tale signs that the notification is not real. The message starts with “Dear Customer” for a start. It would be reasonable to assume that Facebook would know the account holder’s name and would address the email to them personally. Not that Facebook sends out email notifications such as this, although many users would be unaware of that. The message also uses poor grammar, and an ow.ly link rather than a facebook.com hyperlink.
Suspected Page Forgery Facebook Scam Email Targets Business Users
Another version of this scam uses the same format as Facebook notifications sent to account holders via email. This email is harder to identify as a Facebook phishing scam. The link supplied appears to be a genuine Facebook link and the address supplied in the email also appear to be genuine. Correct English is used and the email has been very carefully crafted.
Clicking the link will take the user to a webpage that uses the Facebook logo and color scheme. The page explains there has been a violation of Facebook’s Terms of Service and that an unacceptable offer has been made using Facebook’s offer creation tool. Users are asked to secure their account if this is a mistake. To secure the account users must enter their username and password, and set a new security question. As with the other version, the account details will be used to hijack the account.
All Facebook users – businesses and individuals – should be particularly wary about Facebook emails and be wary of scams. If any Facebook messages are received, the account should be checked by logging in via the browser or using the Facebook App, never using the link supplied in the email. If there is a problem with the account, users will be informed of this when they login.
by titanadmin | May 20, 2016 | Email Scams, Industry News, Phishing & Email Spam, Spam Advice, Spam News |
According to a recent report on spam email from anti-virus software developer Kaspersky Lab, the decline in spam email over the past few years appears to have reversed, with the first quarter of 2016 seeing a major increase in malicious spam email volume.
Major Increase in Malicious Spam Email Volume Reported by Kaspersky Lab
Over the past few years there has been a decline in the number of spam emails, as cybercriminals have sought other ways to deliver malware and defraud computer users. In 2015, the volume of spam emails being sent fell to a 12-year low. Spam email volume fell below 50% for the first time since 2003.
In June 2015, the volume of spam emails dropped to 49.7% and in July 2015 the figures fell further still to 46.4%, according to anti-virus software developer Symantec. The decline was attributed to the taking down of major botnets responsible for sending spam emails in the billions.
Malicious spam email volume has remained fairly constant during 2015. Between 3 million and 6 million malicious spam emails were detected by Kaspersky Lab throughout 2015; however, toward the end of the year, malicious spam email volume increased. That trend has continued in 2016.
Kaspersky Lab figures show that spam email messages containing malicious attachments – malware, ransomware, malicious macros, and JavaScript – started to increase in December 2015. That rise has continued, and in March 2016 malicious spam email volume had risen to four times the level seen in 2015. In March, 2016, Kaspersky Lab detected 22,890,956 malicious spam emails. Spam email volume as a whole increased over the quarter, rising to an average of 56.92% for the first three months of 2016.
Image source: Kasperky Lab
Wide Range of Malicious Files Being Sent in Spam Email
While it was common for virus-loaded executable files to be sent as email attachments, these are now commonly caught by email filters and are marked as spam. However, spammers have been developing new methods of getting past traditional webmail spam filters. The spam emails intercepted by Kaspersky Lab now contained a wide variety of malicious files.
One of the most common methods now used by spammers is to send office documents infected with malicious macros. Microsoft Word files with the extension DOC and DOCX are commonly used, as are rich text format files RTF, Adobe PDF files, and Microsoft Excel spreadsheets with the extensions XLS and XLSX.
These file formats are commonly opened as many end users are less suspicious of office documents than they are about ZIP, RAR, and EXE files. Most office workers would know not to open a EXE file that was emailed to them by a stranger, yet an office document – a file format they use on a daily basis – is less likely to arouse suspicion.
Instead of the emails containing the actual malware, virus, or ransomware payload, they contain Trojan downloaders that download JS scripts. Those scripts then perform the final stage of infection and download the actual malware or ransomware. This method of attack is used to bypass anti-virus protections.
Web Filters and Email Spam Filters Should be Used to Reduce the Risk of a Malware Infection
There has been an increase in drive-by downloads in recent years as attackers have lured victims to websites containing exploit kits that probe for vulnerabilities in browsers and browser plugins. Visitors are redirected to these malicious websites when visiting compromised webpages, via malvertising, and malicious social media posts. While drive-by downloads are still a major threat, the use of web filters and anti-virus software browser add-ons are blocking these malware downloads and malicious websites.
Email is still a highly effective way of getting past security defenses and getting end users to install malware on their devices. Carefully crafted emails that include unique text increase the likelihood of the scammers getting users to open malicious attachments. Oftentimes, the messages include personal information about the recipient such as their name or address. This has helped the spammers to get the victims to take the desired action and run malicious macros and install malware.
It may be too early to tell whether spam email volume has only temporarily spiked or if there is a reversal in the decline of spam, but organizations and individuals should remain vigilant. The increase in malicious spam email volume should not be ignored.
Staff members should receive regular training on how to identify malicious email messages and phishing scams. It is also a wise precaution to use a robust spam filter such as SpamTitan. SpamTitan blocks 99.97% of malicious spam email messages, dramatically reducing the probability of malware, ransomware, adware, and spyware being installed.
by titanadmin | May 12, 2016 | Email Scams, Phishing & Email Spam, Spam Advice, Spam News |
Scammers are constantly coming up with crafty ways to fool computer users into revealing login credentials and installing malware, with the latest speeding ticket email scam being used for the latter. Emails are being sent to individuals claiming they have been caught driving too fast and are sent a link to click to pay their speeding ticket.
If the targeted individual clicks on the link contained in the spam email they will be directed to a malicious website that will download malware onto their computer.
This particular scam has been used to target drivers in Philadelphia. While the majority of spam emails are sent out randomly in the millions in the hope of fooling some individuals into clicking on malicious links, this particular campaign is anything but random. Individuals are being targeted that are known to have exceed the speed limit.
Not only have the attackers obtained the email addresses of their targets, they have also send details of where the individual exceeded the speed limit. So how is this possible?
This particular speeding ticket email scam is understood to have been made possible by the attackers hacking a Smartphone app that has access to the GPS on the phone. The attackers use location data and the phones GPS to determine which individuals have exceeded the speed limit. They are then sent a speeding ticket scam email telling them to click on a link where they can see details of their vehicle license plate in the location where the infraction took place. They are also informed of the speed limit in that location together with speed that the individual was travelling. The speeding driver is told he or she has 5 days to pay the citation.
While this speeding ticket email scam could easily be used by the attackers to obtain credit card details or phish for other information, it appears to only be used to install malware. Clicking on the link in the email to view license plate details does not actually reveal the image. It silently installs malware.
The police department in Tredyffrin, PA, where drivers were targeted with this speeding ticket email scam, has not cited callers for their speeding violations when they have called to query the fine, even when they have confessed to speeding over the phone.
How to Protect Yourself Against Email Scams
This speeding ticket email scam is particularly convincing as it uses real data to fool users into clicking on the malicious link. Many spam email campaigns now use personal information – such as real names and addresses – to fool targets into opening infected email attachments or clicking on malicious links. This type of targeted spear phishing email is now all too common.
To protect against attacks such as this, there are a number of steps that should be taken.
- If contacted by email and asked to click a link, pay a fine, or open an attachment, assume it is a scam. Try to contact the individual or company to confirm, but do not use the contact information in the email. Perform a search on Google to obtain the correct telephone number to call.
- Carefully check the sender’s email. Does it look like it is genuine?
- Never open email attachments from someone you do not know
- If you receive an email offering you a prize or refund, stay safe and delete the email
- Ensure that anti-virus software is installed on your computer and is up to date.
by titanadmin | May 9, 2016 | Email Scams, Internet Security, Phishing & Email Spam |
File-encrypting ransomware is now one of the main UK cybersecurity threats. Rather than stealing sensitive corporate data, criminals have taken to locking it with powerful encryption to prevent businesses from performing day to day functions. Without access to data, business often grinds to a halt.
Ransomware is nothing new, but over the past few years it has become much more popular with cybercriminals who are increasingly targeting businesses. If criminals can succeed in breaching businesses’ security defenses and locking critical files, a ransom can be demanded in order to supply security keys to unlock the encryption. If no viable backup copy exists, businesses may be left with no alternative but to give in to attackers’ demands. Those demands include sizable payments in Bitcoin – A virtually anonymous currency.
Ransomware attacks in the United States have attracted the headlines, but across the pond, ransomware attacks on UK businesses have also been increasing. According to the latest research from ESET, ransomware is now one of the main UK cybersecurity threats accounting for more than a quarter of threats. In the week of April 19 to 26, 26.16% of threats involved ransomware.
How to Block Ransomware Infections
Unfortunately, there is no single method of blocking ransomware infections that is 100% effective, although by using a multi-layered approach, small to medium-sized businesses can greatly reduce the probability of ransomware being installed on their computers and networks.
Ransomware is installed via a number of different methods, although one of the most common methods of ransomware delivery is spam email. Spam email is used to send out malicious attachments that install malware, which in turn installs ransomware on computers. One of the most common methods of infection is Word documents containing malicious macros.
Attackers also use emails containing malicious links. End users are enticed to click those links using social engineering techniques. One click is often all that is required to install ransomware. While it is possible to train employees to be more security aware, all it takes is for one member of staff to install malware for a network to be encrypted. The latest strains of ransomware are capable of encrypting files on single computers, connected USB drives, and network drives. It is important to provide staff training, but a software solution should also be used to block spam emails and prevent them from being delivered.
SpamTitan can keep an organization well protected from malware and ransomware infections. SpamTitan uses two leading anti-virus engines – Bitdefender and ClamAV – to block the vast majority of spam email. SpamTitan detects and blocks 99.98% of spam email, which prevents end users’ spam and phishing email detection skills from being put to the test.
SpamTitan blocks malicious emails, infected email attachments, and links to phishing websites and sites where drive-by downloads of malware take place. This single software solution can help organization mitigate the risk from many of the main UK cybersecurity threats.
If you want to block ransomware and malware and reduce the time your employees spend sifting through spam email, contact the sales team today for further information or sign up for a free SpamTitan trial.
by titanadmin | Apr 29, 2016 | Email Scams, Phishing & Email Spam, Spam Advice, Spam News |
Businesses have been put on alert following the discovery of a new personalized phishing scam that attempts to trick users into installing malware on their company’s computers. These new personalized phishing scam emails are primarily being used to spread CryptoWall ransomware, although that is far from the only payload delivered.
New Personalized Phishing Scam Delivers Wide Range of Malware
The new scam is also being used to deliver the Arsnif/RecoLoad POS reconnaissance Trojan to organizations in the retail and hospitality industries, as well as the Ursnif ISFB banking Trojan.
The current attack does not target all employees. Instead it is used to try to install malware on the computers of users with elevated network privileges such as senior executives, CFO’s, senior vice presidents, CEO’s, heads of finance, and company directors. These individuals not only have access to a far greater range of data, they are also likely to have access to corporate bank accounts.
If the payload is delivered it can result in POS systems being infected, access to bank accounts being gained, as well as widespread data encryption with ransomware. Once single email could cause a considerable amount of damage. The emails are currently being used to target organizations in the financial services, although the retail, manufacturing, healthcare, education, business services, technology, insurance, and energy sectors have also received large volumes of these emails.
What makes this particular phishing campaign stand out is the fact that the emails have not been delivered to random individuals. Many spammers send out phishing emails in the millions in the hope that some individuals will respond. However, this is a personalized phishing scam targeting specific individuals. Those individuals have been researched and the emails include data specific to the target.
Each email refers to the recipient by name and includes their job title, address, and phone number in the body of the email. The subject is specific, the email crafted for a particular industry, and the attached files and links have been named to make them appear genuine. The emails have also been well written and do not contain the spelling and grammar mistakes typical of spam email.
A personalized phishing scam such as this is not usually conducted on such a large scale. Spear phishing emails are usually send to just a handful of individuals, but this personalized phishing scam is being sent to many thousands of people, in particular those in the Unites States, United Kingdom, and Australia.
The data used in the email body could have been harvested from a social media site such as LinkedIn, although the scale of the attack suggests data has been obtained from elsewhere, such as a previous cyberattack on another company such as a supplier or an Internet site. Companies that do not use a robust spam filter such as SpamTitan are particularly at risk.
by titanadmin | Apr 22, 2016 | Email Scams, Phishing & Email Spam, Spam News, Spam Software |
Eastern European hackers may only have had access to GozNym banking malware for a few days, but they have already used the malicious software to make fraudulent bank transfers from more than two dozen bank accounts. The new malware is primarily being used to target banks and credit unions, although the attackers have also used the malware to attack e-commerce platforms. 22 attacks have been conducted on financial institutions in the United States with a further 2 attacks in Canada. So far the attackers behind the GozNym banking malware have managed to steal at least $4 million from U.S and Canadian banks.
GozNym Banking Malware Combines Gozi ISFB with Nymaim Source Code
As the name suggests, GozNym banking malware was developed by combining two different malware strains – Nymaim and Gozi ISFB.
IBMs X-Force Research team believe the new malware is the work of the team behind Nymaim malware, as the source code of Nymaim is understood to be only held by the original developers of the malware. The source code for Gozi ISFB malware has previously been leaked on two occasions. X-Force analysts think the Nymaim malware developers obtained that source code and used the best parts to form the new hybrid Trojan.
Nymaim malware has previously been used almost exclusively as a method of ransomware delivery, although the group behind the malware started using it as a banking Trojan late last year. Nymaim malware is a two stage malware dropper that is loaded onto computers using an exploit kit.
Links to a website containing the Blackhole Exploit Kit are sent via spam email. Once Nymaim has been loaded onto a computer, the second payload is deployed. In the case of GozNym banking malware the second stage is the running of Gozi ISFB code.
GozNym banking malware is stealthy and persistent. The malware remains dormant on a computer until the user logs into their bank account. When account details are entered, GozNym records the login credentials and silently sends them to the attackers’ command and control server. If GozNym banking malware is installed, the user will be unaware that their banking sessions have been compromised.
IBM recommends using adaptive malware detection solutions to reduce the risk of an attack. Anti-spam solutions such as SpamTitan can prevent emails containing the malicious links from being delivered, while WebTItan web filtering solutions can be used to block websites containing malicious code and exploit kits.
With new malware constantly being developed – around 1,000,000 new malware samples are now being released every day according to Symantec – organizations now need to implement sophisticated multi-layered defenses to protect their networks from malware infections.
by titanadmin | Apr 15, 2016 | Email Scams, Industry News, Phishing & Email Spam, Spam News |
Over the past three years business email compromise scams have been conducted with increasing regularity. However, over the past year the number of business email compromise scams reported to the Federal Bureau of Investigation (FBI) have increased dramatically.
Since January 2015, the FBI reports there has been a 270% increase in BEC attacks. FBI figures suggest the total losses from business email compromise scams since October 2013 has risen to $2.3 billion. Reports of successful BEC scams have been sent to the FBI from over 79 different countries around the world, which have affected more than 17,642 businesses.
Business email compromise scams involve the attacker gaining access to a corporate email account, such as that of the CEO, and requesting a bank transfer be made to their account. An email is sent from the CEO’s account to an accounts department employee, and all too often the transfer is made without question.
Unfortunately for U.S Businesses, BEC attacks are likely to increase as more cybercriminals get in on the act. Security experts have warned that the situation is likely to get a lot worse before it gets better. With the average fraudulent bank transfer between $25,000 and $75,000 and considerable potential to obtain much higher sums, criminals are more than willing to conduct the attacks.
A recent report from Dell SecureWorks indicates some hackers are selling their services on underground marketplaces and are offering access to corporate email accounts for just $250. Since cybercriminals could buy access to corporate email accounts, even relatively unskilled criminals could pull off a BEC scam and potentially have a million dollar+ payday. A number of large corporations have been fooled by these scams and have recorded losses of well over $1 million.
Business Email Compromise Scams Can Be Highly Convincing
BEC scams are convincing because even with security training, staff members tend to assume attacks will come from outside their organization. Employees are suspicious about emails that request the disclosure of login credentials, and a request to make a bank transfer that has not come from within an organization is likely to be immediately flagged as a scam.
However, when the CEO sends an email to a member of the accounts department requesting a bank transfer, many employees would not think to question the request. The person arranging the transfer would be unlikely to call the CEO to confirm payment. The transfer may go unnoticed for a number of days, by which time the funds would have been withdrawn from the attackers account and would be impossible to recover.
To conduct this type of attack the attacker would need to gain access to the email account of the CEO or an executive in the company who usually sends bank transfer requests to the accounts department. Once access has been gained, the attacker can read emails and learn the terminology typically used by that member of staff.
An email can then be written in the same language used by that individual. This ensures that the email does not rouse suspicions. Attackers research the transfer requests that are typically made and set the dollar amounts accordingly.
Since the account transfers are made to bank accounts outside the United States, the companies most frequently targeted are those that often make International payments. To the targeted accounts department employee, the request would seem perfectly normal.
How to Reduce the Risk of Employees Falling for BEC Scams
There are a number of ways that organizations can reduce the risk of employees falling for business email compromise scams. SpamTitan could not block a request sent from a compromised email account, but oftentimes attackers spoof email addresses. They purchase a domain that looks very similar to the targeted company, often transposing two letters. Oftentimes a domain is purchased replacing a letter “i” or an “L” with a “1”. If the email address of the sender is not carefully checked, this could well go unnoticed. SpamTitan can be configured to automatically block these spoofed email addresses to prevent these emails from being delivered.
To prevent employees from falling for business email compromise scams sent from compromised email accounts, policies and procedures should be introduced that require all account transfers to be verified by two individuals. Large transfers should also, where possible, be confirmed by some means other than email. A quick call to sender of the email for instance.
Organizations that choose to do nothing could regret failing to take precautions. Take the Austrian Airline parts company FACC for example. It reportedly lost approximately $55 million to such a scam.
by titanadmin | Apr 8, 2016 | Internet Security, Phishing & Email Spam, Website Filtering |
Vulnerabilities in Adobe Flash Player are discovered with such regularity that news of another raises few eyebrows, but the latest critical vulnerability – discovered in Adobe Flash Player 21.0.0.197 and earlier versions – is a cause for concern. It is already being exploited by hackers and is being used to infect users with ransomware.
Any device that is running Adobe Flash Player 21.0.0.197 (or earlier) is at risk of the vulnerability being exploited and malicious file-encrypting software being installed. The latest vulnerability can be used to attack Windows, Macs, Linux systems and Chromebooks, according to ProofPoint, although Adobe reports that the vulnerability only affects Windows 10 and earlier versions running the vulnerable versions.
Flash vulnerabilities are usually exploited by visiting malicious websites or webpages that have been compromised and infected with exploit kits. Those exploit kits probe for a range of weaknesses, such vulnerabilities in Adobe Flash Player, and exploit them to download malware or ransomware to the user’s device.
These drive-by attacks occur without users’ knowledge, as the downloaded file is not displayed in the browser and is not saved to the download folder. It is also difficult to determine whether a website has been compromised or is malicious in nature without software solutions that analyze the website content.
Vulnerabilities in Adobe Flash Player Exploited to Deliver Cerber and Locky Ransomware
The latest attack uses the Magnitude exploit kit. The fact that it is Magnitude suggests the latest ransomware attacks are the work of an individual cybercriminal gang. That gang has acted quickly to include the latest Flash vulnerability into Magnitude.
According to Trend Micro, the vulnerability is being used to deliver Locky ransomware – the malicious file-encrypting software that has been used to attack hospitals in the United States in recent weeks. Locky was reportedly the ransomware used in the attack on Hollywood Presbyterian Medical Center in February. That infection cost the healthcare organization $17,000 to remove, not to mention the cost of attempting to remove the infection and restore backup files prior to the ransom being paid.
ProofPoint suggests the vulnerability is being used to deliver Cerber ransomware. Cerber is a new ransomware that has was released in the past month. It can be used to encrypt files on all Windows versions, although not those in Russian.
Cerber and Locky are being downloaded via malicious websites, although these are typically not visited by the vast majority of Internet users. In order to get traffic to these sites the attackers are using spam email containing malicious attachments.
In contrast to many malicious spam emails that install malware using executable files and zip files, the attackers are using Word documents containing malicious macros. The macros do not download the ransomware directly, instead they direct the victim, via a number of redirects, to a malicious site where the drive-by download takes place.
The vulnerability, named as CVE-2016-1019, will crash Adobe Flash when it is exploited. Adobe reports that the vulnerability exists in 21.0.0.197. Trend Micro says the exploit will not work on versions 21.0.0.197 and 21.0.0.182, only on Flash 20.0.0.306 and earlier versions due to mitigations put in place by Adobe.
ProofPoint’s Ryan Kalember said that the exploit has been engineered to only work on earlier versions of Flash and that attacks have been degraded to evade detection. All versions of Flash could potentially be used for the attack should the criminals behind the Magnitude exploit kit so wish.
Of course, this is just one of many vulnerabilities in Adobe Flash Player that can be exploited and used to deliver ransomware or other forms of malware. To prevent attacks, sysadmins should ensure that all devices are updated to the latest version of the software. Adobe said it was releasing a security update to address the vulnerability on April 7, 2016.
Vulnerabilities in Adobe Flash Player are addressed with updates, although there are two software solutions that can help to protect users from attack. Anti-spam solutions such as SpamTitan can be used to prevent spam email from being delivered, reducing the risk of end users opening Word documents infected with malicious macros.
WebTitan products tackle these attacks by blocking malicious websites, preventing users from visiting sites where drive-by downloads take place. There is usually a wait while vulnerabilities in Adobe Flash Player are addressed, and these two solutions can help keep devices malware free until updates are applied.
by titanadmin | Mar 31, 2016 | Industry News, Internet Security, Network Security |
The past two months have seen a number of healthcare organizations attacked by cybercriminals; however, the MedStar Health ransomware attack discovered on Monday this week must rank as one of the most severe.
The MedStar Health ransomware attack is the latest in a string of attacks on U.S. healthcare organizations, as hackers up the ante and go for much bigger targets where the potential rewards are greater. It would appear that the 10-hospital health system will not need to pay a ransom to regain access to its data, but for three days MedStar Health has been forced to work without access to some of its computer systems after they were shut down to prevent the spread of the infection.
MedStar Health Ransomware Attack Affects 10 Hospitals and More than 250 Outpatient Facilities
MedStar Health is a large U.S health system operating more than 250 outpatient facilities and ten hospitals in the Washington D.C., area. On Monday morning, a virus was discovered to have been installed. The infection triggered emergency IT procedures and rapid action taken to limit the spread of the virus. Three clinical information systems were shut down, including email and the electronic health record system used to record and view patient data.
Without access to email and patient data, services at the hospital were slowed although business continued as close to normal as possible. No facilities closed their door to patients. However, in the 48 hours since the virus was discovered, IT security teams have been working around the clock to bring systems back online. Yesterday, MedStar Health reported that systems were being brought back online with enhanced functionality added bit by bit.
MedStar Health has kept the media and patients notified of progress via social media. The health system reported that “The malicious malware attack has created many inconveniences and operational challenges for our patients and associates.”
While no information was initially released on the exact nature of the computer virus that was discovered to have infiltrated its systems, a number of sources indicate the malicious software was ransomware. It has since emerged that the MedStar Health ransomware attack involved a ransomware from the Samsam family. The ransomware is also known as MSIL and Samas. The attack occurred at the Union Memorial Hospital in Baltimore.
Some computer users were presented with a message demanding a ransom to unlock files. The Baltimore Sun reported that the MedStar Health ransomware attack saw attackers demand a ransom of 45 Bitcoin (approximately $18,500) to unlock all 18 computers that were infected, with an offer to unlock one machine for 3 Bitcoin (approximately $1233).
FBI Issued Warning About Samsam Ransomware on March 25
The FBI reached out to businesses for assistance dealing with the latest ransomware threat from Samsam. While many ransomware infections use email as the vector, Samsam is installed via a tool called JexBoss. JexBoss is used to discover a vulnerability that exists in JBOSS systems. This attack is not conducted using phishing or website exploit kits, instead it works by compromising servers and spreading the infection laterally.
The vulnerability exploited is in the default configuration of the Boss Management Console (JMX) which is used to control JBoss application servers. In its default state, JMX allows unsecured access from external parties and this is used to gain shell access to install the ransomware.
Once a web application server has been infected, the ransomware does not communicate with a command and control server, but will spread laterally and to infect Windows machines, hence the need to shut down systems. The MedStar Health ransomware attack could have been much more severe had rapid action not been taken.
This attack highlights just how important it is to ensure that all systems are patched and default software configurations are changed. Other attacks recently reported by healthcare organizations in the United States have involved Locky ransomware, which is spread via exploit kits on compromised websites and via email spam. Healthcare organizations can protect against those attacks by using web filtering and anti-spam solutions. However, it is also essential to train staff never to open email attachments from unknown sources.
by titanadmin | Mar 25, 2016 | Email Scams, Phishing & Email Spam, Spam News |
It is getting harder for cybercriminals to deliver malware via email, so attack methods have had to become more sophisticated; the latest attempt uses a malicious PNG file to deliver a banking Trojan.
Simply sending malware as an attachment in a spam email is certain to result in some unsuspecting users’ computers being infected, but cybercriminals are now having to use more advanced techniques to evade detection and get past spam filters and antivirus software. The latest attack method is an example of how attackers are using much more sophisticated methods to evading detection.
Malicious PNG File Used to Infect Windows, OS X, and Linux Machines
A new campaign has been discovered by SecureList which is being used, at present, to attack computers in Brazil. However, while the majority of victims are located in Brazil, the malware is also being used to attack users in Spain, Portugal, the United States and beyond.
To evade detection, the attackers have encrypted a malicious payload in a malicious PNG file – a common image format many people do not usually associate with malware.
The image file is not attached to an email and sent in a spam message, instead the initial attack takes place using a PDF file containing a malicious link. The PDF file is sent out in spam emails which use social engineering techniques to fool users into opening the attachment. The PDF file does not contain any malicious code, instead it uses a link to infect users. Clicking the link in the PDF file initiates the infection process.
The link is used to get users to download a malicious Java JAR file, which in turn downloads an infected ZIP file. The zip file contains a number of other files, including a malicious PNG file, or file with a PNG header. Researchers analyzed the binary file and determined that the PNG file size was much larger than it should be for the size of the image.
Further analysis showed how the malicious PNG file was loaded to the memory – using a technique called RunPE which is used by hackers to hide malicious code behind a legitimate process. In this case that process is iexplore.exe.
The malicious PNG file cannot infect a user on its own, as a launcher is required to decrypt the contents of the file. The attackers send the PDF file to start the infection process. Since the zip file contains the PDF extension, users downloading the file are likely to double click to open, thus infecting their systems. Since the malicious code in the PDF file is encrypted, it is not picked up by antivirus software. However, SecureList points out that the malicious files used in this attack are picked up by Kaspersky Lab products.
by titanadmin | Mar 16, 2016 | Email Scams, Phishing & Email Spam, Spam News |
A new wave of spam email has prompted antivirus companies to issue a warning about emails infected with Nemucod malware. The emails are rapidly spreading around the globe, with Japan currently the worst hit; however, the prevalence of infected spam email is also particularly high in Europe, Australia, Canada, and the United States.
Nemucod Malware Used to Infect Devices with Teslacrypt and Locky Ransomware
Nemucod malware is a Trojan downloader that is used to install a payload of ransomware. Currently Nemucod malware is being spread via spam email and is being used to download Locky and Teslacrypt ransomware onto the devices of anyone who opens the infected email attachments.
Nemucod malware (JSTrojan/Downloader.Nemucod) is a JavaScript downloader. The malware is being distributed as a ZIP file and will run when opened and will download a payload of file-locking ransomware. The ransomware will lock numerous files and a ransom will be demanded by the attackers. Only if that ransom is paid will a security key be supplied to unlock data.
In contrast to many malware-infected emails which contain numerous grammatical and spelling mistakes, the emails being used to spread this nasty malware are well written and convincing. The emails claim the attachment is an invoice or an official document such as a notice requiring the target to appear in court.
As we have previously reported, Teslacrypt and Locky ransomware are particularly nasty ransomware. On download they search the user’s computer for a wide variety of file types and lock all of those files with powerful encryption. They will also search for files on attached portable storage devices, virtual devices, and network drives. Locky is also capable of removing volume shadow copies (VSS) making it impossible for infected users to restore their devices to a point before the ransomware infection.
Documents, images, spreadsheets, system files, and data backups are all encrypted. Locky has been programmed to encrypts hundreds of file types. Fortunately, there are a number of steps that can be taken to prevent malware and ransomware infections.
How to Prevent a Ransomware Infection
Steps can be taken to reduce the risk of ransomware being installed, but even the best defenses can be breached. It is therefore also essential to ensure that all critical data files are backed up regularly. If a daily backup is performed, at worst, an organization should only lose a maximum of 24 hours of data.
It is essential that once backups are made, the drive uses to store the backup files is disconnected. Some ransomware variants are capable of scanning network drives and can encrypt backup files on connected backup devices.
Simply receiving a malicious spam email that has been infected with malware will not result in a device being infected. A device will only be infected if an end user opens the infected attachment.
The best way to defend against ransomware is never to open email attachments that have been sent from unknown individuals. While this is straightforward for individual users, for businesses it is harder to ensure that no member of staff will be fooled into opening an infected email attachment.
It is therefore essential to provide all members of staff with security training to ensure they are aware about best practices to adopt to reduce the risk of installing ransomware. However, all it takes is for one member of staff to open a malicious email attachment for the network to be infected. For peace of mind, a robust spam filtering solution for businesses should be implemented. SpamTitan blocks 99.9% of all spam email, drastically reducing the risk of ransomware and other malicious emails from being delivered to end users.
by titanadmin | Mar 10, 2016 | Email Scams, Network Security, Phishing & Email Spam, Spam News |
Locky ransomware may be a relatively new threat for IT security professionals to worry about, but it has not taken long for the malicious malware to make its mark. It has already claimed a number of high profile victims and is fast becoming one of the most prevalent forms of ransomware.
Early last month Hollywood Presbyterian Hospital in California experienced a ransomware attack that took some of its systems out of action for a week until a ransom demand of $17,000 was paid and the hospital’s EHR was decrypted. During that week, staff at the hospital were forced to record data on paper, were unable to check medical records, and X-Ray, CT scans and other medical imaging files were inaccessible. The hospital was not targeted, instead it was the victim of a random attack. That attack was linked to Locky ransomware.
Locky Ransomware Capable of Encrypting Files Stored on Network Drives
Locky ransomware infections occur via spam email messages and it appears that Hollywood Presbyterian hospital’s systems were infected via an email campaign. Locky ransomware is not delivered via spam email directly, instead infection occurs via a malicious Word macro.
When the macro is run, the malicious code saves a file to the disk and downloads the ransomware from a remote server. Upon download the malware searches for a range of file types located on the device on which it is saved, as well as searching portable drives, virtual devices, and network drives to which the computer is connected. Volume Snapshot Service (VSS) files are also removed, removing the option of restoring via Windows backup files.
Staff training on malicious file detection often covers common file types used to mask malicious software such as screensaver files (SCR), executables (EXE), and batch files (BAT). In the case of Locky ransomware, users are more likely to be fooled as infections occur as a result of Word document (DOC) macros. Any user who receives and opens an infected Word document will automatically download Locky to their computer if they have macros set to run automatically. Since users are instructed to enable macros upon opening the infected document, many may do so in order to read the contents of the file.
That is not the only way that Locky is spread. It is also being installed via a ZIP file, which when run, downloads a JavaScript installer that in turn downloads and runs the ransomware.
According to Trustwave SpiderLabs, 18% of the spam emails it had collected over the course of the past week were ransomware, and Locky is believed to comprise a large percentage of those emails. The ransomware is being delivered by the same botnet that was used to send out Dridex malware last year. While the mastermind behind the Dridex banking malware, Moldovan Andrey Ghinkul, has now been apprehended and extradited to the U.S, the botnet infrastructure is being used for this much simpler attack.
The attacks may be simpler but they are providing to be effective. According to Fortinet, over three million hits have been recorded from the Command and Control server used to communicate with Locky.
The infections are unlikely to end until the botnet is taken down. In the meantime, it is essential to exercise caution. While the ransomware does not attack Russian systems, all other users are at risk. Businesses in particular should take action to reduce risk, such as advising staff of the threat of infection via Word files and Zip files. Using a spam filtering solution such as SpamTitan to block malicious attachments is also strongly advisable to prevent malicious emails from being delivered to staff inboxes.
by titanadmin | Mar 4, 2016 | Email Scams, Phishing & Email Spam, Spam News |
A number of new tax season scams have been uncovered in recent weeks, with one in particular causing concern due to the sheer number of victims it has already claimed. Over the past three weeks, four healthcare providers in the United States have been added to the list of victims. The four healthcare providers have recently announced members of staff have fallen for a W-2 phishing scams and have emailed lists of employees to scammers. Names, Social Security numbers and details of employee earnings have been disclosed.
Healthcare Providers Targeted by New Tax Season Scams
Healthcare HR and payroll staff are being targeted by scammers attempting to gain access to the names, contact details, and Social Security numbers of hospital employees with a view to using the data to commit tax fraud. The latest tax season scams are convincing. The scammers find out the names of staff working in the HR and payroll departments who are likely to have access to employee W-2 forms. A spear phishing email is then sent to the employees requesting a list of W2 copies of employee wage and tax statements for the previous year. They are instructed to compile the lists and enter them in a spreadsheet or PDF and email them as soon as possible.
What makes the scams convincing, and employees likely to respond, is the requests appear to come from within the organization and appear to have been sent by either the CEO or a senior executive. The emails appear to have been sent from the correct email address of the CEO or executive, leading the employees to believe the requests are genuine.
The “From” email address is usually masked so that it appears genuine; although it is not. A reply to the email will be sent outside of the company to an email account being monitored by the scammers. In some cases, domains have been purchased that are very similar to those of the target organizations. Usually two letters have been transposed making the domains appear genuine. An email account is then set up with the same format as used by the company. A quick glance at the email address may not rouse any suspicion.
It may take days or weeks before these tax season scams are detected. By that time, fake tax returns are likely to have been filed in the names of the victims.
HR and payroll staff must be particularly vigilant at this time of year as tax season scams are rife. However, the rise in number of successful phishing attacks suggests that payroll and HR staff have not received refresher training on the dangers of phishing. With attacks still taking place, now is a good time to issue an email bulletin to all staff with access to employee data to warn them of the risk, and to advise them to exercise extreme caution and not send any employee data without checking and double checking the validity of the email request.
IRS Issues New Warning About W-2 Phishing Scams
At the start of February, the IRS issued a warning about the sharp rise in tax season scams this year. Just over a month into tax season and record number of phishing scams and tax season-related malware had been discovered. In January, 1,026 reports of tax-related incidents had been reported, which is an increase of 254 over the previous year.
The incidents continued to increase throughout February, with last year’s total of 1,361 already having been exceeded in the first two weeks of the month. The high volume of tax season scams reported in February prompted the IRS to issue another warning on February 29, with the W-2 phishing scams causing particular concern. So far this tax season, reported tax-related malware and phishing attacks have increased 400% year on year.
by titanadmin | Feb 23, 2016 | Email Scams, Phishing & Email Spam, Spam News |
Last week a healthcare provider had its electronic health record system locked by ransomware; now a Zika virus email scam has been uncovered, showing the depths that some hackers and cybercriminals will stoop to in order to make a quick buck.
The latest email scam takes advantage of the public interest in the Zika virus epidemic in Brazil. Since April last year, the number of reported cases of Zika fever has grown. Zika fever is caused by the transmission of the Zika virus by Aedes mosquitos. Zika fever produces similar symptoms to Dengue fever, although the symptoms are often milder.
Scientists have also been alerted to a rise in the number of cases of microcephaly reported in Brazil. Microcephaly is a birth defect resulting in babies being born with a smaller than average head as well as other poor pregnancy outcomes. The rise in microcephaly has been linked to the increase in cases of Zika virus.
While no concrete evidence has been uncovered to suggest that pregnant women contracting Zika are likely to give birth to babies with microcephaly, there is concern that Zika can cause the birth defect. The World Health Organization (WHO) reports the virus has now spread to 23 countries. People are naturally worried. Women in Brazil and Columbia have been told to avoid becoming pregnant and hold off having children, while the government in El Salvador has told women not to get pregnant until 2018.
A potentially global health issue such as Zika is naturally a worry for any woman looking to start a family, and understandably the latest news about the virus is likely to be read. Scammers have been quick to take advantage of the media interest, and a scam has been developed to take advantage and infect computers with malware
Zika Virus Email Scam Delivers JS.Downloader Malware
The Zika virus email scam is currently doing the rounds in Brazil and is being sent in Portuguese. The Zika virus email scam appears to have been sent from Saúde Curiosa (Curious Health), which is a legitimate health and wellness website in Brazil. The email contains an attachment infected with JS.Downloader. JS. Downloader is a malware that is used to download malicious malware to infected users’ devices.
The subject line of the email is “ZIKA VIRUS! ISSO MESMO, MATANDO COM ÁGUA!” which translates as Zika Virus! That’s Right, killing it with water!” The email tells the recipient to click on the link contained in the email to find out how to kill the mosquitos that carry the virus, although the email also contains a file attachment which the email recipient is urged to open. Doing so will install the malware onto the user’s device. The link directs the user to Dropbox with the same outcome.
Anyone receiving an unsolicited email with advice about the Zika virus, regardless of the language it is written in, should treat the email with suspicion. This is unlikely to be the only Zika virus email scam sent by cybercriminals this year. With the Olympics taking place in Brazil in the summer, criminals are likely to use topics such as the Zika virus to spread malware.
If you want information about Zika, check the WHO website. If you receive an Zika virus email, delete it and do not click on any links in the email or open any attachments.
by titanadmin | Feb 18, 2016 | Email Scams, Internet Security, Network Security, Phishing & Email Spam, Spam News, Spam Software |
Over the past 12 months, cybercriminals have used ransomware with increasing frequency to extort money out of businesses, leading some security experts to predict that healthcare ransomware infections would become a major problem in 2016.
Would cybercriminals stoop so low and attack the providers of critical medical care? The answer is yes. This week a U.S. hospital has taken the decision to pay a ransom to obtain the security keys necessary to unlock data that had been encrypted by ransomware. The attack does not appear to have been targeted, but the ransom still needed to be paid to unlock the hospital’s electronic medical record system.
Last year, Cryptowall infections were regularly reported that required individuals to pay a ransom of around $500 to get the security key to recover files. However, when businesses accidentally install ransomware the ransom demand is usually far higher. Cybercriminals can name their price and it is usually well in excess of $500.
Healthcare Ransomware Infection Results in Hospital Paying $16,664 to Unlock EHR
While businesses have been targeted by cybercriminal gangs and have had their critical data locked by ransomware, it is rare for healthcare providers to be attacked. The latest healthcare ransomware infection does not appear to have been targeted, instead a member of staff inadvertently installed malware which locked the hospital’s enterprise-wide electronic health record system (EHR): The system that houses patient health records and critical medical files.
The EHR of Southern California’s Hollywood Presbyterian Medical Center was locked on February 5, 2016., with physicians and other members of the hospital staff unable to access the EHR to view and log patient health information. An investigation into the IT issue was immediately launched and it soon became apparent that the database had been locked by ransomware.
No one wants to have to pay cybercriminals for security keys, and the hospital took steps to try to recover without having to give in to ransom demands. The Police and FBI were contacted and started an investigation. Computer experts were also brought in to help restore the computer system but all to no avail.
The news of the healthcare ransomware attack broke late last week, with early reports suggesting the hospital had received a ransom demand of 9,000 Bitcoin, or around $3.4 million. The EHR was taken out of action for more than a week while the hospital attempted to recover and unlock its files.
Eventually, the decision had to be taken to pay the ransom. While it may have been possible for patient health data to be restored from backups, the time it would take, the resources required to do that, and the disruption it would likely cause was not deemed to be worth it. Allen Stefanek, CEO of Hollywood Presbyterian Medical Center, took the decision to pay the ransom to obtain the security key to unlock the data.
In a statement posted on the company’s website he confirmed that the reports of a ransom demand of 9,000 Bitcoin were untrue. The attackers were asking for 40 Bitcoin, or $16,664, to release the security key to unlock the hospital’s data.
Stefanek said, “The quickest and most efficient way to restore our systems and administrative functions was to pay the ransom and obtain the decryption key. In the best interest of restoring normal operations, we did this.”
Fortunately, healthcare ransomware attacks are relatively rare, as many healthcare providers in the United States already have controls in place to reduce the likelihood of an attack being successful. Staff are trained to be vigilant and not to install software on healthcare devices or open suspicious email attachments. Many use a spam filter to quarantine suspect emails. The latter being an essential protection against healthcare ransomware attacks.
The Importance of a Robust Spam Filter to Prevent Healthcare Ransomware Attacks
A healthcare ransomware attack does not just have a financial impact; it has potential to cause actual harm to patients. The delivery of healthcare services is slowed as a result of the inability to access and share healthcare data, and not being able to view patient health records could delay the delivery of critical patient care or result in incorrect medications being prescribed. That could be a life or death matter. Preventing healthcare ransomware attacks is therefore essential. A technological solution should be employed for maximum protection.
TitanHQ’s SpamTitan software has been developed to keep businesses protected from malware and ransomware attacks. SpamTitan uses two anti-malware engines to maximize the probability of spam emails and malicious attachments being caught and prevented from being delivered to end user inboxes. SpamTitan catches 99.9% of Spam email and quarantines emails with suspicious attachments to prevent them from being delivered.
If you want to reduce the risk of a suffering a ransomware attack and having to pay cybercriminals to unlock critical data, using a robust, powerful anti-spam solution such as SpamTitan is the best way to protect computers and networks from attack. Along with staff training to improve understanding of healthcare ransomware and other malware, it is possible to prevent attacks from being successful.
For further information on SpamTitan anti-spam solutions, contact the TitanHQ team today:
US Sales +1 813 304 2544
UK/EU Sales +44 203 808 5467
IRL +353 91 54 55 00
Or email sales@spamtitan.com
by titanadmin | Feb 12, 2016 | Email Scams, Phishing & Email Spam, Spam News |
Virgin Media customers have been complaining about an increase in spam emails since September last year, with many targeted with spoofed emails; however, the Virgin Media spoofed emails are not the result of a data breach according to a statement recently issued by the ISP.
Virgin Media Spoofed Emails Not the Result of a Data Breach
Customers first started to receive spam and spoofed emails in September last year, shortly after Virgin Media moved from Google to its own platform. The problem appears to be affecting individuals with blueyonder and ntlworld email accounts.
The Virgin Media spoofed emails indicate the company has suffered a data breach and hackers are in possession of email accounts and email address books. Virgin Media has denied it has suffered a data breach, although the ISP has acknowledged that some its users are being targeted by spammers and that it is aware of a “spoofed email message problem.”
Virgin Media are claiming that the increase in email spam is a consequence of the change of platform. The ISP maintains its own spam filters are not as effective as those used by Google, hence the increase in email spam since the switch of platform.
While this is plausible and would explain the increase in email spam, it does not adequately explain the Virgin Media spoofed emails. Customers have reported that a number of their address book contacts have received spoofed messages which would appear to have been sent from their email accounts.
Some of the affected customers claim that the spoofing occurs in waves every 3 to 4 weeks. Emails are sent to five address book contacts at a time. Those emails contain a link to a malicious website which is used to download malware to the users’ computers. The victim is aware of the spoofing as they often receive bounce-backs from undeliverable messages.

Customers Blamed for Virgin Media Spoofed Emails
The lack of a reasonable answer and a solution to stop the Virgin Media spoofed emails from being sent has led a number of customers to take to social media sites to vent their spleens and share details of their experiences. A Facebook group has been set up for this purpose. Around 70 customers have come forward and shared their experiences on the Facebook group so far.
Customers complaining about the email spoofing to Virgin Media are being informed that the message storm problem is due to customers, not a data breach. Customers disagree, with many claiming the problem cannot be local. Many bounce backs are generated as the email addresses are out of date, whereas the address books on local computers are not. The problem is therefore with the email address books stored on Virgin Media servers.
Disgruntled customers unhappy with the response they have received from Virgin Media have now complained to the Information Commissioner’s Office, which is looking into the issue.
by titanadmin | Feb 5, 2016 | Email Scams, Spam News |
What are the penalties for spamming? A man from Indianapolis has just discovered the penalties for sending spam can be severe, having been recently sentenced to serve over 2 years in jail.
Indianapolis man discovers the penalties for spamming can be severe
Phillip Fleitz, 31, of Indianapolis was recently sentenced to 27 months in a federal penitentiary after violating the CAN-SPAM Act of 2003: A law introduced to make the spamming of cell phones and email accounts illegal. The law was introduced by George W. Bush to protect U.S. citizens from unwanted marketing messages and pornography. Under the CAN-SPAM Act of 2003, the penalties for spamming include lengthy jail terms and hefty fines.
US District Judge Maurice Cohill Jr. passed sentence in a Philadelphia court earlier this month. The judge said the spam campaign orchestrated by Fleitz was “sophisticated and serious,” and resulted in millions of spam messages being sent to U.S. citizens. Fleitz, along with two other individuals involved in the massive spamming campaign, were raking in between $2,000 and $3000 per week. They were paid for the clicks they managed to generate by sending users to marketing websites.
The marketing websites gathered contact details from visitors, a practice which is legal. What is not legal, and contravenes the CAN-SPAM Act of 2003, is using spam marketing to generate traffic to those websites.
Fleitz was the only individual from the trio to receive a jail term as he was the architect of the scheme. “It was his idea. He was the first to do it,” said prosecuting US attorney Jimmy Kitchen. Last year, Fleitz pled guilty to using a protected computer to relay or retransmit multiple commercial electronic mail messages with the intent to deceive or mislead recipients, with the sentence only just being passed.
Spammer arrested after Darkode website takedown
Flietz was arrested as part of an FBI investigation into Darkode, a website used by hackers and cybercriminals to market illegal computer skills. The taking down of the website resulted in 12 individuals being charged for computer crimes.
The two other individuals involved in the spam campaign, Naveed Ahmed, 27, wrote the program that allowed the scheme to operate. He received 2-years’ probation and was sentenced last year. Dewayne Watts, wrote the spam messages which were designed to fool users into responding. He received 2-months’ probation, including a period of 6 months of being confined to his house.
The spamming campaign was run via servers based in China between September 2011 and February 2013. Fleitz recruited Ahmed to write a computer program that enabled the spammers to send millions of spam text messages and emails to mobile phones and computers. Ahmed’s program mined cellphone numbers and matched them up with carriers. The messages written by Watts advised the recipients they had won gift cards that could be claimed by clicking the links contained in the messages.
The penalties for spamming under the CAN-SPAM Act of 2003 can be severe. While Fleitz only received 27 months in jail, he could potentially have been sentenced to a maximum of 60 months of jail time and fined up to $250,000. When determining the penalties for spamming, judges take prior history into consideration as well as the severity of the offences.
TitanHQ.fr a cet article en français.
FAQ
Who is in charge of enforcing the CAN-SPAM Act?
The CAN-SPAM Act is enforced primarily by the Federal Trade Commission, which can seek civil penalties of up to $16,000 per violation. In certain circumstances the Act is enforced by various other federal agencies such as the Federal Communications Commission, state attorneys general, and Internet Service Providers. There is no private right of action.
Who can I complain to about spam and phishing emails?
It depends on the nature of the email and whether or not you have responded to it. For example, complaints about emails advertising financial investments should be sent to the Securities and Exchange Commission, while those relating to miracle medical cures should be sent to the Food and Drug Administration. You will find the full list of who to complain to on the Department of Justice website.
Has the CAN-SPAM Act been updated since it was first enacted?
In 2017, the Federal Trade Commission sought public comment on the CAN-SPAM Act ahead of a review. After receiving 92 comments “overwhelmingly” in favor of keeping the rules as they are, in 2019 the Commission concluded the Act still benefits businesses and consumers without imposing substantial economic burdens on genuine email marketing and the rules were kept the same.
How can I prevent my business receiving spam and phishing emails?
Speak with us about our email filtering service which can detect up to 99.97% of spam emails and significantly reduce the likelihood of a phishing email being delivered. Our team will be happy to organization a no-obligation demonstration of our service in action and give you the opportunity to take advantage of a free trial in order to evaluate our service in your own environment.
by titanadmin | Jan 25, 2016 | Internet Security, Network Security, Spam News, Website Filtering |
Each January, the PwC Annual Global CEO Survey is published detailing the major perceived threats to corporate growth. This year the results of the survey show that CEOs are more worried about the cost of dealing with cyberthreats, and believe that they can actually have a major negative impact on corporate growth.
Cost of dealing with cyberthreats a major impediment to 2016 growth
The global survey probed 1,409 CEOs about their concerns about impediments to growth, with cyberthreats ranking as one of the top ten major problems. 61% of respondents said they were worried about cyberthreats and the effect they will have on growth this year.
Over-regulation and geopolitical uncertainty were considered to be more pressing concerns, being cited by 79% and 74% or respondents, while the availability of key skills was mentioned as a major threat to growth by 72% of CEOs. The cost of dealing with cyberthreats was ranked as the eighth biggest impediment to growth in 2016.
While 60% of CEOs believe there are more opportunities for growth than 3 years ago, 66% said there were now more threats to growth. 26% said they only saw more opportunities, while 32% saying they only saw more threats.
The cost of dealing with cyberthreats is considerable, although nowhere near as high of the cost of failing to deal with them. Last year the Ponemon Institute calculated the cost of cyberthreats and determined the cost to businesses is soaring, with the IBM sponsored study determining the average cost of dealing with security breaches had risen to $3.8 million.
Some of the large organizations included in the study suffered cybercrime losses as high as $65 million, with the cost of cyberthreats having risen by 23% over the course of the past two years.
The IBM Cost of Data Breach Study determined the cost per stolen record to be between $145 and $154. When cybercriminals manage to steal millions of customer records, the cost to business can therefore be considerable.
Major cyberthreats of 2016
- Cloud computing
- Mobile devices
- Malware
- State sponsored hacking
- Phishing attacks
- Ransomware
- Medical devices
Cyberthreats may be an impediment to growth, but it doesn’t mean that those threats cannot be mitigated. Given the increasing risk it is imperative that adequate security defenses are put in place to repel attacks. Malware and ransomware are becoming more sophisticated and much more difficult to identify, as are the phishing campaigns that are used to deliver the malicious software. Anti-phishing strategies must therefore be implemented to block malicious emails and staff members must be trained how to identify phishing attacks when they do occur.
Implement SpamTitan to block emails from being delivered to employee’s inboxes, conduct regular staff training exercises to better educate employees, and perform phishing email tests to ensure that members of staff get practice at identifying dummy phishing emails.
It is also essential to develop policies and controls to limit the types of websites that employees are able to visit when using their work computers as well as for BYOD. Drive-by malware downloads are an increasing threat. Exploit kits are much more commonly used to probe for security vulnerabilities, such as out of date plugins. These can be exploited and used to download malware to devices without any interaction from the user.
To mitigate the risk, patch management policies must be developed. It is more essential than ever to ensure that all software is updated as soon as patches are released.
by titanadmin | Jan 22, 2016 | Industry News, Phishing & Email Spam, Spam Software |
What was the best antivirus software solution for 2015 for the enterprise?
Protecting against the ever increasing number of cyberthreats is a full time job. The attack surface is now broader than ever before and hackers are developing increasingly sophisticated methods of obtaining data. The measures that must now be implemented to keep cyberattackers at bay have also increased in diversity and complexity.
Once of the core protections required by all organizations and individuals is an anti-virus software solution, and there is certainly no shortage of choice. But what was the best antivirus software solution for 2015?
The best AV software engines rated by AV-Comparatives
What AV engine detects and removes the most malware? What product offers the best real world protection? Which boasts the best file detection rates? These are all important considerations if you want to keep your organization protected. These and other factors were assessed over the course of the year by AV-comparatives.
AV-Comparatives is an independent testing lab based in Innsbruck, Austria. Each year the company publishes a report detailing the results of the AV tests the company conducted over the course of the year. The report is an excellent indicator of performance.
The company tested 21 of the top AV products on the market, subjecting each to a wide range of rigorous tests to determine the potential of each to protect users against malicious attacks.
The test results clearly show that not all antivirus products are the same. While all AV engines under test offered an acceptable level of performance, “acceptable” may not be good enough for enterprise installations.
The best antivirus software solution of 2015
AC-Comparatives rated performance and issued a number of awards to companies that excelled in specific areas of antivirus and antimalware protection. Gold, Silver and Bronze awards were awarded along with an overall best antivirus software solution for 2015 award.
Antivirus award categories:
- Real-world detection
- File detection
- False positives
- Overall performance
- Proactive protection
- Malware removal
Contenders for the ‘Best Antivirus Software Solution for 2015 Awards’
The Antivirus protects tested and considered for the awards were:
- Avast Free Antivirus
- AVG Internet Security
- Avira Antivirus Pro
- Baidu Antivirus
- Bitdefender Internet Security
- BullGuard Internet Security
- Emsisoft Anti-Malware
- eScan Internet Security Suite
- ESET Smart Security
- F-Secure Internet Security
- Fortinet FortiClient (with FortiGate)
- Kaspersky Internet Security
- Lavasoft Ad-Aware Free Antivirus+
- McAfee Internet Security
- Microsoft Windows Defender for Windows 10
- Panda Free Antivirus
- Quick Heal Total Security
- Sophos Endpoint Security and Control
- Tencent PC Manager
- ThreatTrack VIPRE Internet Security
- Trend Micro Internet Security
The Best Antivirus Software Solution for 2015 Award
After assessing all categories of anti-virus protection there were two AV products that excelled in all categories and received an Advanced+ rating: Bitdefender and Kaspersky Lab, with Kaspersky Lab bestowed the best antivirus software solution for 2015. Kaspersky Lab is one of the two AV engines at the core of SpamTitan anti-spam solutions.
The Russian antivirus company also received a Gold Award for “Real-World” protection, file detection, and malware removal, as well as a Silver Award for proactive (Heuristic/Behavioral) protection, and a Bronze Award for overall low system impact performance.
Cet article est disponible en anglais.
by titanadmin | Jan 19, 2016 | Phishing & Email Spam, Spam News |
The astronomical cost of remediation after a cyberattack prompts many companies to take out a cyber insurance policy, but what exactly do cyber insurance policies cover? Is phishing covered by cyber insurance for instance? How about accidental data exposure by employees? Fraudulent bank transfers? Before taking out a cyber insurance policy it is vital to check exactly what the policy covers. If you already have a policy, it might be a good idea to check that too before you need to make a claim.
Debate over whether phishing covered by cyber insurance
In the United States, one company is currently embroiled in a dispute with their cyber insurer over whether phishing is covered by a cyber insurance policy taken out by the company to protect against computer fraud and cyberattacks.
Ameriforge Group Inc., took out cyber insurance with a subsidiary of Chubb Group. The policy, provided to AFGlobal Corp by Federal Insurance Co., was believed to cover computer fraud and funds transfer fraud. A claim was recently submitted to recover $480,000 after a member of staff from its accounting department fell for a spear phishing attack and made a $480,000 bank transfer to the account of the attacker. The insurance policy provided up to $3 million in cover, yet the claim was denied by the insurer on the grounds that the policy did not cover CEO fraud or business email compromise (BEC) as a result of phishing.
In order for the policy to payout, a cybersecurity attack must involve the forgery of a financial instrument. That did not occur in this case. The insurer maintains that the scam email did not qualify as a financial instrument, and therefore the losses suffered cannot be claimed under the terms of the policy.
The business email compromise scam that the policy does not cover
The phishing scam in question is one that is being conducted with increasing frequency. The risk is so high that last year the FBI issued a warning about BEC attacks. These attacks are being conducted all too often on U.S. businesses.
In this case, the person to fall for the BEC phishing scam was AFGlobal Corp’s accounting director Glen Wurm. He received an email from his CEO requesting a bank transfer be made for $480,000. The email was written in a style which was typical of the communications sent from the CEO. This suggested the attacker was well aware of the relationship between the two individuals and had been monitoring email communications.
The phishing email is reported to have contained the following message:
The email was followed up with a phone call from a person claiming to be Steven Shapiro, after which, wiring instructions were sent to allow the transfer of funds to an Agricultural Bank of China account. The money was transferred as requested and it was only when a follow up email was received a week later requesting a further transfer of $18 million that suspicions were raised. Of course, by that point the transferred funds had been withdrawn and the account had been closed.
Chubb Group claims phishing not covered by cyber insurance policy
Chubb Group maintains that this cyberattack is not covered by the insurance policy issued, as the incident falls outside the forgery coverage provided. The claim refers to forgery by a third party and that the email was a financial instrument. The issue in this case is whether the phishing email qualifies as a financial instrument. Chubb’s legal team claims it doesn’t.
In order to be a financial instrument, Chubb says:

For the claim to be paid, the financial instrument must have involved a written promise, order or direction to pay that is ‘similar’ to a “check” or “draft”. As it stands, Ameriforge Group will be required to cover the cost.
This is not the first time that Chubb Group has refused to pay a fraud claim, and Chubb Group is certainly not the only insurance company to refuse to pay out after a phishing attack. Companies are therefore advised to check whether phishing is covered by a cyber insurance policy, and also to find out the specific criteria that must be met in order for a successful claim to be made. It may be a wise precaution to obtain additional cover if the terms of the policy do not allow phishing fraud claims to be made.
by titanadmin | Jan 15, 2016 | Email Scams, Internet Security, Phishing & Email Spam, Spam News |
If you receive an email alerting you to a new WhatsApp voicemail message that you have received, it could well be the latest WhatsApp scam email that is currently doing the rounds. This new scam is particularly nasty.
Malicious WhatsApp scam email discovered
The WhatsApp scam email is being used as part of an attack on businesses and consumers, and will result in Nivdort malware being loaded onto the device used to open the email.
Security researchers at Comodo discovered the WhatsApp scam email and have warned that the malware contained in the email attachment has been developed to affect users of Android phones, iPhones, as well Mac and PC users.
The WhatsApp scam email looks like it has been sent by WhatsApp, although there are a number of tell-tale signs that the WhatsApp scam email is not legitimate. For a start, WhatsApp will not send messages to a user’s email account, but will only inform users of a missed call or voicemail message through the app itself. However, many of the 900 million users of the chat software program will not be aware of that.
The email contains the imagery typically associated with the Facebook-owned messaging platform, but a check of the sender’s address will reveal that this email has not been sent from WhatsApp. The email also contains a zipfile attachment. Opening the zip file will result in malware being installed onto the device used to open the attachment.
The attackers are sending out multiple variants of the email with different subject lines. Each subject line also contains a string of three, four, or five randomly generated characters after the message, such as “xgod” or “Ydkpda”
The subject lines in some of the scam emails have been detailed below:
If you receive any email from WhatsApp you should treat it as suspicious. You should never open any email attachment from any person you do not known, and must be particularly caution with .zip files. If in doubt, delete the email and remove it from your deleted email folder.
Malware Delivered by the WhatsApp scam email campaign
Nivdort is a family of Trojans that collect data from the computers on which they are installed. In order to avoid being detected the malware is loaded into the Windows folder. The latest variant is loaded to multiple system folders and also the registry. Even if detected by anti-virus software it is possible that not all traces of the malware will be removed. The malware may still be able to receive commands and exfiltrate data from the infected device.
by titanadmin | Jan 9, 2016 | Phishing & Email Spam, Spam News |
It seems like almost every day that a new bank transfer email scam is launched, yet the perpetrators of these email scam campaigns appear to rarely be caught and punished for their offenses. However, one such scammer has now been arrested and made to stand trial for his alleged crimes against companies in Texas.
Nigerian, Amechi Colvis Amuegbunam, 28, of Lagos was arrested in Baltimore and has now been charged with defrauding 17 companies in North Texas and obtaining $600,000 via bank transfers.
Nigeria is famed for 419 email scams, otherwise known as advance fee scams. These spam email campaigns receive their name from the section of the Nigerian criminal code that the email scams violate. These bank transfer scams typically require the soon-to-be victim to make a transfer of a sum of money to cover fees or charges in order to receive a substantial inheritance. This type of email bank transfer request scam is not only conducted by criminal gangs operating out of Nigeria, although that is where a substantial number of the criminals are based.
Convincing bank transfer request scam used to defraud Texas companies of over $600,000
However, Amuegbunam obtained funds from Texan companies using a much more believable scenario; one that is being increasingly used by organized criminal gangs operating out of Africa, the Middle East, and eastern Europe.
The emails Amuegbunam sent appeared to have come from the email accounts of company executives, which had been forwarded onto members of staff who were authorized to make bank transfers on behalf of the company. By using the real names of top executives, account department employees were fooled into believing the transfer requests were legitimate. The companies being targeted had been researched, the correct email account format determined, names of senior executives and management determined, and the names of account executive targets discovered.
To make the bank transfer request scam more believable, Amuegbunam used a domain name that differed from the real company domain by two characters. By transposing just two characters, the email address appeared to be genuine at first glance, certainly enough to fool the victims.
The FBI started investigating the bank transfer request scam in 2013 after employees from two companies in North Texas were fooled into making large bank transfers. Amuegbunam has used the domain lumniant.com instead of luminant.com to make an email appear to have come from within the company. The account executive who fell for the bank transfer request scam made a transfer of $98,550. The second company fell for the same scam and transferred $146,550.
Amuegbunam has now been charged with defrauding 17 Texas companies using the same method. If convicted of the crimes, he faces a fine of up to $1 million and a jail term of up to 30 years. He is just one individual however. Many more are operating similar scams.
It is therefore essential that members of the accounts department, and others who are authorized to make transfers on behalf of the company, are told how to identify a bank transfer request scam. They must also be instructed to carefully check domain names on any transfer requests and to specifically look for transposed letters.
by titanadmin | Dec 30, 2015 | Email Scams, Phishing & Email Spam, Spam News |
In the United States, tax season starts on January 1 and Americans are required to complete their annual tax returns before the April 15, deadline. As is customary at this time of year, new IRS tax refund spam email campaigns have been launched by cybercriminals.
During the first quarter of the year employees must get their tax documents from their employers and collect and collate all paperwork relating to their earnings over the year. Many dread having to pay out thousands of dollars in tax, but for some there is some good news.
The IRS has been sending emails to millions of Americans telling them that their previous tax returns have been assessed and they are due for a tax refund. The notifications have arrived by email and details of the refund are contained in an email attachment. All the recipient needs to do is to open the attached file to find out how much money they are due to have refunded.
Unfortunately, the email notifications are bogus and have not been sent from the IRS. This is just the latest IRS tax refund spam campaign to be launched by cybercriminals. The email is anything but good news. The IRS tax refund spam email contains a zip file, but instead of details of a refund, the file contains a rather nasty selection of malware and ransomware. Worse still, the batch of malware is sophisticated and capable of evading detection. The malware remains resident in the memory of the device used to open the email attachment. The mail recipient is unlikely to discover their device has been infected until it is too late.
If anti-spam solutions have been installed the IRS tax refund spam emails should be caught and quarantined. Even if not, some users will have to try hard to infect their devices. If security software has been installed on the device, opening the attachment should result in warnings being issued. The user will need to ignore those warnings before proceeding. Many do just that. The attraction of a tax refund after overspending at Christmas is too difficult to resist.
For many users the latest strains of malware included in the zip file will not trigger AV engines and even some anti-malware software programs will not identify the files as being malicious. The threat to businesses is therefore serious. If the attachment is opened and run, the malware will be installed and granted the same network and device privileges as the user.
IRS tax refund spam contains CoreBot and the Kovter Trojan
Opening the email attachment will deliver the latest strain of the Kovter Trojan. Kovter is not installed on the computer’s hard drive as commonly occurs with malware. This makes it much more difficult to detect. Instead, malicious code is run with the malware residing in the memory. Memory resident malware does not tend to persist. Once the infected computer is rebooted, the malware doesn’t reload. However, in the case of Kovter it does. Kovter is reloaded via the registry each and every time the computer is booted. Kovter is fileless malware that runs commands via Powershell in a similar fashion to Poweliks. If a computer does not have Powershell installed, the user is not protected. Kovter will just download it and install it on the device.
Kovter is not new of course. It was first identified two years ago, but it has since evolved to evade detection. In addition to being used to deliver ransomware, which locks the computer until a ransom is paid, it is also being used to perform click-fraud and generate revenue for the hackers via CPC campaigns.
Kovter is known to be used on an affiliate basis. Any individual who signs up is paid based on the number of devices they are able to infect. Cybercriminals have been spreading infections via a range of exploit kits such as Angler, Neutrino, and Fiesta. The IRS tax refund spam attack is a new way of getting the malware installed on devices.
The zip file also installs CoreBot; a particularly nasty malware that poses even bigger problems for businesses. If employees are fooled by the IRS tax refund spam and open the zip file, CoreBot can prove particularly problematic to detect, and can potentially cause a lot more damage. CoreBot is a modular malware that can have additional functions added by hackers as and when they desire. It has previously been used as a data stealer, although recently it has been used for man-in-the-middle-attacks on financial applications and web services. The malware is capable of stealing banking credentials and login information. It can also be used to exploit new zero-day vulnerabilities.
It security professionals should be wary and should warn their company’s employees of the tax refund spam, and instruct them not to open any zip file attachments, or any email attachments that have been sent from unknown senders. The IRS will not notify individuals of a tax refund in this manner. Any IRS email with a file attachment is likely to be spam and contain malware.
by titanadmin | Dec 29, 2015 | Email Scams, Phishing & Email Spam, Spam Advice |
If you work in the accounting department of your company, you need to be more vigilant as cybercriminals are specifically targeting account department executives. Whaling attacks are on the increase and cybercriminals are using domain spoofing techniques to fool end users into making bank transfers from corporate accounts. Once money has been transferred into the account of the attacker, there is a strong probability that the funds will not be recoverable.
Whaling, as you may suspect, is a form of phishing. Rather than cybercriminals sending out large volumes of spam emails containing malware or links to malicious websites, individuals are targeted and few emails are sent. Cybercriminals are putting a lot of time and effort into researching their targets before launching their attack.
The aim is to gather intel on an individual that has the authorization to make bank transfers from company accounts. Individuals are usually identified and researched using social media websites such as Twitter, LinkedIn, and Facebook.
When individuals are identified and the name and email address of their boss, CFO, or CEO is discovered, they are sent an email requesting a bank transfer be made. The email is well written, there is a pressing need for the transfer to be made, and full details are provided in the email. They are also given a reasonable explanation as to why the transfer must be made. The email also comes from senior management.
In the majority of cases, the transfer request will not follow standard company procedures as these are not known by the attackers. However, since an email will appear to have been sent from a senior figure in the company, some account department employees will not question the request. They will do as instructed out of fear of the individual in question, or in an attempt to show willingness to do what is required of them by their superiors.
Unfortunately for IT security professionals, whaling emails are difficult to detect without an advanced spam filtering solution in place. No attachments are included in the email, there are no malicious links, just a set of instructions. The attack just uses social engineering techniques to fool end users into making the transfer.
What is Domain Spoofing?
The whaling attacks are often successful, as users are fooled by a technique called domain spoofing. Domain spoofing involves the creation of an email account using a domain that is very similar to that used by the company. Provided the attacker can get the correct format for the email, and has the name of a high-level account executive, at first glance the email address will appear to be correct.
However, closer inspection will reveal that one character in the domain name is different. Typically, an i will be replaced with an L or a 1, an o with a zero, or a Cyrillic character may be used which is automatically converted into a standard letter. If the recipient looks at the email address, they may not notice the small change.
To reduce the risk of account department employees falling for whaling attacks, anti-spam solutions should be implemented and configured to block emails from similar domains. Staff must also be told not to make any transfer requests that arrive via email without first double checking with the sender of the email that the request is genuine, and to always carefully check the email address of the sender of such a request.
by titanadmin | Dec 22, 2015 | Phishing & Email Spam, Spam News |
A new Lloyds Bank phishing scam has been uncovered. The UK bank’s customers are being targeted just before Christmas with a highly realistic email, apparently sent from Lloyds Banking Group. Christmas is a time when people let their guard down. Its busy at work, there is much to do, and minds are invariably on Turkey, holidays, and rushing to get last minute preparations completed.
New Lloyds Bank phishing scam is highly realistic
The email contains the exact same font, logo, and styling that are used on the real online banking portal, making the campaign one of the most realistic online banking phishing scams we have seen.
The latest Lloyds Bank phishing scam is pure simplicity. It is brief and to the point, and has been designed to scare users into clicking on the link and signing into their account to check their bank balance.
All that the email says, is “You have One New Message. Your account has been accessed in multiple locations. Click below to update your Lloyds Bank Account, with a hyperlink using the anchor text “Sign In.” There are no spelling mistakes or grammatical errors to warn users that the email is anything but genuine.
In fact, even clicking the sign in link is unlikely to arouse suspicion. The link will direct the soon-to-be victim to a website containing an exact copy of the Lloyds Bank portal that customers will be very familiar with. All of the text is genuine, and the website features apparently clickable links in all the right places. It is an almost exact replica of the real site.
Only if a user decides to click on any of the links will they realize something is not quite right. The scammers have only taken an image of the real site. They have not made any of the links actually clickable.
But then again, after the recipient of the email has been sent a warning telling them their account is under threat, they are unlikely to suddenly decide to check the latest mortgage rates or take out a loan.
The only part of the website that works is the section where users are required to enter their user ID, password, and memorable word. Once the credentials have been entered, the victim will be redirected to Lloyds. That may arouse suspicion when their login attempt did not work, but the scammers hope that few will bother to change their password when they realize their account has not been compromised.
The scammers are likely to act quickly. Once they have a User ID, password, and memorable word, they have the basic information necessary to access the account. That information may be sufficient to gain access to the account and make a fraudulent transfer. If not, it will be used as the basis for a further spear phishing email to attempt to get the answer to a security question. If the victim fell for the first campaign, chances are they will fall for another.
There is only one other giveaway that this is a Lloyds Bank phishing scam. The URL is not lloydsbank.com.
The scam highlights the importance of checking the URL before entering any login credentials and checking to make sure the site address starts with https://. This site is clearly not genuine and has no green padlock, indicating something is amiss to anyone even casually checking the web address. However, not all online banking customers will do that when the website appears to look like the real deal.
by titanadmin | Dec 16, 2015 | Industry News, Internet Security, Phishing & Email Spam, Spam Software, Website Filtering |
Following the recent news that Intel Security will be discontinuing McAfee SaaS Email Protection products, SpamTitan is preparing for 2016 when business customers start looking for a new email security vendor to ensure continued protection.
McAfee SaaS Email Protection to Come to an End
Intel Security, the new company name for McAfee, has taken the decision to exit the email security business. The company will be dropping McAfee SaaS Email Protection products and will be concentrating on other areas of business.
From January 11, 2016, McAfee SaaS Email Protection and Archiving and McAfee SaaS Endpoint will stop being sold by Intel Security. The news is not expected to trigger a mass exodus in early 2016, as Intel Security has announced that it will continue to provide support for the products for a further 3 years. Support for both McAfee SaaS Email Protection and Archiving and SaaS Endpoint will stop after January 11, 2019. However, many customers are expected to make the switch to a new email security provider in the new year.
SpamTitan Technologies Anti-Spam Solutions
SpamTitan Technologies offers a range of cost effective business email security appliances which keep networks protected from malware, malicious software, and email spam. Users benefit from dual AV engines from Bitdefender and Clam Anti-Virus, offering excellent protection from email spam, phishing emails, and inbox-swamping bulk mail.
SpamTitan is a highly effective anti-spam solution that was first launched as an image solution. Following an agreement with VMware, SpamTitan was developed into a virtual appliance. The range of anti-spam products has since been developed to include SpamTitan OnDemand in 2011 and SpamTitan Cloud in 2013. In August 2015, SpamTitan blocked 2,341 billion emails and has helped keep business networks free from malware and viruses.
SpamTitan was the first Anti-Spam Appliance to be awarded with two Virus Bulletin VBSPAM+ awards and has also received 22 consecutive VBSpam Virus Bulletin certifications. Additionally, SpamTitan was awarded the Best Anti-Spam Solution prize at the Computing Security Awards in 2012.
Companies in over 100 countries around the world have chosen SpamTitan as their anti-email spam partner. The email security appliance stops 99.98% of email spam from being delivered.
WebTitan Web Filtering Solutions from SpamTitan Technologies
WebTitan Gateway offers small to medium businesses a cost effective method of blocking malware and malicious websites, with highly granular controls allowing individual, group, and organization-wide privileges to be set. Delivered as a software appliance that can be seamlessly integrated into existing networks, it is an essential tool to protect all business users and allow the Internet to be viewed securely.
WebTitan Cloud is a cloud-based web filtering solution requiring no software installations. Create your own web usership policies and block malware-infected websites, objectionable websites, and restrict Internet access to work-related content with ease. Benefit from a comprehensive set of reporting tools which allow the browsing activity of every end user in the organization to be easily monitored.
WebTitan Wi-Fi has been developed for Wi-Fi providers and MSPs to allow easy control of Internet access. WebTitan Wi-Fi allows users to easily block objectionable content and malicious websites, with controls able to be applied by location. The cloud solution requires no software installations. All that is required to start protecting your business is a simple DNS redirect to WebTitan cloud servers.
WebTitan web filtering solutions blocked 7,414 malware-infected webpages in August 2015, and have helped keep businesses better protected from malicious website content, phishing campaigns, and drive-by malware downloads.
by titanadmin | Dec 10, 2015 | Email Scams, Industry News, Network Security, Phishing & Email Spam, Spam Software |
In the United States, healthcare industry phishing campaigns have been responsible for exposing the protected health records of well over 90 million Americans over the course of the past 12 months. That’s over 28% of the population of the United States.
This week, another case of healthcare industry phishing has come to light with the announcement of Connecticut’s Middlesex Hospital data breach. The hospital discovered four of its employees responded to a phishing email, resulting in their email account logins being sent to a hacker’s command and control center. In this case the damage caused by the phishing attack was limited, and only 946 patients had their data exposed. Other healthcare organizations have not been nearly so lucky.
Largest ever healthcare industry phishing attack suffered in 2015
In February, Anthem Inc., the second largest health insurance company in the United States, discovered it had suffered the mother of all healthcare data breaches. Approximately 78.8 million health insurance subscriber records were obtained by criminals in the attack. The breach did not occur in February, but months previously, with the hackers being allowed plenty of time to exfiltrate data.
Another U.S. health insurance company discovered it too had been hacked just a couple of weeks later. Premera Blue Cross similarly found out that hackers had gained access to its systems many months previously and had potentially obtained the records of over 11 million insurance subscribers.
Both security breaches were highly sophisticated in nature, but were discovered to have their roots in healthcare industry phishing campaigns. Employees had responded to phishing emails which ultimately allowed hackers to gain access to huge volumes of highly confidential healthcare data.
In 2014, Community Health Systems suffered a data breach that exposed the PHI of 4.5 million individuals in what was then the second largest healthcare data breach reported. That data breach had its roots in a phishing campaign sent to its employees.
Healthcare industry phishing attacks occurring with alarming frequency
In just 12 months, many healthcare providers and health plans have suffered at the hands of phishers. Some of the healthcare industry phishing attacks have been summarized in the table below:
Successful U.S. Healthcare Industry Phishing Attacks in 2015
| Company |
Records Exposed |
| Anthem Inc. |
78,800,000 |
| Premera Blue Cross |
11,000,000 |
| CareFirst Blue Shield |
1,100,000 |
| Seton Healthcare |
39,000 |
| Saint Agnes HealthCare |
25,000 |
| Partners Healthcare |
3,300 |
| Middlesex Hospital |
946 |
| St. Vincent Medical Group |
760 |
Cybercriminals attracted by easy targets and big rewards
In the United States, healthcare organizations and their business associates are covered by legislation which requires robust protections to be put in place to keep computer networks secure and patient health data safeguarded from attack. The Health Insurance Portability and Accountability Act (HIPAA) requires administrative, technical, and physical controls to be used to keep the Protected Health Information (PHI) of patients secure at all times.
Even though the industry is heavily regulated, the industry lags behind others when it comes to data security. Hackers often see healthcare organizations as an easy target. Their networks are complex and difficult to protect, and IT security budgets are insufficient to ensure that all of the appropriate protections are put in place to keep data secure.
On top of that, healthcare providers and health insurers store an extraordinary volume of highly sensitive data on patients and subscribers. Those data are much more valuable to thieves than credit card numbers. Health data, Social Security numbers, and personal information can be used to commit identity theft, medical fraud, insurance fraud, credit card fraud, and tax fraud. One set of patient data can allow criminals to fraudulently obtain tens of thousands of dollars, and the data can typically be used for much longer than credit card numbers before fraud is detected.
It is therefore no surprise that healthcare providers are such a big target. There are potentially big rewards to be gained and little effort is required. Healthcare industry phishing is therefore rife, and spear phishing campaigns are now increasingly being used to get busy healthcare employees to reveal their login credentials. Many of those campaigns are proving to be successful.
Industry reports suggest that the healthcare industry in the United States does not have sufficient controls in place to prevent against phishing attacks. A KMPG study conducted earlier this year showed that 81% of U.S. healthcare organizations had suffered cyberattacks, botnet, and malware infections. Other research conducted by Raytheon/Websense suggested that the healthcare industry in the United States suffered 340% more data breaches than other industries.
Healthcare industry phishing emails are not always easy to identify
Just a few years ago, a phishing email could be identified from a mile away. They contained numerous spelling mistakes and grammatical errors. Nigerian 419 scams were commonly seen and easily spotted. Malicious email attachments were sent, yet they could be easily identified as they were rarely masked. It is easy to train staff never to open an executable file sent via email.
Today, it’s a different story. Healthcare industry phishing emails are not always easy to identify. Malicious emails are crafted with a high level of skill, spell checks are used, subjects are researched, as are the targets. Links are sent to phishing websites that cybercriminals have spent a lot of time, money, and resources developing. Even a trained eye can have trouble identifying a fake site from a real one. The threat landscape has changed considerably in just a few years.
Sometimes healthcare industry phishing emails are so convincing that many members of staff are fooled into responding. Franciscan Health System is a good example. In 2014, a phishing campaign was sent to the healthcare provider via email. The scam was straightforward. Workers were sent an email containing a link and a good reason to click it. They clicked through to a website which required them to enter their login credentials. 19 workers reportedly fell for the campaign and revealed their email account login names and passwords. Contained in their email accounts were patient data. As many as 12,000 patients were affected.
What can be done to reduce the risk of phishing attacks?
There are a number of controls and safeguards that can be implemented to reduce the risk of healthcare industry phishing campaigns being successful, and multi-layered defenses are key to reducing risk.
Conduct Regular Staff Training
All members of staff should be trained on email and internet security, and told how to identify phishing emails and phishing websites. They must be issued with a list of best practices, and their knowledge should be tested. The sending of dummy phishing emails is a good way to check to see if they have taken onboard the information provided in training sessions.
Use Powerful Anti-Virus and Anti-Malware Software
Separate anti-virus and anti-malware solutions should be used and virus/malware definitions updated automatically. Regular scans of the network and individual devices should be scheduled at times of low network activity.
Employ Spam Filtering Software
Spam filtering solutions are essential. One of the best ways of preventing end users from falling for phishing emails is to make sure they never receive them. Powerful anti-spam solutions will block and quarantine malicious email attachments and prevent phishing emails from being delivered to end users.
Implement Web Filtering Solutions
Not all phishing campaigns come via email. Social media websites are often used as an attack vector and malicious website adverts can direct users to phishing websites. Implementing a web filter to limit the types of websites that users are permitted to visit can significantly reduce the risk of users falling for a phishing campaign. Web filtering solutions will also block access to known phishing websites.
by titanadmin | Dec 3, 2015 | Spam News, Website Filtering |
A recent study conducted by CyberArk has revealed that enterprises now face a high level of risk of privileged account hacking. In fact, the majority of enterprises are at risk of being hacked. Many companies are underestimating the risk, although IT professionals have long been aware of the danger of privileged account hacking.
The study suggests 88% of enterprise networks are susceptible to attack. A complete compromise of the corporate network is possible via 40% of Windows machines. The researchers predict that all it would usually take is for one privileged account to be hacked to allow the attackers to gain access to most accounts and systems. The researchers also determined that any enterprise that has Windows hosts is susceptible to attack via privileged account hacking.
To produce the report “Analyzing Real-World Exposure to Windows Credential Theft Attacks” CyberArk surveyed 51 organizations of varying sizes to determine the level of risk faced from privileged account hacking and the extent to which networks could be compromised should hackers manage to gain access to super-user and/or service accounts.
The results of the survey paint an incredibly worrying picture. The hacking of privileged accounts is not just a problem that must be dealt with by large corporations. Small to medium-sized businesses are also being targeted. Hackers are gaining access to their systems and are using them to launch attacks on their supply chain partners.
The privileged account hacking risk is often underestimated
Many organizations are not even aware how substantial the privileged account hacking risk is. An organization employing 500 individuals may have 1500 or more privileged accounts according to the researchers. The risk of attack is greatest with servers and lower with workstations. This is because servers can be used to gain access to a much wider range of systems and data than workstations. If any one server is compromised, attackers can use that machine for privileged account hacking and can gain access to many other Windows hosts on the network.
Attackers have months to analyze the network infrastructure and exfiltrate data
Mandiant recently estimated the median number of days for enterprises to discover their networks have been compromised is 229 days. The latest report from CyberArk also suggests a similar timescale for detection – placing the time frame at between 6 to 8 months. Once attackers have gained access to a network, they are exceptionally good at hiding and covering their tracks, and have months to browse the network.
How are hackers gaining access to privileged account login credentials?
In many cases, user credentials are stolen via phishing campaigns. Oftentimes, the attacks are highly sophisticated and highly targeted. Individual users are selected and a campaign is developed to fool them into visiting a malicious website and downloading malware or opening an infected email attachment.
Information about the target is obtained via social media networks such as Facebook, Twitter, or LinkedIn. Their contacts are identified, and a phishing email is either sent from a hacked colleagues account or is masked to make it appear that it has been sent from a trusted individual.
All too often a sophisticated attack is not necessary. If malware can be installed on just one single computer, shared-privilege accounts can be used to gain access to a wide range of systems.
What can enterprises do to protect their networks from privileged account hacking?
Protecting against the hacking of privileged accounts is difficult. It is not possible to eliminate privileged accounts as they essential to the functioning of the business. Since these accounts cannot be eliminated, efforts must be made to make accounts more secure. Unfortunately, the management of privileged accounts is complicated and is difficult to automate.
A survey recently conducted by Dimensional Research/Dell highlights the extent of the current problem. 560 IT professionals were asked about privileged access management and 41% revealed that they did not use any software at all or rely on Excel or other spreadsheet software packages to manage their accounts.
Fewer than half of respondents did not log or monitor privileged account access. 23% did not have a defined account management process. 28% did not have a defined process for changing default passwords on new equipment and software. Passwords were also found not to be changed frequently. Only a quarter of organizations changed admin passwords every month.
Make it harder for networks to be compromised by privileged account hacks
In order to improve security and prevent the hacking of privileged accounts, IT professionals should:
- Develop a defined process for managing privileged accounts
- Conduct a full audit of the network to locate all privileged accounts
- Ensure all passwords are unique, complex, and very difficult to guess
- Monitor and audit account passwords
- Use different passwords for different systems
- Change default passwords on all new devices and software
- Change passwords at least once a month
- Implement an automated solution to manage privileged accounts
- Ensure that a full risk assessment is conducted and any security holes are plugged rapidly (Hours rather than weeks or months)
- Conduct an audit of all suppliers and business partners to ensure they have sufficient security in place
- Implement solutions to protect users from phishing and spear phishing attacks, such as anti-spam software with anti-phishing controls
- Implement a web filter to reduce the probability of a user downloading malware to the network from malicious websites.
Fail to secure your login credentials, and privileged account hacking will not be only be a risk; it will be a reality.
by titanadmin | Nov 27, 2015 | Spam News |
Cryptowall 3 ransomware is the latest incarnation of the Trojan that first appeared in the latter half of 2014. This variant was discovered earlier this year and it has been used to extort millions out of individuals and businesses.
The threat from ransomware is growing
Ransomware infections have been reported much more frequently in recent months. A fortune has already been spent undoing the damage caused. Unfortunately, since the malware is evolving, it can be difficult to block.
Cryptowall 3 ransomware is very similar to previous incarnations and operates in a very similar fashion. The problem is that the algorithm it uses to obfuscate the dropper, which is applied three times, differs from Cryptowall 2. This makes it harder to identify.
Cryptowall 3 ransomware employs multiple dropper files and contains a number of different exploits. Once initiated, code is injected into a new explorer.exe process which installs the malware while disabling system protections. Malicious code is then hidden in a new SVChost.exe process.
The malware collects a considerable amount of data from the host computer, obtains an external IP address, establishes a connection, and registers the machine with the hacker’s command and control center. A POST request is made and the main Cryptowall 3 thread is initiated.
Cryptowall 3 ransomware subsequently encrypts certain file types on mounted network drives and local drives using public-key cryptography. The key to unlock the encryption is only stored on the hacker’s server. The victim is then advised to pay a ransom to have the infection removed and files unlocked. Failure to respond will see files locked forever or permanently deleted.
Cryptowall 3 ransomware is spread via email spam
Cryptowall 3 ransomware is primarily, but not exclusively, spread via spam email. The email contains a zip file attachment which houses an executable file. If the executable file is run, it installs the malware on the host computer. Videos, text files, and images files are then encrypted with its RSA2048 algorithm. Users often have files created on the desktop instructing them how to unencrypt their computer. Once infected, users are given approximately 7 days to pay the ransom, which is commonly $500 in the form of Bitcoins (2.17).
There is no guarantee that payment will result in the encryption being removed, although oftentimes it is. Payment certainly does not mean all traces of the malware will be removed from the infected machine. Users are often allowed to decrypt certain files to prove that the criminals behind the campaign can actually make good on their promise.
Victims are usually given little alternative but to give into the hacker’s demands, unless they want to lose all the files that have been encrypted.
Millions have been obtained from Cryptowall 3 ransomware infections
Cryptowall 3 ransomware has spread rapidly and the malware has already claimed tens of thousands of victims. The malware was only discovered in January 2015, yet already the criminals behind the infections have managed to obtain an estimated $325 million in ransoms according to Cyber Threat Alliance (CTA) figures. The ransoms have been tracked via Bitcoin payments, although the system used to assess criminals’ profits is somewhat unreliable. The figure of $325 million has been confirmed, but the total profits from Cryptowall 3 ransomware infections could well be double that total.
Cryptowall 3 ransomware infections usually start with a phishing campaign. The phishing campaigns usually contain an attachment with an innocent looking name, such as “invoice” or “fax”.
Drive-by attacks have been known to install the malware. These take advantage of security vulnerabilities in browser plugins. Exploit kits such as Angler are also used.
Fortunately, it is possible to train employees to be more cautious and not to open file attachments sent from unknown individuals. However, the emails may appear to have been sent by a friend, relative, or colleague inside their company.
Training should be provided to employees and company-wide warnings issued. However, the best defense is to prevent the ransomware from being delivered to inboxes. If SpamTitan Anti-Spam solutions are implemented, Cryptowall 3 ransomware email spam will be blocked and quarantined. End users will then be prevented from accidentally installing the malware.
by titanadmin | Nov 25, 2015 | Spam Advice, Spam News |
‘Tis the season to be jolly, but it is also the season for holiday email spam. Malware infections increase during holiday periods and this year is unlikely to be any different. Holiday email spam is coming, and it doesn’t matter whether you’ve been naughty or nice. If you do not take precautions, you are likely to receive a gift of malware this Christmastime.
Holiday email scams are sent in the billions at this time of year because of one simple fact: They work. People let their hair down over Christmas and New Year, but they also let their guard down. That gives online criminals an opportunity to get malware installed, fool consumers with phishing campaigns, and generally cause some festive mayhem.
Holiday email spam is now being sent: Avoid the Christmas rush and get your malware now!
Christmas week may see many people infected with malware, but the run up to Christmas can be even worse. As soon as the first decorations go up in the shops, holiday email spam starts to be sent. Email is commonly used to send malware.
Nasty malicious programs are masked as Christmas screensavers, phishing campaigns will appear as festive quizzes, and you can expect an African prince to need your assistance with a huge bank transfer. Don’t be surprised to find out that you have won a Sweepstake in a country you have never visited or that one of your online accounts will be hacked requiring you to receive technical support.
These and many more scams will be delivered in a wave of holiday email spam and, if you let your guard down, you may inadvertently fall for one of these often cleverly devised scams. Some of the latest phishing scams are incredibly convincing, and you may not even realize you have fallen for the scam and have become a victim.
Employers Beware: End users are especially gullible at this time of year
Everyone must be wary at this time of year due to the huge increase in spam email campaigns. Employers especially must take care as employees can be particularly gullible at this time of year. Their minds are on other things, and they are not as diligent and security conscious as they may usually be.
To make matters worse, each year the scammers get better and holiday email spam becomes more believable. If one of your employees falls for holiday email spam attack, it may not only be their own bank account that gets emptied. Phishing campaigns are devised to get employees to reveal critical business data or login credentials. The FBI has warned that business email is being targeted. In the past two years over 7,000 U.S. firms have been targeted and have suffered from criminal attacks. Those attacks initially target employees, and the festive season is an ideal time for a business email compromise (BEC) attack to take place.
Common Holiday Email Spam Campaigns in 2015
Send an email bulletin to your employees highlighting the risk that holiday email spam poses, and warn them that they may shortly start receiving phishing emails and other spam campaigns. They are likely to have forgotten how risky the festive season can be.
Business Email Compromise (BEC) Attacks
The FBI has already released a warning this year to organizations that perform wire transfers on a regular basis and/or work with foreign suppliers. They are being targeted by cybercriminals using sophisticated scams that start with the compromising of a business email account. Social engineering and phishing tactics are used to get employees to reveal their login credentials. Once access to bank accounts has been obtained by criminals, fraudulent transfers are made. Holiday email spam campaigns are expected to be sent targeting organizations and specific employees within those organizations. During the holiday period employees must be told to be ultra-cautious.
Holiday e-card scams
Holiday e-card scams are common at Christmastime. Criminals take advantage of the growing popularity of e-cards and send out spam emails in the millions telling the recipient to click a link to download their e-card. However, those links are sent to convince users to download malware to their computers. Any email containing a file attachment claiming to be an e-card is likely to be fake. The attachment may be malware.
Holiday-themed screensavers
Christmas and other holiday-themed screensavers are commonly downloaded by employees. These screensavers can be fun and festive, but may actually be malicious. Employers should consider implementing a ban on the downloading of screensavers as a precaution. Staff members should be warned that any .scr file sent in an email should be treated with suspicion and not downloaded or installed. Criminals mask attachments and the .scr file may actually be an executable file that installs malware.
Ashley Madison revelations and TalkTalk scams
A number of major data breaches have been suffered this year that have resulted in customer data being exposed. Criminals are threatening to expose personal data, especially in the case of Ashley Madison clients. Emails are sent threatening breach victims, informing them that they must pay not to have their data posted on the internet. Some criminals will be in possession of the data; other scams will be speculative. If an email is received, it is essential that professional advice is sought before any action is taken.
If you receive an email asking you to take action to secure your account after a company you use has suffered a data breach – TalkTalk for example – it is essential to only change your password via the official website. Do not click on links contained in emails. They may be phishing scams.
Free Star Wars tickets
You can guarantee that such a major event for moviegoers will be the subject of multiple email spam campaigns. Criminals would not pass up the opportunity to take advantage of the release of a new Star Wars film.
There are likely to be competitions aplenty, free tickets offered, and many other Star Wars spam campaigns in the run up to the release. This is the biggest movie release of the year for many people. Fans of the films are excited. They want to see snippets of the film, read gossip, and find out if Luke Skywalker will actually be in the new film. Many people are likely to fall for scams and click phishing links or inadvertently install malware.
Get prepared this holiday season and you can keep your computer and network spam and malware free. Fail to take action and this holiday time is unlikely to be jolly. Quite the opposite in fact.
by titanadmin | Nov 23, 2015 | Spam Advice, Spam News, Spam Software |
Criminals are increasingly using ransomware – Chimera ransomware for example – to extort victims. Ransomware encrypts certain file types with a powerful algorithm that cannot be unlocked without a security key. Unfortunately, the only person to hold that key is the hacker responsible for the ransomware infection.
Organizations and individuals that perform regular data backups can avoid paying the ransom demands and not face losing important files. If files are encrypted, they can be recovered from backups – provided of course that regular backups of critical data have been performed. Worst case scenario: Some data may be lost, but not a sufficient amount to warrant a ransom being paid.
Criminals are aware of this failsafe and have recently started to up the stakes. The criminals behind Chimera ransomware have been found to be using a new tactic to scare victims into giving into their demands. Even if a backup file has been made, victims can be easily convinced to pay the ransom. They are told that if the ransom is not paid, the files will be made public. Confidential information will be posted on darknet sites or listed for sale in online marketplaces.
Criminals Target Businesses and Encrypt Critical Files Using Chimera Ransomware
Hackers are known to send ransomware out randomly. The more computers that are infected; the more ransoms can be collected. Chimera ransomware on the other hand is being used more specifically, and small to medium sized businesses are being targeted. This stands to reason. An individual may not be willing, or able, to pay a ransom. Businesses are different. They may have no choice but to pay to have files unlocked. If data are posted online, the potential cost to the business could be far higher than the cost of the ransom.
How are computers infected with Chimera ransomware?
Spam emails are sent to specific individuals within an organization. Those emails contain innocent looking email attachments: the types of files that would commonly be received by the individuals being targeted. Business offers are sent, applications for employment, or invoices.
Attachments may not be opened or could be blocked by spam filters. To get around this issue, hackers often send links to cloud-storage services such as Dropbox. The user clicks the link and downloads the malware thinking it is a genuine file.
Once installed the malware gets to work encrypting files stored on local and mounted network drives. The user is not made aware of the infection until their computer is rebooted. In order to unencrypt files, the end user must pay the ransom. This is typically $500 in the form of Bitcoins.
It is not known whether hackers have acted on their threats to publish company data. Many businesses have been too scared to find out and have given in to the ransom demand.
How to protect your business from Chimera ransomware
There is no such thing as 100% protection from Chimera ransomware, but it is possible to reduce the risk of infection to a minimal level. Installing Anti-Spam solutions can prevent malware from reaching inboxes; however not all products offer protection from phishing links.
SpamTitan software on the other hand employs a powerful spam filter which uses dual AV engines to maximize the probability of malicious emails being caught. It also includes an anti-phishing module to protect against phishing links. If you don’t want to have to pay a ransom to recover your data, installing SpamTitan is the logical choice.
Are you protected from Chimera Ransomware? Would you risk the publishing of your business data or would you pay the ransom?
by titanadmin | Nov 19, 2015 | Spam Advice |
If you live in Ireland, you may receive an email offering you a refund on your electricity bill; however, the email is not genuine. Scammers are targeting current and former customers of Electric Ireland hoping they will respond to the offer of a refund. By doing so they will receive no money. They will just have their bank accounts emptied.
The Electric Ireland phishing scam is highly convincing
The Electric Ireland phishing emails appear to be genuine. They give a valid reason for clicking on the link contained in the email, and have been well written. The link directs the recipient to a phishing website that looks genuine. Even the request made on the website is perhaps not unreasonable.
In order to receive the refund, customers must enter in their banking information to allow the electricity company to make a transfer. In order to confirm their identity, current and former customers must supply proof of identity. The scammers ask for a scan of customers’ passports.
Other reports indicate that some customers have been sent links to fake websites that require them to disclose their mobile phone numbers as well as security codes and passwords.
It is unclear how the scammers have obtained the email addresses of Electric Ireland customers, as according to the utility company there has been no security breach, and the database in which customer account information is stored remains secure. However, an audit is being conducted by the company’s IT department to determine if any individual has managed to infiltrate its network or has otherwise gained access to customer data.
A spokesman for the Garda has confirmed that many Irish citizens have already fallen for the Electric Ireland phishing scam and have reported that fraudulent withdrawals have been made from their personal bank accounts.
The Electric Ireland phishing scam is one of many highly convincing campaigns to have been uncovered in recent weeks. Online criminals have become more skilled at crafting emails and setting up malicious websites, and it can be difficult to determine whether a request is genuine or fake.
The Electric Ireland phishing scam may look genuine, but legitimate companies would not send emails requesting sensitive information of that nature to be disclosed over the Internet. It should also be noted that if a company has taken excess funds from a bank account to pay a bill, the company would be able to issue a refund directly to the same bank account. They would not require those details to be provided again – nor request copies of ID, mobile phone numbers, or passwords.
If any individual who has fallen for the Electric Ireland phishing scam they should contact their bank immediately and place a block on their account. This will prevent the criminals from making any fraudulent transfers. However, it may be too late for many customers to prevent losses being suffered.
To reduce the risk of falling for phishing scams, the best defense is to block spam and scam emails from being delivered. To do this a spam filter should be used, such as that provided by SpamTitan. SpamTitan Technologies Anti-Spam solutions also include an Anti-Phishing module to ensure all users are better protected from malicious websites when surfing the Internet.
Any time an email is received that offers a refund, it is ill advisable to click on an email link. Attempts should be made to contact the company directly by calling the number listed on that company’s website. The matter should first be discussed with the company’s customer service department. Never open an email attachment contained in the email, and never divulge confidential information over the internet unless 100% sure of the genuineness of the website.
by titanadmin | Nov 18, 2015 | Spam News |
Cybercriminals are using SSL certificates installed on fake domains to fool users into thinking that the websites are genuine. The websites often use names that closely resemble a well-known brand. We have previously reported that criminals have been using domains containing typos to obtain website traffic and fool the unwary; however, it is also common for domains to be purchased using a well-known company name with additional words added to the end.
Because the websites contain the brand name, many visitors will be fooled into thinking that the websites are genuine. This is even more likely if a website has a valid SSL certificate and displays a padlock next to the URL. This is seen as a sign by many consumers that the website is real. A SSL certificate can no longer be trusted. It is only one indication that a website is genuine. Many new websites are offered a free SSL certificate.
Electronic Frontier Foundation phishing scam brought to an end
One website that has been fooling visitors into thinking the site was official is believed to have been set up by the cybercriminals behind the Pawn Storm phishing campaign: A group of hackers known as APT28. The group, which has links to the Russian government, used the brand name of the Electronic Frontier Foundation as part of a phishing campaign.
The Electronic Frontier Foundation phishing campaign used a .org website with the domain name, ElectronicFrontierFoundation. The official site used by the company is also a .org, but just uses the company’s initials: EFF.
The Electronic Frontier Foundation phishing site was not used to obtain bank account or credit card details, instead it was used to spread malware. The fake site was discovered to contain malware that exploited a zero-day vulnerability in Java software.
Electronic Frontier Foundation was alerted to the existence of the website and issued a complaint to the UN’s World Intellectual Property Organization (WIPO) – an organization that helps protect the intellectual property rights of corporations. After assessing the compliant, WIPO ruled that Electronic Frontier Foundation was entitled to take control of the domain, which has been ordered to be transferred to the non-profit digital rights group. Once that happens, the site will no longer pose a threat and ownership will be transferred from an individual based in Bali, Indonesia.
Organizations believing their copyright has been infringed can attempt to claim a registered domain by following the Uniform Domain-Name Dispute-Resolution Policy (UDRP) set up by ICANN. However, it can take a long time for the process to be completed. All the time that a fake domain is active it can result in a loss of income for the company concerned. Many customers or potential customers could have malware installed or be defrauded until the matter has been addressed and ownership of the website transferred.
In a case such as this, the domain name and SSL certificate made the website appear 100% legitimate, which no doubt resulted in many people having their computers infected with the malware.
by titanadmin | Nov 10, 2015 | Spam News |
Bermuda residents and holiday home owners have been put on high alert after a new BELCO email scam has been uncovered. A warning has now been issued by the company after some customers were targeted by scammers and were sent malware-infected emails from the company’s email domain.
BELCO, the Bermuda Electric Light Company Limited, supplies electricity to homes in Bermuda and is the only supplier in the British Overseas Territory. All individuals who own or rent a property on the islands are at risk of receiving a spam email that could potentially infect their computer, mobile phone, tablet or laptop with malware.
The type of malware sent in the spam emails is a form of ransomware. This type of malware is particularly nasty as it will allow the perpetrators of the campaign to lock files on an infected computer and potentially also on a business network to which the device connects. The malware delivered in the BELCO email scam can also cause corruption of computer files. The criminals behind the campaigns have designed the malware to give victims little choice but to pay the ransom.
Critical files are encrypted via the ransomware to prevent the user from gaining access. The only way of regaining access to the files is by restoring them from a backup or by paying a ransom to the criminals behind the campaign. Once a ransom has been paid, the criminals behind the BELCO malware attack will supply a security key that can be used to unlock the data. There is no guarantee that the security key will be provided once the ransom has been paid and it is conceivable that the criminals could continue to extort customers who give into their demands.
On a personal computer, files such as personal documents or family photographs could potentially be encrypted and lost. For business users the risk is even higher. Without access to critical files, all business could effectively grind to a halt. Even when a backup can be used to restore the ransomware-encrypted files, significant losses could be suffered. Performing a full restoration of data takes time and unless a backup was made just minutes before files were encrypted, some data will invariably be lost. Customers will also experience disruption to services while remediation takes place and systems are restored.
BELCO email scam uses legitimate company domain
The BELCO email scam uses a common technique to fool targets into installing malware on their devices. Criminals have been using email to deliver malware for many years, but they are now getting very good at creating highly convincing campaigns. It is becoming much harder to identify a spam email containing malware.
What makes this campaign particularly convincing is the emails appear to have been sent from the BELCO.bm domain. Even an individual who has adopted email security best practices, such as checking the sender’s address before opening an attachment, may be fooled into installing the malware contained in the email.
The email informs the recipient of an unpaid electricity bill and includes a warning that electricity will be cut off if the bill is not paid promptly. In order to find out how much money needs to be paid customers are required to open the attachment. Doing so will result in the malware being installed.
The email was sent from the address billerz @belco.bm. The domain is correct, although there is no official billerz address used by the electricity company. A warning sent to customers advises that any legitimate bill sent by the company will come from ebilladmin @belco.bm.
Simply receiving the email will not infect a computer but it is imperative that the attachment is not opened under any circumstances. Any customer receiving the email should delete it immediately from their inbox or spam folder. They should then ensure it is also deleted from their deleted email folder.
Identifying spam and scam emails
The BELCO email scam is convincing. It could easily pass for a genuine email if the recipient of the email is not particularly security conscious. There are tell-tale signs that it is a fake.
- The email address differs from the one usually used by the company to send electronic electricity bills
- There is a threat contained in the email – Immediate action is required to avoid unpleasant consequences
- Insufficient information is included in the email body, requiring the user to open an attachment
- The email address contains an odd spelling not typically used by a reputable company – billerz
Individuals, and especially companies, should consider implementing additional controls to prevent emails such as this from being delivered. Using a spam filtering solution will prevent the vast majority of spam and scam emails from being delivered. As more phishing and spam emails are being sent, and the perpetrators are becoming more skilled at creating convincing campaigns, this is one of the best defenses to prevent accidental malware infection. The cost of an Anti-Spam solution will be considerably less than the cost of a ransom to unlock vital data.
by titanadmin | Nov 9, 2015 | Spam Advice, Spam News |
UK workers are being targeted with a new email money transfer scam, according to a new police intelligence report. The current threat level has been deemed to be high enough to warrant a warning being issued by Financial Fraud Action UK to alert UK employees to the risk of attack.
Rather than the campaign being sent in mass email spam mailings, individuals are being targeted by criminals using a new spear phishing campaign that attempts to fool users into making a transfer from their personal account in order to secure an important work contract, or help resolve an urgent work issue.
The highly convincing scam involves the sending of emails to individuals in a particular organization that is being targeted. The perpetrators of the campaign have masked the email address of the sender, making it appear as if the email has actually been sent by their boss, a work colleague, or member of the accounts department. In some cases, the emails have actually been sent from a real account.
Email money transfer scam conducted in two separate attacks
Criminals first compromise an email account in the organization under attack by gaining access to an individual’s login credentials using a separate phishing campaign or by hacking passwords. Criminals have been able to gather a large amount of data on individuals via social media networks such as Facebook, Twitter, and LinkedIn. That information is subsequently used to craft convincing email campaigns to fool their targets into revealing sensitive information to gain access to their email accounts.
Those accounts are then used to send email requests to other individuals within the organization asking for a bank transfer to be made. The requests are out of the ordinary but, as explained in the scam emails, the payments are critical to the running of the business. Once a transfer has been made, the money is rapidly withdrawn from the scammer’s account. Victims are left with little recourse to get their money back.
The email money transfer scam has proved to be particularly effective. Employees see that the email has been sent by a manager and out of a sense of duty, or fear of job loss, they respond without first checking the genuineness of the email. Oftentimes, the perpetrators of the crime have sent emails from senior managers and partners’ accounts. An employee lower down the ladder would typically not usually have direct contact with these people, lessening the chance of them contacting that person directly to validate the request. Contact information is often provided in the email that will put the target in direct contact with the scammer, who will then validate the request.
Senior managers and partners are the initial targets in this new email money transfer scam. Criminals attempt to fool them into revealing their login credentials. Employees are the secondary targets who actually arrange the transfers to the fraudsters’ accounts. Both groups of individuals should be warned of the risk, and measures should be implemented to reduce the risk of the phishing campaigns being delivered.
To protect against the first attack made by the perpetrators of this email money transfer scam, it is recommended that companies make the following changes to improve security:
- Issue alerts to their employees, including senior managers, warning of the latest wave of phishing campaigns to put them on high alert.
- Enforce changes to email account passwords, ensuring that only secure passwords are used. Stipulate a minimum of 8 characters, force the use of special characters (!,”,£,$,%,^,&,*,(, or ) for example), and ensure that at least one capital letter and number is included.
- Purchase a robust Anti-Spam filtering solution to prevent phishing emails from being delivered to employee’s inboxes. SpamTitan also includes an Anti-Phishing module that can provide additional protection against complex campaigns such as this.
- Ensure that all Anti-Virus software has virus definitions updated on a daily basis
- Scammers often attempt to obtain login credentials by fooling targets into visiting a link to a malicious website containing malware. The sites may contain malicious code that probes for weaknesses in the target’s browser. The attackers then use SQL injection techniques to exploit software vulnerabilities and install keyloggers to obtain passwords. Anti-Phishing software can block these sites, providing protection even if an email link is clicked.
- Security vulnerability scans should be conducted regularly. Updates may be issued regularly so daily checks should be conducted. A scan may reveal a critical Windows 10 security update is required, or Oracle, Chrome, Firefox, Skype, or Adobe Flash may need to be updated.
- Inform employees of the company’s processes for requesting payments via bank transfers and confirm that under no circumstances would an employee receive a request via email to make a transfer to a senior manager or partner.
Protecting end users from becoming victims of an email money transfer scam
End users should also be informed about the correct actions to take when receiving email requests:
- This email money transfer scam relies on the user being fooled into thinking the email has been sent from a manager’s account. End users should check the email address used to make sure it has been sent from a company account, but to be wary that an email could have been hijacked.
- To contact the person who has made the request directly. Since email accounts may have been compromised, this should be done via telephone using the company switchboard or direct deal numbers, not the telephone numbers supplied in the email.
- To exercise extreme caution when receiving any request which appears to be out of the ordinary, especially when that request involves making a bank transfer or requests that sensitive information is disclosed.
- To read any email carefully, and then re-read it to identify spelling errors, grammatical mistakes or language that would be out of keeping with an email typically sent by that individual.
by titanadmin | Nov 6, 2015 | Spam Advice, Spam News |
A new DRIDEX email scam has been discovered that has prompted an angry reaction from Swedish furniture retailer Ikea. The criminals behind the malware have targeted Ikea customers by sending fake emails encouraging them to open a DRIDEX-infected email attachment. It has been estimated that hundreds of thousands of emails have been sent in the past few days alone.
As is common with spam emails, users are not specifically targeted. Instead the senders of the emails rely on volume. This is why targeting a retailer the size of Ikea is particularly effective. The chances of an email arriving in the inbox of a customer is relatively high in Europe. Many individuals regularly visit IKEA or have done so in the past.
What is particularly worrying about this campaign is the fact the emails look genuine. They contain an attachment which appears to be a purchase receipt from IKEA. The receipt looks exactly the same as one supplied by the store.
IKEA is concerned that the spam emails will tarnish the company’s reputation, even though there is nothing the company could have done to prevent the campaign from being launched. The advice provided is not to open any attachments in emails that appear to have been sent by the furniture retailer.
What is DRIDEX Malware?
DRIDEX is a nasty malware designed to steal online banking login names and passwords, and is a new variant of CRIDEX: A known form of malware with a worm and Trojan variant (W32.Cridex and Trojan.Cridex). The new form of the Cridex malware achieves its objective via HTML injection. This is a technique used by hackers to inject code to exploit vulnerabilities in popular applications such as Java or ActiveX. HTML injection modifies page content.
This method of attack is effective as the user is fooled into thinking a site being visited can be trusted, as the page is located within a trusted domain. When the user enters a login name and password, these are then sent on to the hacker. In this case, the user would reveal their bank logins and passwords, which would then be used to make fraudulent transfers to a hacker’s account.
DRIDEX malware first emerged in November last year and attacks have mainly affected computer users in Europe. Due to the ease at which the perpetrators of this campaign can obtain users’ banking credentials, this malware is particularly dangerous. All users, not just IKEA customers, should be particularly wary about opening email attachments or responding to emails containing links to webpages, especially if the emails are sent from individuals not known to the email recipient.
The malware was first used in the UK, but has since spread around Europe and has now been received in Sweden where IKEA is based. To date it has been estimated that the malware has allowed the perpetrators of the campaign to obtain around £20 million from fraudulent transfers, in addition to $10 million from U.S. banks. IKEA is now monitoring the situation and is attempting to identify the source of the emails; however, since the perpetrators of campaigns such as this are typically mobile, it is particularly difficult to catch the criminals responsible.
How is it possible to protect against DRIDEX Malware?
Email scams such as this are becoming increasingly common and users can easily be fooled into installing malware. DRIDEX appears to be primarily transmitted by spam email attachments.
Fortunately, there is an easy way of protecting against a DRIDEX malware infection. Since spam emails are now becoming harder to spot, the easiest solution is to prevent DRIDEX emails from being delivered. To do that, a spam filter such as SpamTitan is required.
SpamTitan is able to identify spam emails containing DRIDEX as the signature of the malware is present in the Anti-Virus engines used by the software. SpamTitan uses two separate AV engines which increases the probability of the malware being detected.
Since new malware is being devised and sent with increasing regularity, all email users should also be taught how to identify potential phishing emails as a failsafe to ensure. This will help to ensure they do not become another email scam victim, or inadvertently compromise their employer’s network.
by titanadmin | Nov 4, 2015 | Spam Advice, Spam News |
Email spam may not be the first choice of hackers for making money, but there are plenty of online criminals who still use email to fool users into installing malware on their computers or revealing sensitive information.
This week, two new email spam warnings have been issued following reports that consumers have received emails that have aroused their suspicions. When checking the authenticity of the emails received, they discovered they were scams. The warnings were issued by the Better Business Bureau (BBB) in an effort to prevent the scams from claiming victims.
The latest email spam campaigns differ from each other, but use tried and tested techniques which have proven to be highly effective in the past.
Jury Duty Scam Email Discovered
Trust in authority figures is being exploited in a new email spam campaign in which users are urged to take action as a result of missing jury duty. A similar email is doing the rounds warning recipients of an impending court case. Should the recipient of the email ignore the request, the case will be heard in their absence and they will not be allowed to mount a defense.
The emails shock recipients into taking rapid action such as clicking a link or opening an email attachment. These two emails are clever in the fact they warn users of the need to respond to a judge or turn up in court, yet the crucial information needed to do so is not supplied in the email body.
Any email recipient believing the email is genuine is likely to open the attachment or click a link to find out which court needs to be visited. By doing so they are guaranteed to have their computer, laptop or mobile device infected with malware.
The BBB was alerted to the scams and issued a warning advising recipients of these emails to delete them immediately. Advice provided saying the U.S. Courts would not contact individuals about jury duty by email. Letters are mailed or telephone calls are made in this regard.
Church Leaders Warned not to Fall for Money Transfer Email Spam Campaigns
The second scam was recently reported by the finance director of Grace Bible Church, who received a request via email to transfer funds to a senior pastor. In this case, the email appeared to be official, having been sent from the senior pastor’s email account.
It is a good security practice to always check the authenticity of an email that requests a transfer of funds. In this case all it took was a quick phone call to the pastor in question to reveal that the request was bogus.
If it is not possible to contact the individual, deleting the email would be the best next course of action. If the request is genuine, the individual in question is likely to make contact again. Spammers tend to send these campaigns randomly. A second request is unlikely to be received if the first is ignored.
The Fight Against Email Spam is Getting Easier
Spam email campaigns are still an effective method of malware delivery. Social media posts and infected websites may now be the preferred method of infection, but users must still be wary about opening attachments or visiting links sent from people they do not know.
Awareness of the tell-tale signs of an email scam has improved in recent years. So has security software used to detect phishing campaigns. SpamTitan Technologies is one such company that provides a highly effective spam filtering solution. It boasts an exceptionally low false positive rate and catches over 99.98% of all spam emails.
Part of the reason why SpamTitan’s Award Winning Anti-Spam solution is so effective at catching email spam is in part due to the power of the AV engines used. Instead of using one class-leading AV engine, it uses two: Bitdefender and Clam Anti-Virus.
By installing this anti-spam solution, malicious emails used to phish for sensitive information can be blocked before they are delivered to an email inbox. Businesses looking to reduce the risk of end users infecting their desktop computers, laptops and portable devices with malware and viruses, will find SpamTitan’s Anti-Spam solutions for the enterprise highly cost-effective. Rather than purchasing a package that offers protection for far more IP addresses than are required, IT professionals can purchase a license that covers end users without wastage.
by titanadmin | Oct 23, 2015 | Spam News |
Softlayer Rated Biggest Spam Hosting ISP by Spamhaus
According to a new report by the not-for-profit anti-spam organization, Spamhaus, the biggest spam hosting ISP is Softlayer, the IBM-owned cloud computing provider. A reported 42% of the ISP’s outbound emails have been discovered to be spam.
The report, issued on Wednesday, shows the ISP to be the current biggest offender, found to be supporting spammers and hosting numerous malware operations. The extent of the company’s emails found to be spam is astonishing, making it the undisputed champion of spam. Spamhaus has recorded over 685 separate spam issues on Softlayer, almost three times as many as the ISP in second place, Unicom-sc, which has had 232 reported spam issues.
Typically, the biggest web hosting companies and internet service providers do not feature so highly in the spam list, as they tend to employ numerous measures to prevent their servers being used by spammers and internet criminals. While Softlayer has not featured so highly in the past, recently it has been rising up the rankings, even though it does make efforts to fight spammers and implements controls to prevent them from using its servers.
In recent years the company has increased efforts to keep spammers at bay, and has taken firm, decisive action when reports of spamming have been received. But this has not proved to be sufficient.
It would appear that the ISP is now being targeted by Brazilian cybercriminals who are using its services to send out high volumes of spam emails and host numerous malware-infected websites. Softlayer is understood to have relaxed its criteria and vetting processes recently in an effort to attract more business; which does appear to have been successful, albeit for the wrong kind of business.
Spamhaus also pointed out that it has received requests to have Softlayer removed from its listing, but will only do so when it is clear that all of the issues have in fact been resolved. Spamhaus pointed out that cyber-criminals from Brazil were so active that “many listed ranges were being reassigned to the same spam gang immediately after re-entering the pool of available addresses.” The report went on to say, “these specific issues would not be removed until Softlayer was able to get control of the overall problem with these spammers.”
Softlayer has responded to the new number 1 ranking, saying affirmative action is being taken to tackle the issue. Communications Director, Andre Fuochi, recently told Krebsonsecurity, “We are aggressively working with authorities; groups like The Spamhaus Project, and IBM Security analysts to shut down this recent, isolated spike.”
Unfortunately, while action is being taken, it is not fast enough to stop the spammers. As soon as accounts and websites are shut down, more are created. Users are able to provision and de-provision sites and applications cheaply and quickly, which is why the ISP is struggling to stop spam emails from being sent and malware sites from being created.
Cloudmark recently confirmed Spamhaus’s rating, saying the Softlayer network was the largest single source of spam in the world during the third quarter of this year. The spammers and scammers will always find a home somewhere, but to find it at a company owned by IBM must come as a major embarrassment. IBM is, after all, a major player in the software security market.
by titanadmin | Oct 21, 2015 | Spam News |
A bank phishing scheme operated by a Moldovan man has resulted in $3.55 million being transferred from the bank accounts of a Pennsylvania mining company – the Penneco Oil Company Inc. – according to federal prosecutors.
The perpetrator of the campaign, Andrey Ghinkul, 30, has been charged following his recent arrest in Cyprus. He is awaiting extradition to the United States, with a hearing scheduled for next week.
The phishing campaign was sent out to numerous companies, with a number of recipients reportedly opening the email, only to have their computers infected with Bugat malware. Bugat Malware is a little known form of malware, operating in a similar fashion to the well-known Trojan Zeus.
Bugat malware functions as a SOCKS proxy server, allowing hackers to directly download and execute programs on an infected host’s computer, or upload files to remote servers. In order to escape detection, the malware communicates encrypted data with its command, and by doing so fails to trigger many traffic inspection software warnings.
The malware has been used to log information entered during online banking sessions, with Firefox and Internet Explorer browsers so far exploited. With the information obtained, hackers are able to make fraudulent wire transfers and ACH transactions. So far, small to mid-sized businesses have been most commonly targeted.
While many organizations are now looking out for Zeus infections, this new form of malware can escape detection more easily. The attacks also show how cybercriminals are diversifying their attacks in order to gain access to financial account information and avoid detection.
The phishing campaign was used to send emails to a number of recipients in U.S companies, with the emails appearing to have been sent from medical providers, indicating the recipients had received a positive diagnosis for cancer.
Bugat Malware Bank Phishing Scheme Nest Hackers Over $10 Million
According to the FBI, Bugat malware has resulted in around $10 million in funds being transferred from U.S company accounts to hackers in Russia and Belarus.
The transfers from Penneco Oil’s accounts were made possible by the malware, which recorded bank passwords as they were entered on the infected computer. That information was then used to make the transfers. The first transfer of $2.2 million was made in August 2012, with the funds being received by a bank based in Krasnodar, Russia. A second transfer was made the following month, this time the recipient account was in Minsk, Belarus.
While the transfers did go through, action was swiftly taken by the bank – Indiana, PA-based First Commonwealth – and the funds were rapidly restored. Senior Vice President of Penneco, D. Marc. Jacobs, said the bank “worked to completely restore our funds almost immediately.” In this case, Penneco had all funds restored and the bank had to cover the cost.
Should Ghinkul be extradited, the case will be heard in Pittsburgh where another attempted victim was targeted. Sharon City School District nearly lost $999,000 to a Russian account. Fortunately, that transaction was successfully blocked.
by titanadmin | Oct 19, 2015 | Spam News |
A new iTunes email scam has been uncovered which attempts to trick users into revealing their credit card numbers, according to a recent report issued by Malwarebytes.
The latest iTunes email scam targets users of iTunes and offers them a refund for a purchase that has been made using their iTunes account, indicating they have been affected by an email scam already. In order to receive the refund, the users must provide their Apple ID, password, and credit card details so the refund can be processed.
Emails have been sent to iTunes account holders telling them that their account has been fraudulently used to purchase an app valued at £34.99 ($53), with the emails containing a fake receipt for the purchase. The app is question is provided by CoPilot Premium HD, a supposed navigation service. The receipt contains a link that the recipient of the email must click in order for their refund to be issued, if the purchase is not genuine.
There is of course no such app, and the high price is perhaps a warning that something is amiss. Unfortunately for users looking to protect themselves from fraud, the very actions they take to protect themselves will actually ensure they do become victims.
Not the Only iTunes Email Scam Recently Uncovered
This is not the only email phishing scam to have been sent to Apple users in recent weeks. Another email spam campaign attempts to get users to click a link to update their credit/debit card, which users have been informed in the email is about to expire. Users have been requested to click a link and enter their new card details, including the CSC code on the reverse of their card, as well as the new expiry date.
As with many email scams of this nature, the email is sent with a threat of account suspension if they do not comply. In this case, users have little time to respond. The email link is said to expire in one hour’s time if it is not clicked, reducing the time for users to verify if the email is in fact genuine.
They are provided with a link to store.apple.com which is seemingly genuine; however, hovering over the link will reveal that the link directs them to a different location.
There are other common tell-tale signs that the email is a fake, even though the correspondence does contain seemingly genuine Apple imagery and appears to have been sent from Apple’s customer service department. One of the most telling signs is the volume of spelling mistakes contained in the email. Any email sent by Apple is likely to have at least been run through a spell check before being used as a template for millions of Apple device owners. A sure sign that the email is not genuine.
The email contains spelling and grammatical errors such as informing the recipient that the link will “expire one hours after the email was sent.” iPhone “ore” iPads is another, and feature is spelled “feauter.”
The advice to all Apple users is to take time to carefully read any email sent from Apple, and to attempt to verify any request to provide ID numbers or financial information.
by titanadmin | Oct 16, 2015 | Spam News |
It has now been over a year since the U.S Postal Service was affected by a phishing campaign that resulted in the exposure of the personal information of 800,000 current and former workers, yet the postal service is still not effectively dealing with the phishing threat. Employees have been tested, and they are not identifying phishing emails.
Postal Service Employees are at Risk of Falling for Phishing Emails
The network data breach of 2014 occurred as a result of employees falling for spear phishing campaigns, which allowed criminals to gain access to postal service networks containing sensitive data. The data thieves were able to gain access to the network and exfiltrate data without meeting much in the way of resistance. It would appear that if a similar campaign was conducted again now, even more data may be exposed.
The Office of the Inspector General (OIG) recently took the decision to put postal service workers to the test, to determine whether lessons have been learned since last year. In total, 3,125 fake phishing emails were sent to employees of the U.S Postal Service to determine whether they were actually able to identify a potential phishing campaign.
There was some good news. 75% of workers were able to resist the temptation to click on the phishing links in the emails. The bad news was 25% did click. Unfortunately, all it takes is for one person to respond to a phishing email for criminals to gain access to data. 780 responses to fake phishing emails shows risk is not being effectively managed.
However, perhaps worse still, was the lack of compliance with policies that had been put in place in the wake of last year’s successful attack. For instance, the postal service’s Computer Incident Response Team should be alerted if a suspicious email is received by workers, yet only 7% of employees did so during the test.
The reason is perhaps quite easy to explain. Only 4% of staff had completed the Postal Service cybersecurity training course, so presumably were unaware of the policy of reporting suspicious emails, if they were in fact able to identify them as suspicious.
OIG Report Shows Postal Service is Not Dealing with the Phishing Threat
The OIG report on the cybersecurity test stated that awareness training does have a positive impact, and can substantially reduce the risk of employees responding to a phishing campaign. Research shows training can reduce security-related risks by as much as 70%.
Policies must of course be turned into procedures, and the staff must receive training. The OIG said, “When management does not require all employees with network access to take annual information security awareness training, users are less likely to appropriately respond to threats.”
One of the main problems for organizations trying to tackle the threat of phishing is the fact that criminal organizations and hackers are developing ever more complex and convincing campaigns to fool users into opening malware-infected attachments and visiting links to malware-infected websites. However, if training is not provided to the staff, even uncomplicated phishing campaigns could well succeed.
At present, only new members of staff and CIO office members are required to undergo annual cybersecurity training: That is not the most effective way of dealing with the phishing threat. However, in response to the OIG report, the Postal Service will be implementing new training policies by April 2016.
by titanadmin | Oct 14, 2015 | Spam News |
The Federal Trade Commission has issued a warning over a new gaming email phishing scam that targets video game players and takes advantage of their love of the games to get them to divulge their account information.
Gamers invest considerable time and money into buying add-ons and developing gaming characters; however, the fear of loss of their gaming account is seeing many fall for the latest scam.
Cyber Criminals Opt for Gaming Phishing Email Scam
Hardcore gamers are not difficult to find, having registered on forums and gaming websites, providing their email addresses and other information about their gaming habits. Once criminals obtain email addresses of gamers, they are sent fake emails from gaming companies suggesting they have been discovered to have sold gaming items or characters for real money, and by doing so have violated the rules of the game.
Consequently, the users are threatened with account suspensions, or in some cases, legal action. A number of emails have been received by gamers with threats that they will be sued for amounts up to $2,700 for repeated violations of gaming rules and regulations. The intention is not to get the users to part with that money, but to get them to reveal details of their bank accounts or credit cards used to make purchases.
Users are often fooled into responding out of fear of losing their accounts or being suspended or banned from their favorite games. The email campaigns can also be highly convincing, using templates that appear legitimate, often including company logos and names the users may be familiar with.
The scammers have been targeting users of some of the most popular online games, such as World of Warcraft and Diablo III, both produced by Blizzard Entertainment, although the scam is not restricted to players of these games. The volume of emails sent to gamers, and complaints received, has resulted in Blizzard emailing users to tip them off to what it called “rampant scams.”
The FTC has also got involved, issuing a warning of its own. According to the FTC warning, targets are advised that they should check the status of their accounts and challenge the suspension if they have done no wrong. They are supplied a link for this purpose and are required to fill in a ‘verification’ form.
They are then asked to enter information in order to confirm their accounts and identities, and must reveal account and financial information. The perpetrators of the scam then empty their accounts.
This is not the only technique used by online fraudsters to get users to reveal their credentials. Gamers are being sent spam emails asking them to login in order to receive free gifts and exclusive game add-ons, with users requested to click a link in the email to login in order to claim their prize.
It is not always essential that account details are entered in the online forms to which the users are directed to. The links contained in the emails can direct the users to malware-infected websites. Malicious software is automatically downloaded to the users’ computers, allowing the perpetrators to gain access to the device and trawl files looking for personal information such as bank account details, login names and passwords.
Gamers have been warned to always try to verify any such emails, and not to click on links, open attachments or use the contact details provided. All requests that are out of the ordinary should be independently verified with the company concerned, using the gaming website’s contact information.
by titanadmin | Oct 12, 2015 | Spam News |
There has been some good news reported recently that indicates email spam levels are now at the lowest point seen in the past 12 years. According to a report issued by Security company Symantec, spam emails fell to 49.7% of all emails sent in June this year. Spam email levels fell further still in July, dropping to 46.4% of total email volume. Symantec also reported that the volume of phishing campaigns also saw a fall in June.
A number of reasons have been cited for the fall in spam levels, including bringing a number of spammers to justice and closing down their criminal networks, in addition to shutting down a number of rampant botnet networks, many of which were located in the United Kingdom.
The botnets were identified by UK police forces which orchestrated a number of takedowns. UK and European internet service providers had been collaborating with the police and passed on information on suspected botnets, helping to reduce the effectiveness of the networks, ultimately leading to many being shut down.
While this is good news, this does not mean there has been a reduction in risk. Phishing schemes may have seen a small drop in June, but the number of malware variants now being discovered has increased dramatically. The variation in malware is causing a problem, as the malicious software is becoming harder to identify. The extent of the increase in variants is considerable. In just two months the number of malware types had almost doubled from 29.2 million in April to 57.6 million pieces of malware caught by Symantec in July. This is the second highest figure reported in the past 12 months, with only November 2014 seeing more malware attacks caught (63.6 million).
The attack landscape is constantly changing, with cybercriminals now diversifying their attack vectors. Ransomware for instance, is becoming more popular. Just under half a million attacks (477,000) were thwarted by Symantec in June, with the volume of ransomware having risen for two months in a row.
While cyber criminals based in the UK and United States may be diversifying attack vectors, hackers in other countries still favor email spam, with eastern Europe and China still seeing huge volumes of spam emails being sent. It is certainly not a time to let one’s guard down or become complacent about email spam.
Businesses Still Receiving High Volumes of Spam Emails
Overall, levels of spam may have fallen, but small to mid-sized companies are still seeing high levels of spam emails received, with the percentage of spam emails remaining above 50%. Spam email traffic to small to medium companies (those with one to 250 employees) stood at 52% in June.
Malicious emails are also still being used extensively to target organizations of all sizes. In June, malicious emails were being most commonly used against companies employing 1501-2500 individuals, with one in 164 emails recorded as being malicious in nature.
In July the figures had improved, with organizations employing 251-500 individuals the most common recipients of malicious emails, registering one email in 260 as being malicious in nature, closely followed by small organizations employing under 250 individuals, with one in 275 emails rated as malicious.
Spam emails were still being sent at high levels to particular industries, with mining and manufacturing industries receiving high levels of spam in June. Over 56% of emails received in the mining sector were spam, with the manufacturing, construction, retail and non-traditional service industries all registering spam email volumes of 53% or more in June.
The figures for July actually showed an increase in spam for some industry sectors. Mining had increased to 55.7%, with only very slight falls in spam levels in other industry sectors. Manufacturing, retail and construction all registered spam percentages above 53%.
Each of the other 6 industry sectors (Professional services, agriculture/forestry/fishing, wholesale, non-classifiable establishments, finance/insurance/real estate, and non-traditional services) all registered spam email percentages of between 51.9% and 52.5%, indicating email spam remains a major problem for most U.S. businesses.
by titanadmin | Oct 9, 2015 | Spam News |
The Ponemon Institute has released a new report detailing the cost of phishing attacks on U.S businesses, suggesting the average annual cost for U.S companies has now risen to $4 million. Ponemon calculated phishing attacks take an average of 23.7 days to resolve, and are having a huge impact on U.S organizations, with smaller companies often suffering the most.
Cost of Phishing Attacks & Cyber Crime Assessed
The report indicates that the biggest costs suffered as a result of cyber crime come from phishing campaigns and social engineering, which accounted for 16% of total cyber crime costs. Phishing and social engineering were found to have affected 59% of organizations, while botnets affected 66% and web-attacks were suffered by 76% of organizations.
The Ponemon study, conducted in conjunction with HP Enterprise, involved a representative sample of 58 private and public sector U.S organizations being surveyed on cyber crime and the costs of dealing with criminal attacks. The results of the study show that in the U.S, the mean annualized cost of cyber crime has risen to $12.7 million per year, with the highest total average cost of dealing with cyber crime being $15.42 million – more than double that of Germany in second place.
The study showed that organizations are having to pay between $1.6 million and $61 million per year to resolve cyber attacks. The cost of the dealing with those attacks was found to be higher for larger organizations, although the per capita costs were highest for smaller organizations.
The new 2014 Cyber Crime Report shows the cost of dealing with attacks has risen 19% in just 12 months, with the global average cost of cyber crime estimated to have exceeded $7.7 million. Some companies are having to cover costs of up to $65 million to resolve criminal attacks, which were shown to have increased in both frequency and severity during the past 12 months. Email attacks remain one of the biggest causes for concern, being one of the main methods used by criminals seeking access to computer networks.
Phishing Emails Are Proving to be Highly Effective
Earlier this year, communications company Verizon produced a report indicating phishing campaigns can be highly effective methods of attack, and suggested that all too often staff training efforts are not particularly effective. Many organizations are now providing staff with information on how to identify phishing emails, yet this information does not appear to be retained. The study found that 23% of individual who received a phishing email opened it, and an alarming 11% of recipients clicked on the link contained in the email or opened the attachment.
The provision of training manuals on phishing to employees can be effective, but retention of information tends to be poor. The Ponemon study did suggest that one of the best methods of training staff how to identify phishing emails is to provide examples, indicating the sending of simulated phishing emails was particularly effective at reinforcing training, providing up to a 37% return on investment.
With phishing emails representing such a substantial proportion of cyber security costs, and training proving not always particularly effective at substantially reducing the risk of attacks being successful, greater efforts should be put into intercepting phishing emails and preventing them from being delivered to recipients’ inboxes. For that, a robust and effective email spam filter is required.
by titanadmin | Oct 8, 2015 | Spam News |
Although many reports suggest that email spam is reducing, email spam and botnet infection is still a major issue for most U.S organizations and individuals – with criminal practices netting cybercriminal gangs billions of dollars every year.
Determining the infection levels and the volume of spam being sent was one of the missions of the Messaging, Malware and Mobile Anti-Abuse Working Group (M3AAWG). M3AAWG, is a global organization tasked with promoting cybersecurity best practices and fighting organized internet crime. M3AAWG was formed a decade ago by a number of leading internet service providers, with the goal of improving collaboration and sharing knowledge to make it harder for criminals to spam account users. By reducing the impact of email spam on individuals and organizations, ISPs would be able to better protect users, IPS’s email platforms and their reputations.
Quantifying Email Spam and Botnet Infection a Complex Task
It was discovered that quantifying email spam and botnet infection levels was a complex task; one that was only possible with collaboration between internet service providers. As a result of this collaboration, the organization has produced reports on the global state of email spam and botnet infection. Its latest analysis suggests that approximately 1% of computer users are part of a botnet network.
The data gathered by M3AAWG involved assessing 43 million email subscribers in the United States and Europe.,The data analysis showed that IPS’s typically block between 94% and 99% of spam emails. The company’s report suggests that on the whole, IPS’s do a good job of blocking email spam.
The figures look impressive but, considering the huge scale of email spam, billions of spam emails are still getting through to users, with financial organizations and other companies now being regularly targeted with spam and malware.
Email spammers are well funded, and criminal organizations are using email spam as a means of obtaining tens of billions of dollars each year from internet fraud. Spam emails are sent to phish for sensitive information, such as bank account information, credit card details and other highly sensitive data including Social Security numbers. Accounts can be emptied, credit cards maxed out and data used to commit identity theft; racking up tens of thousands of dollars of debts in the victims’ names.
In years gone by, email spammers concentrated on sending emails randomly to accounts with offers of cheap Rolexes, Viagra, potential wives and the opportunity to claim an inheritance from a long lost relative. Today, spammers have realized there are far greater rewards to be had, and emails are now sent containing links to malware-infected websites which can be used to compromise users’ PCs, laptops and Smartphones, gaining access to highly sensitive data or locking devices and demanding ransoms.
Some emails may still be sent manually, but the majority are sent using botnets. Networks of infected machines that can be used to send huge volumes of spam emails, spread malware or organize increasingly complex attacks on individuals and organizations. The botnets are available for hire, with criminals able to rent botnet time and use them for any number of reasons.
Many of the attacks are now coming from countries where there is little regulation and a very low risk of the perpetrators being caught. Countries in Africa, as well as Indonesia and the Ukraine house huge volumes of cybercriminals. They have even set up call centers to deal with the huge volume of enquiries from criminals seeking botnet time to orchestrate phishing and spamming campaigns. Tackling the problem at the source is difficult, with corruption rife in the countries where the perpetrators reside.
However, it is possible to reduce spam level, and the risk of employees falling for a scam or downloading malware by installing a robust email antispam filter, reducing the potential for spam emails and phishing campaigns getting through to individual accounts. According to Verizon, 23% of users open phishing emails and 11% open attachments and click on links. Stopping the emails from reaching users is therefore one of the best methods of defense against attacks.
by titanadmin | Oct 6, 2015 | Spam News |
Lawyers representing plaintiffs affected by spammy marketing practices by business networking website LinkedIn have reached a $13 settlement in a California court, with the LinkedIn email spam lawsuit likely to result in users of the website receiving a payout of around $10 per person.
Lawyers argued that the marketing practices used to attract new users breached California’s common law right of publicity and constituted unfair competition, with millions of users having had their privacy violated. The class-action lawsuit was filed in September 2013 and lasted two years before LinkedIn agreed to settle the case without admission of liability. LinkedIn claimed no wrongdoing and that its business practices broke no laws.
Alleged Spammy Marketing Practices used by LinkedIn to Attract New Users
Users of LinkedIn are permitted to import contacts from email accounts such as Gmail. Users electing to “Add Connections”, will generate an email that is sent to their contacts list inviting those individuals to connect and sign up for an account with the website.
Site users were asked before emails were sent to their imported email contacts, but they were not advised about a further two emails that were triggered if their contacts did not respond to the original email request within a fixed period of time. The follow-up emails were reminders that the invitation was still waiting for approval.
The lawyers claimed that LinkedIn had been “breaking into its users’ third-party email accounts, downloading email addresses that appear in the account, and then sending out multiple reminder emails.” The case centered on the fact that users were not advised that this would be the case. It was claimed that the website was using the names and likeness of users to drum up more business without consent, thus breaching the privacy rights of site members.
Last year, LinkedIn petitioned U.S. District Judge Lucy Koh requesting the case be dismissed, as users had in fact given their consent for contacts to be sent emails; however, Koh ruled that while consent had been provided for one email to be sent, users had not given LinkedIn consent to send any further emails if individuals did not respond to the initial request to join the website.
Other claims made against LinkedIn were rejected, such as the breach of federal wiretap law and claims of hacking users accounts. As a result, the case was required to be resubmitted.
LinkedIn Users Invited to Submit Claims for Compensation
The LinkedIn email spam lawsuit has now been settled, although users of the site are unlikely to receive much in the way of compensation. Any user who used the Add Connections feature of the website between September 17, 2011 and October 31, 2014 have now been invited to submit claims, and have until December 14, 2015 in order to do so.
Due to the volume of individuals affected, it is probable that the payout for each affected user will be around $10. LinkedIn has agreed to add further funds – $750,000 – if the volume of claims it receives results in individuals qualifying for a payout of less than $10 a head. Linked in will also be required to cover legal fees in addition to paying the $13 million settlement.
From the end of the year, all users of the “Add Connections” feature will be informed that by doing so, they are giving their consent for their imported email contacts will be sent one email, and up to two follow-up emails if no response is received from the initial request. There will also be a new option added which will allow invitations and reminder emails to be stopped.
by titanadmin | Oct 1, 2015 | Spam News |
The threat from phishing emails is causing Health IT professionals major headaches, and is one of the main data security concerns according to a recent HIMSS cybersecurity survey. The recent HIMSS survey was conducted on 300 healthcare IT security professionals and suggests that the increase in phishing emails is one of the main reasons why the healthcare industry is having to invest so heavily in data security. 69% of survey respondents believed that to be the case.
Phishing campaigns are now being devised that are difficult to identity, with cybercriminals investing considerable time and effort into creating highly convincing emails in an attempt to get healthcare employees to divulge their login credentials.
Threat from Phishing Keeps CISOs Awake at Night
Criminals may still be sending random email spam in an attempt to obtain credit card details and banking information, but healthcare providers are now being increasingly targeted for the high volume of Social Security numbers and other personal patient information held; data that can be easily used to commit identity theft and obtain far more than is possible with credit card numbers. According to HIMSS Senior Director of Research Jennifer Horowitz, phishing is now “the number one thing that keeps CISOs up at night.”
The survey showed that data security has become one of the main business priorities for healthcare organizations, with 87% of respondents claiming data security has increased in priority over the course of the last year. Out of the respondents that said data security is a main priority now, two-thirds believe phishing to be the main cause for concern, and the same volume of respondents claimed their organizations had already suffered a phishing or other online scamming attack.
Phishing is a technique used by cybercriminals to obtain personal information, and is used as part of a wider attack on a corporate network. If users can be convinced to visit a link to a website or open an attachment, malware is downloaded to their device. A third of survey respondents indicated they have already become the victim of such an attack this year.
One problem faced by the healthcare industry in particular is the tactics used by criminals frequently change. Phishing was a technique most commonly associated with mass spam emails sent by individuals in the hope that some email users would fall for the scams. It would appear that now individuals, or specific groups of individuals, are being targeted. Many criminals now opt for quality over quantity, and are devising campaigns to target individuals with access to the data they seek. These “spear phishing” campaigns can prove to be highly effective.
Tackling the Threat from Phishing Emails
Efforts are being made by healthcare organizations to reduce the risk of individuals falling for campaigns. Spam filtering can be effective at limiting the volume of emails that make it through to the inboxes of healthcare workers, and training is now being provided to staff to help individuals recognize the signs of a phishing email. However, it would appear that while training is sometimes provided, this is not subsequently tested in many cases. Phishing email exercises designed to test users’ ability to identify phishing campaigns are still not being used by the majority of healthcare organizations. Only a quarter claimed they are using exercises to test staff readiness to deal with the threat, and that is a recipe for disaster.
by titanadmin | Sep 15, 2015 | Spam Advice |
City of London Police are sending emails containing important information about a murder suspect. You must be vigilant, and if you see this individual, you should not approach him! The attachment sent via email contains his image, so you will know to avoid him and alert the police if you see him. Unfortunately, opening the attachment will make you a victim. You will not be murdered, but you may end up having your bank account emptied. Yes, this is a City of London Police email scam, and it attempts to convince the good, law abiding public to infect their devices with malware.
City of London Police Email Scam Warning!
One of the latest email scams to be wary of, especially if you live in the UK, involves spam emails with the subject “London City Police.” Contained in the email is a bulletin detailing a murder suspect on the loose, together with a malware-infected attachment.
Fortunately for the wary, there is a clue in the subject that the email is not genuine. There is of course no “London City Police.” The police force in question is called “The City of London Police.” That said, the shock of receiving an email from law enforcement about a murderer on the loose may be enough to convince many to open the email and the attachment.
As one would expect, the email contains a stern warning, with the content phrased in such a way that it could in fact have been sent by the police force. A murderer on the loose in London is a serious matter, and this cunning email spam campaign has been devised to play on the fear that such a matter is likely to create.
How would the Police force have got your email address, and those of everyone else living in your area? That is something that many victims of this email scam may ponder after opening the attachment. Of course, by then it will be too late. Opening the attachment will result in malware being installed on the victim’s computer.
Fortunately, email scams such as this are easy to avoid, in fact, they would not even get to the point of being delivered to an inbox, if precautions have been taken, as explained by Steven Kenny, Customer Support Manager at TitanHQ.
Kenny pointed out that by using SpamTitan, computer users will be protected. He said, “This malware was blocked by SpamTitan before it had a chance to make it to users’ inboxes.” He went on to say, “The malware contained in the attachment was flagged as a virus. The attachment is a zip file, once executed; the malware goes to work.”
SpamTitan Blocked the City of London Police Email Scam
The image below is a screenshot of the City of London Police email scam, which was successfully blocked by SpamTitan.
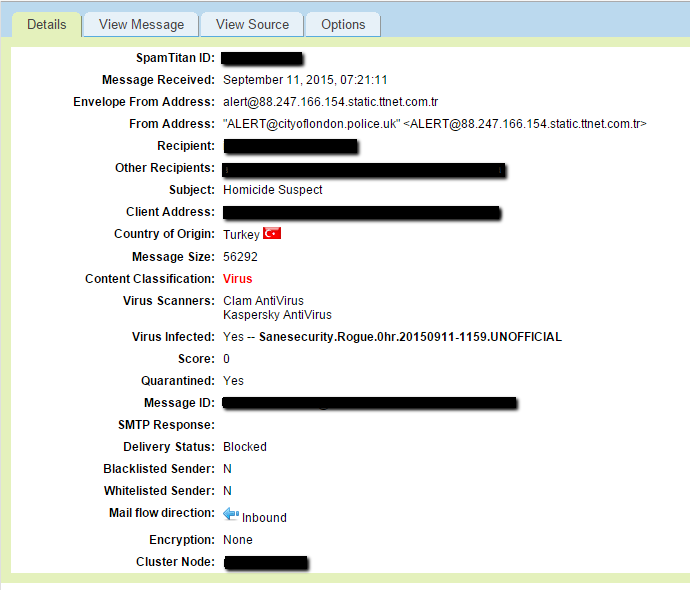
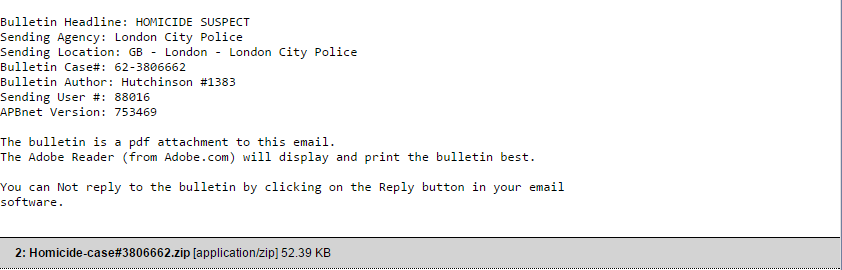
Current High Risk of Malware Infection
Malware poses a major risk to individuals, but businesses are especially at risk of infection. Employees may be wary of opening emails on their own devices, but are they as security conscious at work?
It is perhaps easier to believe that a work email address would be in the police database, rather than a personal email account. This may lead employees to believe that the email is genuine. Unfortunately, all it takes is for one employee to open an infected attachment, and their computer, and the network it connects to could be infected.
Since email is essential in business, protections must be put in place to ensure networks are not compromised as a result of the actions of employees. If malware is installed, the losses suffered can be considerable. It therefore can pay dividends to implement protection such SpamTitan spam filtering. This will prevent malware-infected emails from being delivered to employees’ inboxes.
by titanadmin | Sep 9, 2015 | Spam News |
A new Netflix phishing scam has been uncovered which works by telling users their Netflix accounts have been closed, requiring action to regain access to the service. Doing so will give your confidential login details to the scam operators.
Netflix has 62.27 million users, making it a highly attractive target for email scammers and spammers, and consequently Netflix phishing scams are common.
Latest Netflix Phishing Scam Convinces users to Reveal their Account Details
Recipients of the fake Netflix emails are required to click a link in order to reactivate their accounts. Unknown to the victims of this Netflix phishing scam, clicking on the link will direct them to a fake Netflix page, and by reactivating their accounts they will be giving the scammers their account names, passwords, and potentially other sensitive information.
Unfortunately for Netflix users, revealing passwords for one account may also mean other online accounts are compromised. Many users share their passwords across different websites, often using the same or similar passwords for Netflix, Facebook, and a host of other sites, including online banking portals.
TitanHQ recommends Netflix users ignore the email and delete it, and certainly do not to click on the link in the email. Phishing scams such as this usually direct users to a website that has been infected with malware, and clicking the link will result in that malware being downloaded, even if no information is entered on the page.
The best course of action is to login to your Netflix account as you would normally do, by typing in the URL or using your bookmark, and check your account status directly with Netflix. In all likelihood, it will still be active.
Further Information on the New Netflix Phishing Scam
Below is a screenshot of the latest Netflix phishing scam. The email appears genuine enough, although close inspection will reveal a few grammatical errors, such as missing apostrophes and misplaced exclamation marks. However, the email could be enough to fool the unwary, and especially individuals who tend to skim read emails and click first and think later.
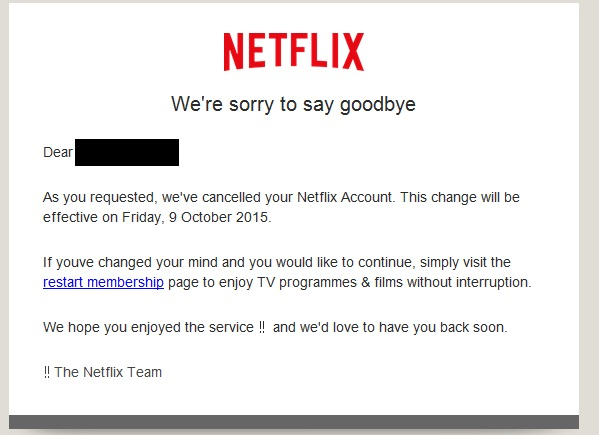
This phishing campaign is similar to others that have been recently sent to users of other online services. Phishing emails are devised to give the recipient a legitimate reason for handing over sensitive information, usually via webpage.
These include, but are not limited to:
- Upgrading security settings
- Performing essential system maintenance
- Verifying account details to prevent fraud
- Claiming a refund for a bill that has been paid
- Giving money back for an incorrect charge
- Offering you a free gift or service
Email scams often deliver malicious programs – malware – that has been created to steal confidential data such as account login names and passwords. Phishing campaigns are launched on social media, although email is the most common way that these scams are delivered.
Generally speaking, phishing campaigns can be categorized in three types:
Off-the-Shelf Jacking Toolkits
Criminals can purchase malware online which can be used to scam users into revealing passwords, which can subsequently be used to empty bank accounts, rack up debts, or hold people to ransom (the latter is becoming increasingly common and is referred to as ransomware). Once access is gained to an account or computer, Ransomware is used to encrypt data. The users are then required to pay a ransom to the perpetrator of the scheme in order to get their data unlocked.
These campaigns are usually opportunistic in nature, and involve millions of spam emails being sent. It is a numbers game, and some users will click on the phishing links and compromise their computers and networks.
Zero-day Vulnerability Exploits
The net is also cast similarly widely with these email phishing campaigns; however, the malware delivered is more complex, and the hackers behind these schemes are considerably more skilled. Zero-day vulnerabilities are new security flaws that have been discovered in software that have yet to be discovered by the software vendor. Consequently, patches do not exist to deal with the threat. Malware is created to exploit these vulnerabilities, which is usually delivered via an infected email attachment, although it can be downloaded when users visit a phishing website.
Spear Phishing Campaigns
These are targeted attacks that are conducted on individuals, or in some cases, organizations. The perpetrators of these schemes are skilled, and invest considerable time and effort into creating convincing campaigns. Oftentimes extensive information is gathered on the targets prior to the phishing emails being sent.
These schemes similarly use zero day vulnerabilities, and these advanced persistent threats (APT) have been used in a number of high profile attacks, such as the recent Carbanak malware attacks which have made the headlines recently.
How to Avoid Becoming a Phishing Victim
The best defense against attack is to be vigilant. Security awareness training for employees is essential. Staff members must be alerted to the risk, the consequences of clicking on a phishing link, and told how to identify scams. They should be instructed to check links before clicking (by hovering the mouse arrow over the link to check the real address).
It is also essential to keep all software patched and up to date. This applies to operating systems, applications, web browsers and other software. Software should be configured to update automatically wherever possible. Organizations should also develop concise patch management policies. Continuous security audits should be conducted and multi-layered network security controls developed.
There are a number of ways that spam and phishing emails can be prevented from being delivered to users, such as using a spam filter. Web filtering is particularly useful in prevent users from visiting known malware and phishing sites.
by titanadmin | Aug 26, 2015 | Spam News |
In 1998, ICANN issued the first domain names and IP addresses. There were not many top level domains (TLDs) to choose from. Each country had its own domain suffix, but the choice was limited to .com, .org, .net, .edu, .mil and .gov. Over the years, a few more options have been introduced such as .me, .mobi, .tv and .biz, but the suffix that has caused the most controversy is .xxx – a TLD intended for websites containing images of a sexual nature.
The .xxx TLD was seen as a method of introducing a red light district to the Internet, cleaning it up aside from a dirty corner that could be policed and easily blocked. Some purveyors of pornography allegedly welcomed the move, while others were opposed to it.
There were protests, but the new TLD was released in December 2011, and ICM Registry – a Fort Lauderdale for-profit business – was assigned responsibility for allocating the TLDs. Incidentally, the contract for this was quite lucrative. ICM Registry expected to make in the region of $200 million per year out of the deal.
Sometimes a good idea on paper doesn’t always work out so well in practice. For instance, some companies had spent a long time building up a brand name. They operated their domain on the .com domain, had bought up the .net, .mobi, .org versions and all other TLDs to protect their brand. They did not like the idea of having to do that again with the XXX version, and neither would they be willing to move their main site over to the .xxx TLD.
Few were in favor of the new XXX TLD
Pornographers were not the only objectors to the introduction of the .xxx TLD. The Bush Administration was opposed to the release. In fact ICANN was asked to withdraw support for the proposal. Criticism of the proposal mounted and ICANN came under a considerable amount of pressure. The American Department of Commerce, that has power over ICANN, received over 6,000 complaints about the introduction of the .xxx TLD. Even politicians who had originally backed the idea in the year 2000 changed their mind a decade later. Naturally, conservative groups also applied pressure to block the proposal. It was not enough. The TLD was released – with a delay of a month – and a swathe of new porn websites were subsequently launched.
Unsurprisingly, there has not been a reduction in the number of .com porn websites on the Internet. The new domain has seen even more created. Go figure!
ICANN was subsequently sued on the grounds that it had created a monopoly and that the introduction of the TLD forced businesses to spend even more money registering domain names to protect their brands from being piggybacked. After a couple of years, the lawsuit was dropped.
Controls put in place to protect trademarks
ICM regulators created the new TLD in order to clean up the Internet apparently. The .xxx TLD was seen as a way to make it easier for people wanting to view pornography to find it (it wasn’t exactly difficult, it must be said – type “porn” into a search engine for example) and as a way of promoting a responsible attitude toward it. It would, in theory at least, eventually lead to a dedicated area where pornographic websites could be housed.
However, trademark and patent protection advocate Inventa pointed out that opposition to the new .xxx TLD was virtually universal. No one wanted it apart from ICANN (and ICM Registry).
As for the fears that domain-sitters and entrepreneurs would take advantage, there were controls to prevent this. Eligibility criteria needed to be met. A company owning the trademarked .com version of a website could purchase the corresponding .xxx TLD to use as an adult domain or to prevent others from using it. Amazon.xxx, for example, could only be bought by Amazon.com. The ICM Registry reserved it for them. If there was no trademark, the domain name could be bought by anyone.
Was it worth all the effort?
ICM Registry would be inclined to agree, but as for making the Internet a safer place for children, cleaning up some porn, and having a dedicated online red light district, that clearly hasn’t worked. The biggest names in Internet porn still use their dotcom websites and have not made the switch to XXX domains. People interested in viewing pornography do not need an .xxx TLD to be able to find it, and don’t care what the name of the website is let alone the TLD, provided it gives them what they are looking for.
It is no easier to block pornographic websites than it was before the release. Simply blocking access to XXX suffixed websites will make no discernable difference to the amount of porn that is viewable online.
Until laws are passed to force porn websites to use the XXX domain – which would be incredibly difficult to implement – the move has not been particularly effective.
The only way to block effectively access block pornography from being displayed is to use a web filter such as SpamTitan Technologies. By using real-time classification, URL filtering, blocklists, keyword filters and other tools, SpamTitan Technologies web filtering solutions prevent the websites from being viewable. Something very important for schools, universities, colleges, charities, and corporations.
Any organization believing written policies on allowable uses of the Internet are sufficient to stop inappropriate use, should bear in mind that surveys have revealed that 20% of men and 13% of women have admitted to downloading pornographic content while at work. A recent pool of 500 Human Resources professionals indicated two thirds had discovered pornographic content on work computers, and the majority of porn is viewed during office hours (between 9am and 5pm).
If you want to stop employees accessing pornography in the workplace, the only effective way of doing so is with a robust web filtering solution.
by titanadmin | Aug 18, 2015 | Spam News |
Former employees of Kaspersky Labs have tipped off the media to an alleged practice of faking malware. It is claimed the company used fake malware to get rival anti-virus companies to flag the programs as malicious, potentially tarnishing their reputations with numerous fake positives.
For obvious reasons, the tip-offs have come from anonymous individuals who claim to have worked for Kaspersky Labs, yet their identities naturally cannot be verified. They could in fact be employees of rival anti-virus companies. It is therefore difficult to determine whether there is any truth in the allegations. Kaspersky Labs denied the allegations, in fact Eugene Kaspersky has been quite vocal on social media and has spoken out on Twitter, vehemently denying the accusations.
In an effort to find out more, we contacted Kaspersky Labs to find out further details. We received a reply as follows:
Kaspersky Denies Fake Malware Claims
“Contrary to allegations made in a Reuters news story, Kaspersky Lab has never conducted any secret campaign to trick competitors into generating false positives to damage their market standing. Such actions are unethical, dishonest and illegal.” Kaspersky went on to say, “Accusations by anonymous, disgruntled ex-employees that Kaspersky Lab, or its CEO, was involved in these incidents are meritless and simply false. As a member of the security community, we share our threat intelligence data and IOCs on advanced threat actors with other vendors, and we also receive and analyze threat data provided by others. Although the security market is very competitive, trusted threat data exchange is a critical part of the overall security of the entire IT ecosystem, and we fight hard to help ensure that this exchange is not compromised or corrupted.”
Interestingly though, there does appear to be a grain of truth in the accusations, with the anti-virus software giant confirming that harmless malware was in fact created and uploaded. However, this was part of a test of its own software systems, not an attempt to discredit rivals. The statement issued explained the experiment:
“In 2010, we conducted a one-time experiment uploading only 20 samples of non-malicious files to the VirusTotal multi-scanner, which would not cause false positives as these files were absolutely clean, useless and harmless. After the experiment, we made it public and provided all the samples used to the media so they could test it for themselves. We conducted the experiment to draw the security community’s attention to the problem of insufficiency of multi-scanner based detection when files are blocked only because other vendors detected them as being malicious, without actual examination of the file activity (behavior).” The story was reported at the time in the media.
Kaspersky also explained that “After that experiment, we had a discussion with the antivirus industry regarding this issue and understood we were in agreement on all major points.” Further information on cascading false positives can be found here.
“In 2012, Kaspersky Labs was among the affected companies impacted by an unknown source uploading bad files to VirusTotal, which led to a number of incidents with false-positive detections. To resolve this issue, in October 2013, during the VB Conference in Berlin, there was a private meeting between leading antivirus vendors to exchange the information about the incidents, work out the motives behind this attack and develop an action plan. It is still unclear who was behind this campaign.”
False positives are common in the internet security industry. What is not known, and probably never will be, is who creates the bad samples that lead to false positives. As Ronan Kavanagh, CEO at TitanHQ, points out,“Kaspersky is an excellent product, we have never had an issue with it, quite the opposite in fact. Of course we have seen false positives, we were targeted by bad samples as were many other security vendors but we would have no visibility on who carried out these attacks. The critical thing is that as an industry we work together in fighting back”.
Have you discovered false positives when you have run your software security programs?